1/ A pro-Hamas persona is making noise from recent airport “hacks”, including broadcast system defacements in 🇨🇦 Kelowna & 🇺🇸 Harrisburg.
But digging deeper, their actions remain low-impact and opportunistic. Lets take a deeper look..🧵
But digging deeper, their actions remain low-impact and opportunistic. Lets take a deeper look..🧵
2/ Their “operations” rely on publicly exposed CMS, display, and PA systems, seemingly no exploits, no malware, just abused public services which may lack proper authentication controls. The targets are selected for visibility and attention, not strategic value.
3/ The timeline begins in August 2025, with Turkish website defacements, later spreading to Israeli domains. Claims of website “takedowns” followed, though all were short-lived and often quickly restored.
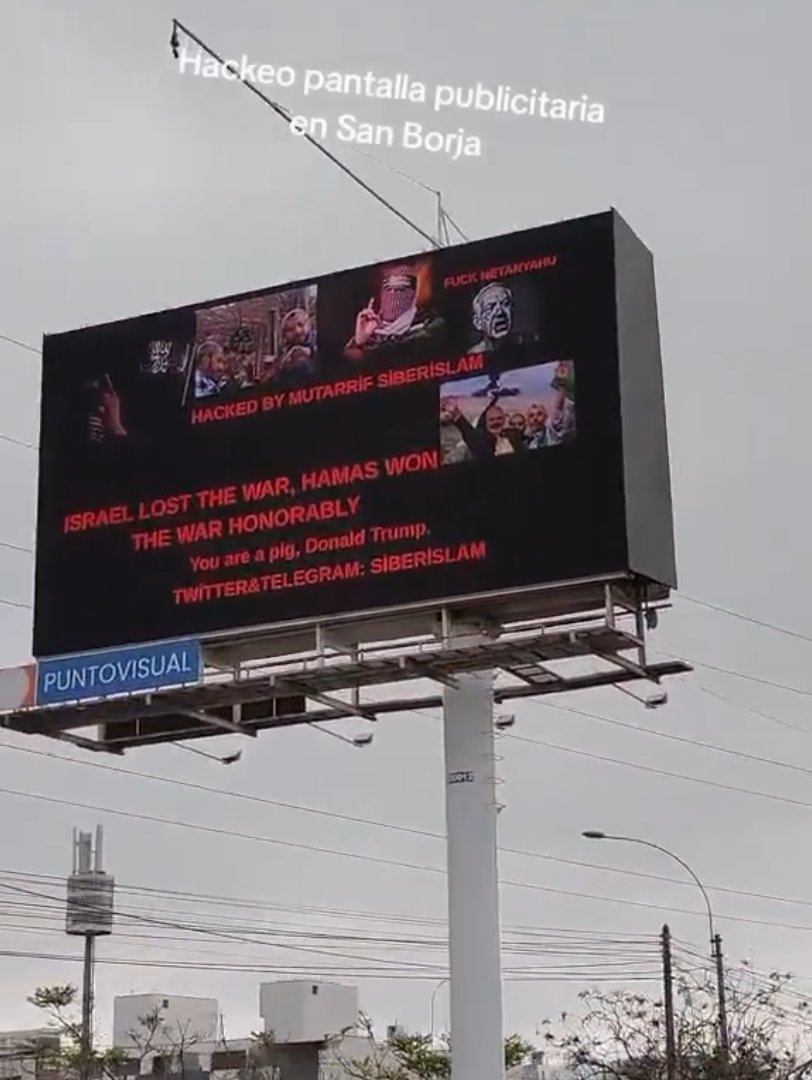
4/ By September, they aimed at digital signage systems, such as some public billboards in Peru, and fast-food menus in Turkey, the U.S., and Israel. These are soft targets with dramatic optics but zero real operational impact. Several were major Western brands operating in TR/IL. 


4.25/ They had a limited case of "hacking a TV station". Looks like it was a news station in Nigeria exposing their broadcast platform system online. 

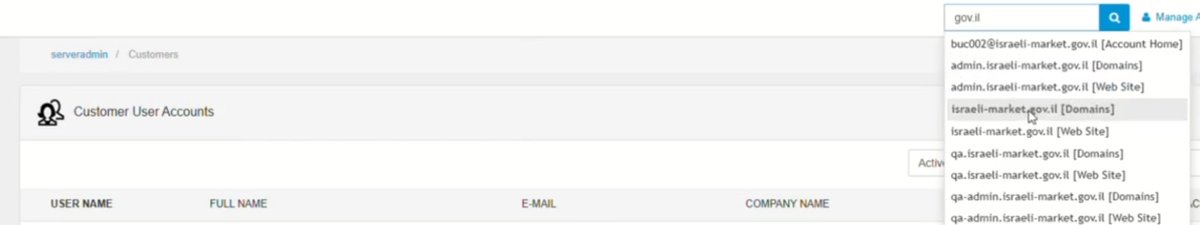
4.5/ Note, some limited personal contact info leaking and claims of calling Govt. officials (IL/TY), but unable to verify authenticity of those calls. However sources appear to simply be, again, exposed CMS systems with customer details. Examples: 


5/ This week’s incidents at Canada's Kelowna International Airport (@ylwkelowna) and Harrisburg International Airport (PA, USA - @FlyHIA) elevated the group’s visibility.
6/ In both cases, the actor accessed announcement systems, broadcasting pro-Hamas messages on par with their usual message. The only signage I see impacted are from the individual airline checkin counters in CA.
(audio: )
(audio: )
https://x.com/WGAL/status/1978445844106949058

7/ These are not aviation security breaches, they’re public-facing system compromises, embarrassing but short-lived. Outsider hot take: only a disruption of commercial comms, not operations. (Flights were temporarily delayed, and airport staff reverted to manual announcements.)
8/ Now, who’s behind it?
Our analysis suggests this persona is likely a single individual, not a coordinated collective. Their style, cadence, and digital footprint indicate one operator maintaining multiple social media channels.
Our analysis suggests this persona is likely a single individual, not a coordinated collective. Their style, cadence, and digital footprint indicate one operator maintaining multiple social media channels.
9/ They’re active across Telegram and Twitter/X, posting defacement screenshots and recycling imagery from real Hamas propaganda to amplify credibility.
9.5/ Fun.. in some google search hype vids they post online, their default browser language is Turkish, and using Microsoft Edge browser. Other cases its Chrome in Turkish, but local German ads. VPN be poppin'
10/ Notably, the persona repeatedly uses Abu Obaida’s headshot, the masked spokesperson of Hamas’ military wing, despite the fact that the real Abu Obaida was reported killed in August. 

11/ This tactic of reusing authentic wartime media is common among low-skill influence actors. It’s a way to borrow legitimacy from real conflict footage and inflate perceived alignment with larger operations.
12/ From an analytical perspective, this persona fits the mold of ideologically motivated but technically shallow hacktivists.. Prioritizing message reach and emotional impact over actual intrusion capability.
13/ It’s also worth noting: this exact pattern of “hacktivist” behavior... opportunistic website defacements, Telegram propaganda, and recycled imagery, has historically been used by Western individuals and as a cover for Iranian state-sponsored actors.
14/ Current assessment (based on VIBESINT™):
👉 Likely a single ideological actor
👉 Not directly coordinated with Hamas or a state entity
👉 Motivated by identity, attention, and perceived alignment with global conflict narratives
👉 Likely a single ideological actor
👉 Not directly coordinated with Hamas or a state entity
👉 Motivated by identity, attention, and perceived alignment with global conflict narratives
15/ Bottom line atm:
- Opportunistic, low-impact activity
- Heavy on propaganda, questionable on skill
- Visibility ≠ capability
A reminder that not all “cyber warfare” headlines represent capable adversaries. Sometimes, they’re just one person with a vpn, kali and a message.
- Opportunistic, low-impact activity
- Heavy on propaganda, questionable on skill
- Visibility ≠ capability
A reminder that not all “cyber warfare” headlines represent capable adversaries. Sometimes, they’re just one person with a vpn, kali and a message.
• • •
Missing some Tweet in this thread? You can try to
force a refresh