This report contains 287 browser extensions tracking 37 million+ users. These were identified using methodology of sandboxing extensions, automatically browsing to URLs, and measuring a data ratio transferred. Real companies, fake services, well established, it's a mixed bag. 

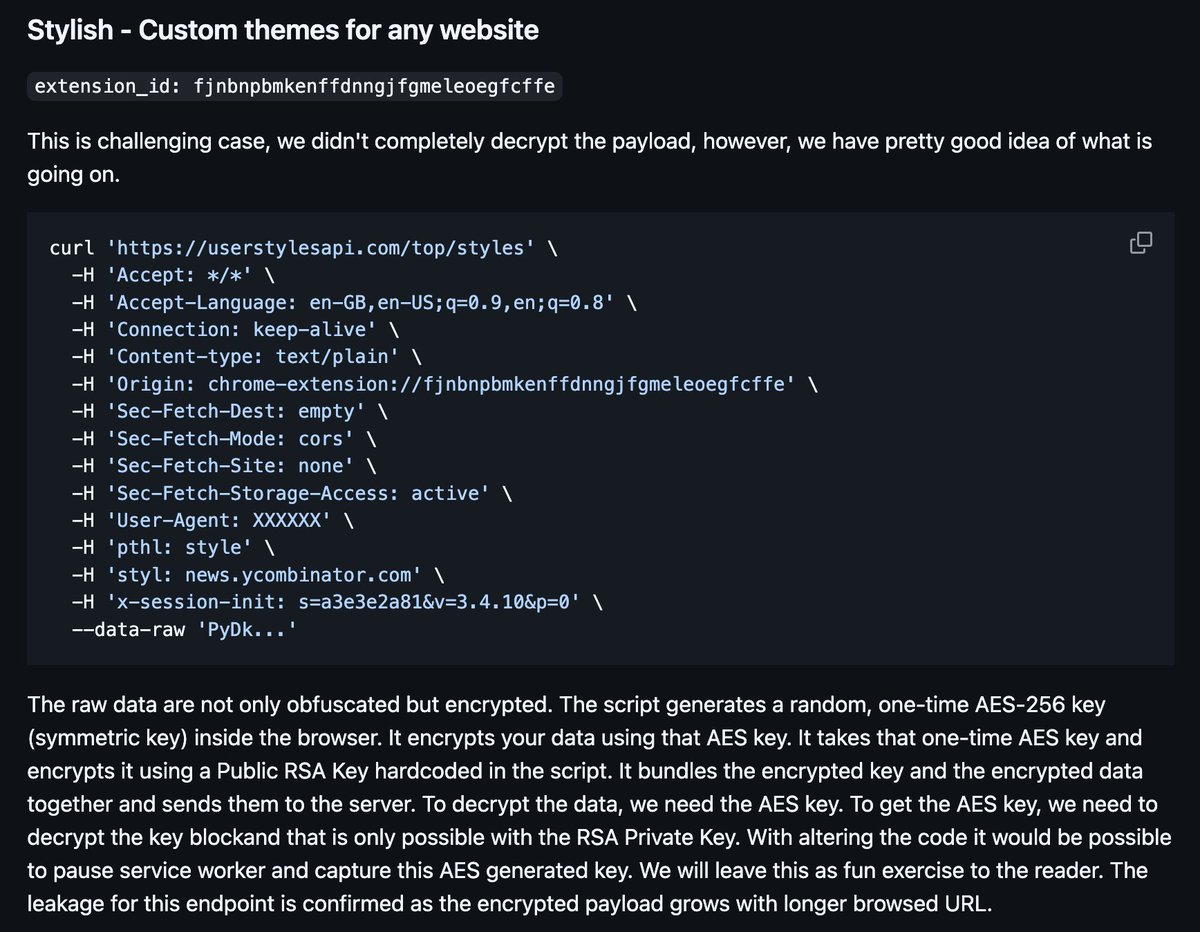
For many of these extensions, it isn't just an incidental leak that might be tracking your browsing session. They add methods to encrypt payloads before sending to their callback services. 
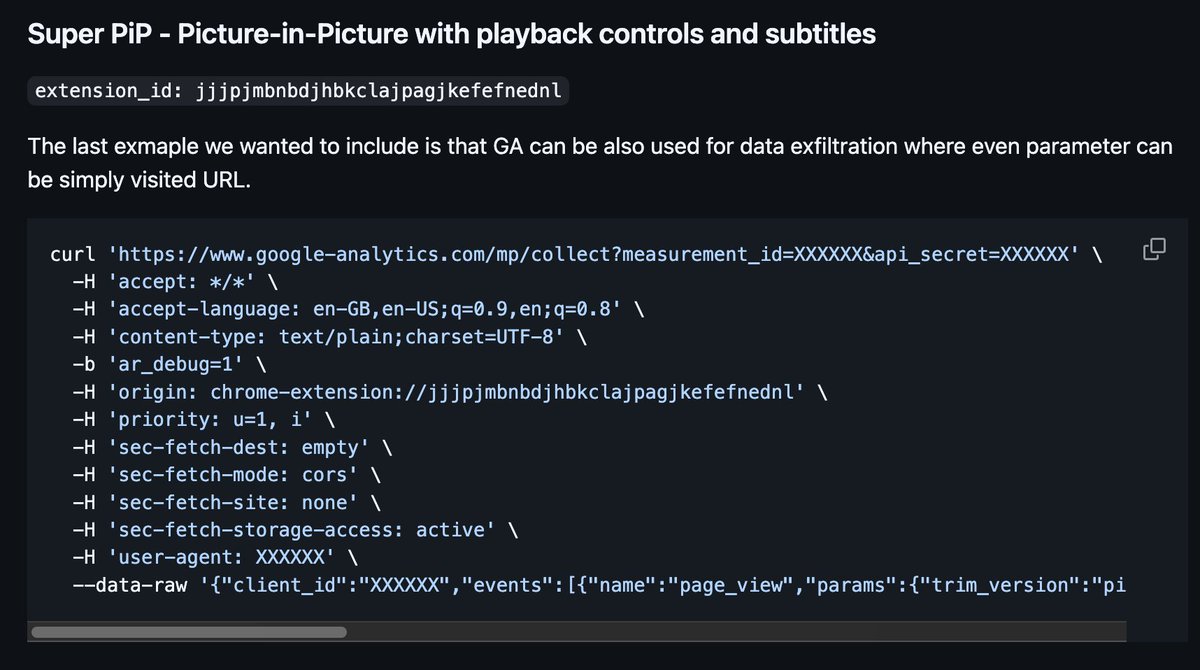
Others abuse well known services like Google Analytics as an exfil destination. What should likely only be approved for extension usage analytics ends up capturing full browsing behaviors. 
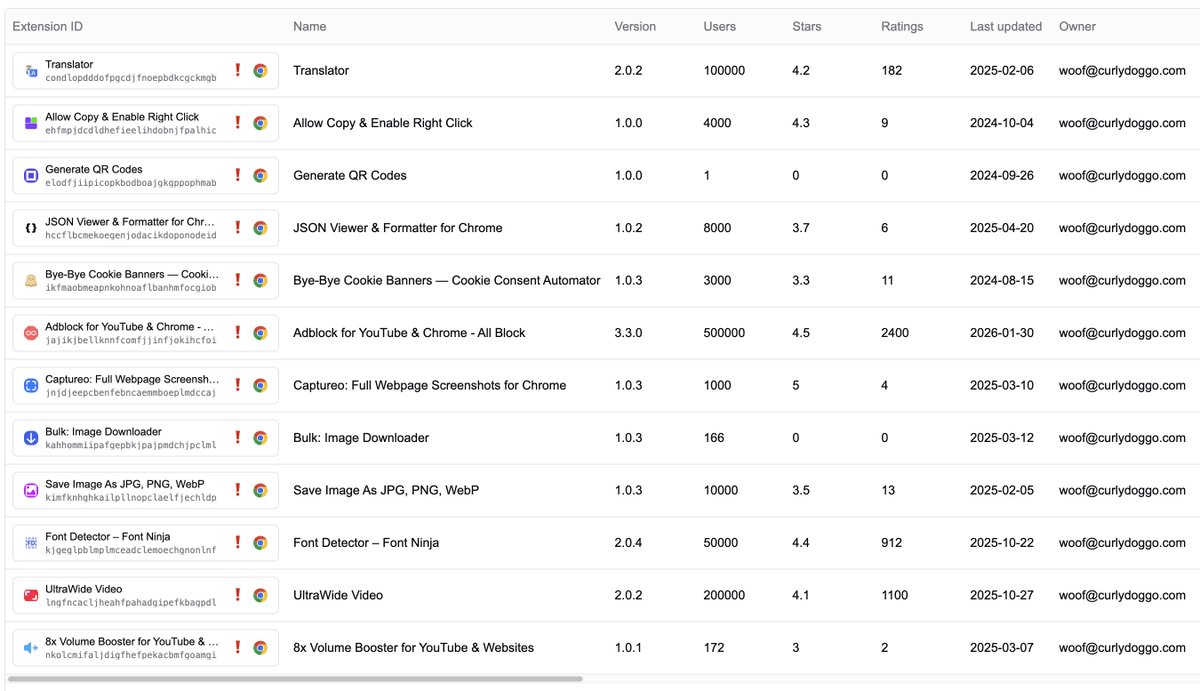
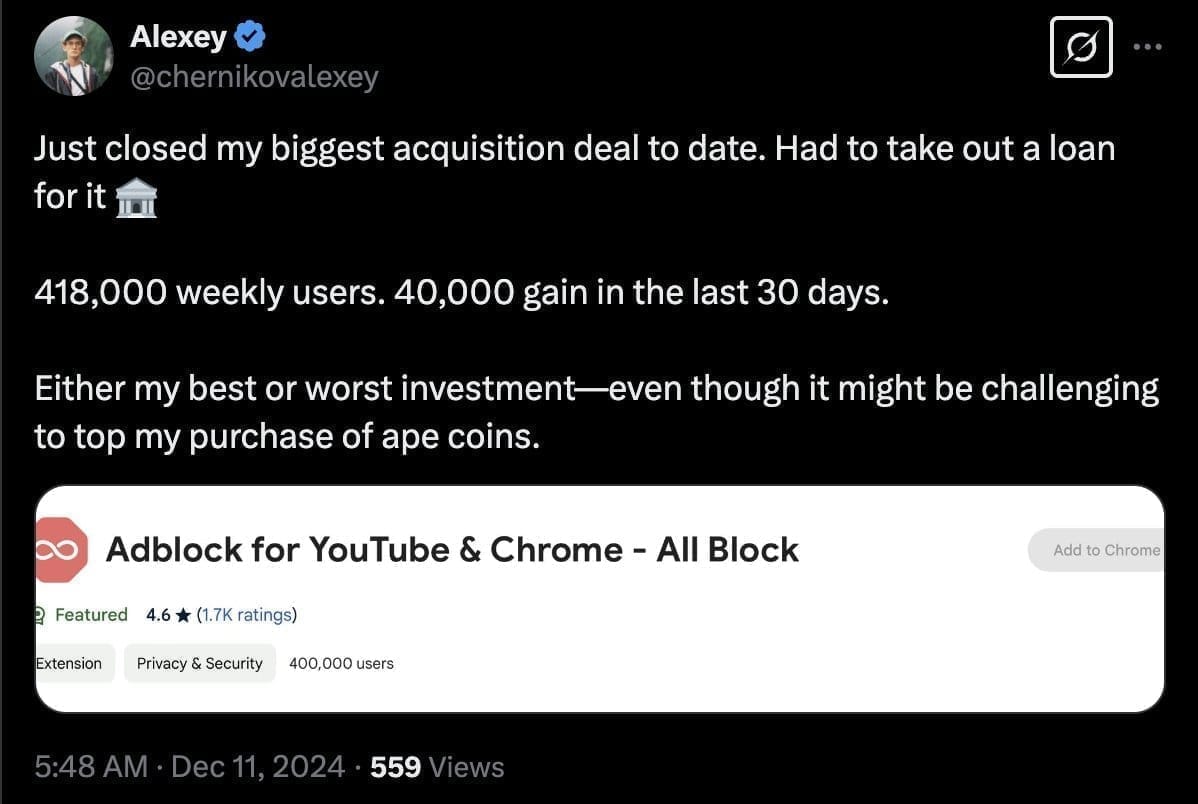
We've identified ~12 of these by the same publisher which has a history of buying extensions and adding tracking behaviors to them. These ownership transfer events have been included in @secureannex for over a year. 

The full list below. Browsing tracking can be a grey area, but obviously poor for user privacy. What is clear is how pervasive it can be in extensions that advertise 'ad blocking', 'mouse gestures', 'chatgpt sidebars' and other benefits.
github.com/qcontinuum1/sp…
github.com/qcontinuum1/sp…
• • •
Missing some Tweet in this thread? You can try to
force a refresh










