Thread 🧵
1/ Ukrainian hackers, working alongside independent OSINT analysts, have conducted a successful counter-operation targeting #Russian attempts to bypass #Starlink restrictions.
We are revealing the details now — because the operational effect has already been secured.
1/ Ukrainian hackers, working alongside independent OSINT analysts, have conducted a successful counter-operation targeting #Russian attempts to bypass #Starlink restrictions.
We are revealing the details now — because the operational effect has already been secured.
2/ After technical restrictions limited Russian #military access to Starlink, Russian channels began actively searching for “drops” — Ukrainian citizens willing to activate terminals on their behalf for small crypto payments. This vulnerability was anticipated. 

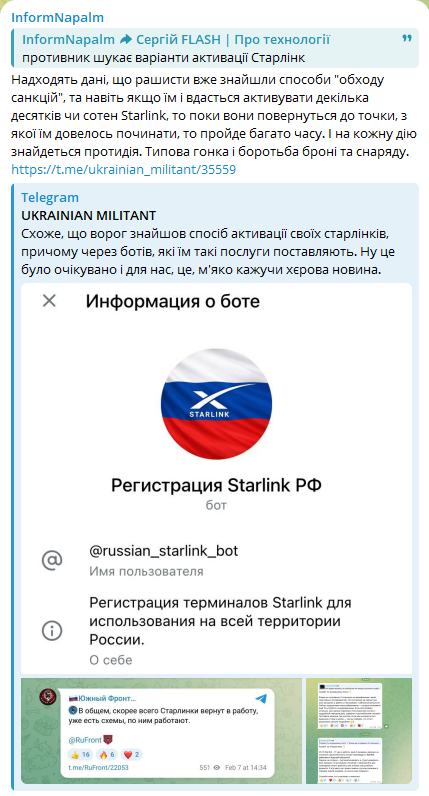
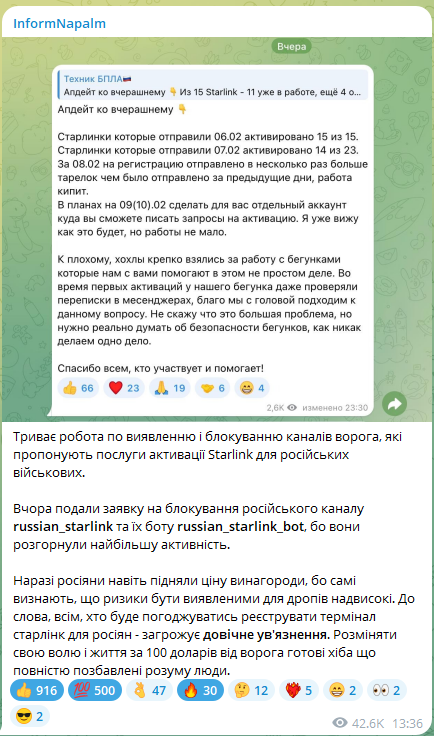
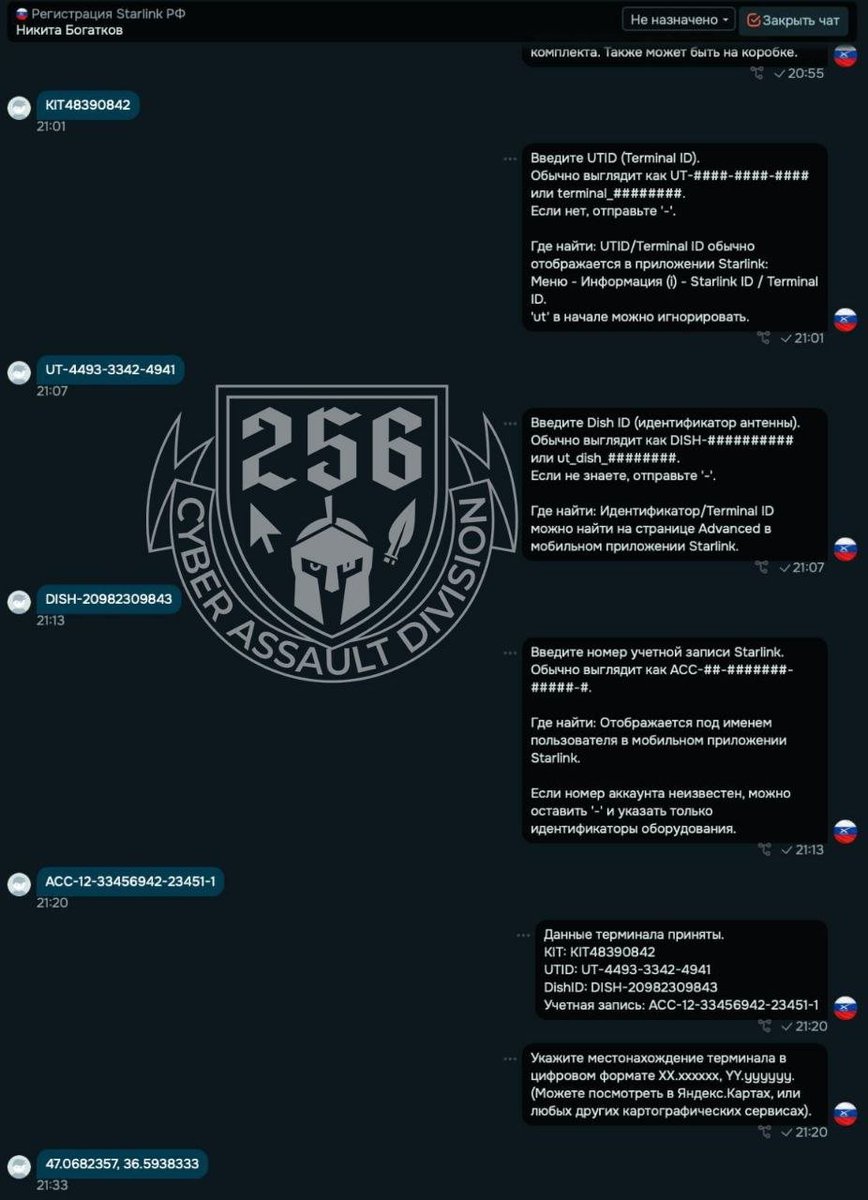
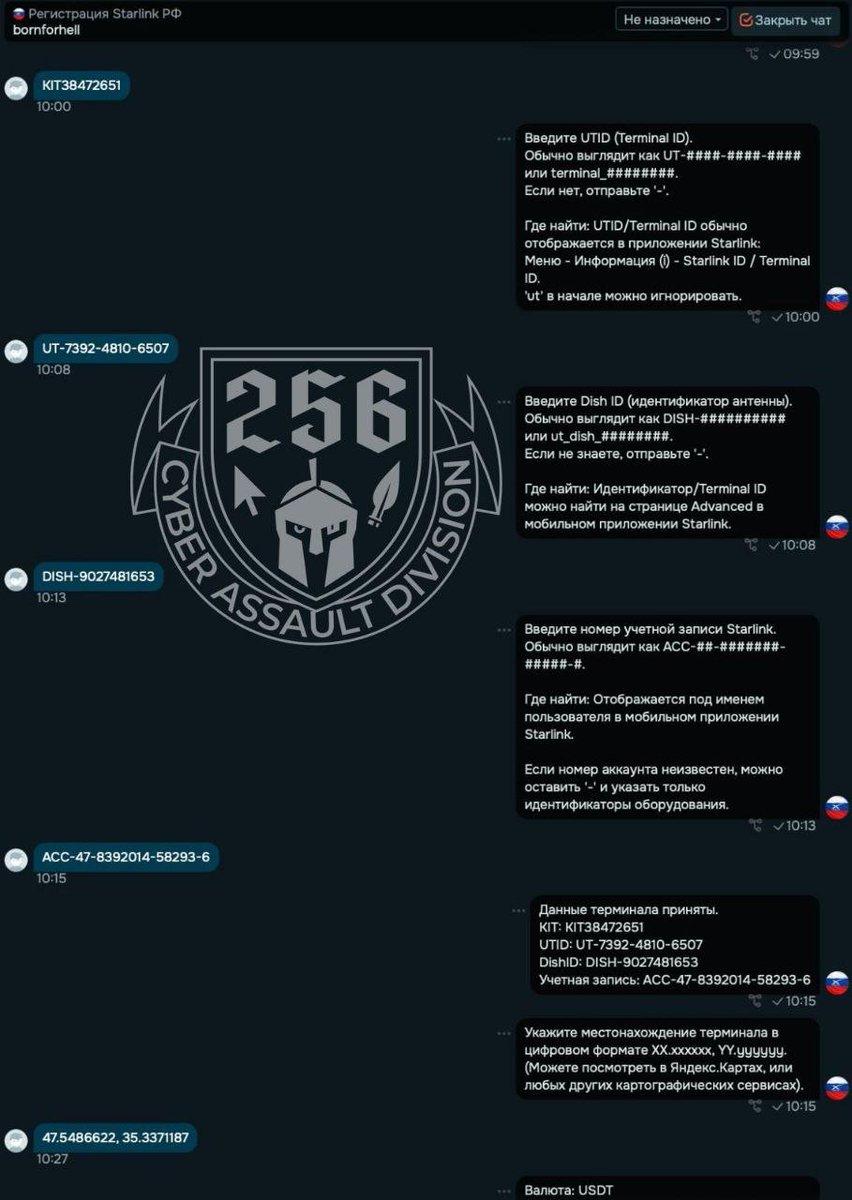
3/ Instead of passively observing, Ukrainian cyber specialists @256CyberAssault and OSINT volunteers @InformNapalm & MILITANT created controlled channels and bots offering “activation services.”
The goal was not activation.
The goal was collection.

The goal was not activation.
The goal was collection.
@256CyberAssault 4/ Within a week, the operation resulted in:
• 2,400+ data packages on Russian-operated Starlink terminals
• Dozens of contacts from collaborators willing to assist the enemy
• Thousands of dollars transferred by Russian servicemen desperately trying to restore connectivity
• 2,400+ data packages on Russian-operated Starlink terminals
• Dozens of contacts from collaborators willing to assist the enemy
• Thousands of dollars transferred by Russian servicemen desperately trying to restore connectivity
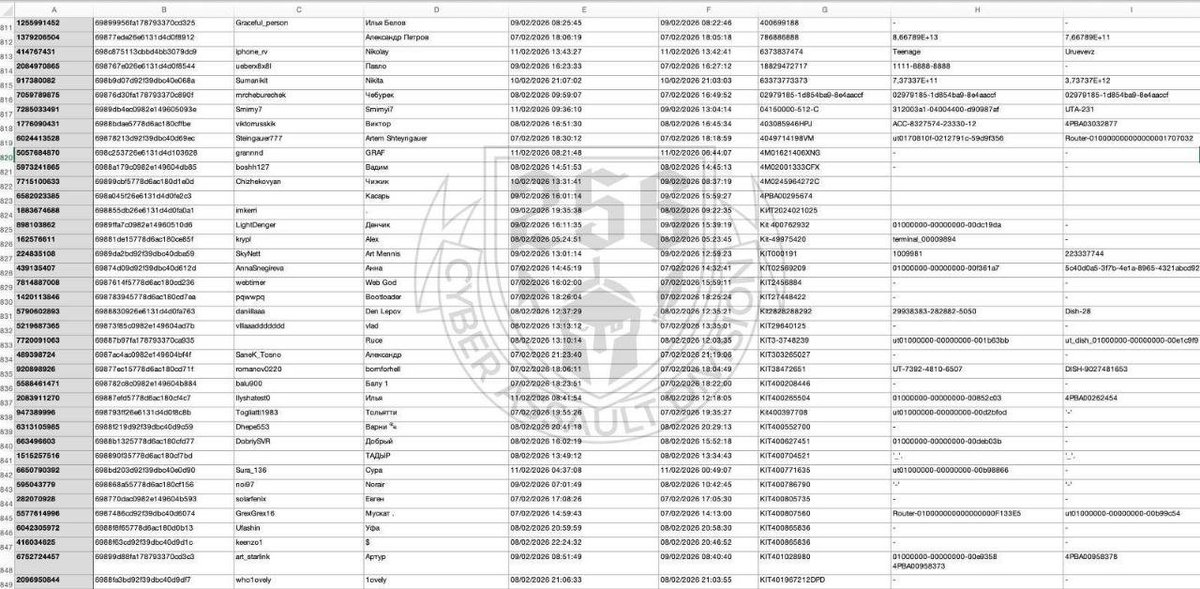
@256CyberAssault 5/ All relevant technical data was transferred to the appropriate Ukrainian structures.
Terminals identified in the process were rendered permanently inoperable.
Attempts to exploit Ukrainian civilians were documented.
Terminals identified in the process were rendered permanently inoperable.
Attempts to exploit Ukrainian civilians were documented.
@256CyberAssault 6/ We disclose this now for two reasons:
First, the operational phase has concluded and the intended effect has been achieved.
Second, transparency serves a strategic purpose.

First, the operational phase has concluded and the intended effect has been achieved.
Second, transparency serves a strategic purpose.

@256CyberAssault 7/ Russian forces must understand:
Attempts to bypass restrictions will not only fail — they will expose positions, identities, and networks.
Every workaround becomes an intelligence opportunity.
Attempts to bypass restrictions will not only fail — they will expose positions, identities, and networks.
Every workaround becomes an intelligence opportunity.
@256CyberAssault 8/ This operation demonstrated something essential:
#Ukrainian #cyber and volunteer #intelligence communities do not react passively.
We anticipate, we adapt, and we act several steps ahead.
#Ukrainian #cyber and volunteer #intelligence communities do not react passively.
We anticipate, we adapt, and we act several steps ahead.
@256CyberAssault 9/ #Starlink restrictions were only the beginning.
The battlefield is not limited to trenches or drones.
It includes networks, deception, data, and psychological pressure.
The battlefield is not limited to trenches or drones.
It includes networks, deception, data, and psychological pressure.
@256CyberAssault 10/ For the Russian military, uncertainty is now part of the equation. For #Ukraine, coordination between hackers, OSINT analysts, and defense structures remains a force multiplier.
End of thread 🧵
End of thread 🧵
• • •
Missing some Tweet in this thread? You can try to
force a refresh