
Building @Vulncure ⚡| Helping founders fix vulnerabilities before hackers find them. Talk to me about: Bug Bounties, LLM Security & React.👇 Book a 15-min Demo
4 subscribers
How to get URL link on X (Twitter) App




 Usage (Bookmarklet)
Usage (Bookmarklet)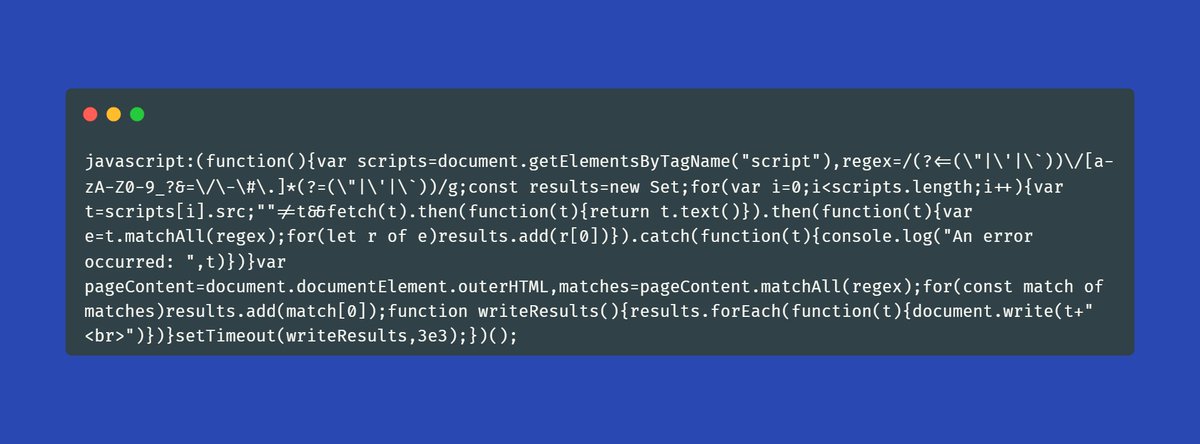

 📌 GET:
📌 GET: 


 💻Security Misconfiguration Occurance:
💻Security Misconfiguration Occurance:
 • Don’t report Information Disclosure, try to use it (Privileges Escalation).
• Don’t report Information Disclosure, try to use it (Privileges Escalation).
 • 7:00 AM - 7:30 AM: Meditation and reading Spiritual Book
• 7:00 AM - 7:30 AM: Meditation and reading Spiritual Book
 • Gain a strong understanding of the Android operating system and the underlying Linux system that it is built on
• Gain a strong understanding of the Android operating system and the underlying Linux system that it is built on


