The first #Emotet spam run of the last quarter of 2018 adds malicious PDF files in the infection chain. PDF attachments have malicious link that downloads a doc with malicious macro. If allowed to run, the macro in the doc executes a PowerShell code that downloads the payload. 



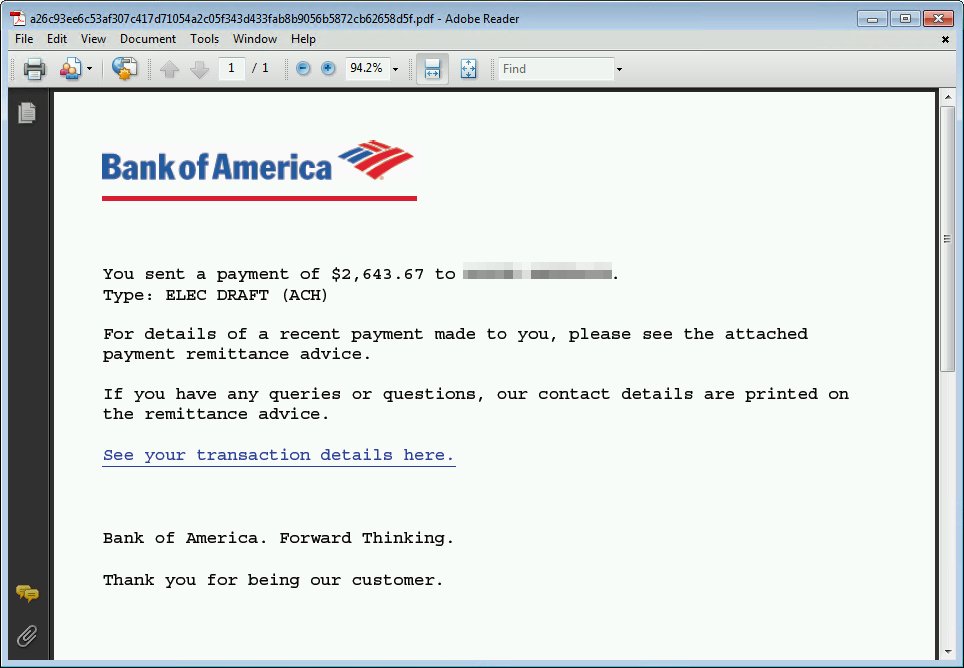

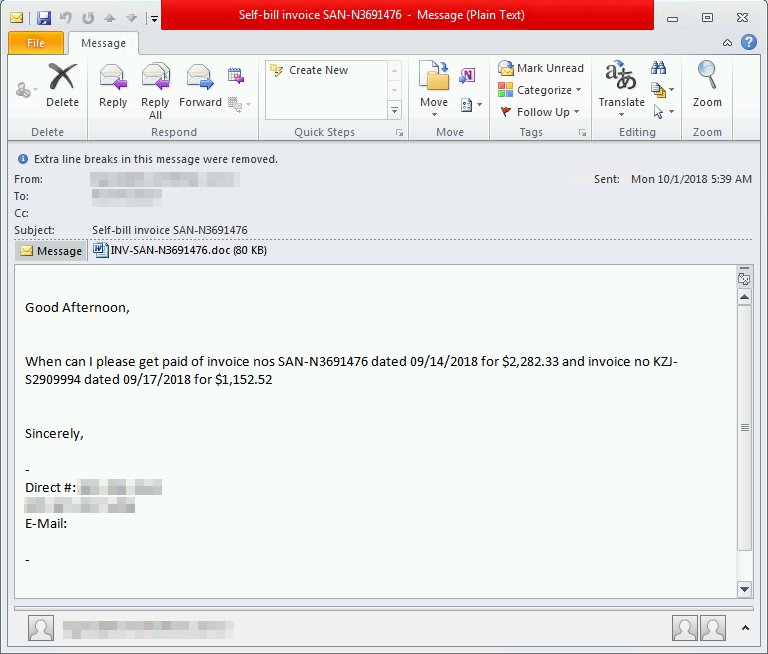
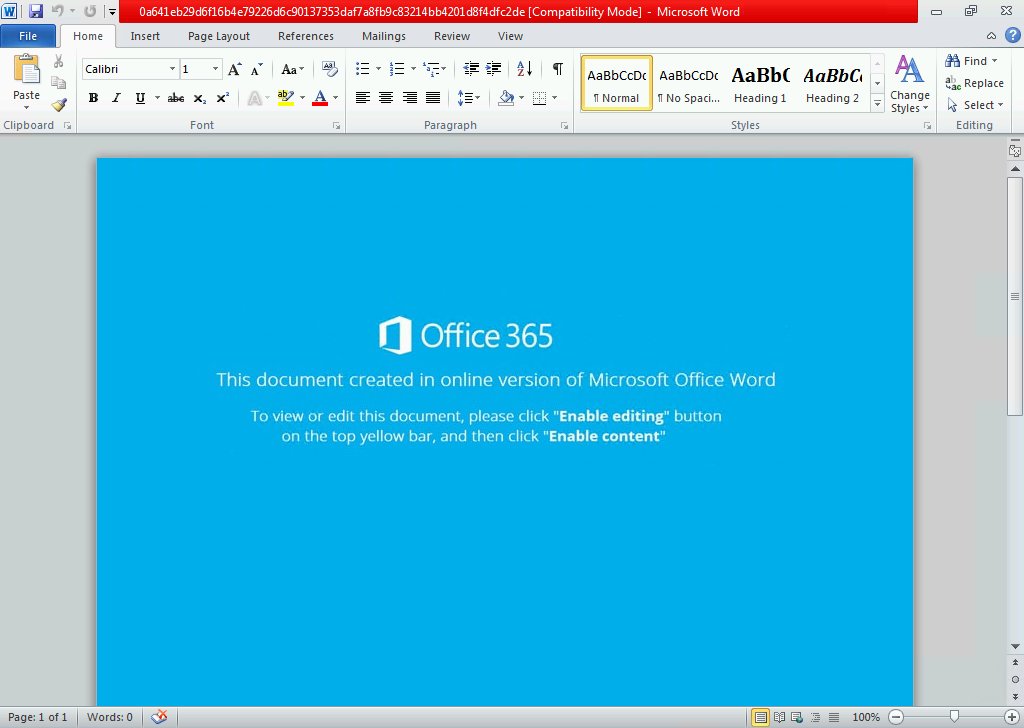
Notably, some emails ditch the PDF and carry the malicious document itself (as per usual). No matter, antivirus capabilities in Windows Defender ATP block the malicious PDF and doc files in this campaign as Trojan:O97M/Sonbokli.A!cl. Office 365 ATP blocks the malicious emails.
The payload of this campaign is #Emotet (SHA-256: 86770d8bd51a10131e0b4b3b1bc3f49578d05b372d7f19ace910bb7abc5f70a8)
• • •
Missing some Tweet in this thread? You can try to
force a refresh








