
We are Microsoft's global network of security experts. Follow for security research and threat intelligence.
9 subscribers
How to get URL link on X (Twitter) App


 To execute this tactic, the threat actor masquerades as a South Korean government official and over time builds rapport with a target before sending a spear-phishing email with an PDF attachment.
To execute this tactic, the threat actor masquerades as a South Korean government official and over time builds rapport with a target before sending a spear-phishing email with an PDF attachment.

 Exploitation of vulnerabilities remains a key method for initial access. In October, the threat actor Lace Tempest, known for exploiting 0-days in file-transfer software, was observed exploiting vulnerabilities in Cleo products (CVE-2024-50623, CVE-2024-55956).
Exploitation of vulnerabilities remains a key method for initial access. In October, the threat actor Lace Tempest, known for exploiting 0-days in file-transfer software, was observed exploiting vulnerabilities in Cleo products (CVE-2024-50623, CVE-2024-55956).

 Vanilla Tempest receives hand-offs from Gootloader infections by the threat actor Storm-0494, before deploying tools like the Supper backdoor, the legitimate AnyDesk remote monitoring and management (RMM) tool, and the MEGA data synchronization tool.
Vanilla Tempest receives hand-offs from Gootloader infections by the threat actor Storm-0494, before deploying tools like the Supper backdoor, the legitimate AnyDesk remote monitoring and management (RMM) tool, and the MEGA data synchronization tool.

 Octo Tempest, known for its sophisticated social engineering techniques, identity compromise and persistence, focus on targeting VMWare ESXi servers, and deployment of BlackCat ransomware, accounts for a significant bulk of our investigations and incident response engagements.
Octo Tempest, known for its sophisticated social engineering techniques, identity compromise and persistence, focus on targeting VMWare ESXi servers, and deployment of BlackCat ransomware, accounts for a significant bulk of our investigations and incident response engagements.

 The PDF contained a URL that downloads a digitally signed Windows Installer (.msi). Executing the MSI led to Qakbot being invoked using export “hvsi” execution of an embedded DLL. The MSI package was signed with the SignerSha1/Thumbprint 50e22aa4b3b145fe1193ebbabed0637fa381fac3.
The PDF contained a URL that downloads a digitally signed Windows Installer (.msi). Executing the MSI led to Qakbot being invoked using export “hvsi” execution of an embedded DLL. The MSI package was signed with the SignerSha1/Thumbprint 50e22aa4b3b145fe1193ebbabed0637fa381fac3. 

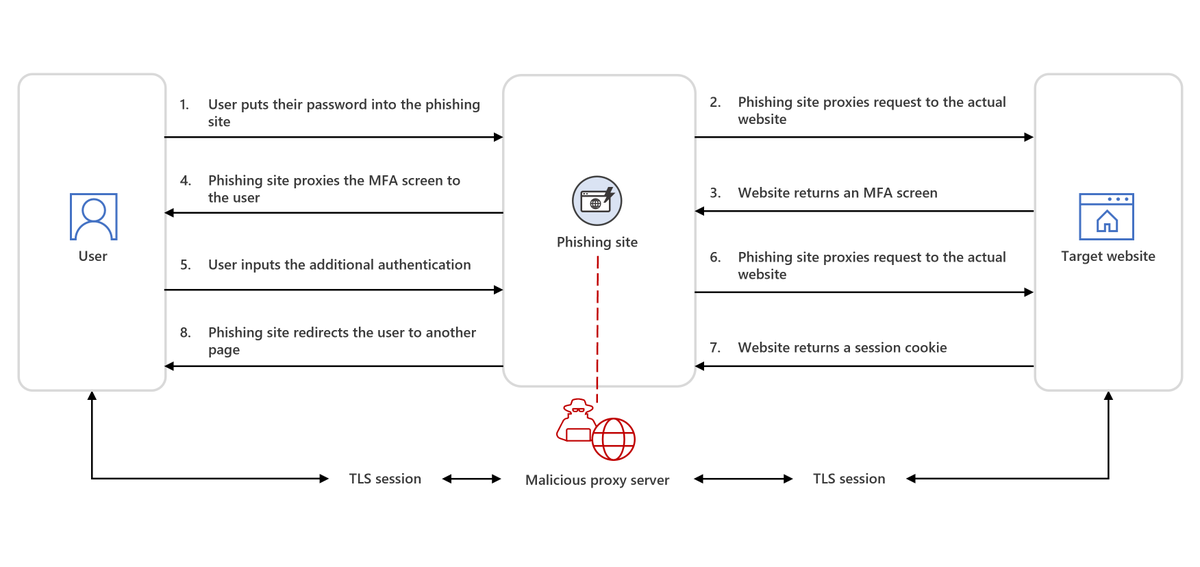


 Exploitation is often followed by deployment of a web shell w/ data exfil capabilities. CVE-2023-34362 allows attackers to authenticate as any user. Lace Tempest (Storm-0950, overlaps w/ FIN11, TA505) authenticates as the user with the highest privileges to exfiltrate files.
Exploitation is often followed by deployment of a web shell w/ data exfil capabilities. CVE-2023-34362 allows attackers to authenticate as any user. Lace Tempest (Storm-0950, overlaps w/ FIN11, TA505) authenticates as the user with the highest privileges to exfiltrate files.
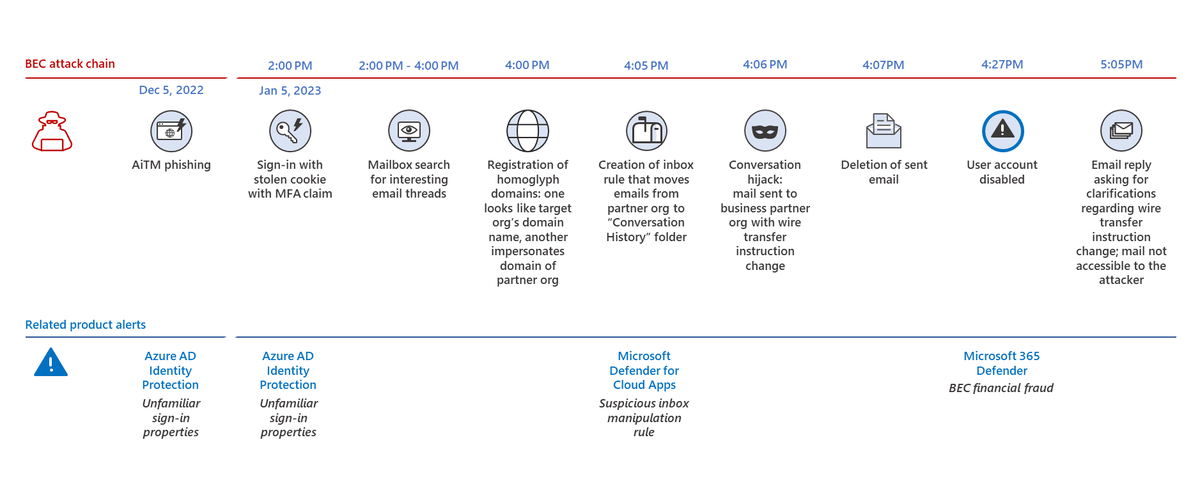
 In this attack, after signing in, attackers spent about 2 hours searching the compromised account’s mailbox for an email thread to hijack. Finding one, the attackers registered 2 homoglyph domains, one to impersonate the target org, one for a partner org relevant to the thread.
In this attack, after signing in, attackers spent about 2 hours searching the compromised account’s mailbox for an email thread to hijack. Finding one, the attackers registered 2 homoglyph domains, one to impersonate the target org, one for a partner org relevant to the thread.