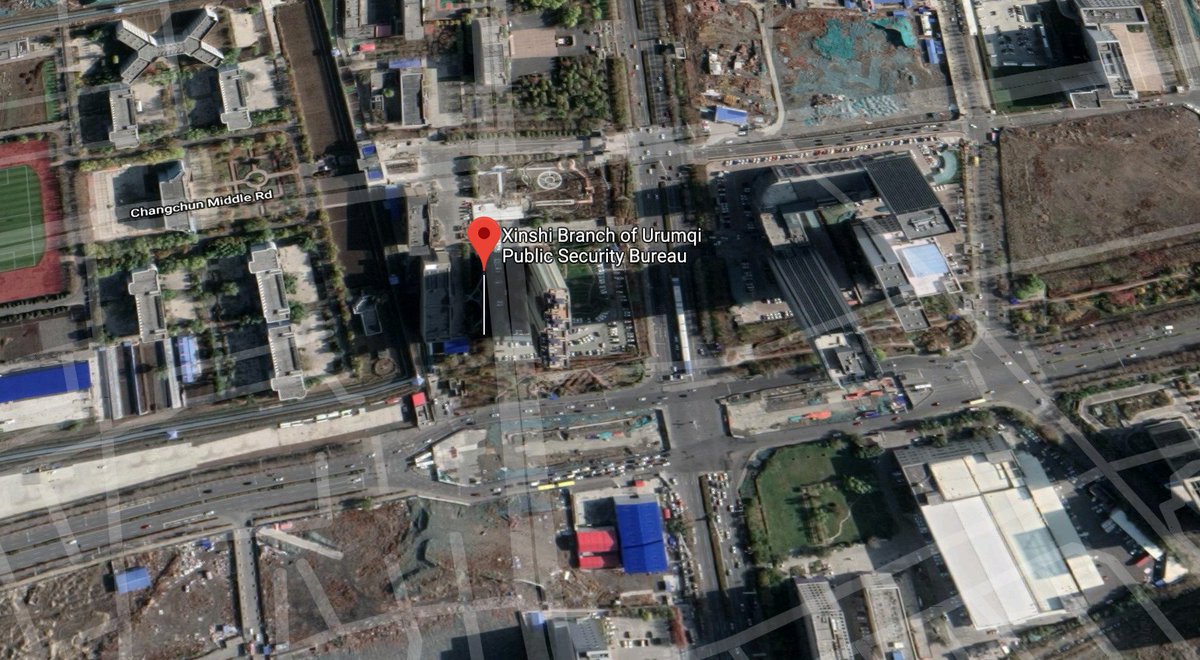
There is this company in China named SenseNets. They make artificial intelligence-based security software systems for face recognition, crowd analysis, and personal verification. And their business IP and millions of records of people tracking data is fully accessible to anyone. 
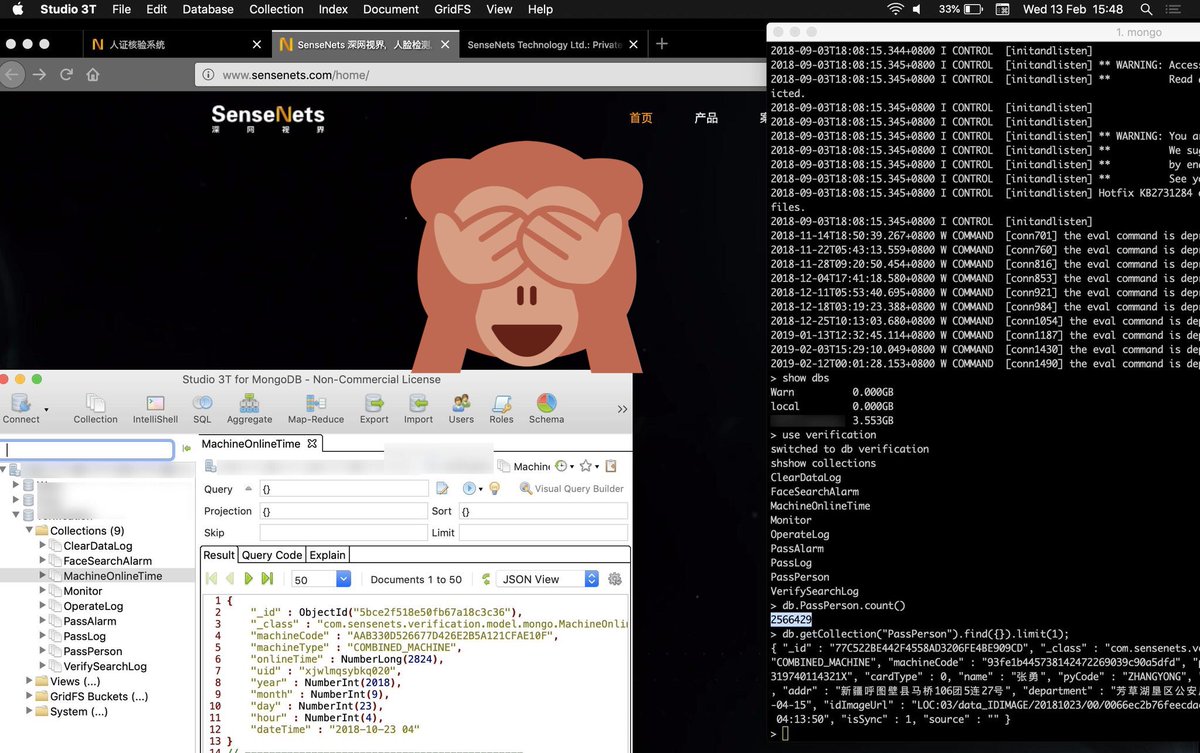
This database contains over 2.565.724 records of people with personal information like ID card number (issue & expire date, sex, nation, address, birthday, passphoto, employer and which locations with trackers they have passed in the last 24 hours which is about 6.680.348 records
The database is now "protected" with a firewall rule. Although the suspicion is that all traffic from outside China is blocked for this service. At least the data is not to access the data anymore for outlanders. 
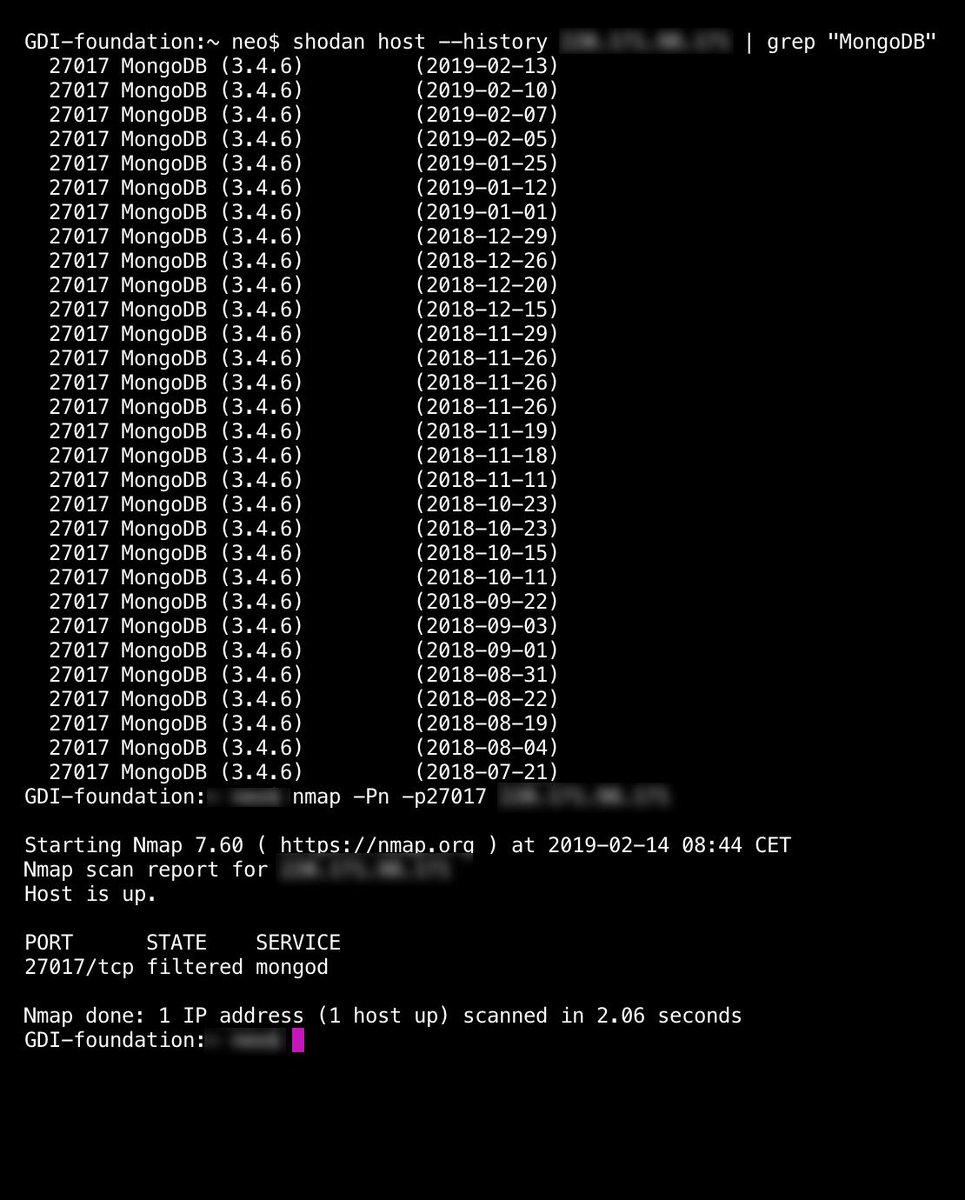
In the process of tracking down each tracker, we even stumbled upon abandon locations (according to Google maps). If there is anyone living or working in Keriya who can confirm this location? We also would like to a photo of the device. 

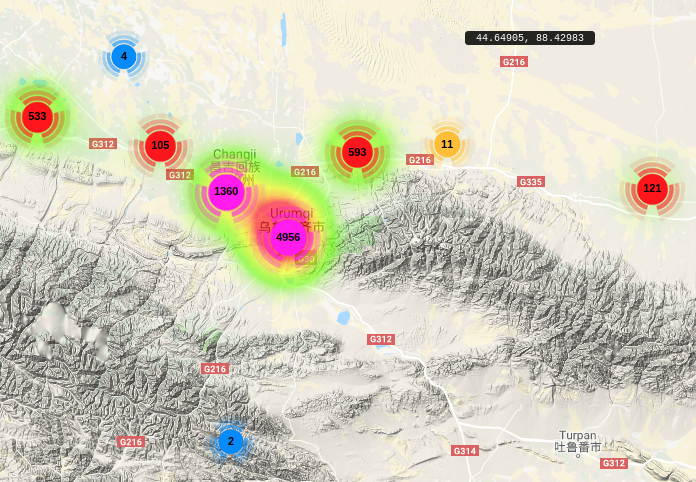
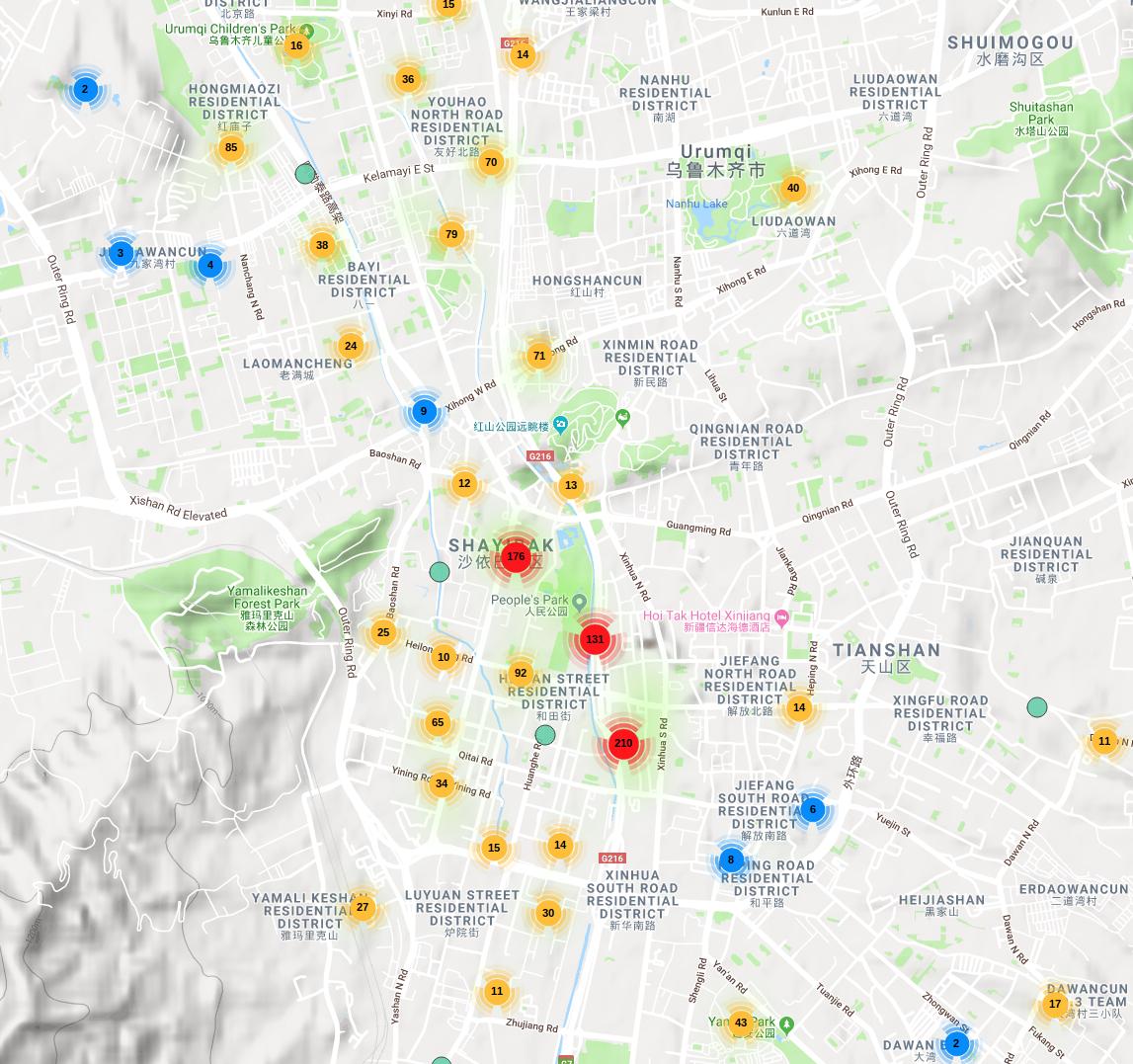
These are the trackers which are connected the SenseNets database. They make part of this artificial intelligence-based security network which uses face recognition, crowd analysis, and personal verification.
mapmakerapp.com/?map=5c66817e4…



mapmakerapp.com/?map=5c66817e4…
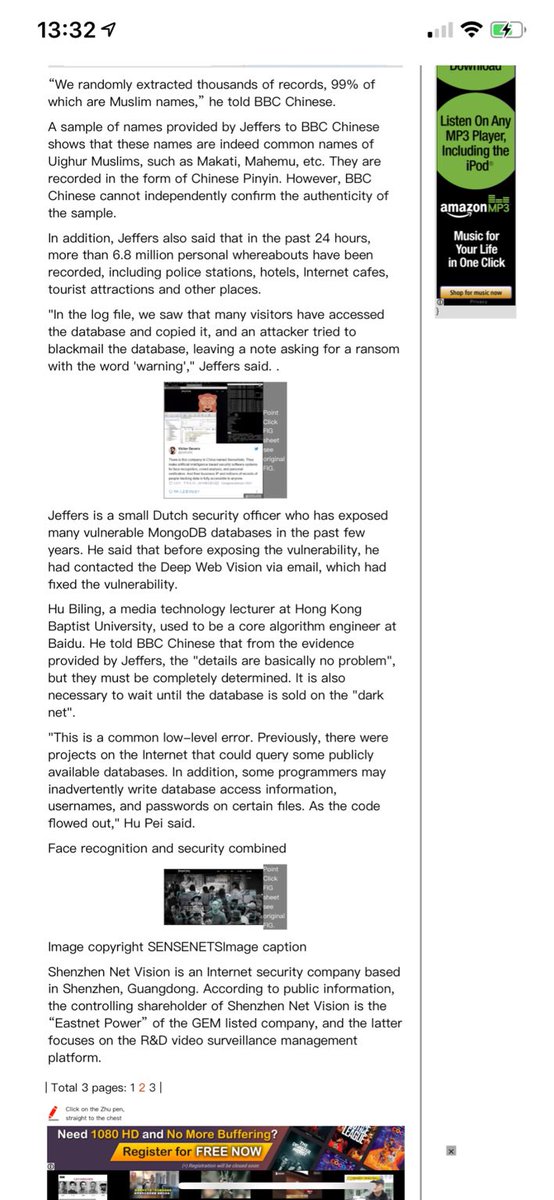
Jeffers got a little bit lost in translation here but does this guy really say: ”details are basically not a problem.”?
And no one is going to sell this database ”on the dark web” because it was given away for free for more than a half year.
popyard.com/cgi-mod/newspa…

And no one is going to sell this database ”on the dark web” because it was given away for free for more than a half year.
popyard.com/cgi-mod/newspa…
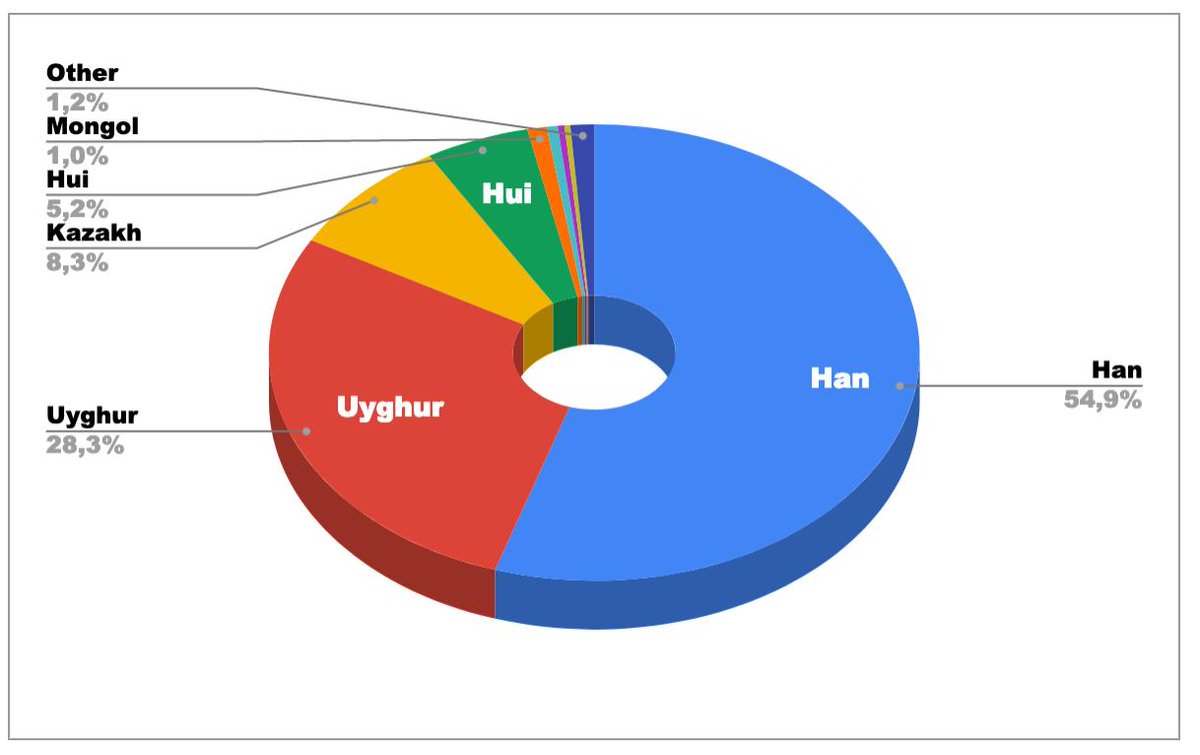
This is small overview of the nationalities in that database.
And this is the data to make of the graph: plot.ly/~0xDUDE/0

And this is the data to make of the graph: plot.ly/~0xDUDE/0
The age of the oldest person is 93. The youngest person with a valid ID number is a girl of the age of 1 year and 5 months. Both have 汉 nationality and no 维吾尔. The youngest person is 9 days old and has no ID number, no nationality, no address and was registered at this loc. 
The oldest woman with 维吾尔 nationality is 88 years old and was last seen by a tracker on 31-01-2019 at 17:57:44
The youngest woman with 维吾尔 nationality and without a valid ID number is a 22 days old infant and was last seen on 13-02-2019 at 10:21:19 on this location.
The youngest woman with 维吾尔 nationality and without a valid ID number is a 22 days old infant and was last seen on 13-02-2019 at 10:21:19 on this location.

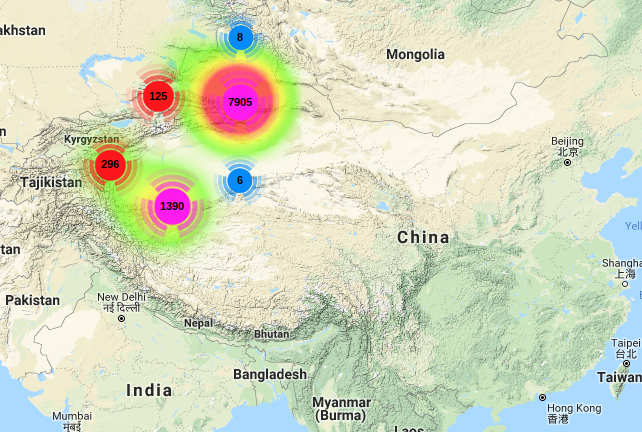
There are 301.214 维吾尔 women with an average age of 32 and
424.590 维吾尔 men with an average age of 30 being tracked.
424.590 维吾尔 men with an average age of 30 being tracked.
Between 2018 and 2019 about 2,280 people from 俄罗斯 🇷🇺 have visited over 1,113 unique locations in the Yunnan, Sichuan, Shandong, Guangdong, Guangxi, Jiangsu, Hebei, Hubei, Fujian and Liaoning province while being tracked. 
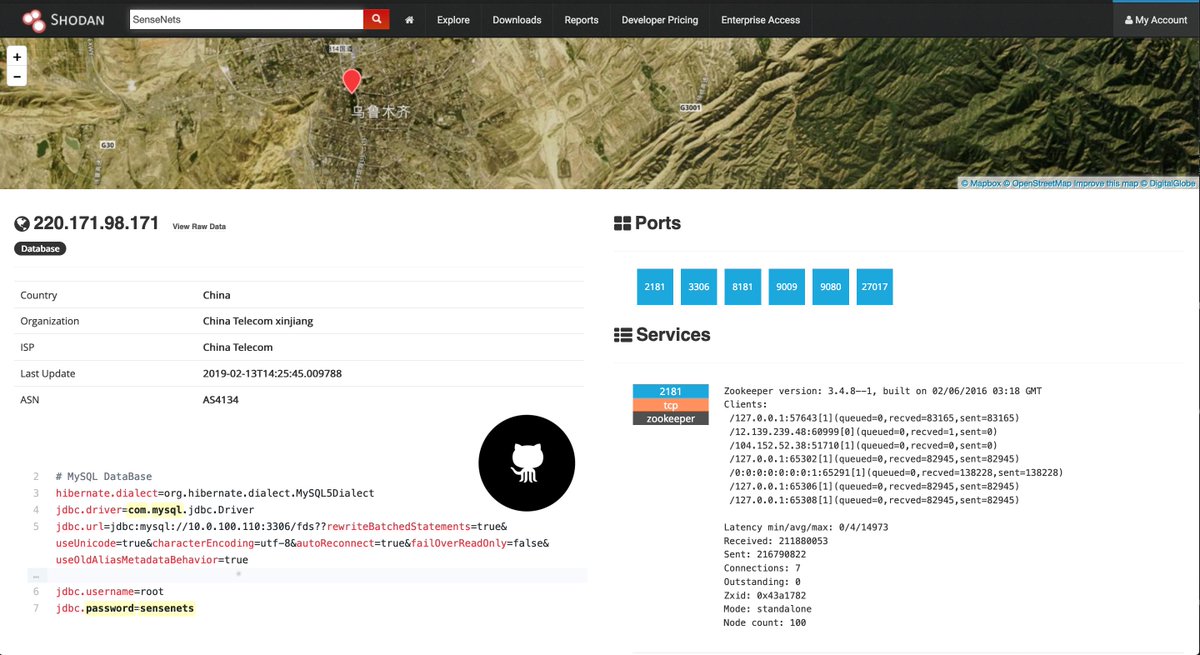
Around the same time all the database of SenseNets were exposed to the internet the developers starting pushing code to Github sharing their internal passwords, but also their emailaccounts & other credentials online services were shared readable to world on this famous platform. 
But even with that confidential information publicly exposed there is no technical knowledge needed to control these cameras. The instructions for these things are also on Github. And this why you should NEVER trust technology because the people behind IT can be ignorant idIOTs. 
It has been 22 days after our initial report about the SenseNets incident. I decided to start investigating the strategic & technical partners from Silicon Valley that contribute to "face recognition" part of this system. Within a few days, I'm going to share some new insights.
The company 微软 also known as @Microsoft has been a precious partner who has turned more than once a blind eye to the (technical)/(mal)practices of the engineers of SenseNets. From pirated versions of Windows servers to offering Azure Cognitive services for Face (recognition). 

And this is not the first time @Microsoft was called out not to sell @Azure cognitive services to provide a face surveillance product to governments.
"To take an ethical stand, and put children and families above profits”
hrw.org/news/2019/01/1…
"To take an ethical stand, and put children and families above profits”
hrw.org/news/2019/01/1…
After SenseNets became news the API key for cognitive services suddenly disappeared from @Github. But other sensitive materials were still leaked by the developers through their personal repos like e-mail, database, SSH and Gitlab credentials, where the lost API key was found.



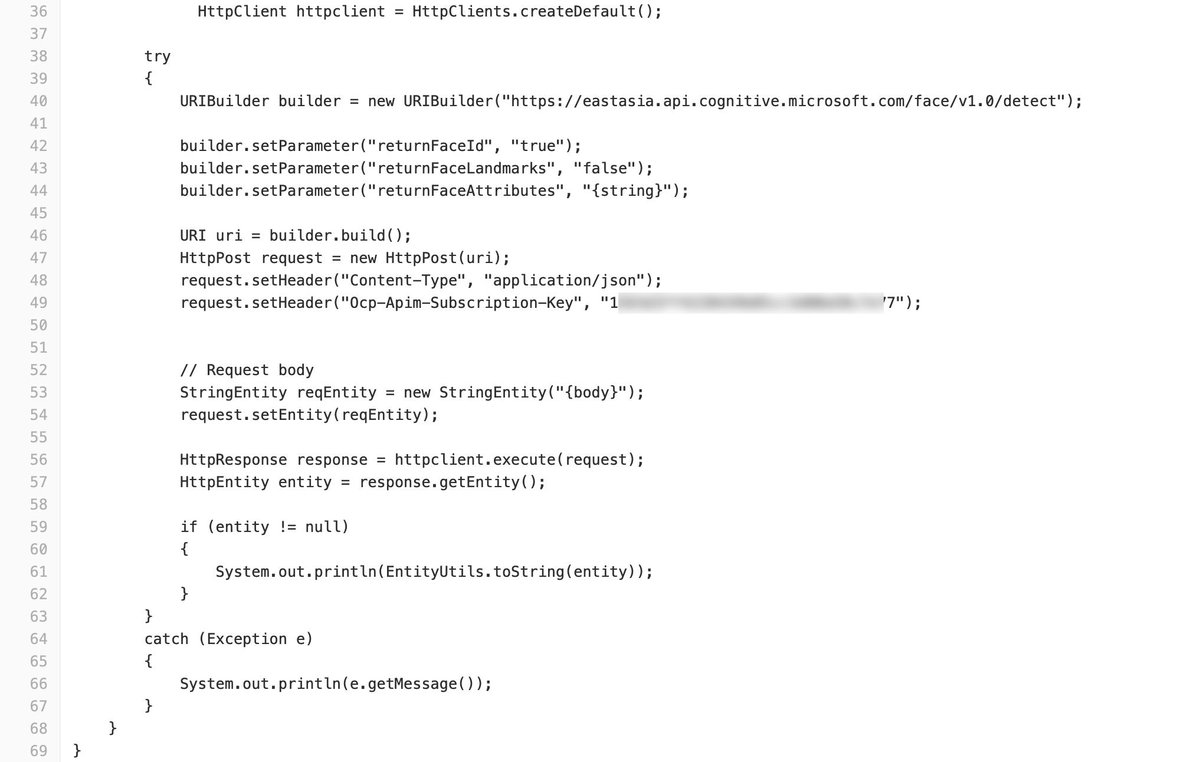
At this moment it is not clear if the @Microsoft @Azure Cognitive services are still being used. The developers of SenseNets did not learn much from the previous incident and keep pushing new code and credentials to @Github for their new "Face device management system". 🤦♂️🤷♂️



The SenseNets case shortly reviewed on an episode off @ChinaUncensored
You should watch the entire video but here the part with some interesting observations made by the host.
You should watch the entire video but here the part with some interesting observations made by the host.
"Protecting democratic freedoms and human rights" is a paragraph of the blog post titled "Facial recognition: It’s time for action" by @Microsoft President @BradSmi where he describes the risk of mass surveillance can encroach on democratic freedoms. 🤷♂️ blogs.microsoft.com/on-the-issues/…


Xinjiang Dispatch. How China Turned a City Into a Prison
A surveillance state reaches new heights.
By Chris Buckley (@ChuBailiang ), Paul Mozur (@paulmozur) and Austin Ramzy (@austinramz)
nyti.ms/2I3Rkr5

A surveillance state reaches new heights.
By Chris Buckley (@ChuBailiang ), Paul Mozur (@paulmozur) and Austin Ramzy (@austinramz)
nyti.ms/2I3Rkr5

Microsoft has been working with a Chinese military-run university on artificial intelligence research that could be used for surveillance and censorship. The government is using these technologies to build surveillance systems and to detain minorities.
irishtimes.com/business/techn…
irishtimes.com/business/techn…
Microsoft accused of complicity in human rights abuses after helping China develop ‘disturbing’ AI. >>
As long they are pushing their code and API keys to public open repositories we can at least keep track of what they are doing.
As long they are pushing their code and API keys to public open repositories we can at least keep track of what they are doing.
https://twitter.com/Independent/status/1116718178409885697
How Microsoft Helped Build China’s Nightmare Surveillance by @ChinaUncensored
Watch the entire episode here:
Watch the entire episode here:
A large publicly available facial recognition dataset with 10 million images of nearly 100,000 individuals known as "Face Model Zoo" was created and maintained by Microsoft is now offline. This is how it went down.
https://twitter.com/FinancialTimes/status/1136599894448332801
There are a lot of (large) data facial recognition datasets publicly available like fopr example CelebA on Kaggle which contains 202.599 face images of various celebrities / 10177 unique identities. 

SenseNets used the Duke MTMC dataset was used for "extensive experiments" on improving person re-identification across multiple surveillance cameras with important applications in suspect tracking for "research" and development of video tracking systems.
megapixels.cc/datasets/duke_…
megapixels.cc/datasets/duke_…
Inside China's 'thought transformation' camps by @TheJohnSudworth of the @BBCNews
The BBC has been given rare access to the vast system of highly secure facilities thought to be holding more than a million Muslims in China’s western region of Xinjiang.
The BBC has been given rare access to the vast system of highly secure facilities thought to be holding more than a million Muslims in China’s western region of Xinjiang.
Chinese ”education” camps in the northwest Xinjiang region of China.
In this video you see up to 600 prisoners (Uighur Muslim men) being moved — they’re shackled together, have shaved heads, are blindfolded and have their hands locked behind their backs.
news.com.au/world/asia/chi…
In this video you see up to 600 prisoners (Uighur Muslim men) being moved — they’re shackled together, have shaved heads, are blindfolded and have their hands locked behind their backs.
news.com.au/world/asia/chi…
"To hide mass detentions in Xinjiang, large numbers of detainees are being relocated from the region to other localities: the neighboring province of Gansu and more distant places, like Henan Province in central China."
bitterwinter.org/xinjiang-camp-…
bitterwinter.org/xinjiang-camp-…
Around these re-education camps, they use security systems which are set up specifically to recognize Uyghurs using facial recognition from unprotected live video feeds. These systems were open and accessible to the entire world.


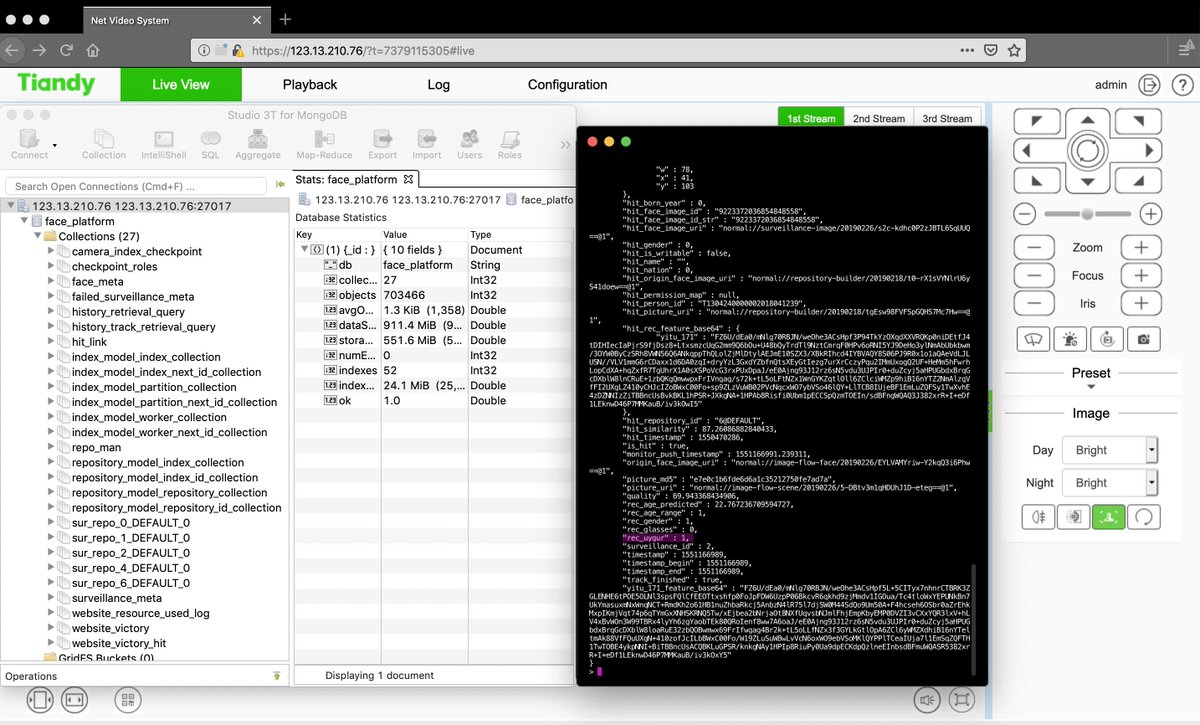
Another (never shared and) remarkable thing is that SenseNets was experimenting/doing something with network cameras which showed live views of (de)construction sites [locations unknown]. We never could find any connection besides the fact that the IPs were in the MySQL database. 

@github @Microsoft @gitlab This is the unmasked Ocp-Apim-Subscription-Key "1319e7ff63901002c1ff5b02e46b5a77". We never got it working when we found it, and it still does not work today. 

Yesterday Belnet (AS2611) was under a DDoS attack and downed the Belgium government's network and other govt and educational entities when the Belgium Parliament was supposed to hear the testimony of a survivor of China's “re-education” camps. 巧合?
https://twitter.com/Techmeme/status/1389656480677122049
@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh