
(Grumpy Old) Hacker. Co-founder @GDI_FDN. Co-founder @DIVDnl. Co-founder @csirt_global. Unfiltered via https://t.co/cpHG9orJvG
2 subscribers
How to get URL link on X (Twitter) App



 To be able to become human in the Parler, you need to get verified. Users can do this by scanning their U.S. drivers license or Passport within the app. I tried a few times with my Dutch Passport but this failed. Even Parlersupport couldn’t help. So I searched for another way.
To be able to become human in the Parler, you need to get verified. Users can do this by scanning their U.S. drivers license or Passport within the app. I tried a few times with my Dutch Passport but this failed. Even Parlersupport couldn’t help. So I searched for another way. 



 Peensees products are used for security applications and use existing face recognition technologies and CCTV cameras. This is a (mockup) dashboard of their open AI R&D environment. It looks like a "SenseNets disaster 2.0" in the making as they have no clue what they are doing. 🤦♂️
Peensees products are used for security applications and use existing face recognition technologies and CCTV cameras. This is a (mockup) dashboard of their open AI R&D environment. It looks like a "SenseNets disaster 2.0" in the making as they have no clue what they are doing. 🤦♂️
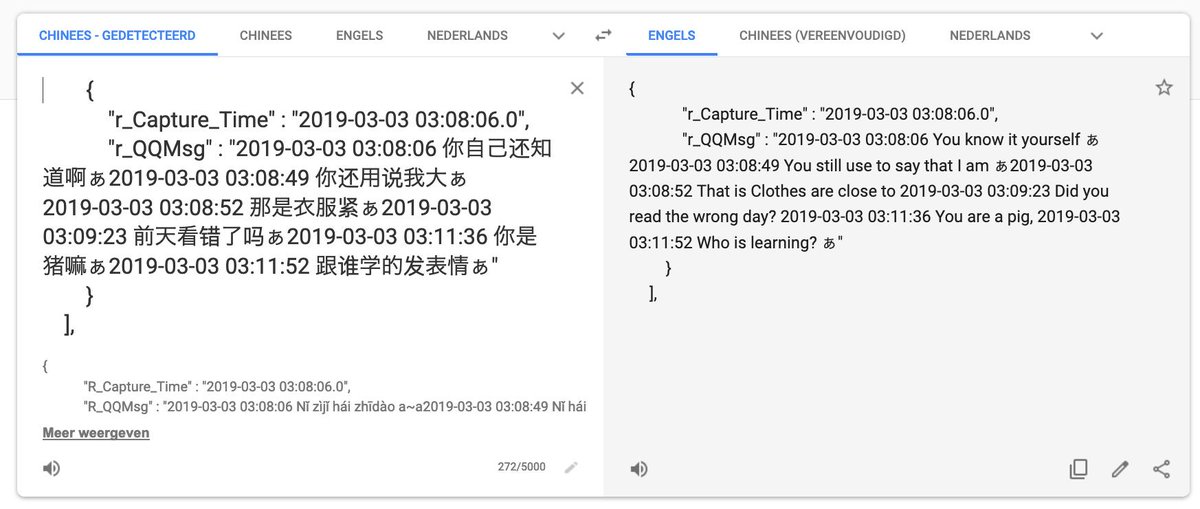
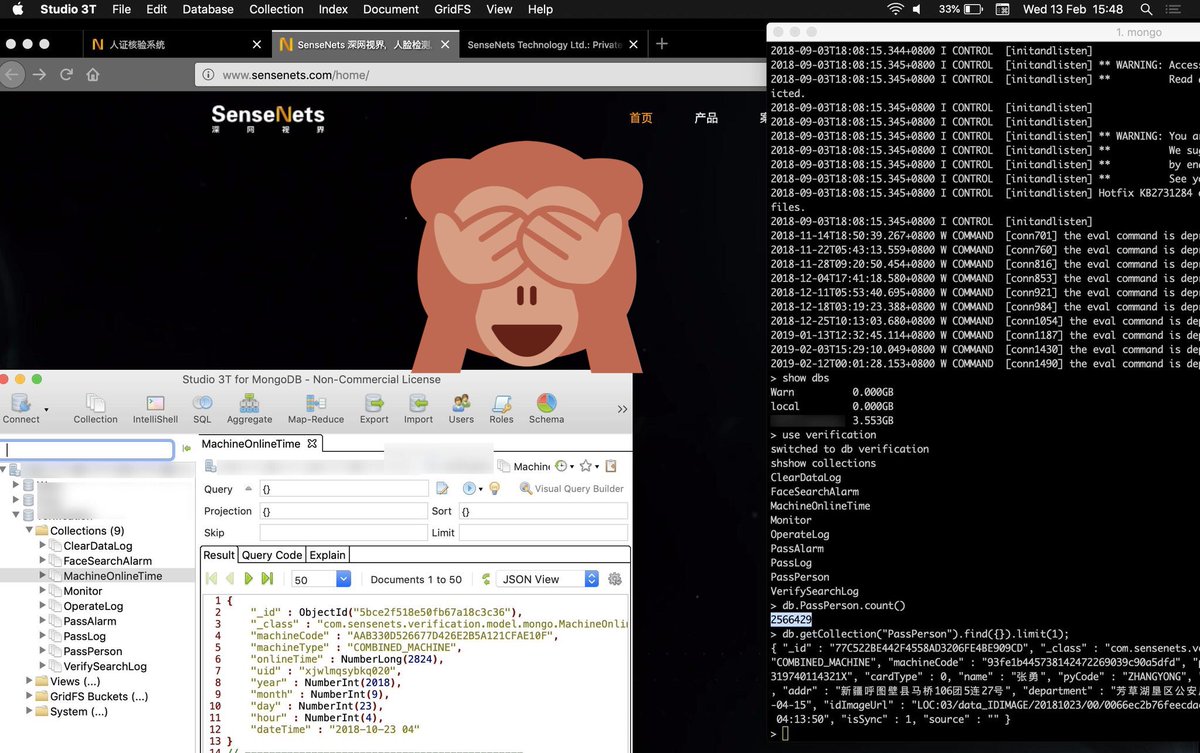
 This database contains over 2.565.724 records of people with personal information like ID card number (issue & expire date, sex, nation, address, birthday, passphoto, employer and which locations with trackers they have passed in the last 24 hours which is about 6.680.348 records
This database contains over 2.565.724 records of people with personal information like ID card number (issue & expire date, sex, nation, address, birthday, passphoto, employer and which locations with trackers they have passed in the last 24 hours which is about 6.680.348 records

https://twitter.com/0xDUDE/status/631520323574181889Until recently many 🇷🇺 companies were using MongoDB not securely.

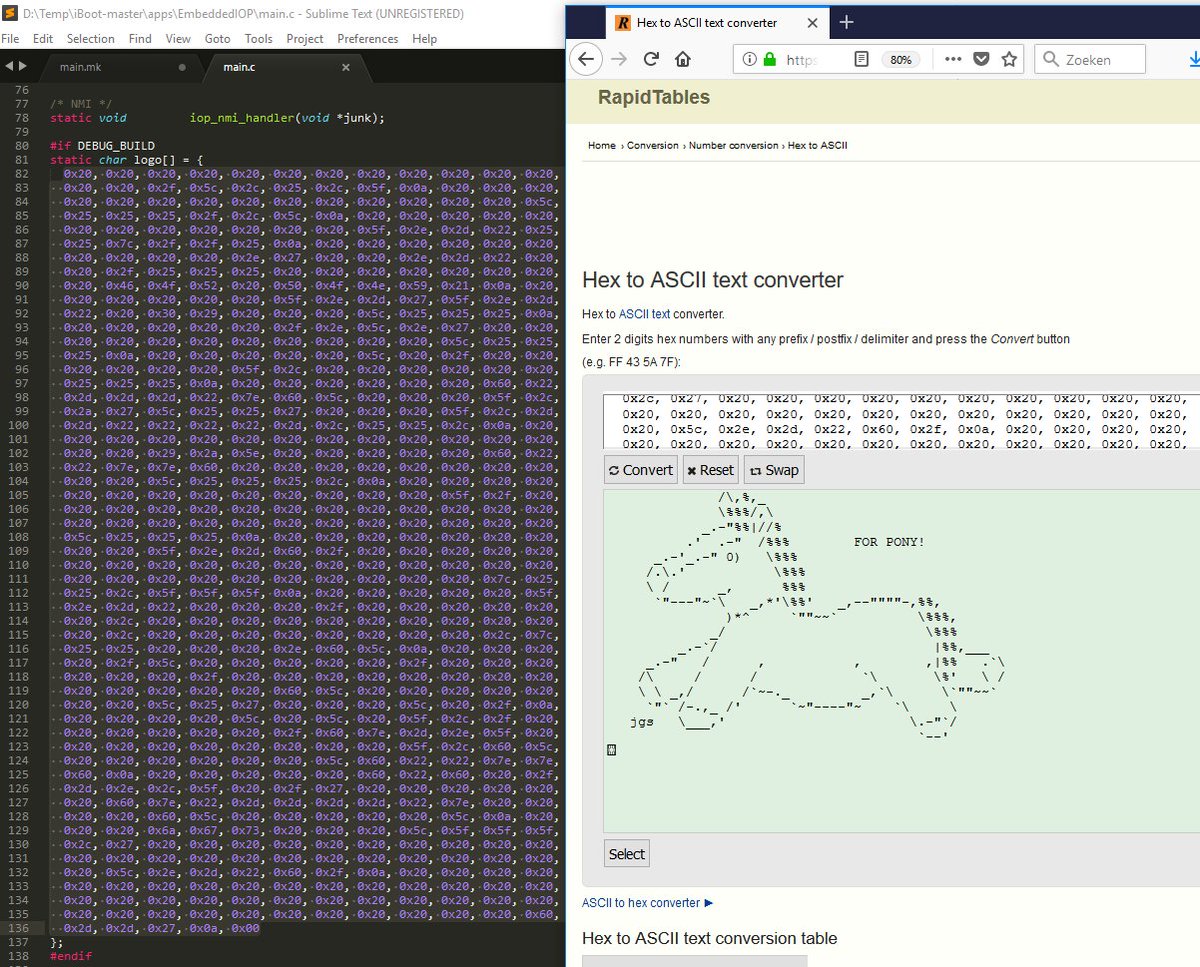 Oh I see that @Zeecka_ already found the pony :
Oh I see that @Zeecka_ already found the pony : :-D
External Tweet loading...
If nothing shows, it may have been deleted
by @Zeecka_ view original on Twitter