More on the info op from Russia that we've dubbed #SecondaryInfektion, for its resemblance to the Soviet-era AIDS libel.
Planting stories far away, then amplifying them with covert assets.
Full report here: docs.wixstatic.com/ugd/9d177c_3e5…
Planting stories far away, then amplifying them with covert assets.
Full report here: docs.wixstatic.com/ugd/9d177c_3e5…

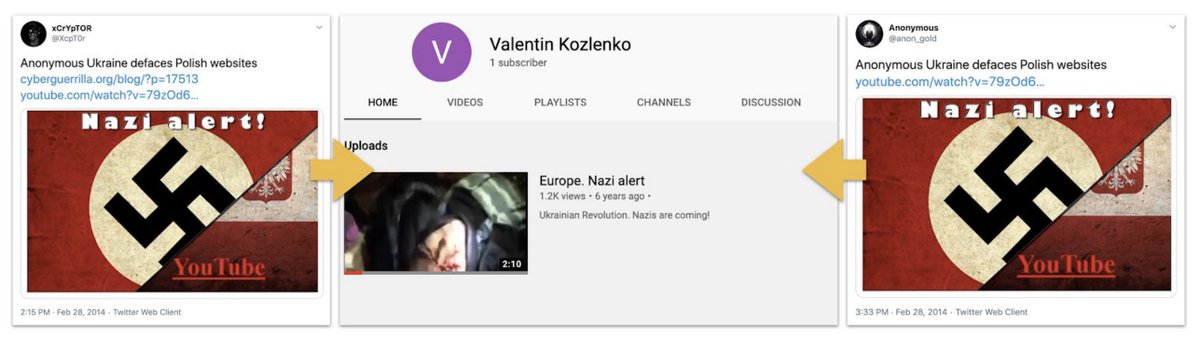
As far as we can tell, the operation started in Russian in early 2014, and focused on Ukraine.
A few of the Russian-language personas were repetitive posters.
Note the blue-face version of @navalny, too. He's a frequent target.
medium.com/dfrlab/russian…
A few of the Russian-language personas were repetitive posters.
Note the blue-face version of @navalny, too. He's a frequent target.
medium.com/dfrlab/russian…
The same persona posted the same story to multiple platforms. The Facebook account started in March 2015; an account with the same name and profile picture was on LiveJournal in early 2014. 

It tied in with operation assets in other languages too. That's especially interesting, because it allows us to trace the op's multi-language approach at least as far back as 2016.
Take this piece on NATO "bioterrorism," for example.
Take this piece on NATO "bioterrorism," for example.

The Russian version claimed to be a translation of an English-language original.
But the English-language original's wording was... interesting.
"The ensuing events remind the thriller from the 90s"??
But the English-language original's wording was... interesting.
"The ensuing events remind the thriller from the 90s"??

The English version started with the words "As is known."
Any English journalist who started a piece like that would face the editor's wrath. But as "как известно", it's acceptable Russian reporting. (These from RIA Novosti.)
This reads like a translation from Russian.
Any English journalist who started a piece like that would face the editor's wrath. But as "как известно", it's acceptable Russian reporting. (These from RIA Novosti.)
This reads like a translation from Russian.

And where else did the English-language version show up?
Medium, that's where. Posted by a burner account that only ever published the one story. That's the fingerprint of this operation.
Note the date: September 2016. This operation has been running a long time.
Medium, that's where. Posted by a burner account that only ever published the one story. That's the fingerprint of this operation.
Note the date: September 2016. This operation has been running a long time.

An interesting angle: a few of this persona's later posts amplified "leaks" from a Telegram account called "SBU Mole" (Кріт СБУ). (SBU = Ukrainian intel.)
The "leaks" went from the Mole, via burner accounts, to the op's Facebook account.
Worth looking more at the Mole.
The "leaks" went from the Mole, via burner accounts, to the op's Facebook account.
Worth looking more at the Mole.

Not all the "blue man"'s posts were about Ukraine. This one was on Azerbaijan, but used the same method: an apparently forged letter, burner accounts, multiple language, stolen profile pic (this time of Felicia Chin). 

A few times, the operation used the same account multiple times in English too. This was the most prolific we've found so far: "Dama Mroczna," the Dark Lady, mostly posting on BeforeItsNews.
medium.com/dfrlab/russian…
medium.com/dfrlab/russian…
Here's one of its stories: a claim that Ukraine had blacklisted @realDonaldTrump for his comments on Crimea. Based on a screenshot, and therefore easily photoshopped.
Attempt to divide Ukraine and the U.S.?
Attempt to divide Ukraine and the U.S.?

Further evidence that this was a) part of the operation, and b) fake: the story was also posted on Medium by a single-use burner account with a stolen profile picture.
Recognise the pattern?
Recognise the pattern?

This was another piece: a conspiracy story on Ukraine.
The use of language is just... well, read for yourselves.
The use of language is just... well, read for yourselves.

What's fascinating here is that the BeforeItsNews version sourced itself to a story on @BuzzFeed. The URL is now broken.
Still trying to establish whether the link was fake, or the op managed to plant a false story on BF.
Cc @JaneLytv @CraigSilverman @kevincollier
Still trying to establish whether the link was fake, or the op managed to plant a false story on BF.
Cc @JaneLytv @CraigSilverman @kevincollier

This was another Dark Lady classic. Ostensibly written by an American journalist, reporting on South Korean "assassination plots" against Kim Jong Un, but oh my, the wording. 

And yet again, the same story showed up on Medium, posted by a burner account.
"Military Observer," this time. Note the profile pic, apparently lifted from the @ItalyMFA website: esteri.it/mae/en/politic…
"Military Observer," this time. Note the profile pic, apparently lifted from the @ItalyMFA website: esteri.it/mae/en/politic…

There was one other story the "Dark Lady" shared, too: a claim that the U.S. was planning a false-flag chemical weapons attack on Venezuela to justify intervention, back in late February.
medium.com/dfrlab/russian…
medium.com/dfrlab/russian…
This one started off in Spanish. Posted to globedia.com, embedding what looks like a letter from @ljsacks73 of @USAID Colombia to @jguaido.
Hell of an intercept... or would be, if it were real.
Hell of an intercept... or would be, if it were real.

But it was posted by a single-use burner account, again.
Created on Feb 26. Posted on Feb 26. Only one post.
The same old pattern.
Created on Feb 26. Posted on Feb 26. Only one post.
The same old pattern.

And the use of language is worthy of a James Bond villain.
"Current situation is jeopardizing our joint action directed against the regime of usurper Maduro"???
Seriously?
"Current situation is jeopardizing our joint action directed against the regime of usurper Maduro"???
Seriously?
The operation really pushed this one. Half a dozen different Spanish sites and subreddits. In German on meinbezirk.at and ask1.org.
Single-use burner accounts, as ever.
"Joined: March 1. Contributions: 1. Last seen: March 1."
Single-use burner accounts, as ever.
"Joined: March 1. Contributions: 1. Last seen: March 1."

A separate burner account posted an English version of the story to @Indybay, which the operation used to plant many of its fakes.
Well, I say "English", but...
("Informational war" is a phrase also used by Russian MoD translators, incidentally.)
Well, I say "English", but...
("Informational war" is a phrase also used by Russian MoD translators, incidentally.)

It's all about spreading division. Discrediting the US in the eyes of others. Dividing Western countries. But in most cases, the secrecy was so high that they buried their own stories.
One case was different. Posts on that later.
One case was different. Posts on that later.
• • •
Missing some Tweet in this thread? You can try to
force a refresh