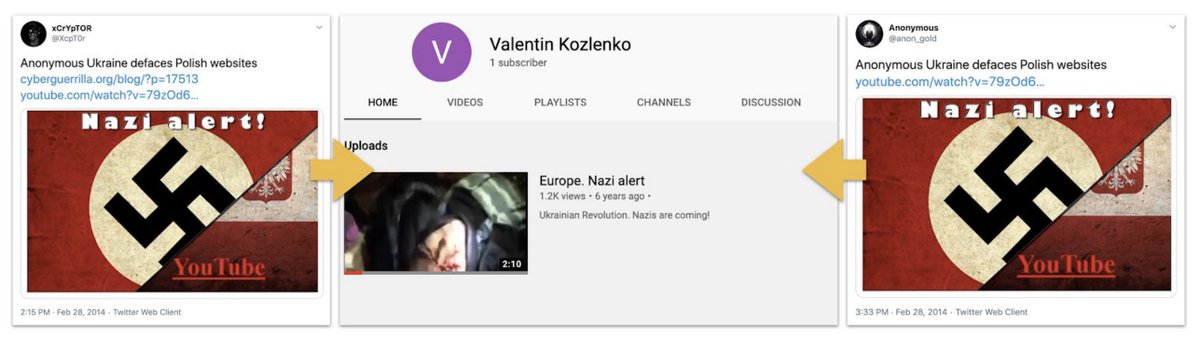
One of the odd things about operation #SecondaryInfektion was how little it was on Twitter - even less than on Facebook.
So far, we've found one account, that the FB account pointed to. Ostensibly a Ukrainian girl in Germany.
So far, we've found one account, that the FB account pointed to. Ostensibly a Ukrainian girl in Germany.

The operation used this account (now suspended) to ping stories to German politicians and commentators, especially AfD. 
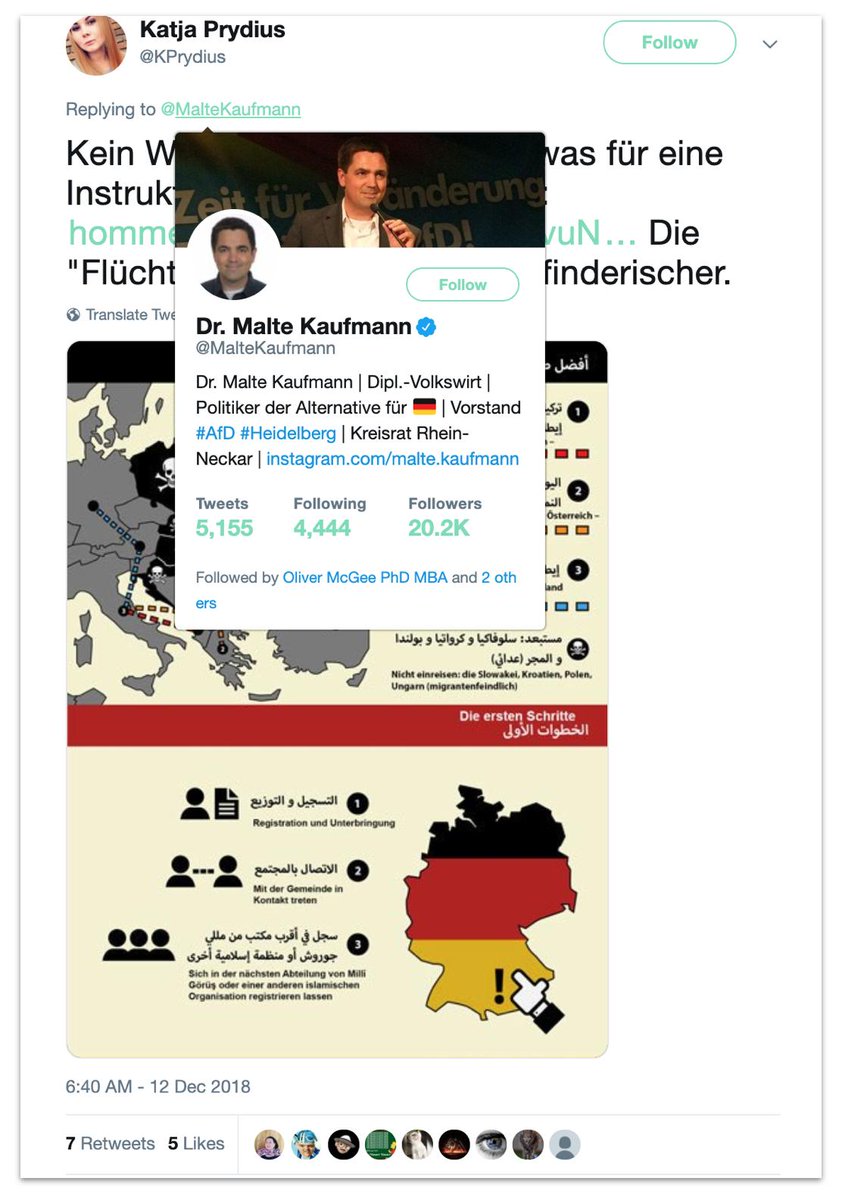
The nastiest story it posted, and the only one that got any traction, was a claim based on a forged "guide to Muslim immigrants" in Germany.
As ever, posted by a single-use burner account.
As ever, posted by a single-use burner account.

As so often, other single-use burner accounts posted it to other platforms in German and English.
The tone was openly vicious and Muslim-baiting.
The tone was openly vicious and Muslim-baiting.

This time, it got picked up on the far right in Germany. This is one of the operation's Facebook accounts, but it's sharing an article that traces back, via Wordpress, to Journalistenwatch, not to the operation itself (as far as we know). 

The thing is, unlike the operation's own production, the Journalistenwatch variant actually got some traction.
That's an anti-Islam and anti-immigrant fake, probably created, and certainly promoted, by a Russian information operation, penetrating the German far right.
That's an anti-Islam and anti-immigrant fake, probably created, and certainly promoted, by a Russian information operation, penetrating the German far right.

That's not the only time the operation tried to reach the far right, either.
There's one story we've found so far about the @Europarl_EN elections. It followed the classic pattern.
medium.com/dfrlab/russian…
There's one story we've found so far about the @Europarl_EN elections. It followed the classic pattern.
medium.com/dfrlab/russian…
We found this one via a French-language account that, unusually, posted two stories. (Bad OPSEC there.)
The second one accused mainstream politicians of a "war against the right."
It was based on a forged letter attributed to @AnnaMariaCB.
The second one accused mainstream politicians of a "war against the right."
It was based on a forged letter attributed to @AnnaMariaCB.

We language-checked the letter (in Swedish) with experts. Definitely non-native (though probably not machine translated).
One of the things about this op is how many languages its operators were +almost+ competent in. That's a major human investment.
One of the things about this op is how many languages its operators were +almost+ competent in. That's a major human investment.
This time, the language versions came in French, German and English almost simultaneously.
Note meinbezirk.at again. The op used it repeatedly.
Note meinbezirk.at again. The op used it repeatedly.

The English version was posted on Medium by a single-use burner account. Surprised?
It started, "It became known earlier that," which is just not English-language journalism, but works in Russian as “Ранее стало известно, что..."
(These from TASS and Sputnik.)
It started, "It became known earlier that," which is just not English-language journalism, but works in Russian as “Ранее стало известно, что..."
(These from TASS and Sputnik.)

These may be my favourite quotes of the whole operation.
Those extreme rights are pretty damn scarily, no?
Oh, and "informational war," again.
Those extreme rights are pretty damn scarily, no?
Oh, and "informational war," again.

It looks like the operation's security habits were slipping by this stage, because they posted the story with an account on meinbezirk.at that posted one other thing.
That was a claim of an "information war" against Germany by the US and Poland. Typically divisive.
That was a claim of an "information war" against Germany by the US and Poland. Typically divisive.

The operation's Twitter account then pinged the story directly to 16 different people, mostly AfD politicians.
"People are actively discussing this online. Can you comment?"
Direct targeting.
"People are actively discussing this online. Can you comment?"
Direct targeting.

As so often, though, the article didn't get traction. At least some of that looks like it was because of user wariness.
That, at least, is a positive sign, as far as it goes.
That, at least, is a positive sign, as far as it goes.
But the thing is, all this op needs is to succeed once; the Muslim-baiting story arguably did just that.
Using so many burner accounts means that it's hard to get impact, but hard to disrupt the whole operation, because they already burned their own assets.
Expect more.
Using so many burner accounts means that it's hard to get impact, but hard to disrupt the whole operation, because they already burned their own assets.
Expect more.
• • •
Missing some Tweet in this thread? You can try to
force a refresh