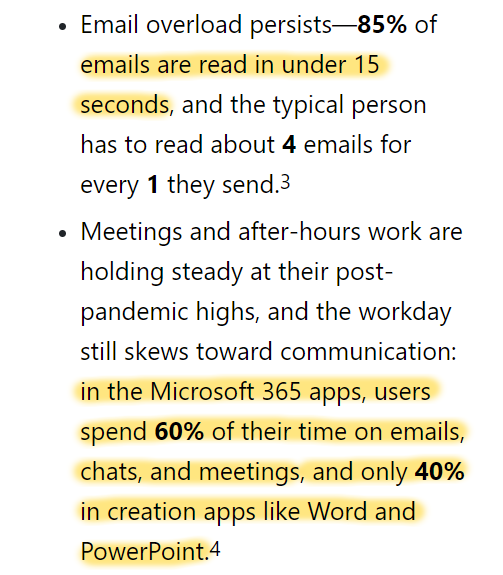
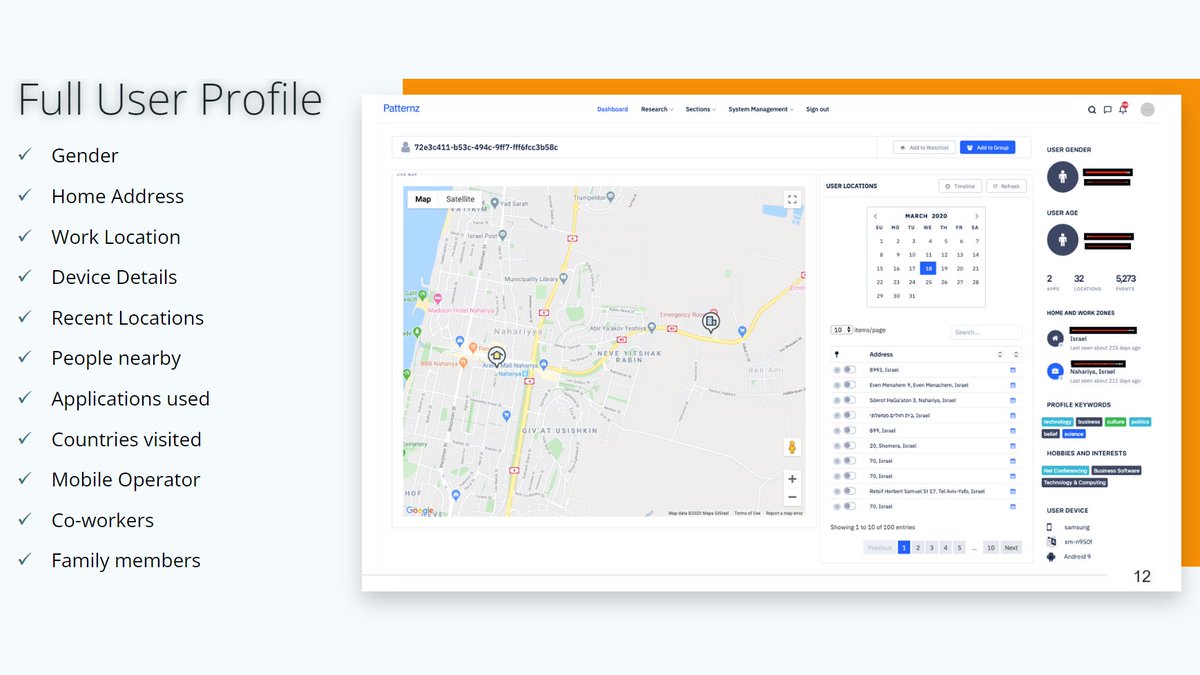
New report on browser extensions selling *highly* sensitive personal data on millions of users. EU authorities must immediately start to investigate the browser extension data industry.
Report:
securitywithsam.com/2019/07/datasp…
Articles:
arstechnica.com/information-te…
washingtonpost.com/technology/201…
Report:
securitywithsam.com/2019/07/datasp…
Articles:
arstechnica.com/information-te…
washingtonpost.com/technology/201…
In 2018, I summarized what we know about browser extensions that secretly access, share or sell highly sensitive personal information.
Thread:
Thread:
https://twitter.com/WolfieChristl/status/1058334596734091265
I wonder, did any EU data protection authority start a single investigation into browser extensions (and the companies that gather personal data from browser extensions) in recent years?
• • •
Missing some Tweet in this thread? You can try to
force a refresh