#GuardrailsOfTheGalaxy
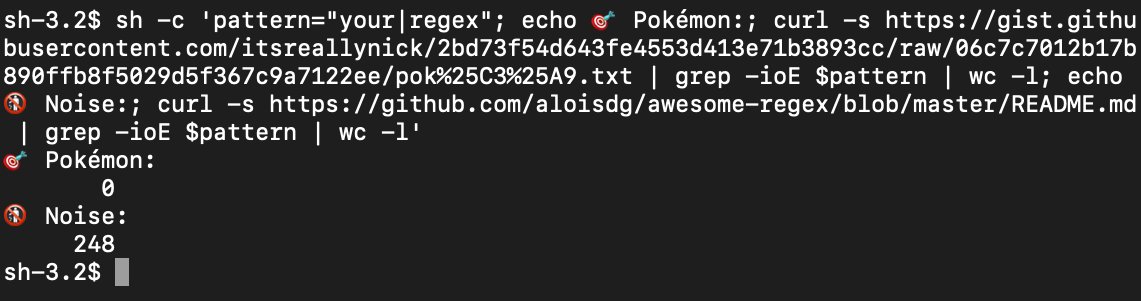
Here is a fun sample uploaded to VT yesterday - combining some adversary guardrails¹ with light obfuscation²
VT (17/58): virustotal.com/gui/file/bc85e…
¹ active directory domain check
² string splits & integer Unicode code point encoding
@MITREattack #T1480



Here is a fun sample uploaded to VT yesterday - combining some adversary guardrails¹ with light obfuscation²
VT (17/58): virustotal.com/gui/file/bc85e…
¹ active directory domain check
² string splits & integer Unicode code point encoding
@MITREattack #T1480




@MITREattack @virustotal @HackingDave I'll try to share more of these techniques/styles on Twitter - with the plan to pull together a cohesive #GuardrailsOfTheGalaxy blog exploring execution guardrails in-the-wild from a defender's perspective.
Here was another previously shared:
Here was another previously shared:
https://twitter.com/ItsReallyNick/status/1130995831451062272
@stvemillertime @MITREattack @virustotal @HackingDave Another one, uploaded 15 minutes ago from same 🇪🇸 submitter. Looks like a few changes to the loader.
VT (16/57): virustotal.com/gui/file/53558…
I understand that this is likely a red team exercise.
VT (16/57): virustotal.com/gui/file/53558…
I understand that this is likely a red team exercise.
• • •
Missing some Tweet in this thread? You can try to
force a refresh