
Tech Director / Threat Intelligence at Microsoft. Previously, Director of Incident Response & Intel Research at Mandiant. Former Chief Technical Analyst at CISA
How to get URL link on X (Twitter) App


 The value of our (+@cglyer) real-time attacker technique collaboration with absolute beasts in the industry @doughsec 😶🌫️, @penninajx + @srunnels 💻 cannot be overstated bringing together puzzle pieces for the RE wizards on each side
The value of our (+@cglyer) real-time attacker technique collaboration with absolute beasts in the industry @doughsec 😶🌫️, @penninajx + @srunnels 💻 cannot be overstated bringing together puzzle pieces for the RE wizards on each side https://twitter.com/itsreallynick/status/1339964643045945347

https://twitter.com/ItsReallyNick/status/1394483035156983808) [2/3]




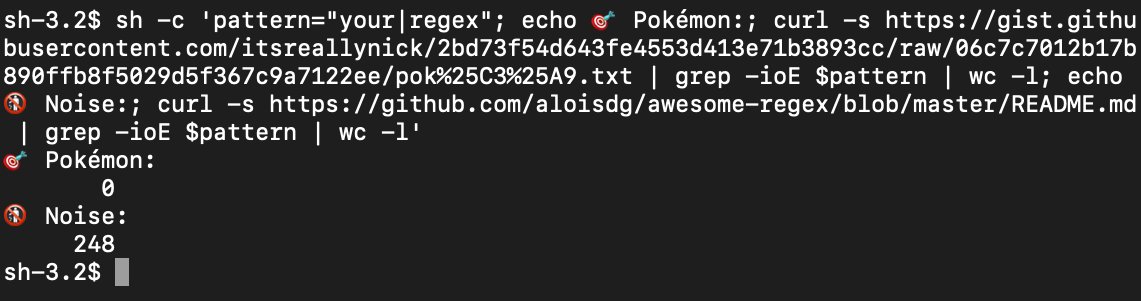

 That last one was much harder to capture than these Iranian TTP Pokémon.
That last one was much harder to capture than these Iranian TTP Pokémon. 


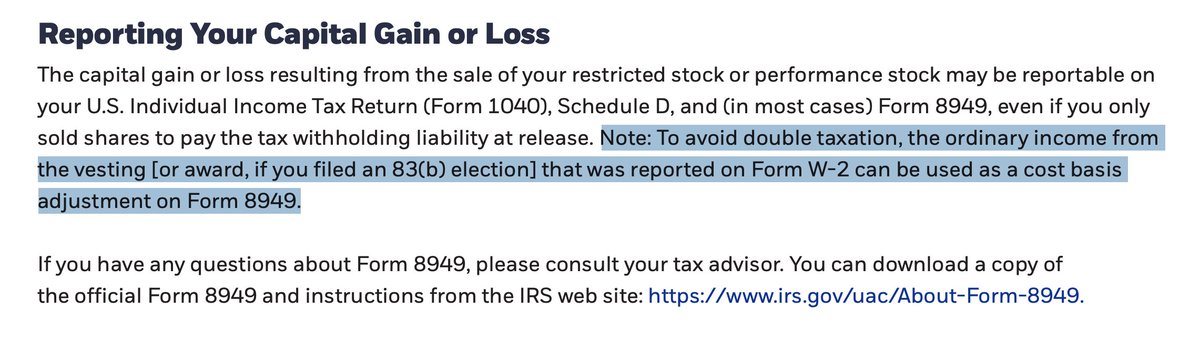


https://twitter.com/ItsReallyNick/status/1176336528970276864?s=20







 👆🏼Is this “malware” & why? <replies welcome>
👆🏼Is this “malware” & why? <replies welcome>


 @Cneelis @_RastaMouse Uploaded 4 hours ago. (🆕)
@Cneelis @_RastaMouse Uploaded 4 hours ago. (🆕)




 "salesforce.docx"
"salesforce.docx"https://twitter.com/cglyer/status/1222255759687372801

 You should process these at scale and - outside of training - it's not a good use of time to step through them manually.
You should process these at scale and - outside of training - it's not a good use of time to step through them manually.
https://twitter.com/FireEye/status/1218246639367798785@sj94356 @QW5kcmV3 Wait, did @YouTube remove the #StateOfTheHack episode? 👉feye.io/soth 👀

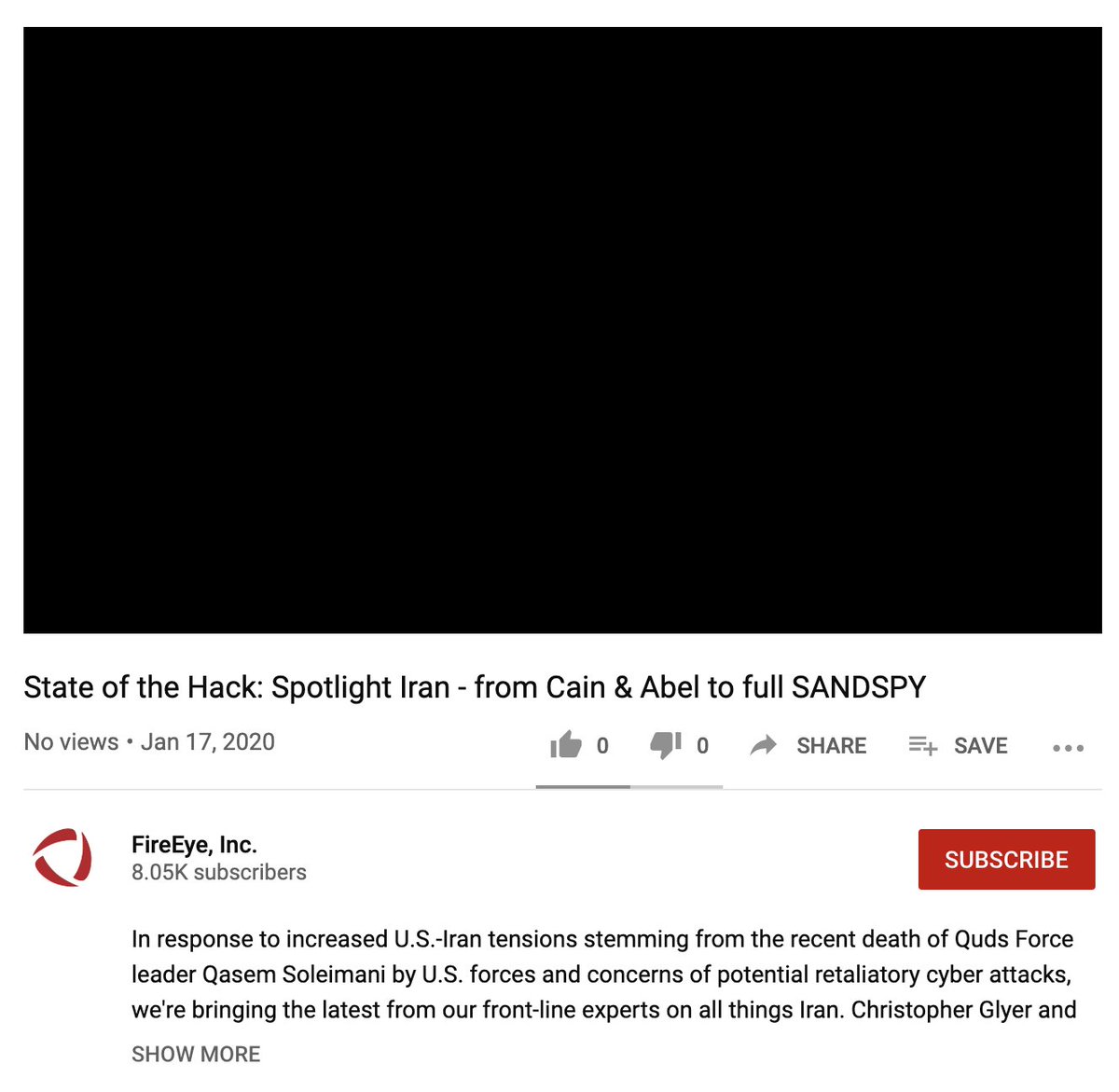




 @_bromiley @snort @mpgn_x64 @TrustedSec @4real_br4nd4n @BakedSec @sans_isc @FireEye @Mandiant Blog contains a sampling of CVE-2019-19781 post-compromise activity: fireeye.com/blog/products-…
@_bromiley @snort @mpgn_x64 @TrustedSec @4real_br4nd4n @BakedSec @sans_isc @FireEye @Mandiant Blog contains a sampling of CVE-2019-19781 post-compromise activity: fireeye.com/blog/products-…

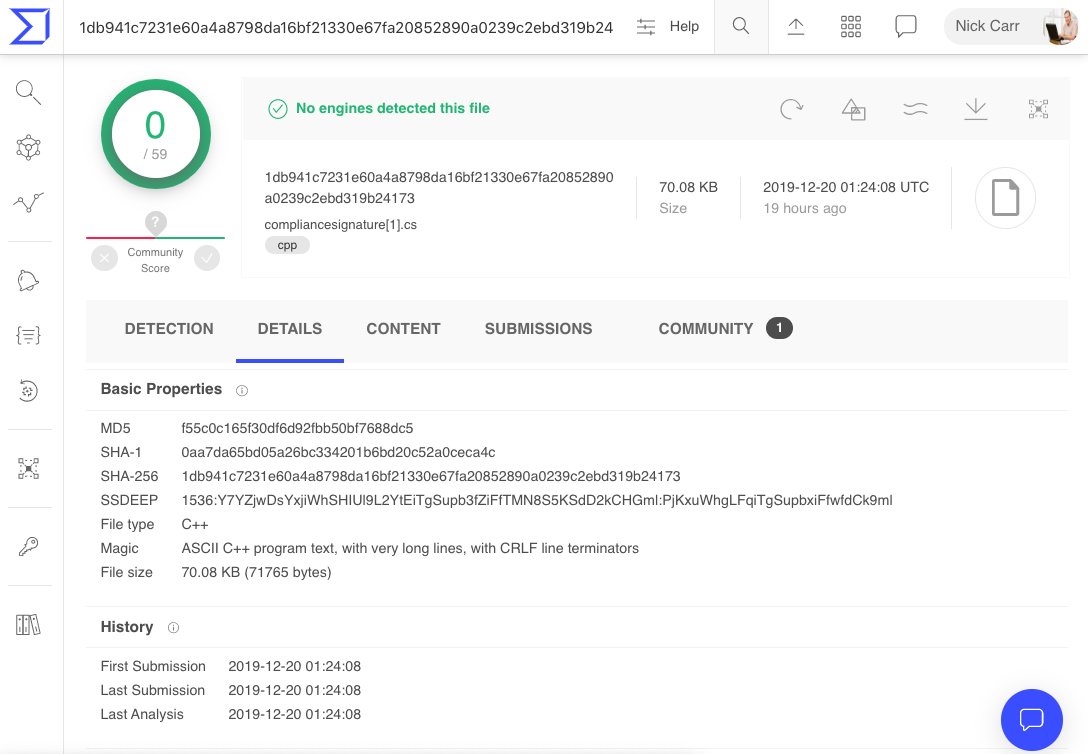 Identify suspicious #InstallUtil code execution payloads with a syntax-based #Yara rule (gist.github.com/itsreallynick/…) from this thread (
Identify suspicious #InstallUtil code execution payloads with a syntax-based #Yara rule (gist.github.com/itsreallynick/…) from this thread (https://twitter.com/ItsReallyNick/status/1196848668097339392?s=20) on a *pretty damn similar* sample 🧐



 Here is the #UNC1194 first stage (recon) payload stored in an attacker-controlled @Azure storage blob:
Here is the #UNC1194 first stage (recon) payload stored in an attacker-controlled @Azure storage blob: https://twitter.com/itsreallynick/status/1199209513137688576
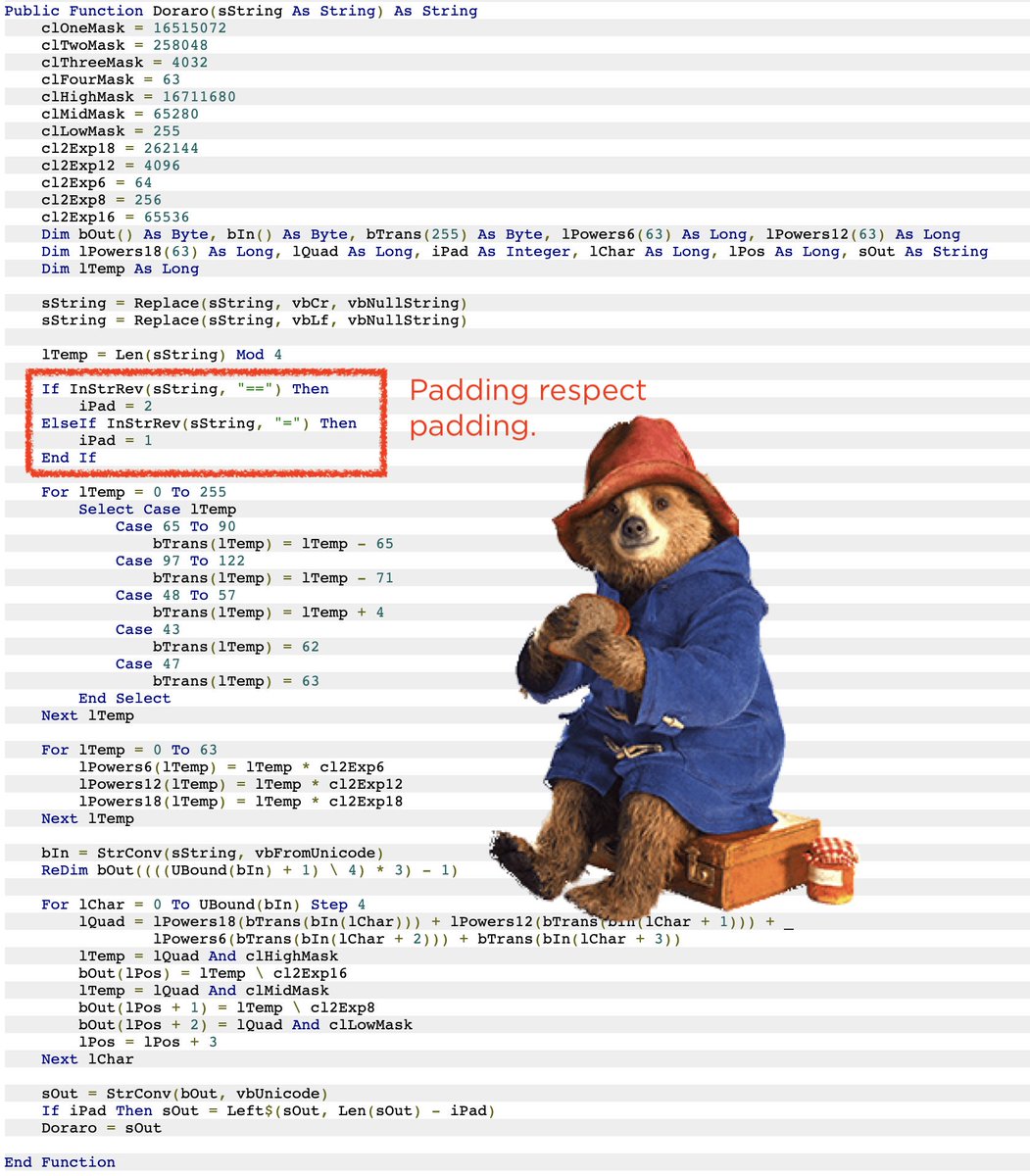

 It's reasonable to expect an aspiring detection engineer to explain what's going on here.
It's reasonable to expect an aspiring detection engineer to explain what's going on here.
