🤙💰 Mahalo FIN7: fireeye.com/blog/threat-re…
• On several on-going investigations we saw #FIN7 trying to retool 🏄🏼
• Used DLL search order hijacking of a legit POS management utility with a signed backdoor (0 detections on VirusTotal)
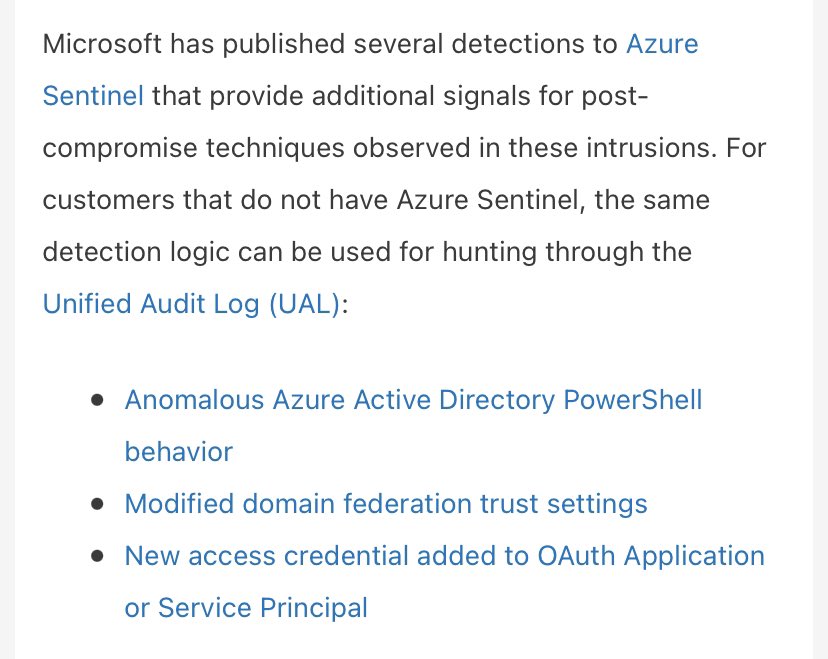
• Hunting for #BOOSTWRITE and #RDFSNIFFER 💳
• On several on-going investigations we saw #FIN7 trying to retool 🏄🏼
• Used DLL search order hijacking of a legit POS management utility with a signed backdoor (0 detections on VirusTotal)
• Hunting for #BOOSTWRITE and #RDFSNIFFER 💳
.@josh__yoder & I stayed up much of the night to get this blog out.
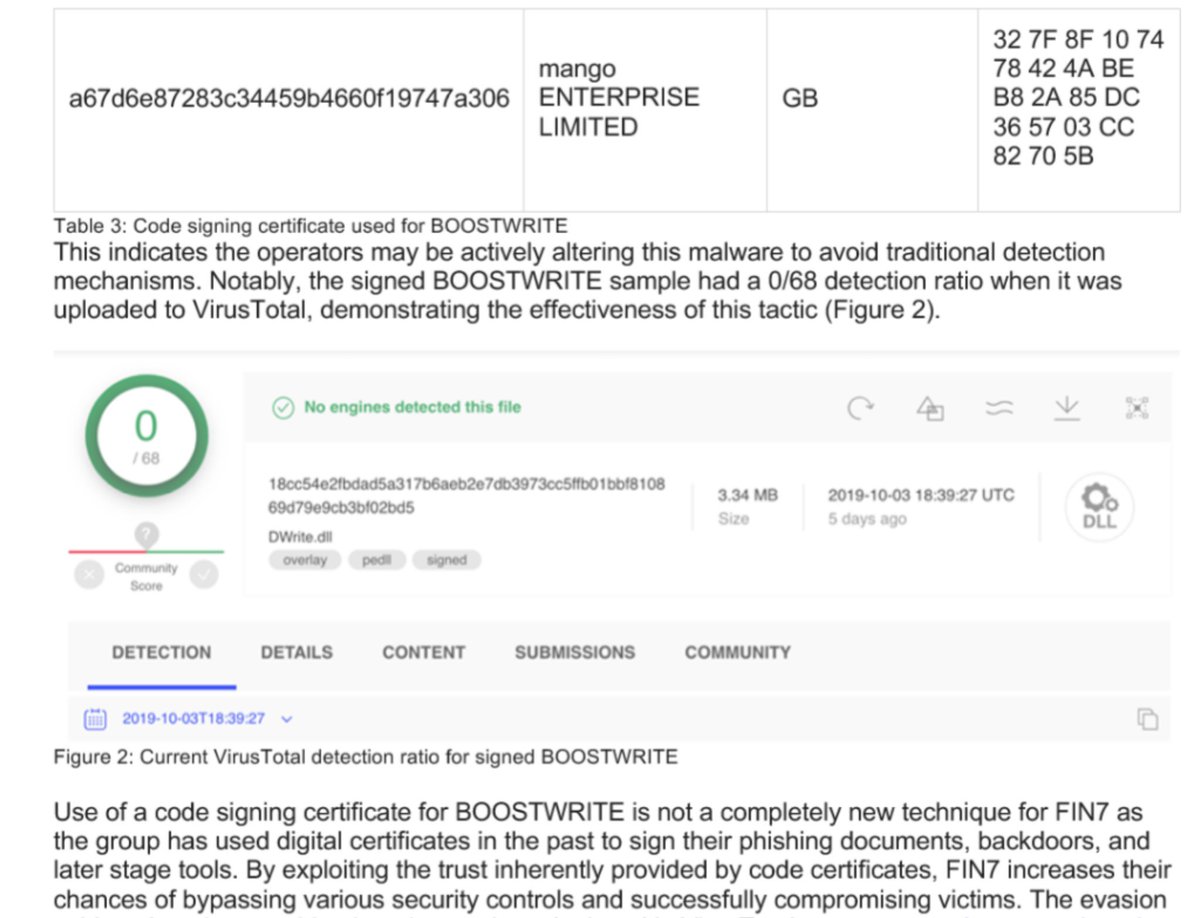
The signed #BOOSTWRITE sample is still undetected by static VT scanners: virustotal.com/gui/file/18cc5…
We were fair on why that is and how that doesn't fully represent detection posture.
Then we provided hunting rules.
The signed #BOOSTWRITE sample is still undetected by static VT scanners: virustotal.com/gui/file/18cc5…
We were fair on why that is and how that doesn't fully represent detection posture.
Then we provided hunting rules.

#FIN7's code signing certificate is purportedly from Mango Enterprise Limited in the UK.
Prob not theirs - based on the street address, I suspect there's more car theft than certificate theft 😜: maps.app.goo.gl/MbznDeJPHJr4n5…
We analyze & discuss how to find the certificate anomalies!



Prob not theirs - based on the street address, I suspect there's more car theft than certificate theft 😜: maps.app.goo.gl/MbznDeJPHJr4n5…
We analyze & discuss how to find the certificate anomalies!




Btw, here's an awesome Yara certificate anomaly signature concept from @wxs in a thread discussing them, including @NCCGroupInfosec's rule from @edeca that's featured in today's #FIN7 blog:
Oh and Google/@virustotal crew was great to work with on the bug!
https://twitter.com/wxs/status/1070716787501731840?s=19
Oh and Google/@virustotal crew was great to work with on the bug!
We tried to share a few examples of #AdvancedPractices 🦅 leveraging certificate, PDB path, and export features for discovery.
I snuck some content in those rules 🌶️ but they are inspired by @stvemillertime, who I've decided has a PhD in hunting
↘️fireeye.com/blog/threat-re…


I snuck some content in those rules 🌶️ but they are inspired by @stvemillertime, who I've decided has a PhD in hunting
↘️fireeye.com/blog/threat-re…



In a perfect confluence *cough* of events, @BarryV talked about #FIN7's historical code signing of binaries, scripts, and even documents @ #FireEyeSummit:
Note the operator environment details we extract for FIN7, like their LNKs
CC @keydet89, @silascutler
https://twitter.com/ItsReallyNick/status/1182350918622334976?s=19
Note the operator environment details we extract for FIN7, like their LNKs
CC @keydet89, @silascutler
Hey so, we accidentally included a #Turla REDUCTOR export DLL name in one of the blog's Yara rules. 🤦♂️ Whoops!
Turla ≠ #FIN7
🧢 h/t @OleVilladsen for the catch!
I updated the rule & noted the change in Figure 7: fireeye.com/blog/threat-re…
Turla ≠ #FIN7
🧢 h/t @OleVilladsen for the catch!
I updated the rule & noted the change in Figure 7: fireeye.com/blog/threat-re…

• • •
Missing some Tweet in this thread? You can try to
force a refresh