#InstallUtil payloads are still very popular for code execution and app whitelisting bypass.
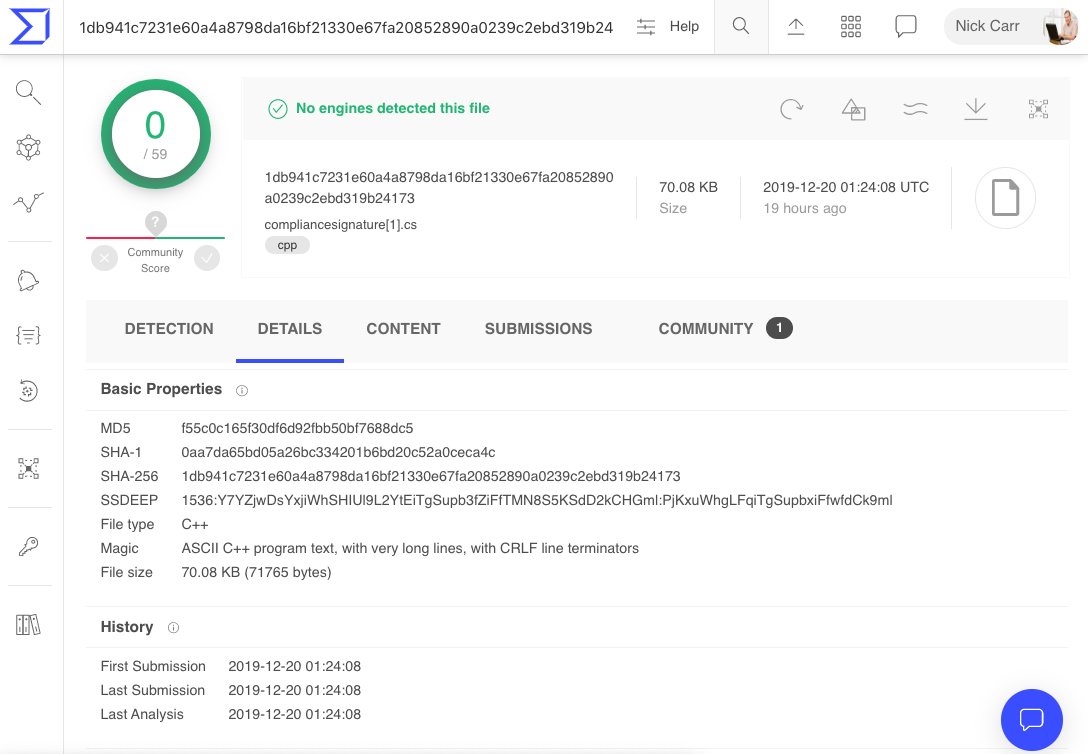
Here's a fresh sample with a #GRUNT payload: "compliancesignature.cs"
MD5: f55c0c165f30df6d92fbb50bf7688dc5
virustotal.com/gui/file/1db94…
0/59 static detections.
So I'll share some rules!
👇👇

Here's a fresh sample with a #GRUNT payload: "compliancesignature.cs"
MD5: f55c0c165f30df6d92fbb50bf7688dc5
virustotal.com/gui/file/1db94…
0/59 static detections.
So I'll share some rules!
👇👇

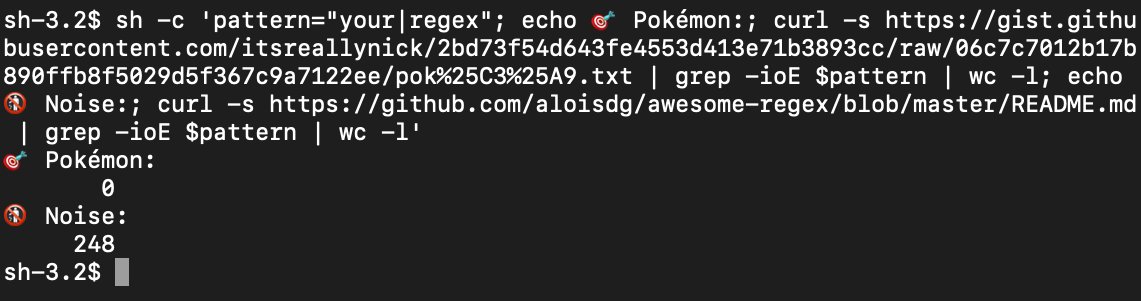
Identify suspicious #InstallUtil code execution payloads with a syntax-based #Yara rule (gist.github.com/itsreallynick/…) from this thread (
Also look closely at both samples' embedded PE information (Original/InternalName) 😉
https://twitter.com/ItsReallyNick/status/1196848668097339392?s=20) on a *pretty damn similar* sample 🧐
Also look closely at both samples' embedded PE information (Original/InternalName) 😉

👋 hello @rapid7 red team btw
Or as I know you, #UNC1769.
You all do some really cool stuff. Keep it up! See you on the field!
Please try not to get as mad at me for putting some VT payloads on Twitter (like, no need to upload a bunch of aggressively-named files this time 😅)
Or as I know you, #UNC1769.
You all do some really cool stuff. Keep it up! See you on the field!
Please try not to get as mad at me for putting some VT payloads on Twitter (like, no need to upload a bunch of aggressively-named files this time 😅)
In a confusing exchange about this #UNC1769 attribution tweet, I offered more context:
https://twitter.com/itsreallynick/status/1208393746464825349?s=21
• • •
Missing some Tweet in this thread? You can try to
force a refresh