LIVE FROM COLUMBIA, IT'S #REALWORLDCRYPTO
First up is the TLS session 🔒
First talk is Johanna Amann on measuring TLS 1.3 deployment in the wild with active and passive methods
#realworldcrypto
#realworldcrypto
The notary method is able to collect a lot of feature usage data but not all, on over 1 billion sessions since 2012 (😱)
#realworldcrypto
#realworldcrypto
"The moment our scanner was able to speak a newer version (Draft) of TLS 1.3, we picked up servers supporting it." Fantastic!
#realworldcrypto
#realworldcrypto
What drives support being relatively high in the beginning, such as in the Alexa top 1million? Possibly being operated by professionals, or because the site is being served/TLS terminated by another service who does stay on top of TLS versions.
#realworldcrypto
#realworldcrypto
Cheers to Cloudflare for their aggressive adoption of multiple draft versions of TLS 1.3!
#realworldcrypto
#realworldcrypto

Don't have data for Google but they also joined late, but once they joined a lot of servers supported it all together (makes sense considering Google front end / terminator deployment strategies).
#realworldcrypto
#realworldcrypto
Digital Ocean support spiked when the RFC was accepted, possibly due to Linux defaulting to the new version of TLS and well-patched droplets picking it up automatically. 💪
#realworldcrypto
#realworldcrypto
"Clients would be using the new ClientOffered extension to advertise really ancient versions of TLS" 😆
#realworldcrypto
#realworldcrypto
Some of these are private versions for companies like Google and Facebook that controlled their own clients and servers until the final draft was adopted.
#realworldcrypto
#realworldcrypto
ANDROID SUPPORT 🙏
Came with the release of Android Q, not including apps that shipped with their own TLS stack and negotiated their own connections earlier.
#realworldcrypto
Came with the release of Android Q, not including apps that shipped with their own TLS stack and negotiated their own connections earlier.
#realworldcrypto
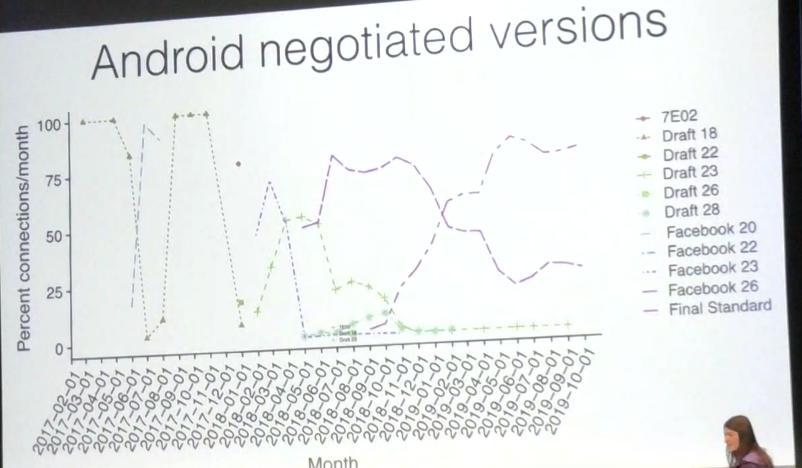
So much faster adoption than previous versions due to investment by several large companies 🎉
#realworldcrypto
#realworldcrypto
NEXT UP: The 9 Lives of Bleichenbacher's CAT: New Cache ATtacks on TLS Implementations
#realworldcrypto
#realworldcrypto
Why do we care if we can break 6% of TLS connections? Because it's not actually those 6% that are vulnerable, downgrade attacks affect more than that.
#realworldcrypto
#realworldcrypto
Only 6% of connections use RSA key exchange, so instead, force a downgrade on servers that _support_ RSA kex but aren't overtly advertising it, using a MITM
#realworldcrypto
#realworldcrypto
Need to keep the session alive during the padding attack, which the user might notice. Instead, use JS in the background to repeatedly reopen connections in the background, instead of reloading the full webpage which the user may notice.
#realworldcrypto
#realworldcrypto
Multiple sessions over multiple servers, looks similar to solving the hidden number problem, which can be attacked via the closest vector problem in a lattice
#realworldcrypto
#realworldcrypto

Paper includes layers of recommended mitigations , but if you really have to use RSA, separate your certificates.
But maybe just… please don't use RSA.
#realworldcrypto
But maybe just… please don't use RSA.
#realworldcrypto
Smart contracts need to be online to respond in a timely manner to things happening in the world.
#realworldcrypto
#realworldcrypto
DECO facilitates privacy-preserving proofs about TLS data to oracles and can be used for these smart contracts
#realworldcrypto
#realworldcrypto
Results in a handshake circuit with AND complexity of ~770k, runs in ~1.40seconds on wired network. Plenty fast for DECO.
#realworldcrypto
#realworldcrypto
So, if this is a proof based on the TLS connection of the data provider, what happens when the data provider gets social engineered or forgets to patch their database backend?
#realworldcrypto
#realworldcrypto
Q: In the MPC it's broken into two parts, what prevents a malicious input in the second part?
A: This will be caught later on in the protocol in the proof stage this will be caught, the two parties commit to their shares beforehand
#realworldcrypto
A: This will be caught later on in the protocol in the proof stage this will be caught, the two parties commit to their shares beforehand
#realworldcrypto
Short break ☕
Next up is the first symmetric crypto session, starting with Attacks only get better: The case of OCB2 by Tetsu Iwata
#realworldcrypto
#realworldcrypto
Nonce changes for every* encryption operation
*except when it doesn't , like when you ask the user to provide a nonce
#REALWORLDCRYPTO
*except when it doesn't , like when you ask the user to provide a nonce
#REALWORLDCRYPTO

GCM, CCM are NIST-certified
IETF ones include GCM, ChaCha20-Poly1305
CAESAR includes 6 more
Some more in the ongoing NIST lightweight crypto competition
#realworldcrypto
IETF ones include GCM, ChaCha20-Poly1305
CAESAR includes 6 more
Some more in the ongoing NIST lightweight crypto competition
#realworldcrypto
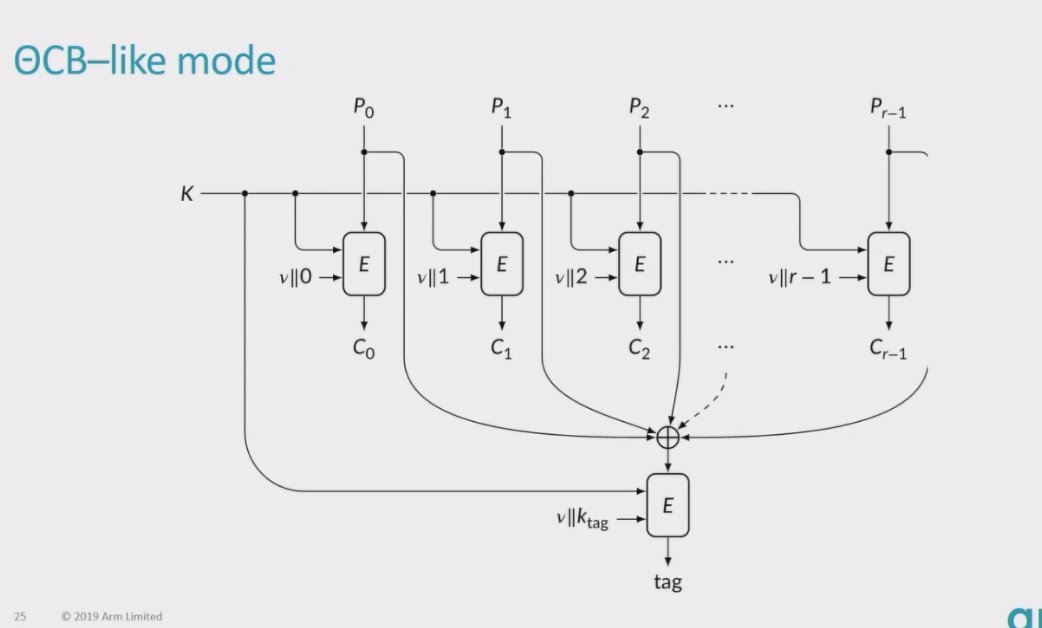
OCB includes 3 versions, nonce-based AE with AD with strong features, including proof of security
#realworldcrypto
#realworldcrypto

> SJCL affected
Free corgi pix to someone who collects metrics on real world usage of the SJCL in the wild. 🐕
#realworldcrypto
Free corgi pix to someone who collects metrics on real world usage of the SJCL in the wild. 🐕
#realworldcrypto
If we encrypt the same message twice, the nonce will* be different and the ciphertext will be different.
* CAVEAT EMPTOR
#realworldcrypto
* CAVEAT EMPTOR
#realworldcrypto
Simplest attack is a minimal forgery (existential forgery), adversary must know content of the message, it might not be that important but it's still not generated by the original sender.
#realworldcrypto
#realworldcrypto

Universal forgery: for any nonce and message (possibly chosen by the adversary), can compute ciphertext and tag that will be accepted as legit
#realworldcrypto
#realworldcrypto
So if we have these attacks, what went wrong with OCB2's proof of security?
It is a complex proof so
#realworldcrypto
It is a complex proof so
#realworldcrypto
Lesson: prove all the statements AND carefully check that they fit together
A good lesson for security in general
#realworldcrypto
A good lesson for security in general
#realworldcrypto
A distinguishing attack was published in 2018, "I saw this paper and wrote my attack in two days and submitted to ePrint" 😆
#realworldcrypto
#realworldcrypto
After the first chink in the armour, everything happened very quickly. "Attacks only get better", very quickly in this case 😬
#realworldcrypto
#realworldcrypto
"OCB2 is broken. Should not be used in any applications."
Attacks not applicable to OCB1 or OCB3. The general structure of OCB is sound.
Even the most promising scheme can fail; active third-party verification of security proofs is important.
#realworldcrypto
Attacks not applicable to OCB1 or OCB3. The general structure of OCB is sound.
Even the most promising scheme can fail; active third-party verification of security proofs is important.
#realworldcrypto
Part you can prove (blue), part you have to rely on an upper probabilistic bound (red)
#REALWORLDCRYPTO
#REALWORLDCRYPTO

Q: Compared to chacha20?
A: Don't have comparison figures, but for hardware implementations we think it is more performant than chacha
#realworldcrypto
A: Don't have comparison figures, but for hardware implementations we think it is more performant than chacha
#realworldcrypto
"I submitted this to the ACM and it was rejected for quite some time." NEVERTHELESS.
#realworldcrypto
#realworldcrypto
"I had to wait until [Diffie and Hellman's paper] was published and then it seemed more acceptable." 😉
#realworldcrypto
#realworldcrypto
"Sometimes there is one reviewer on the committee who does not understand the ideas in your paper."
*audience snickers about reviewer #2*
#realworldcrypto
*audience snickers about reviewer #2*
#realworldcrypto
"Things that are resistant to quantum computers are a Good Idea™️… oh and I introduced some quantum-resistant hash-based signatures" INDEED
#realworldcrypto
#realworldcrypto
Demonstrating real collision attacks to drive deprecation of MD5 and now SHA-1
(ICYMI SHA-1 is hella broken now, don't use it)
#realworldcrypto
(ICYMI SHA-1 is hella broken now, don't use it)
#realworldcrypto
Lunch time!
"There's been a shift in focus in the attack on strong encryption from terrorism to child sexual abusive imagery/materials" - @granick
#realworldcrypto
#realworldcrypto
Facebook says "the device issue is separate from [WhatsApp|Messenger|Insta]", aka trying to divert attention from E2E services and focus on breaking/forcing decryption of the plaintext on the ends (your phones).
#realworldcrypto
#realworldcrypto
"Technology has assured government access to more information about us than has even been available before, even if some of it is now being encrypted." Yes!
#realworldcrypto
#realworldcrypto
So if we assume an E2E world, how do you fight abuse online?
We have to be careful about trading away compromises that we'll be sorry about later on.
#realworldcrypto
We have to be careful about trading away compromises that we'll be sorry about later on.
#realworldcrypto
Backdoors are bad, but I think law enforcement hacking is _also_ really bad (incentivizes vuln hoarding, etc)
#realworldcrypto
#realworldcrypto
What about metadata? If the government relies on metadata to pursue abuse, there is a disincentive to protect privacy and fix metadata leaks from their perspective.
#realworldcrypto
#realworldcrypto
Q: Corporate rights to how their systems are being used (like email privacy for their employees)?
A: Usually terms of service are offered
#RealWorldCrypto
A: Usually terms of service are offered
#RealWorldCrypto
Q: How about homomorphic encryption?
A: This has never come up, the debate is not at this level of sophistication
#RealWorldCrypto
A: This has never come up, the debate is not at this level of sophistication
#RealWorldCrypto
Q: How much of this is a result of the current political climate?
A: I don't think this is a problem of this admin, it's come up in each of the previous admins since the late 80s… Be prepared for the long run.
#realworldcrypto
A: I don't think this is a problem of this admin, it's come up in each of the previous admins since the late 80s… Be prepared for the long run.
#realworldcrypto
Q: How can we listen to people who are victims of abuse online w/o compromising general privacy and security?
A: There are people who are hurt w/ & w/o strong encryption; can we learn from social graph analysis or metadata to ID perps or abuse acts privately.
#realworldcrypto
A: There are people who are hurt w/ & w/o strong encryption; can we learn from social graph analysis or metadata to ID perps or abuse acts privately.
#realworldcrypto
Next up, E-Voting session! Starting with Weaknesses in the Moscow internet voting system Pierrick Gaudry on Weaknesses in the Moscow internet voting system
#realworldcrypto
#realworldcrypto
The security here is additive not multiplicative, so it's only as hard as solving the 3 elgamal's individually. 🙃
#realworldcrypto
#realworldcrypto
Why are all the p's less than 256 bits? Probably because they wanted to shove this into Ethereum smart contracts which is capped at 256 bit integers.
#realworldcrypto
#realworldcrypto

Solving discrete log mod p of 256 bits? Using Number Field Sieve, took _less than 10 minutes_ with less than 1GB of space
Magma took 24 hours with 130 GB
SageMath didn't finish in 4 days :P
#realworldcrypto
Magma took 24 hours with 130 GB
SageMath didn't finish in 4 days :P
#realworldcrypto
Original took generators from the full Z so they probably also leaking bits with small subgroup attacks
#realworldcrypto
#realworldcrypto
🤦♀️
especially in e-voting, 1bit can be the entire value of the plain text (candidate A or candidate B)
#realworldcrypto
especially in e-voting, 1bit can be the entire value of the plain text (candidate A or candidate B)
#realworldcrypto

"The whole protocol is messed up!" 😭🗳️
No privacy, no coercion resistance, no vote buying prevention, only a little bit of verifiability.
#realworldcrypto
No privacy, no coercion resistance, no vote buying prevention, only a little bit of verifiability.
#realworldcrypto
Q: Is there a good open source e-voting system anywhere? Why is internet voting not ready?
A: If you don't care about coercion resistance, there is one in Geneva that has not been deployed but is good. If you want coercion resistance this is very difficult
#realworldcrypto
A: If you don't care about coercion resistance, there is one in Geneva that has not been deployed but is good. If you want coercion resistance this is very difficult
#realworldcrypto
Next up, Knights and Knaves Run Elections by Sarah Jamie Lewis, Olivier Pereira, Vanessa Teague
#realworldcrypto
#realworldcrypto
Surprise! It was in use in an ongoing australian election! But the election commission claimed they were unaffected. 🤔🤔🤔
#realworldcrypto
#realworldcrypto
Quick break!
Next up is the hardware session, starting with "Everybody be cool, this is a robbery!" from Jean-Baptiste Bédrune 🕵️♂️
#realworldcrypto
#realworldcrypto
Definitely used in PKI, bacnking, DNSSEC (@tqbf ), cloud encryption/decryption, and cryptocurrency stuff now I bet
#realworldcrypto
#realworldcrypto
Only a few vendors exist, no public prices, large range of models per vendor, of the numbers that are public, ~10K to 30K USD
#realworldcrypto
#realworldcrypto
FIPS!
Level 1 is just software requirements, levels 2 3 and 4 have physical requirements (TIL!)
#realworldcrypto
Level 1 is just software requirements, levels 2 3 and 4 have physical requirements (TIL!)
#realworldcrypto
Our beloved PKCS #11 /s
Few exposed functions (~70) but > 300 standard mechanisms & proprietary mechanisms.
#realworldcrypto
Few exposed functions (~70) but > 300 standard mechanisms & proprietary mechanisms.
#realworldcrypto
Threats:
- unauth'd users gain access to private objects
- attacker extracts keys that shouldn't be extractable
- auth'd attacker gain access to unauth'd slots
…
#realworldcrypto
- unauth'd users gain access to private objects
- attacker extracts keys that shouldn't be extractable
- auth'd attacker gain access to unauth'd slots
…
#realworldcrypto
NO logical separation across HSM slots
All objects from slots are stored in same flash partition
#realworldcrypto
All objects from slots are stored in same flash partition
#realworldcrypto
Code exec is trivial
No ASLR
But resuming execution is hard, `CreateSecretKEy` needs to be auth'd
#realworldcrypto
No ASLR
But resuming execution is hard, `CreateSecretKEy` needs to be auth'd
#realworldcrypto
Uh oh, a logic bug allows installation of a dummy cert and failing check on firmware updates 😬
#realworldcrypto
#realworldcrypto
This is just one model from one vendor.
HSMs mostly certified against hardware attacks, but this demonstrates there are holes when it comes to software attacks.
#realworldcrypto
HSMs mostly certified against hardware attacks, but this demonstrates there are holes when it comes to software attacks.
#realworldcrypto
Next up, "TPM-Fail: TPM meets Timing and Lattice Attacks" from Daniel Moghimi, Berk Sunar, Thomas Eisenbarth, and Nadia Heninger
#realworldcrypto
#realworldcrypto
Using TPMs for digital signatures is useful for trusted execution of signing and remote attestation ❤️
#realworldcrypto
#realworldcrypto
Intel fTPM, gets you key in a few minutes of collection (not computation)
Get you a key in 80 minutes of collection 👌
#RealWorldCrypto
Get you a key in 80 minutes of collection 👌
#RealWorldCrypto
Ha, the vendor (Intel) forgot to update to the latest version of their own crypto library.
#realworldcrypto
#realworldcrypto
Q: Did you suggest fixes to the vendors or did they come up with them?
A: For intel the only thing they needed to do was update their crypto lib version, which took 9 months, all under embargo. 😬
#RealWorldCrypto
A: For intel the only thing they needed to do was update their crypto lib version, which took 9 months, all under embargo. 😬
#RealWorldCrypto
We don't want things to leak when running on your device, or you app running in the cloud. The HW's owner could be an adversary!
#realworldcrypto
#realworldcrypto
Highest protection requires almost twice as much memory bandwidth as unprotected. :/
#realworldcrypto
#realworldcrypto

Q: Why do you need such a large MAC?
A: Still up to debate, I would feel uneasy with 32bit MACs at the bottom of the merkle tree. Still testing.
#realworldcrypto
A: Still up to debate, I would feel uneasy with 32bit MACs at the bottom of the merkle tree. Still testing.
#realworldcrypto
Done for the day! Back tomorrow.
• • •
Missing some Tweet in this thread? You can try to
force a refresh