LIVE FROM... THE INTERNET, IT'S #REALWORLDCRYPTO !
https://twitter.com/durumcrustulum/status/1348680589113782278?s=19
🤞 fingers crossed 🤞 that #realworldcrypto 2022 will actually be in Amsterdam IRL 🦠
How secure is Bridgefy in real world usage? Not open source, had to reverse engineer and decompile the Android app.
#REALWORLDCRYPTO
#REALWORLDCRYPTO

Bridgefy claims now that they implement the Signal protocol. Mesh-network style Signal would be neat...if that's what they've actually done. No third-party review to confirm.
#REALWORLDCRYPTO
#REALWORLDCRYPTO

Evaluate the properties of your protocol or app in the circumstances it is actually used!!!
#REALWORLDCRYPTO
#REALWORLDCRYPTO

Q: Is there a place for PKCS1.5 padding in modern crypto?
A: This work shows, perhaps there isn't.
(I agree.)
#REALWORLDCRYPTO
A: This work shows, perhaps there isn't.
(I agree.)
#REALWORLDCRYPTO
Q: Mesh vs standard security model for Signal?
A: In Signal you can forget users location, in mesh their proximity is relevant.
#REALWORLDCRYPTO
A: In Signal you can forget users location, in mesh their proximity is relevant.
#REALWORLDCRYPTO
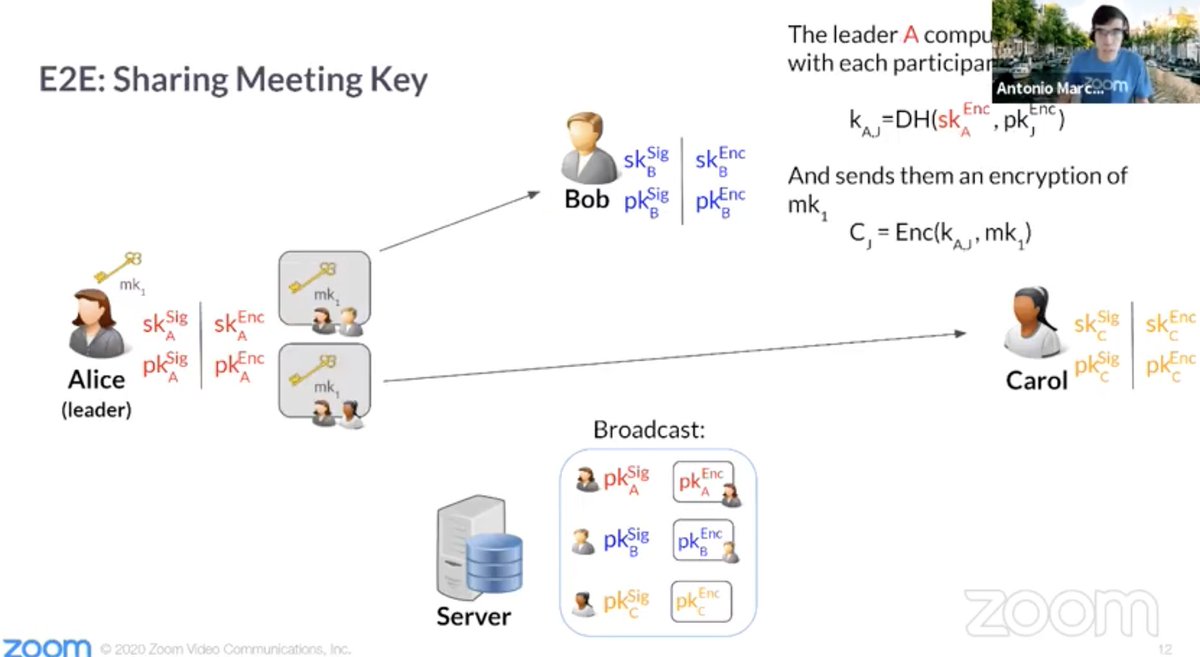
External IdP's can sign/attest to their users as they interact with Zoom's identity infra (has this been integrated with any IdP yet?)
#REALWORLDCRYPTO
#REALWORLDCRYPTO

Q: Do you get E2E benefits without signing up with an email?
A: Yes, will need to rely on security codes to establish ID because you won't have linkable ID between sessions.
(I discussed this exact thing in a blog post ;) zfnd.org/blog/so-you-wa…)
#REALWORLDCRYPTO
A: Yes, will need to rely on security codes to establish ID because you won't have linkable ID between sessions.
(I discussed this exact thing in a blog post ;) zfnd.org/blog/so-you-wa…)
#REALWORLDCRYPTO
A: Each participant uploads streams of different resolutions, no merging done by the server
#REALWORLDCRYPTO
#REALWORLDCRYPTO
Q: MLS?
A: Synchronous not async for Zoom, we can use ephemeral keys, don't provide forward-secrecy _within_ the meeting, just _between_ meetings, so for MLS, not quite applicable.
#REALWORLDCRYPTO
A: Synchronous not async for Zoom, we can use ephemeral keys, don't provide forward-secrecy _within_ the meeting, just _between_ meetings, so for MLS, not quite applicable.
#REALWORLDCRYPTO
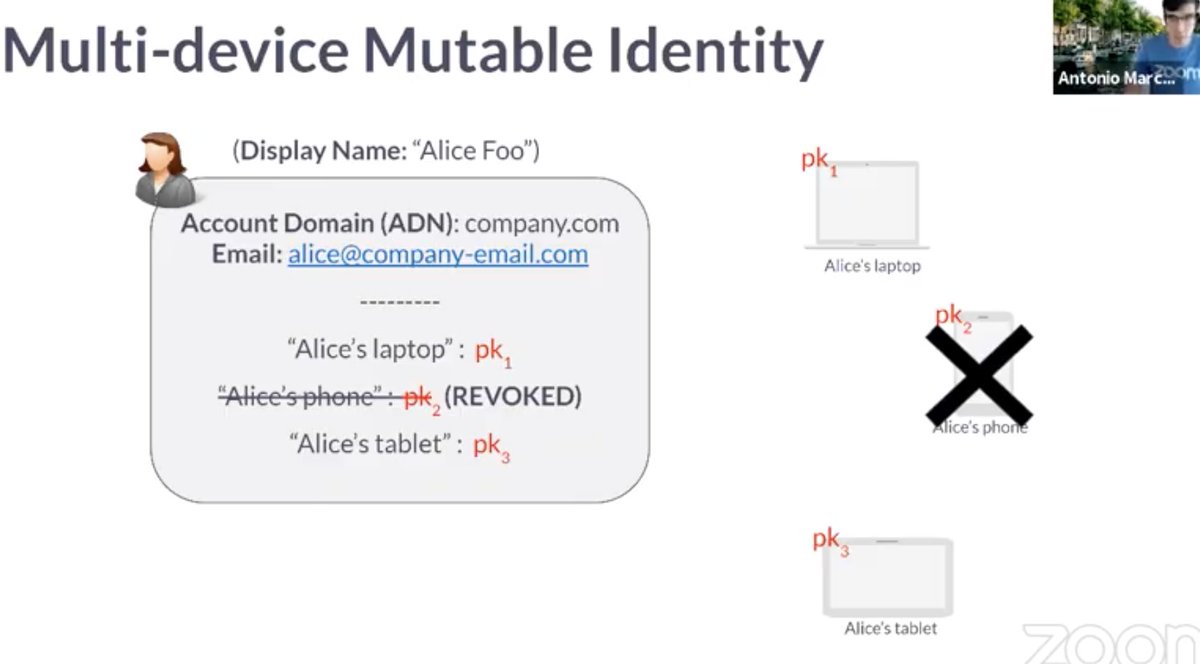
Q: How often do on-device ID keys change?
A: In practice we don't expect device keys to change key often (which is a tradeoff in privacy and security compromise)
#REALWORLDCRYPTO
A: In practice we don't expect device keys to change key often (which is a tradeoff in privacy and security compromise)
#REALWORLDCRYPTO
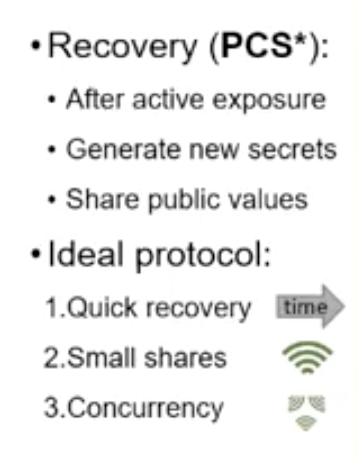
How do you (safely) ratchet key material forward, if one of the previously trusted group members have been compromised?
#REALWORLDCRYPTO
#REALWORLDCRYPTO
- minimal overhead in comms when _t_ users try to recover concurrently
- can a group ratchet protocol reach this minimum?
#REALWORLDCRYPTO
- can a group ratchet protocol reach this minimum?
#REALWORLDCRYPTO
Q: If you are hiding metadata, to you have to do trial encryption?
A: No: Signal encrypts all messages, group or 1:1, the same way, the group membership is separate; in this protocol, these messages are indistinguishable from normal usage patterns
#REALWORLDCRYPTO
A: No: Signal encrypts all messages, group or 1:1, the same way, the group membership is separate; in this protocol, these messages are indistinguishable from normal usage patterns
#REALWORLDCRYPTO
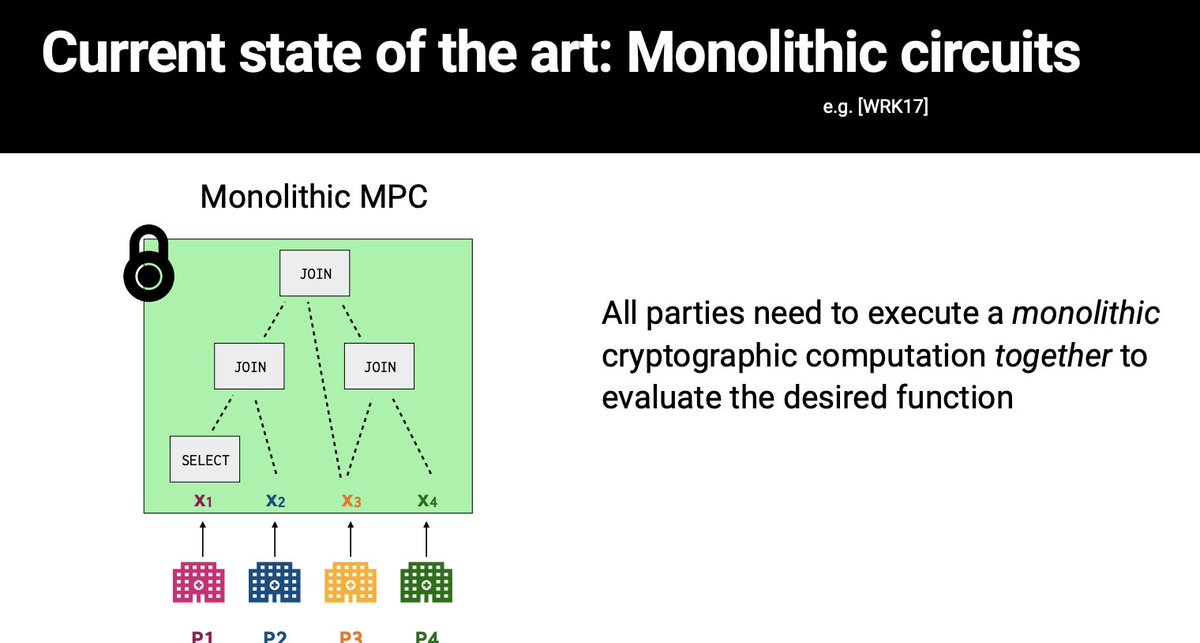
Next up is the Multiparty Computation session, starting with 'Lessons and Challenges in Deploying (Heavy) MPC in Different Environments' by Yehuda Lindell Valery Osheter Samuel Ranellucci, presented by Yehuda Lindell
#REALWORLDCRYPTO
#REALWORLDCRYPTO
Engineering, not cryptographic, solutions exist to make these protocols more practical in SaaS solutions
#REALWORLDCRYPTO
#REALWORLDCRYPTO

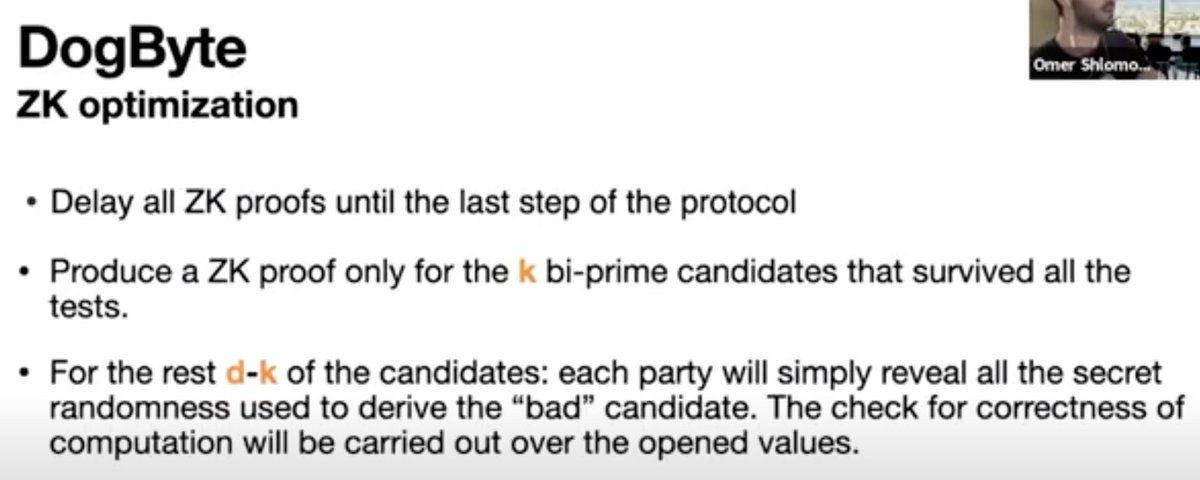
Next up, 'The Red Wedding: Playing Attacker in MPC Ceremonies', presented by Omer Shlomovits
iacr.org/submit/files/s…
#REALWORLDCRYPTO
iacr.org/submit/files/s…
#REALWORLDCRYPTO

Last up, 'Senate: A Maliciously Secure MPC Platform for Federated Analytics', presented by Rishabh Poddar
#REALWORLDCRYPTO
#REALWORLDCRYPTO

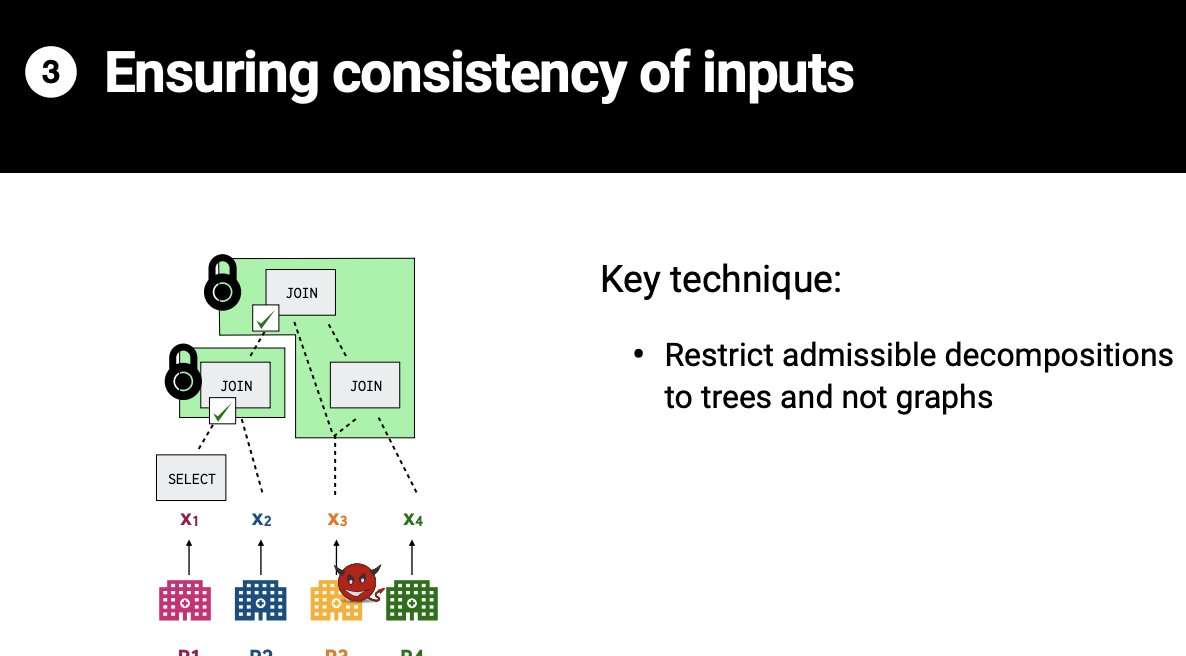
Q: How do you ensure that decompositions are valid?
A: Require that each sub is efficiently invertible
#REALWORLDCRYPTO
A: Require that each sub is efficiently invertible
#REALWORLDCRYPTO
My dear followers, I will have to cover the invited talk on isogenies by @luca_defeo after the fact, it pains me 😭 💫
#realworldcrypto
#realworldcrypto
Q: Are you surprised that NIST has relegated SIKE to the 'consolation' bracket?
A: No, it's a bit early; not surprised that lattices and McElice are the preferred candidates.
#realworldcrypto
A: No, it's a bit early; not surprised that lattices and McElice are the preferred candidates.
#realworldcrypto
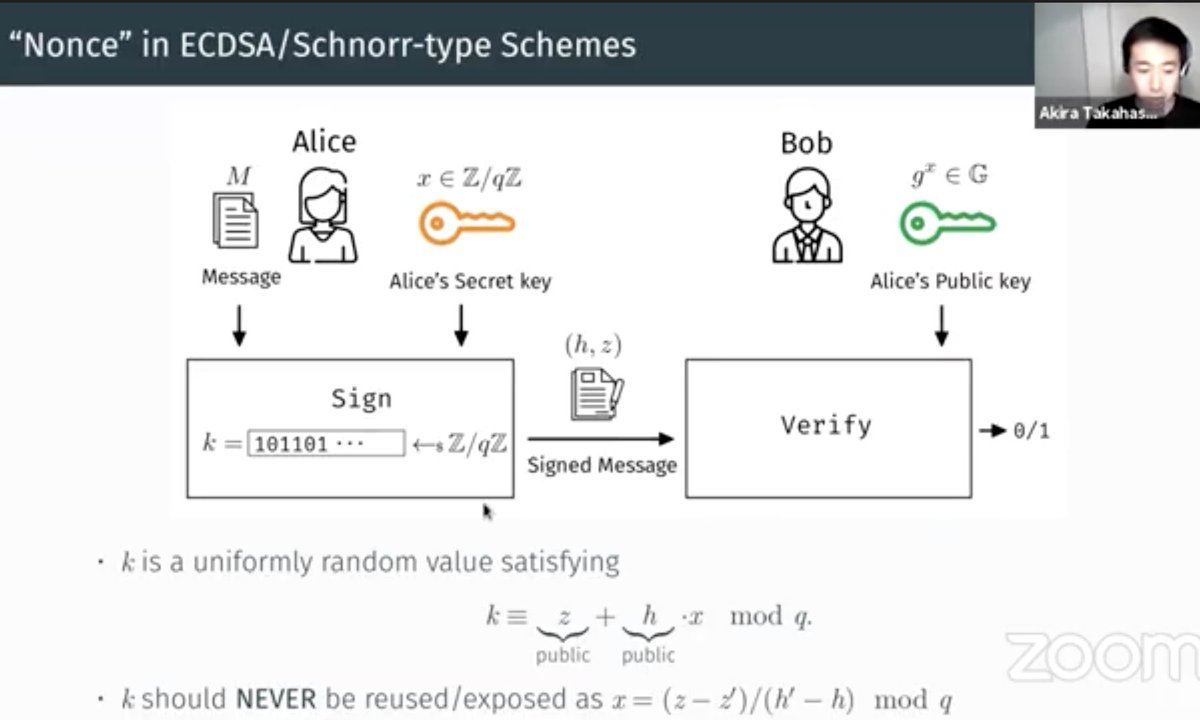
Next up, MuSig2: Simple Two-Round Schnorr Multi-Signatures, presented by Tim Ruffing
#realworldcrypto
#realworldcrypto
(disclosure: i work on a cyberrr co1n)
This nice linearity in the verification underlies all the Schnorr-based signature schemes
#realworldcrypto
#realworldcrypto
Instead of a pre-commitment round, every sender sends 2 pre-nonces, the proper nonce is a random linear combination of those
#realworldcrypto
#realworldcrypto

Convergence on multiple pre-nonces as input to linear combination. Proved under ROM+AGM+OMDL _or_ ROM+OMDL
#realworldcrypto
#realworldcrypto

Q: What's the difference between multi and threshold sigs?
A: N-of-N vs T-of-N where T < M
Q: 2-user case?
A: Having 1-of-2 is not particularly helpful? But our scheme does work for it.
#realworldcrypto
A: N-of-N vs T-of-N where T < M
Q: 2-user case?
A: Having 1-of-2 is not particularly helpful? But our scheme does work for it.
#realworldcrypto
Q: ECDSA?
A: No, depends on the nice linearity inherent in Schnorr, would be hard and cumbersome
#realworldcrypto
A: No, depends on the nice linearity inherent in Schnorr, would be hard and cumbersome
#realworldcrypto
Specifically, 'Asynchronous Remote Key Generation: An Analysis of Yubico’s Proposal for W3C WebAuthn'
#realworldcrypto
#realworldcrypto
Current runtime, 100ms, this scheme would double it, but these are ~one time registration/recovery operations
#realworldcrypto
#realworldcrypto
Q: Can you confine backup keys to only work with some relying parties?
A: Yes, you register a backup key with relying parties, so you can choose not to do that.
#realworldcrypto
A: Yes, you register a backup key with relying parties, so you can choose not to do that.
#realworldcrypto
Q: What about host malware, trying to pretend it is a backup when you register?
A: Pin must be entered on authenticator first
#realworldcrypto
A: Pin must be entered on authenticator first
#realworldcrypto
Q: Can I have one backup for 5 primary keys?
A: Yes! On the one service, using the backup, the 5 primary keys would be revoked (this is the server-side logic).
#realworldcrypto
A: Yes! On the one service, using the backup, the 5 primary keys would be revoked (this is the server-side logic).
#realworldcrypto
Next session, on Humans, Policy, and Crypto
Starting with, 'Mental Models of Cryptographic Protocols - Understanding Users to Improve Security', presented by Katharina Krombholz
#realworldcrypto
Starting with, 'Mental Models of Cryptographic Protocols - Understanding Users to Improve Security', presented by Katharina Krombholz
#realworldcrypto
"Admins were incapable of making informed security decisions"
"I'm afraid of using crypto"
😭
#realworldcrypto
"I'm afraid of using crypto"
😭
#realworldcrypto
How can we measure the mental models users have of security tools and protocols (and just asking them is not so easy)
#realworldcrypto
#realworldcrypto
Q: How do we know that 'human' is the right level of abstraction to understand this problem, vs 'developers' or?
A: Yes, we focus on 'users', which was developed by technology developers; where else do we go, maybe theoreticians?
#realworldcrypto
A: Yes, we focus on 'users', which was developed by technology developers; where else do we go, maybe theoreticians?
#realworldcrypto
Q: What should the role of human factors work in the development of crypto standards?
A: I wish this perspective is incorporated in standardization too
#realworldcrypto
A: I wish this perspective is incorporated in standardization too
#realworldcrypto
Q: How much do users need to _understand_ the crypto? Shouldn't the browser take care of this for them?
A: Yes: ala conservation theory, to protect the end users, we should protect the admins, the designers, the developers, who are upstream in the ecosystem
#realworldcrypto
A: Yes: ala conservation theory, to protect the end users, we should protect the admins, the designers, the developers, who are upstream in the ecosystem
#realworldcrypto
Next up! 'Protecting Cryptography against Self-Incrimination', presented by Sarah Scheffler
#realworldcrypto
#realworldcrypto
Are you testifying that you know a password, or because the password unlocks your cloud drive, that you know the contents of your cloud drive?
#realworldcrypto
#realworldcrypto

"The encryption cases are so all over the place that it's hard to create a reliable benchmark" 😂
#realworldcrypto
#realworldcrypto
"If such a [backdoor key], it would make the whole compelled decryption a foregone conclusion" 😱
#realworldcrypto
#realworldcrypto

It seems like having a password stored in your brain meat is actually protective in this model against compelled decryption
#realworldcrypto
#realworldcrypto
Even without a current quantum computer, you can just save the protected data until it is available.
#realworldcrypto
#realworldcrypto

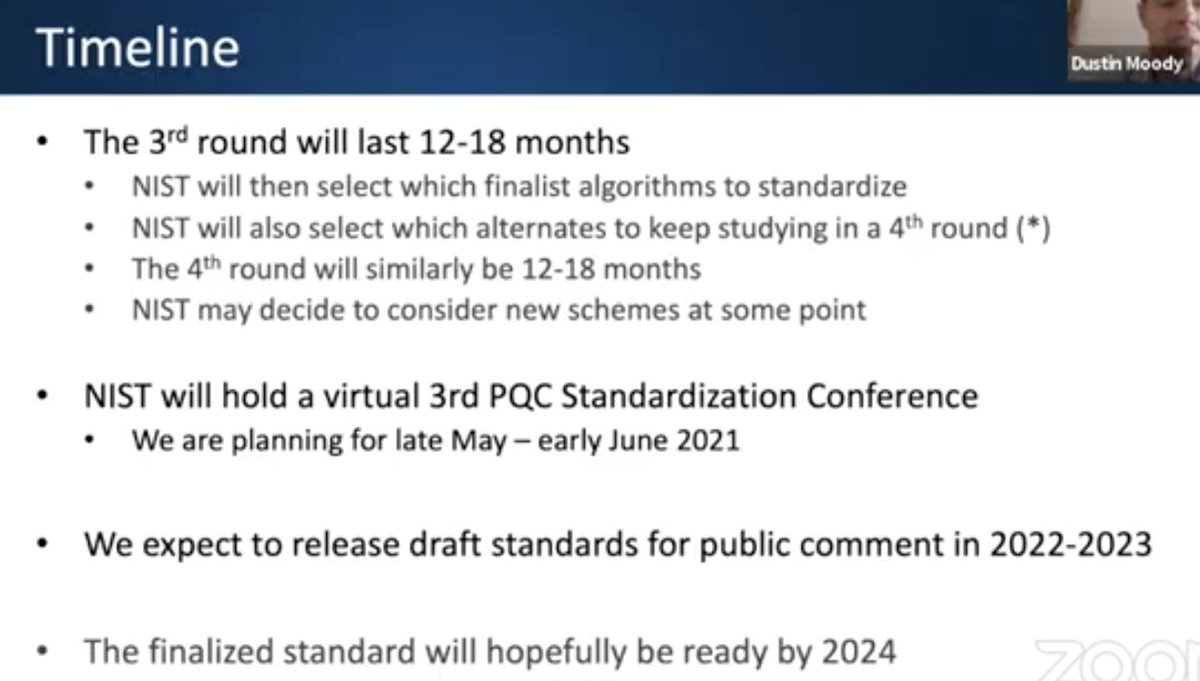
For round 3 selections, two tracks: finalists, and alternates
Alternates have a _potential_ of eventual standardization
#realworldcrypto
Alternates have a _potential_ of eventual standardization
#realworldcrypto

Other challenges:
- IP
- benchmarking
- side channel analysis
- real world experiments (like Chrome, Cloudflare TLS experiments)
- Hybrids!
#realworldcrypto
- IP
- benchmarking
- side channel analysis
- real world experiments (like Chrome, Cloudflare TLS experiments)
- Hybrids!
#realworldcrypto
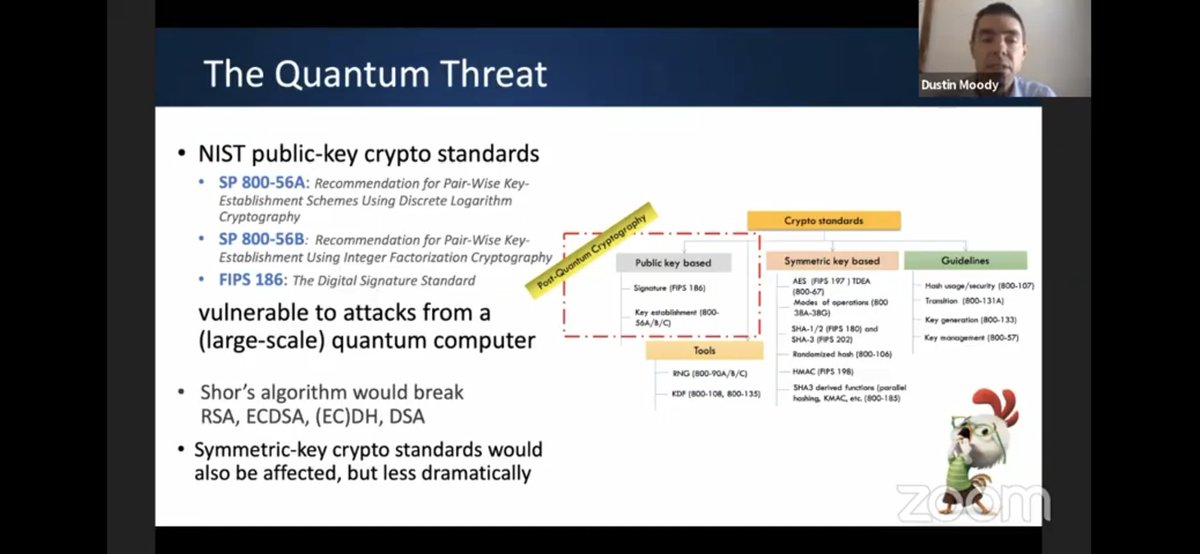
Stateful hash-based signatures were not included in the NIST competition, they are not the same as standard-use digital signatures, have been standardized by IETF, if you are _careful_ about using them, they are quantum-resistant
#realworldcrypto
#realworldcrypto

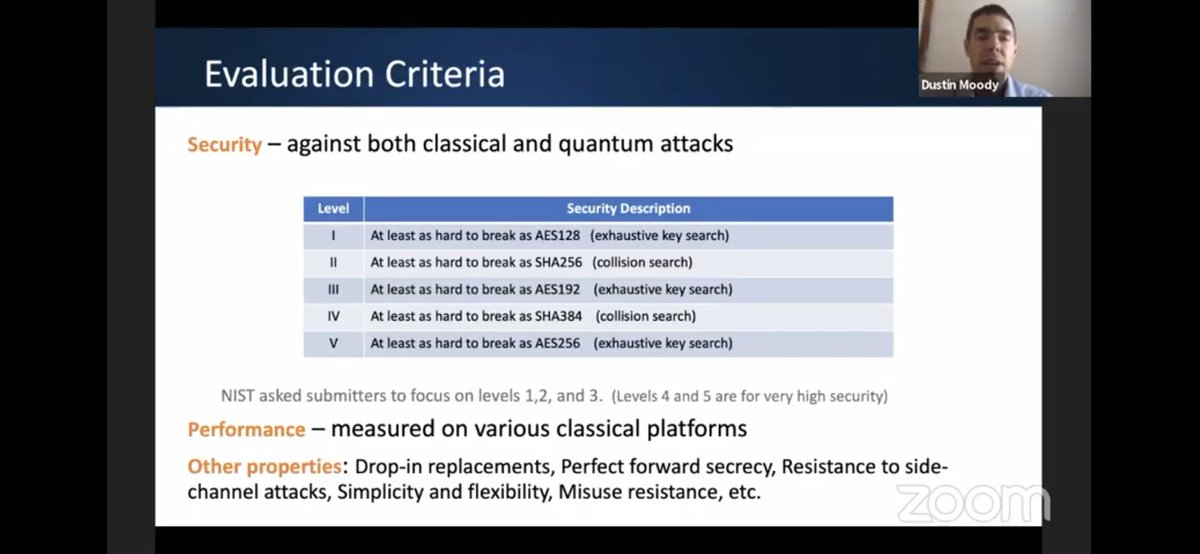
Q: Will criteria such as PKE-robustness inform the selections?
A: Try to weigh everything including that
#realworldcrypto
A: Try to weigh everything including that
#realworldcrypto
Q: Does NIST help with dealing with IP contention issues resolved?
A: Trying to work behind the scenes to help clear up any IP questions by the end of the 3rd round.
#realworldcrypto
A: Trying to work behind the scenes to help clear up any IP questions by the end of the 3rd round.
#realworldcrypto
Next up, the post-quantum session!
Starting with 'Attacks on NIST PQC 3rd Round Candidates' presented by Daniel Apon and James Howe
#realworldcrypto
Starting with 'Attacks on NIST PQC 3rd Round Candidates' presented by Daniel Apon and James Howe
#realworldcrypto
Integrating hints from the side-channel into the lattice-reduction attack algorithm 🤯
#realworldcrypto
#realworldcrypto

- implementation complexity will significantly increase with these standards
- more attack vectors? more countermeasures?
- fragile/sensitive ops
#realworldcrypto
- more attack vectors? more countermeasures?
- fragile/sensitive ops
#realworldcrypto

A question (more of a comment, really) about conflating attacks on implementation vulns and against constructions
#realworldcrypto
#realworldcrypto
Q: Does the existence of fault attacks imply anything?
A: There may be categories of side-channel attacks exploit a property of the algorithm, that can allow you to distinguish between protocols that are similar, that's important.
#realworldcrypto
A: There may be categories of side-channel attacks exploit a property of the algorithm, that can allow you to distinguish between protocols that are similar, that's important.
#realworldcrypto
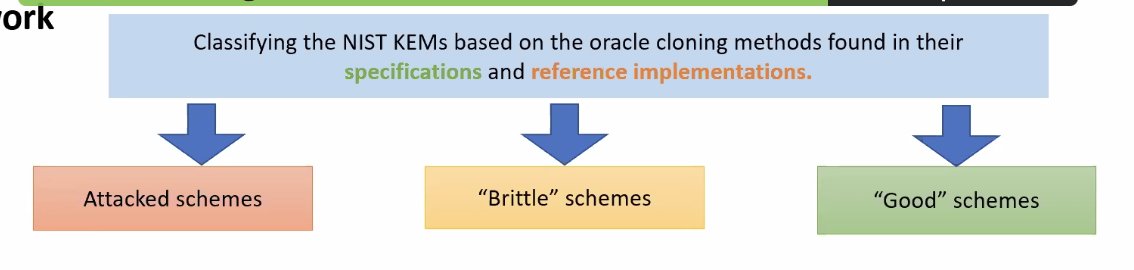
Next up, 'Separate Your Domains: NIST PQC KEMs and Pitfalls in Implementing Random Oracles', presented by Hannah Davis
#realworldcrypto
#realworldcrypto
Round 1 KEM (DAGS) was leaking over half the bits of the session key directly in the ciphertext, none of these were caught in the first round (eliminated for other reasons) 😱
#realworldcrypto
#realworldcrypto
Why? Multiple hash functions in the spec, but only the one same in the implementation.
#realworldcrypto
#realworldcrypto

What about domain separation?
In practice, not always used, or done poorly, but not being caught in evals.
#realworldcrypto
In practice, not always used, or done poorly, but not being caught in evals.
#realworldcrypto
Attacked schemes have been eliminated from NIST PQC, but these attacks were not found before then.
#realworldcrypto
#realworldcrypto
Can be catastrophic, just use one oracle cloning method from the toolbox; one candidate has already done this 🎉
#realworldcrypto
#realworldcrypto
A: Big problems arise when the spec expects 3 different hash functions, and only one is used for all usages. Static analysis may not catch all cases
#realworldcrypto
#realworldcrypto
A: Our hope is that putting specific oracle cloning methods into specifications will become more common, rather than leaving it up to the implementor.
#realworldcrypto
#realworldcrypto
Key concerns:
- secure boot
- over-the-air update
If this is PQ-secure, you can deliver the remaining updates via that platform.
#realworldcrypto
- secure boot
- over-the-air update
If this is PQ-secure, you can deliver the remaining updates via that platform.
#realworldcrypto

Comparing X25519 and lattice-based competitors (but Cortex M4 is considered 'high end' for a lot of the domains mentioned previously)
#realworldcrypto
#realworldcrypto

Q: Why NTRU use so much more stack than Kyber?
A: Not sure if inherent to the scheme or an implementation tradeoff to get more speed.
#realworldcrypto
A: Not sure if inherent to the scheme or an implementation tradeoff to get more speed.
#realworldcrypto
Q: Schemes mandated use of NTT, does that matter?
A: For some embedded devices that is an unfortunate performance impact, maybe make it optional
#realworldcrypto
A: For some embedded devices that is an unfortunate performance impact, maybe make it optional
#realworldcrypto
A: New hardware optimized for winners of the NIST PQC? Codes vs lattice need completely different types of co-processors, so we kinda have to look at using the hardware we have.
#realworldcrypto
#realworldcrypto
I will say the organizers are extremely efficient and uh, well-organized, with their Zoom'ing. 👏
#realworldcrypto
#realworldcrypto
@dstebila speaking on CHES 2021 call for artifacts, to improve reproducibility of crypto research
#realworldcrypto
#realworldcrypto
@FiloSottile on AGE! 'A simple, modern and secure encryption tool (and Go library) with small explicit keys, no config options, and UNIX-style composability'
github.com/FiloSottile/age
#realworldcrypto
github.com/FiloSottile/age
#realworldcrypto
@kobigurk on proof-of-stake blockchain, doing an MPC set up for the params for the circuit
#realworldcrypto
#realworldcrypto
Yaron Gvili on a Swift hash function implementation, look for 'secure homomorphic hash'
#REALWORLDCRYPTO
#REALWORLDCRYPTO
Greg from MSR security and crypto team about remote internships open for this summer! careers.
#REALWORLDCRYPTO
#REALWORLDCRYPTO
@str4d on modeling: trial decryption to scan for notes is slow, we'd like something like a detection key without revealing it, useful for Zcash
#realworldcrypto
#realworldcrypto
From Daniel Apon on NIST PQC monthly seminar talks:
groups.google.com/a/list.nist.go…
#realworldcrypto
groups.google.com/a/list.nist.go…
#realworldcrypto
Back for day 3 of #realworldcrypto! The first invited talk of the day by Carmela Troncoso on 'Privacy by Design -- From Theory to Practice in the Context of COVID-19 Contact Tracing', on the D3PT protocol, which influenced the iOS | Android one
Next up, Vanessa Teague (@VTeagueAus )on a dovetailing talk, 'Unintended Privacy Problems in Some Centralized and Decentralized COVID-19 Exposure Notification Systems'
#REALWORLDCRYPTO
#REALWORLDCRYPTO
@VTeagueAus An unusual example in which an app failing at its core value proposition is undetectable by users.
#realworldcrypto
#realworldcrypto

"For centralized apps like COVIDSafe, inferring social graph edges is the least of our worries." 😭
#realworldcrypto
#realworldcrypto
Some variants of this app allow optional extra exposure information to say a health authority/the government, it all depends on whether ExposureInfo is shuffled before upload; was fixed in June 2020
#realworldcrypto
#realworldcrypto

If Annika opts in to uploading detailed ExposureInfo, and if the metadata is enough to re-identify Bob, Charlie and Dan’s records, the authorities can tell whether a record for Wit appears after them.
#realworldcrypto
#realworldcrypto
- decentralized protect privacy of the social graph of users much more than centralized
- GAEN apps much better than centralized apps
#realworldcrypto
- GAEN apps much better than centralized apps
#realworldcrypto

Q: Android location services needed to be turned on for the app to run?
A: Required to be turned on if any app is scanning for BLE pings; the app did not use location services (did not ping back to Google) unknown but unclear if this allows Google to correlate
#realworldcrypto
A: Required to be turned on if any app is scanning for BLE pings; the app did not use location services (did not ping back to Google) unknown but unclear if this allows Google to correlate
#realworldcrypto
Next up, 'Exposure Notification System May Allow for Large-Scale Voter Suppression' presented by Rosario Gennaro
#realworldcrypto
#realworldcrypto
In the US, contact tracing is state-by-state per the health authorities, all the apps rolled out use the Google | Apple Exposure Notification interoperable API (GAEN)
#realworldcrypto
#realworldcrypto

How do we increase adoption of a public health intervention? We can learn lessons from other campaigns, such as successful campaigns for PReP adoption to combat HIV
#realworldcrypto
#realworldcrypto

Can a relay attack against these COVID alert apps dissuade election-day voters? (Aside: this is why vote by mail was a huge campaign in the US, to avoid COVID impacts on votes getting counted)
#realworldcrypto
#realworldcrypto

Q: Is this still a problem if most people vote by mail ?
A: Those are good countermeasures to this, there a still large number of ballots cast on election day, a compromise of an official government channel in a way that affects the vote could still make a diff
#realworldcrypto
A: Those are good countermeasures to this, there a still large number of ballots cast on election day, a compromise of an official government channel in a way that affects the vote could still make a diff
#realworldcrypto
Next up, 'Privacy-Preserving Bluetooth Based Contact Tracing --- One Size Does Not Fit All', presented by Eyal Ronen
#realworldcrypto
#realworldcrypto
Privacy vs Explainability tradeoff
Balancing false negatives, privacy, and useful notifs
#realworldcrypto
Balancing false negatives, privacy, and useful notifs
#realworldcrypto
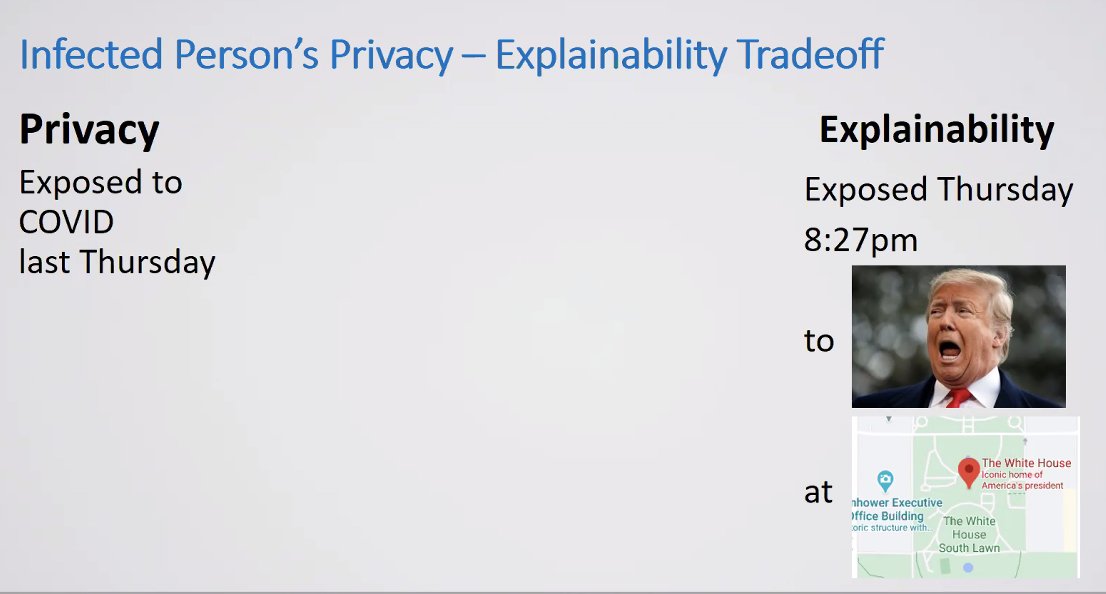
For contact tracing, we don't necessarily need to know geo locations, just proximity and duration
#realworldcrypto
#realworldcrypto
Q: Did HamAgen expose the GPS data of infected users to the rest of the country?
A: No.
#realworldcrypto
A: No.
#realworldcrypto
Next up, 'Privately Connecting Mobility to Infectious Diseases via Applied Cryptography', presented by Lukas Helminger
#realworldcrypto
#realworldcrypto
Aggregating mobility data of infected people, that may catch potential superspreader events early, with small numbers. Problem so far is privacy.
#realworldcrypto
#realworldcrypto

Q: what is the timespan for a single heatmap rated at 2hours/10USD?
A: Last 7 days of mobility data.
#realworldcrypto
A: Last 7 days of mobility data.
#realworldcrypto
Q: is there two variants of the protocol for semi-honest/malicious adversaries, and is there a performance hit if so?
A: We can split them up; there is not much overhead from semihonest to malicious models
#realworldcrypto
A: We can split them up; there is not much overhead from semihonest to malicious models
#realworldcrypto
Q: are there difficulties due to different sets of researchers and different mobile data providers all having separate datasets?
A: Those are issues we'd have to solve when/if this is rolled out
#realworldcrypto
A: Those are issues we'd have to solve when/if this is rolled out
#realworldcrypto
Break!
Next up, "Rosita: Towards Automatic Elimination of Power-Analysis" presented by Yuval Yarom
#realworldcrypto
#realworldcrypto
Using an attacked called "elmo" and a tool called Rosita they wrote to find leakage and rewrite code to remove side channels
#realworldcrypto
#realworldcrypto
Comparing a masked impl of AES, vs a processed version, removes the leak. Adding new instructions slows down by 15% and 64% for ChaCha
#realworldcrypto
#realworldcrypto

Q: Is the masking compiler dependent? Will switching compiler optimization level matter?
A: Independent; switching compiler optimizations changes the code generation, has no effect as we apply our fixes in the assembly itself.
#realworldcrypto
A: Independent; switching compiler optimizations changes the code generation, has no effect as we apply our fixes in the assembly itself.
#realworldcrypto
Q: Can you identify "patches" where you only need to re-order instructions, rather than add new ones? To save impacting performance etc.
A: Not yet; we insert dummy instructions that change the execution to one that has no interactions at the microarch level
#realworldcrypto
A: Not yet; we insert dummy instructions that change the execution to one that has no interactions at the microarch level
#realworldcrypto
Q: What happens when the CPU gets smarter and starts reordering the instruction stream?
A: Pipelining yet baked into the tool, we are targeting CortexM3, for anything more complex we need to re-eval
#realworldcrypto
A: Pipelining yet baked into the tool, we are targeting CortexM3, for anything more complex we need to re-eval
#realworldcrypto
How do I do constant time? Use crypto extensions, avoid table lookups, branches. Krypto
defines encoding rules for constant‐time multiply. A compiler flag should activate it.
#realworldcrypto
defines encoding rules for constant‐time multiply. A compiler flag should activate it.
#realworldcrypto

Q: Any spec for the RNG entropy source?
A: We have a paper here, a lot of design rational in the spec itself and pitfalls to avoid.
#realworldcrypto
A: We have a paper here, a lot of design rational in the spec itself and pitfalls to avoid.
#realworldcrypto

Q: When designing the crypto extensions, Yes; for timing the important ones are table lookups, so we wrapped that up; there are proposals in the spec for constant-time sboxes
#realworldcrypto
#realworldcrypto
Q: Bignum? I'd love to have a simple way to do carry chains and multiply-accumulates with the full width in the hardware.
A: Can use 8 bits out of 64bits as a carry, works on scalar and vectorized instructions;
#realworldcrypto
A: Can use 8 bits out of 64bits as a carry, works on scalar and vectorized instructions;
#realworldcrypto
Next up, 'CacheOut and SGAxe: How SGX Fails in Practice' presented by Stephan van Schaik
#realworldcrypto
#realworldcrypto
Now you can no longer leak in the L2 cache (?), but there are plenty of other microarchitectural attacks remaining
#realworldcrypto
#realworldcrypto
Doesn't fix that you _can_ leak, just flushes buffers frequently enough to make it less likely
#realworldcrypto
#realworldcrypto

Allows short and memorable pins
But this attack allows leaking those pins from SGX, with side channel knowledge
#realworldcrypto
But this attack allows leaking those pins from SGX, with side channel knowledge
#realworldcrypto
Q: Mitigations in the signing bot against abuse?
A: Can only allow certain fields; no evidence of anyone trying to misuse the bot
#realworldcrypto
A: Can only allow certain fields; no evidence of anyone trying to misuse the bot
#realworldcrypto
Q: Which mainstream architectures have been microcode patched?
A: Intel is the only one affected, haven't heard about others being affected.
#realworldcrypto
A: Intel is the only one affected, haven't heard about others being affected.
#realworldcrypto
Next up, 'My other car is your car: compromising the Tesla Model X keyless entry system', presented by Lennert Wouters
#realworldcrypto
#realworldcrypto
It's a BLE peripheral, with over the air download, allowing easier overwriting of firmware on the keyfob; Tesla has mitigated this slightly
#realworldcrypto
#realworldcrypto
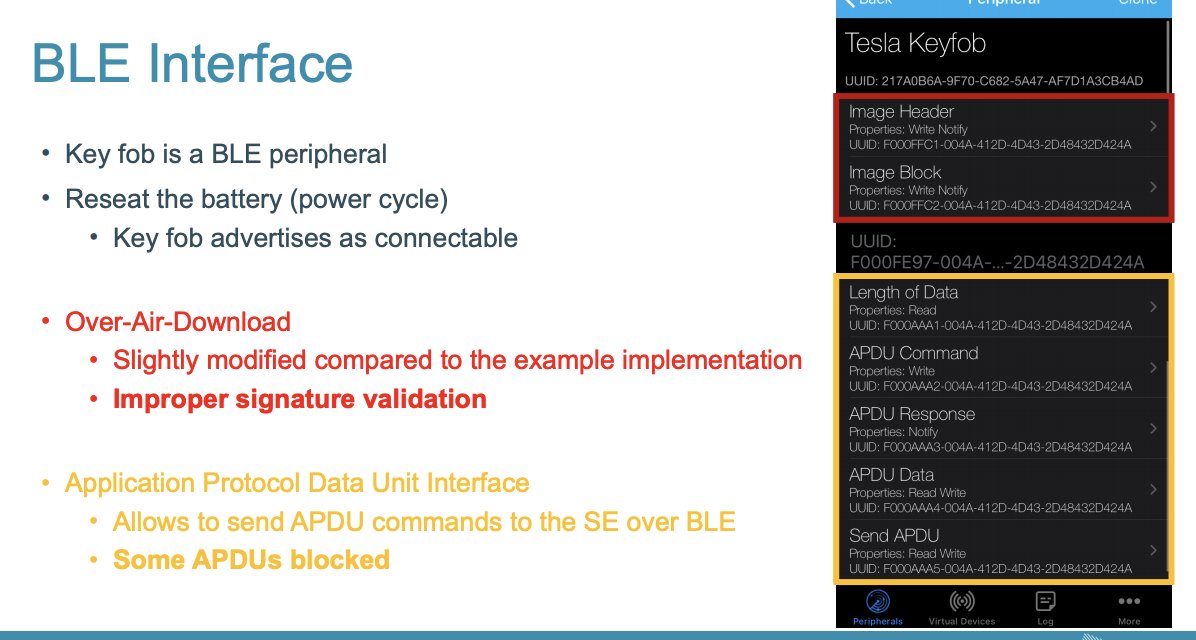
We can modify a keyfob and check all the provisioning-related steps, and go straight to pairing.
#realworldcrypto
#realworldcrypto
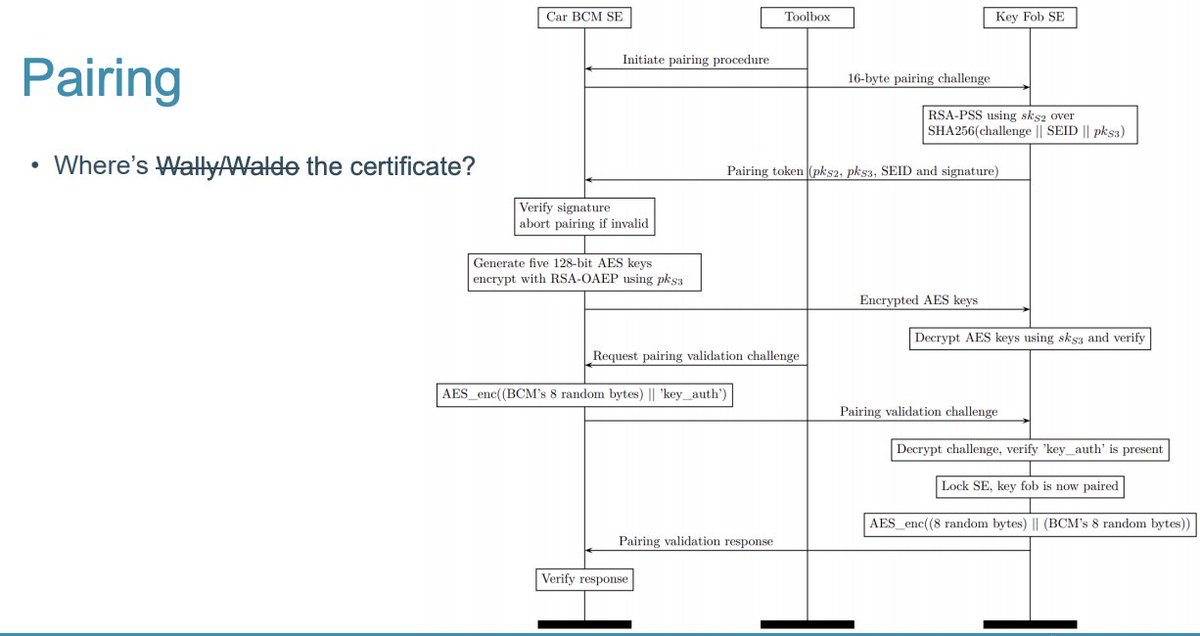
Did not modify the keyfob firmware, but removed secure element and emulated it in Python
#realworldcrypto
#realworldcrypto

The car is completely disjoint from the provisioning and pairing protocol for a new key fob.
#realworldcrypto
#realworldcrypto
Tesla has a second factor (pin code) that you can use to also require to start the car, with the fob, but that may also be bypassable.
#realworldcrypto
#realworldcrypto
Not requiring a power cycle for a new fob seems to be intended to make the lives of service technicians easier
#realworldcrypto
#realworldcrypto
(damnit, that's supposed to be a beaver emoji)
In order to carry formal guarantees down the stack ,we have to check our assumptions and that they continue to hold as we go layer to layer. // @fugueish
#realworldcrypto
#realworldcrypto
@fugueish - Embrace design changes that simplify/modularize reasoning
- Verified compilers, scale assembly verification
- Security-oriented hardware-software contract at the ISA level
- Consolidate each layer of guarantees
#realworldcrypto
- Verified compilers, scale assembly verification
- Security-oriented hardware-software contract at the ISA level
- Consolidate each layer of guarantees
#realworldcrypto
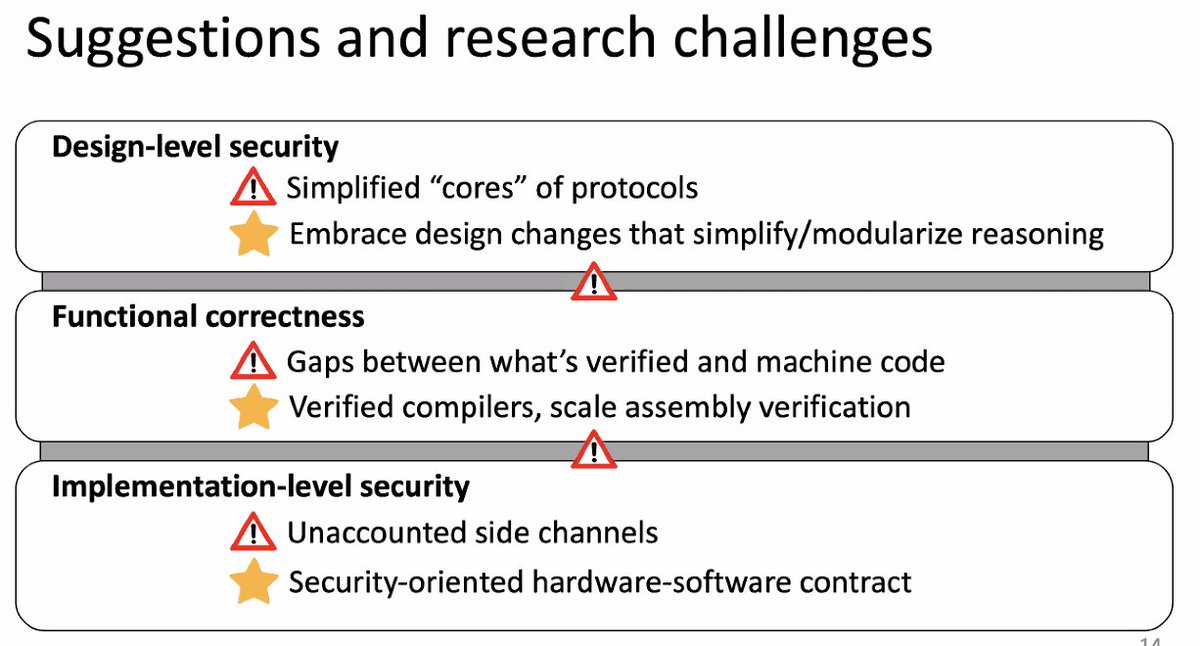
@fugueish We don't need it to be perfect, just need to keep the bar higher than attackers can get over
#realworldcrypto
#realworldcrypto

Q: Formal methods not just for crypto?
A: Crypto is the sweet spot: not a huge volume of code vs a kernel, the benefits far outweigh the costs, may not be the same for every system
#realworldcrypto
A: Crypto is the sweet spot: not a huge volume of code vs a kernel, the benefits far outweigh the costs, may not be the same for every system
#realworldcrypto
Q: How much of this depends on invisible compiler optimizations?
A: There are some verified compiles that preserve side-channel countermeasures
#realworldcrypto
A: There are some verified compiles that preserve side-channel countermeasures
#realworldcrypto
last up for the day, 'Verifpal: Cryptographic Protocol Analysis for the Real World' by Nadim Kobeissi
#realworldcrypto
#realworldcrypto
Collaborators Georgio Nicolas and Mukesh Tiwari sound to be on the job market soon 🎓
#realworldcrypto
#realworldcrypto
That's today, one more day tomorrow!
First up on the last day of #realworldcrypto, Eli Ben-Sasson on 'Scaling Computations on Blockchains with ZK-STARKs' 

"Why don't Bitcoin or Ethereum compete at scale to Visa or Swift?
Your laptop can't do it."
#realworldcrypto
Your laptop can't do it."
#realworldcrypto

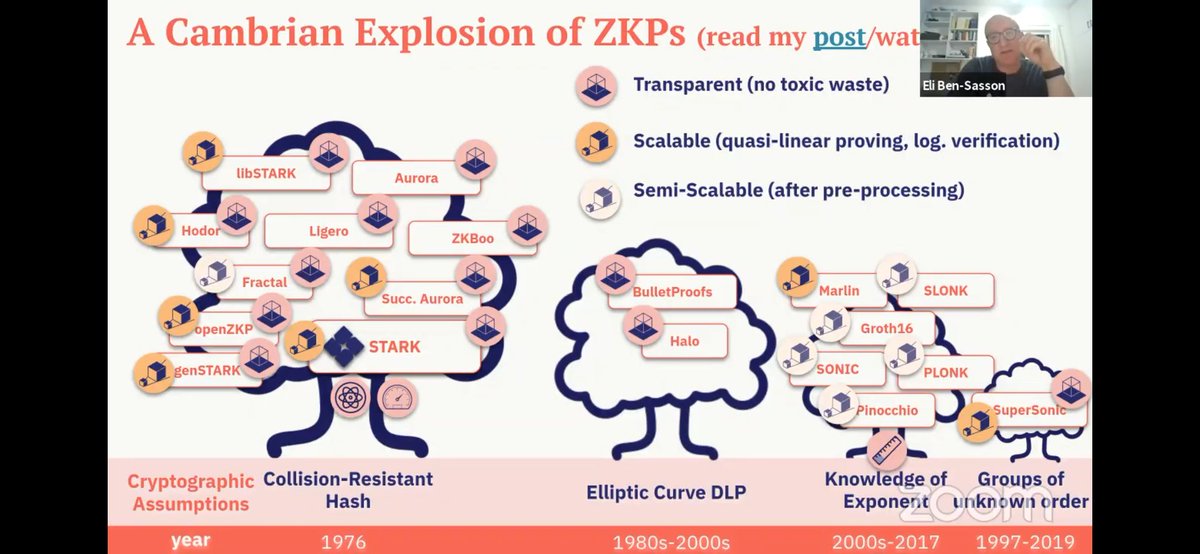
Relying on the hardness of a hash function (eg SHA3) makes STARKs theoretically quantum-resistant 🎉
#realworldcrypto
#realworldcrypto

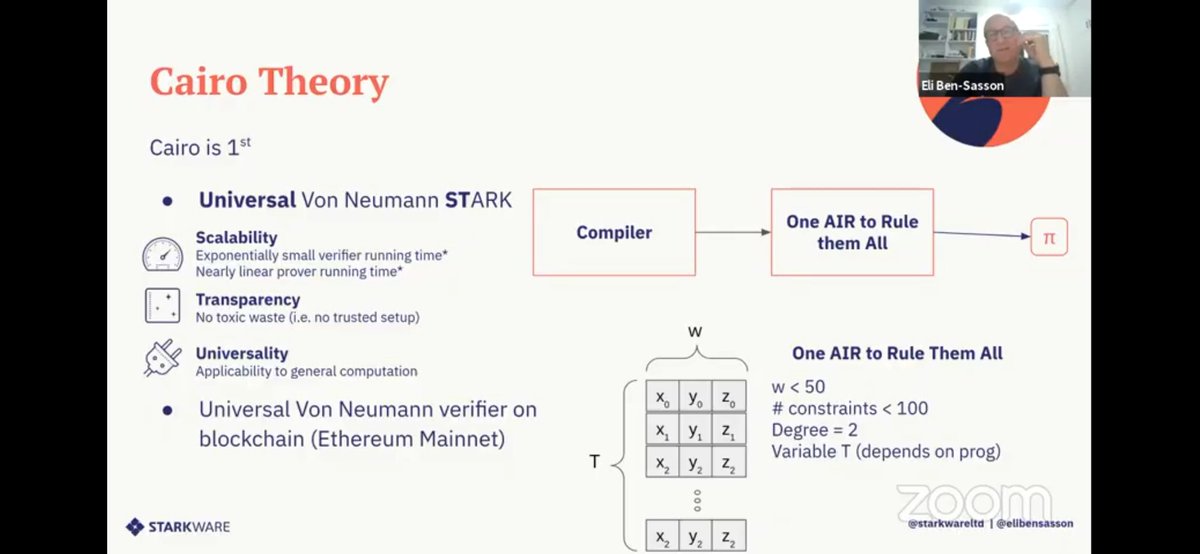
Q: Cairo is a new DSL, among others for proof systems, where does Cairo fit?
A: it's more like assembly for this VM, allows memory access, branching, Turing complete, more similar to TinyRAM. Cairo is production-grade, integrated in existing blockchains
#realworldcrypto
A: it's more like assembly for this VM, allows memory access, branching, Turing complete, more similar to TinyRAM. Cairo is production-grade, integrated in existing blockchains
#realworldcrypto
Q: Does this apply to Bitcoin in any way?
A: Would require Bitcoin to have a STARK verifier of some sort;
#realworldcrypto
A: Would require Bitcoin to have a STARK verifier of some sort;
#realworldcrypto
Q: How has your view of the diff between STARKs & SNARKs changed over the last year w/ transparency for SNARKs too?
A: if the length of the arg is the thing you want to minimize, Groth16 is king; for proving time, verifiying time, min assumptions, STARK wins
#realworldcrypto
A: if the length of the arg is the thing you want to minimize, Groth16 is king; for proving time, verifiying time, min assumptions, STARK wins
#realworldcrypto
Q: In this architecture, can you prevent front-running?
A: Question of sequencing txs, in our system there is an operator, in others, zkRollup, pushes the sequencing to the blockchain
#realworldcrypto
A: Question of sequencing txs, in our system there is an operator, in others, zkRollup, pushes the sequencing to the blockchain
#realworldcrypto
MPC and TSS offer high assurance on
paper thanks to math proofs, but remain susceptible to misimplementations or overlooked threat vectors
#realworldcrypto
paper thanks to math proofs, but remain susceptible to misimplementations or overlooked threat vectors
#realworldcrypto
Q: Have these attacks affected prod systems?
A: They have affected exchanges and been disclosed and patched responsibly.
#realworldcrypto
A: They have affected exchanges and been disclosed and patched responsibly.
#realworldcrypto
I think N=18 is the largest I've encountered but it's usually much lower than that, complexity makes it hard and slow to use w/ large N
#realworldcrypto
#realworldcrypto
Q: stateful vs stateless? e.g. failing to delete/overwrite shares, reusing nonces, etc
A: If you can be stateless it eliminates a lot of vulns
#realworldcrypto
A: If you can be stateless it eliminates a lot of vulns
#realworldcrypto
Next up, 'From Crypto-Paper to Crypto-Currency: the Cardano Consensus Layer', presented by Christian Badertscher
#realworldcrypto
#realworldcrypto
"Protocol must take into account that some (some!) participants are rational, and must be incentivized" 😁
#realworldcrypto
#realworldcrypto
The macroscopic properties of the system must be enumerated, checked against the spec, and possibly tested via property-based tests (❤️)
#realworldcrypto
#realworldcrypto

An open network when anyone can send you data, so you must design with the worst-case behavior in mind.
#realworldcrypto
#realworldcrypto

Q: Property-based testing?
A: Aggressive filtering of incoming data, we can do that because Proof-of-Stake determines blocks, allows forecasting; our prop tests revealed that an expected behavior did not arise, just a very general property test caught this
#realworldcrypto

A: Aggressive filtering of incoming data, we can do that because Proof-of-Stake determines blocks, allows forecasting; our prop tests revealed that an expected behavior did not arise, just a very general property test caught this
#realworldcrypto


Next up, 'Alice in Randomland: How to Build and Use Distributed Randomness Beacons', presented by Bernardo David
#realworldcrypto
#realworldcrypto
It's not just enough to have intuition that your protocol works, a proof that works with arbitrary compositions is also needed.
#realworldcrypto
#realworldcrypto
Next up, 'SWiSSSE: System-Wide Security for Searchable Symmetric Encryption' presented by @kennyog
#realworldcrypto
#realworldcrypto
Existing security notions in the literature to not take into account the actual fetching of the documents 👀
#realworldcrypto
#realworldcrypto

Uses standard HMAC-SHA-256, AES-GCM, Java+JCE, and a Redis server. 6X overhead vs plaintext
#realworldcrypto
#realworldcrypto

In the general setting, we consider the server adversarial (ie, your cloud provider). Also a network attacker, maybe they can see volumes and directionality of traffic, that is taken into account in this model.
#realworldcrypto
#realworldcrypto
Q: What client storage is necessary for this scheme? What about multiple writers?
A: This is a single-writer scheme; in our paper we give worst-case stash size estimates
#realworldcrypto
A: This is a single-writer scheme; in our paper we give worst-case stash size estimates
#realworldcrypto
Q: what happens if a client crashes while processing / writing back a query? Does the system stay available, secure?
A: No impact on security if they crash
#realworldcrypto
A: No impact on security if they crash
#realworldcrypto
Next up, 'In Band Key Negotiation: Trusting the Attacker' presented by @SchmiegSophie
#realworldcrypto
#realworldcrypto
@SchmiegSophie 'alg=none' is not the only problem, it's having a alg field at _all_
#realworldcrypto
#realworldcrypto

@SchmiegSophie Isn't just JWT, a common issue elsewhere, the key is associating metadata about how to verify to the ciphertext/signature itself
#realworldcrypto
#realworldcrypto
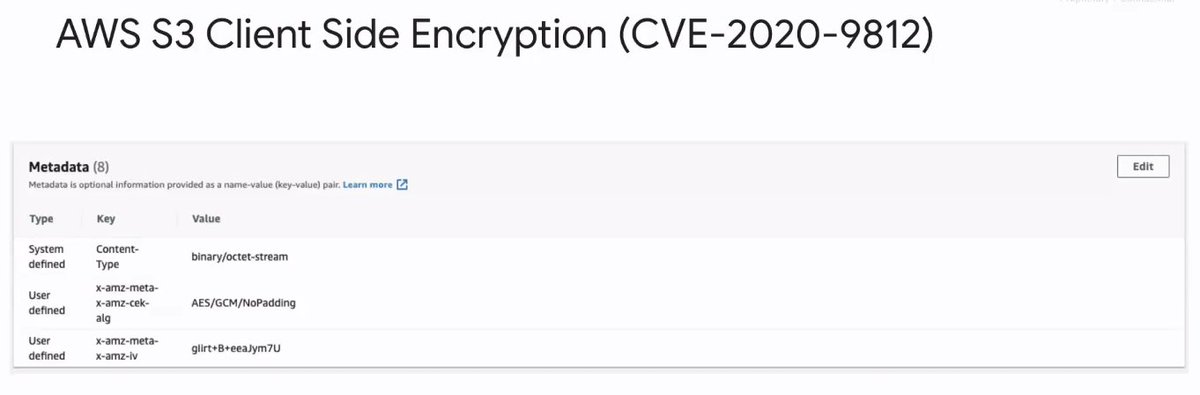
@SchmiegSophie Avoiding this class of problem in Tink (github.com/google/tink): store the metadata with the _key_
All the keys in the keyset are equally trusted
#realworldcrypto
All the keys in the keyset are equally trusted
#realworldcrypto
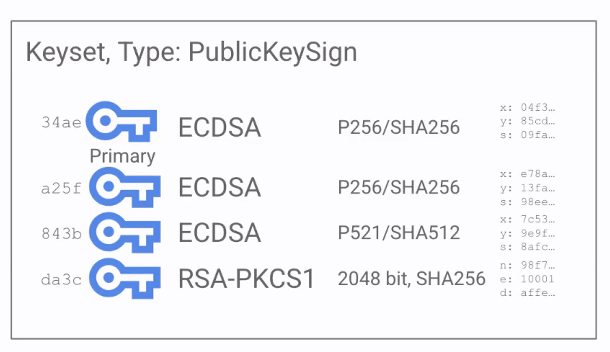
Ciphertext now includes 3 parts:
- version id
- key id
- the rest of the ciphertext/sig
If key gets compromised it must be removed from the key set
#realworldcrypto
- version id
- key id
- the rest of the ciphertext/sig
If key gets compromised it must be removed from the key set
#realworldcrypto
Never trust the ciphertext! It is controlled by the attacker.
Key metadata is part of the key!
Key IDs only within a key set, carefully!
#realworldcrypto
Key metadata is part of the key!
Key IDs only within a key set, carefully!
#realworldcrypto

Q: transport protocols?
A: In an interactive protocol, you negotiate the params before you do any crypto ops
#realworldcrypto
A: In an interactive protocol, you negotiate the params before you do any crypto ops
#realworldcrypto
Q: Can detection of these problems be automated?
A: Determined by the crypto library, often the lib is fine but used in a way that impacts the properties of the larger scheme; automating at the correct scope is tough
#realworldcrypto
A: Determined by the crypto library, often the lib is fine but used in a way that impacts the properties of the larger scheme; automating at the correct scope is tough
#realworldcrypto
Q: Key metadata?
A: algorithm, params to the algorithm, everything you need to turn ~32 random bytes into an actual key
#realworldcrypto
A: algorithm, params to the algorithm, everything you need to turn ~32 random bytes into an actual key
#realworldcrypto
Next up, 'Pancake: Frequency Smoothing for Encrypted Data Stores' presented by Paul Grubbs
#realworldcrypto
#realworldcrypto
• • •
Missing some Tweet in this thread? You can try to
force a refresh