
Here is my little thread about bugs I’ve found in Image3 parsers of various SecureROMs (well, A4 and A6)
None of them are exploitable, but all of them can cause a crash and/or denial-of-service
Why am I posting this? Just for lulz and from hopelessness

None of them are exploitable, but all of them can cause a crash and/or denial-of-service
Why am I posting this? Just for lulz and from hopelessness
https://twitter.com/nyan_satan/status/1178328936926912512?s=20

1) memsetting the whole address space
That’s only for A4 (and maybe lower)
Back in February 2019, someone told me about “SHSH tag length underflow”, that allows “arbitrary memset”. The person failed to tell me which ROM it’s for
That’s only for A4 (and maybe lower)
Back in February 2019, someone told me about “SHSH tag length underflow”, that allows “arbitrary memset”. The person failed to tell me which ROM it’s for
This line validates buffer length of SHSH tag. But if we set shsh_tag->itBufferLength to a high enough value (near 0xFFFFFFFF), the sum will overflow and become a small number, so the check will be passed
SHSH tag data is then erased using memset() even if signature check failed. That very high value of shsh_tag->itBufferLength is passed as length. Such action leads to a hang
github.com/NyanSatan/Imag…
github.com/NyanSatan/Imag…

On A6 (and most likely on any of A5) Apple mitigated that in the following way:
github.com/NyanSatan/Imag…
github.com/NyanSatan/Imag…

Although the expression is arithmetically same, there’s no summing anymore, only subtraction. Underflowing the right part of the expression would have been very convenient, as it will allow arbitrary number of bytes to be memsetted
But unfortunately checks around it are too good (are they actually?)
2) Nested image memory leak
Inside of every Image3’s CERT there’s another little Image3 called “nested image” used for most of constraint validations (CPID, CEPO, PROD, OVRD and etc. go here)
Inside of every Image3’s CERT there’s another little Image3 called “nested image” used for most of constraint validations (CPID, CEPO, PROD, OVRD and etc. go here)

When verify_signature_with_chain() validates a certificate, it also parses its extensions, and one of the extensions - a nested image - is returned to a caller (image3PKIVerifyHash() is a wrapper around verify_signature_with_chain())
github.com/NyanSatan/Imag…
github.com/NyanSatan/Imag…

The caller then passes it to image3InstantiateFromBuffer() with copyBuffer arg set to true. That arg makes it allocate a new buffer on the heap for the image and copy it to there
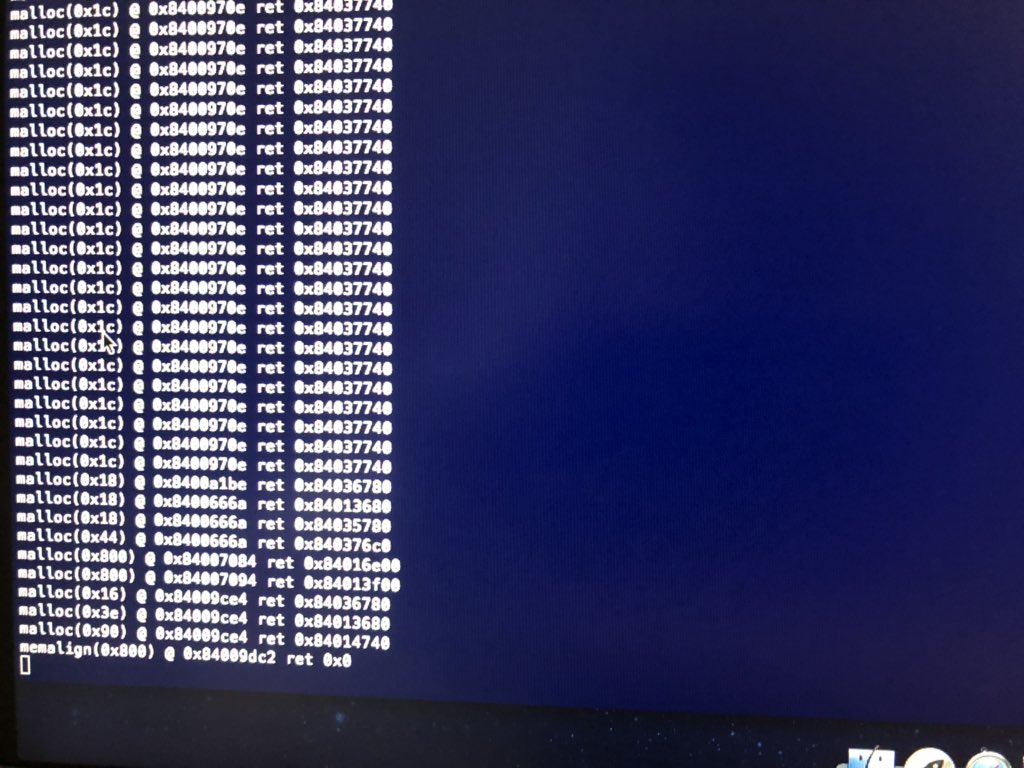
But this buffer is just never freed. By sending correctly signed and yet unpersonalized (or with mismatching constraints) Image3s you can fill out the heap completely 

On A6 it leads to a panic! But don’t worry, it’s just an assertion in malloc() (“malloc() must allocate at least one byte” or something like this) triggered when it cannot allocate anything
A5’s malloc isn’t that fatalistic and just returns NULL. Some USB nonsense fails to be allocated and a device just disconnects 
3) CERT memory corruption
The most interesting bug, discovered only 1.5 months ago
Look at this flow:
github.com/NyanSatan/Imag…
The most interesting bug, discovered only 1.5 months ago
Look at this flow:
github.com/NyanSatan/Imag…

SHSH is stored encrypted on device, so before actual validation it needs to be decrypted. That’s where image3AESDecryptUsingLocalKey() comes to a rescue! It takes just 2 args: the address of buffer and its length:
github.com/NyanSatan/Imag…
github.com/NyanSatan/Imag…

Let’s return to SHSH’s buffer length validation. As you can see it’s only validated not to overlap Image3’s sizeNoPack (whole Image3’s meaningful data length minus header), but not to overlap CERT that lies right after SHSH!
github.com/NyanSatan/Imag…
github.com/NyanSatan/Imag…
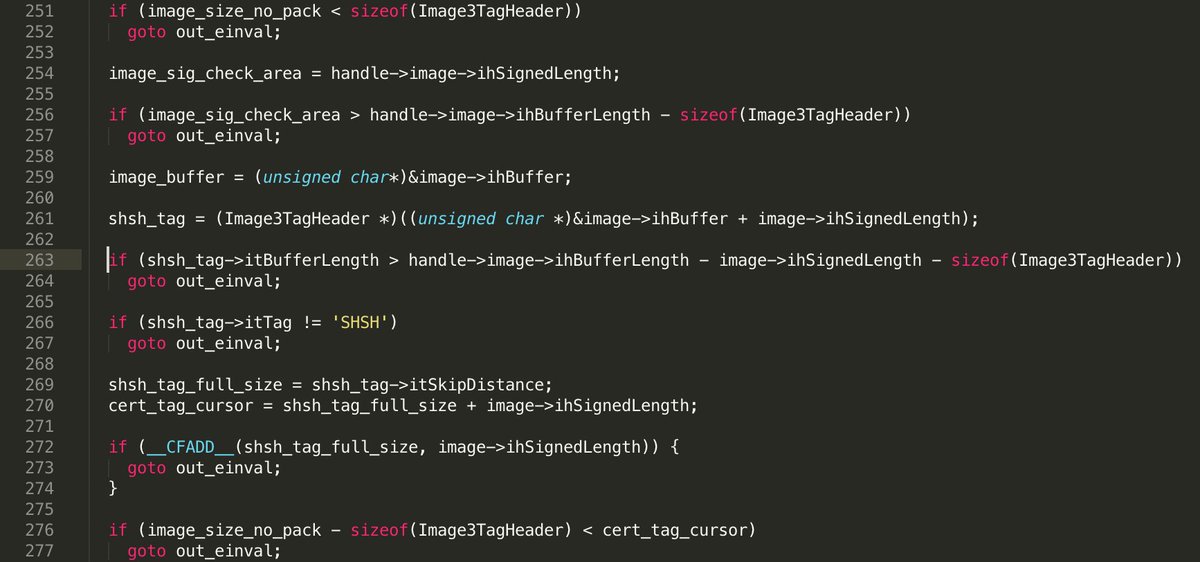
So by setting shsh_tag->itBufferLength to a high enough value, but not that high to overflow sizeNoPack bounds, you can corrupt CERT tag header and data!
For example, you can make CERT’s buffer length value a very big number, overlaping the Image3, load area, SRAM itself…
By constructing malformed certificate I managed to trigger ARM prefetch abort exception (it tried to read somewhere far behind the SRAM bounds)
By constructing malformed certificate I managed to trigger ARM prefetch abort exception (it tried to read somewhere far behind the SRAM bounds)
Unfortunately, certificate data isn’t modified in any way while validation, so that bug doesn’t seem to be very useful. Maybe there’s a point to look inside of PKI code?
On the other hand, someone told me I’m on “the right path”, when I told them about this discovery, so maybe it’s not that useless in the end?
Anyway, I think I'm done with all this nonsense, completely this time. I struggle with F20.0 and people with F20.0 are usually dumber than healthy people - I feel that every day I live this frigging life
So finding that untethered iBoot-1145.3(.3) 0day is just not my fate
And all the people who could help me with that are so fucking tired of my annoyance that no longer even talk to me
And all the people who could help me with that are so fucking tired of my annoyance that no longer even talk to me
• • •
Missing some Tweet in this thread? You can try to
force a refresh










