Were the Chief of the Armed forces of #Syria and Suheil al-Hassan, commander of the “Tiger Forces," present in a command post overlooking a city shortly before it was hit by a chlorine attack?
@N_Waters89 investigates.
bellingcat.com/news/2020/04/1…
@N_Waters89 investigates.
bellingcat.com/news/2020/04/1…
@N_Waters89 Last week, the OPCW’s IIT stated that there are reasonable grounds to believe that a hospital in the Syrian town of al Lataminah was attacked with chlorine on March 25, 2017
We wrote about it.
bellingcat.com/news/mena/2017…
We wrote about it.
bellingcat.com/news/mena/2017…
@N_Waters89 Thanks to a SANA News video, we know that on the same date, a delegation of generals, including Suheil al Hassan, was present in a command post overlooking al Lataminah.
Thankfully, @syrian_archive grabbed a copy before it was deleted from YouTube
Thankfully, @syrian_archive grabbed a copy before it was deleted from YouTube
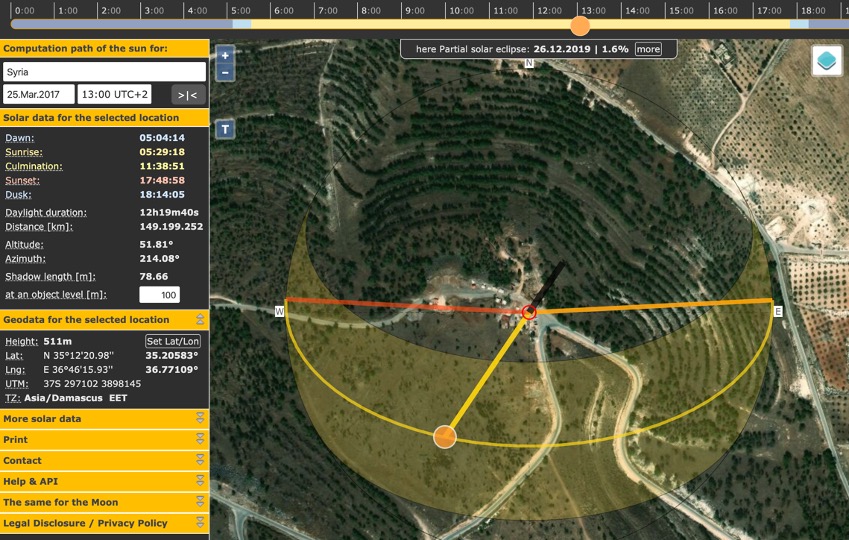
@N_Waters89 @syrian_archive Here's a neat trick otherwise known as #chronolocation
By examining shadows seen in the video we can establish what time certain sections were filmed.
This initial parade took place at around 1300 local time (this is a rough estimate)

By examining shadows seen in the video we can establish what time certain sections were filmed.
This initial parade took place at around 1300 local time (this is a rough estimate)

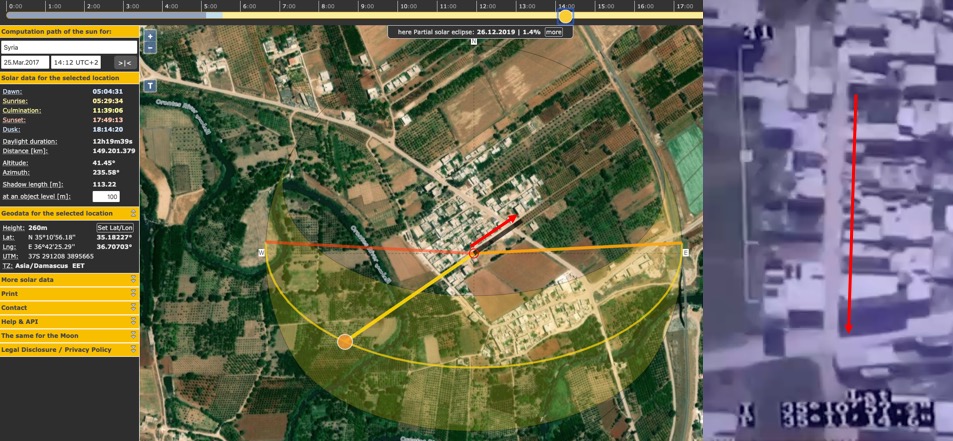
@N_Waters89 @syrian_archive As @N_Waters89 notes,
At one point an ISTAR feed is seen, showing another village in Hama.
If this feed was live, it indicates the time was 1415. We can be more confident about this time than the parade section, as the buildings provide us with shadow reference points

At one point an ISTAR feed is seen, showing another village in Hama.
If this feed was live, it indicates the time was 1415. We can be more confident about this time than the parade section, as the buildings provide us with shadow reference points

@N_Waters89 @syrian_archive You know what else that video contains? Watches!
One seems to show the time at 1315
We used one of
@topazlabs sharpening tools on Gen. Ayoub’s watch
The result looks consistent with our initial assessment.
NOTE: this is the interpretation of the tool, using a similar watch

One seems to show the time at 1315
We used one of
@topazlabs sharpening tools on Gen. Ayoub’s watch
The result looks consistent with our initial assessment.
NOTE: this is the interpretation of the tool, using a similar watch


@N_Waters89 @syrian_archive @topazlabs Take into account the flight time of the helicopter from Hama air base, the time to conduct preflight checks & load chlorine munitions...
...And it appears very likely that these generals were present in the command post as the chlorine attack on al Lataminah was being prepared.
...And it appears very likely that these generals were present in the command post as the chlorine attack on al Lataminah was being prepared.

@N_Waters89 @syrian_archive @topazlabs You know what's extra interesting about this?
The presence of Suheil al Hassan.
The unit he commands, the Tiger Forces, have previously been linked to the use of helicopter-borne chlorine munitions by @GPPi
gppi.net/2019/02/17/the…
The presence of Suheil al Hassan.
The unit he commands, the Tiger Forces, have previously been linked to the use of helicopter-borne chlorine munitions by @GPPi
gppi.net/2019/02/17/the…
@N_Waters89 @syrian_archive @topazlabs @GPPi Please read the article for more information!
We would like to thank @tobiaschneider for drawing our attention to this event
And @Timmi_Allen for aiding with image analysis
bellingcat.com/news/2020/04/1…
We would like to thank @tobiaschneider for drawing our attention to this event
And @Timmi_Allen for aiding with image analysis
bellingcat.com/news/2020/04/1…
• • •
Missing some Tweet in this thread? You can try to
force a refresh