• UTS: System identifiers isolation
• PID: PID space isolation
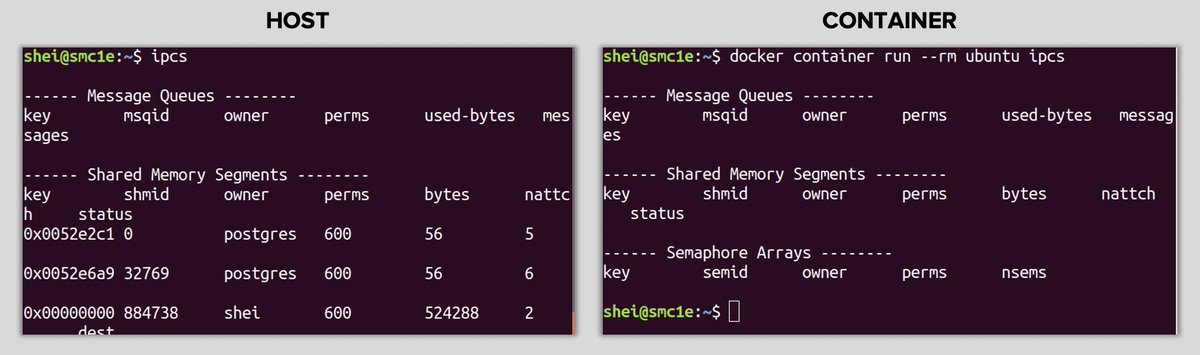
• IPC: IPC resources isolation
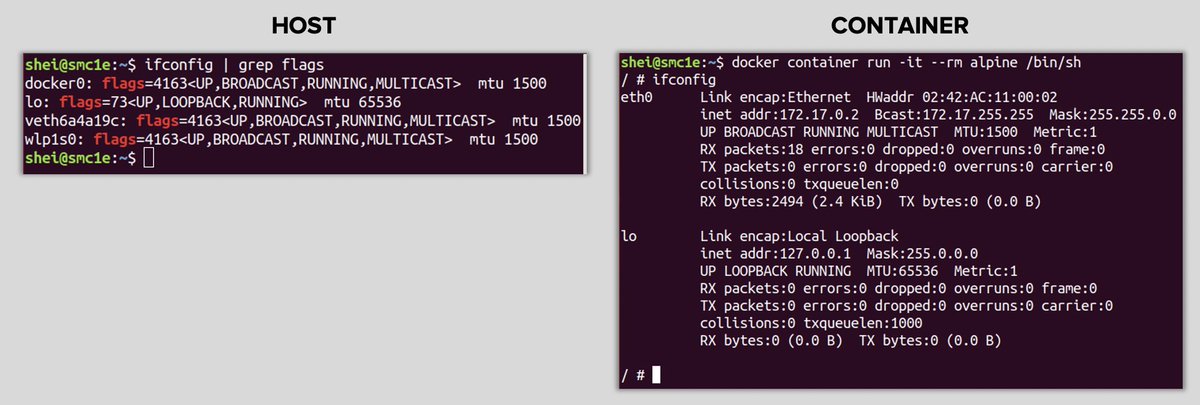
• NET: network interfaces isolation
• USER: User & Group ID spaces
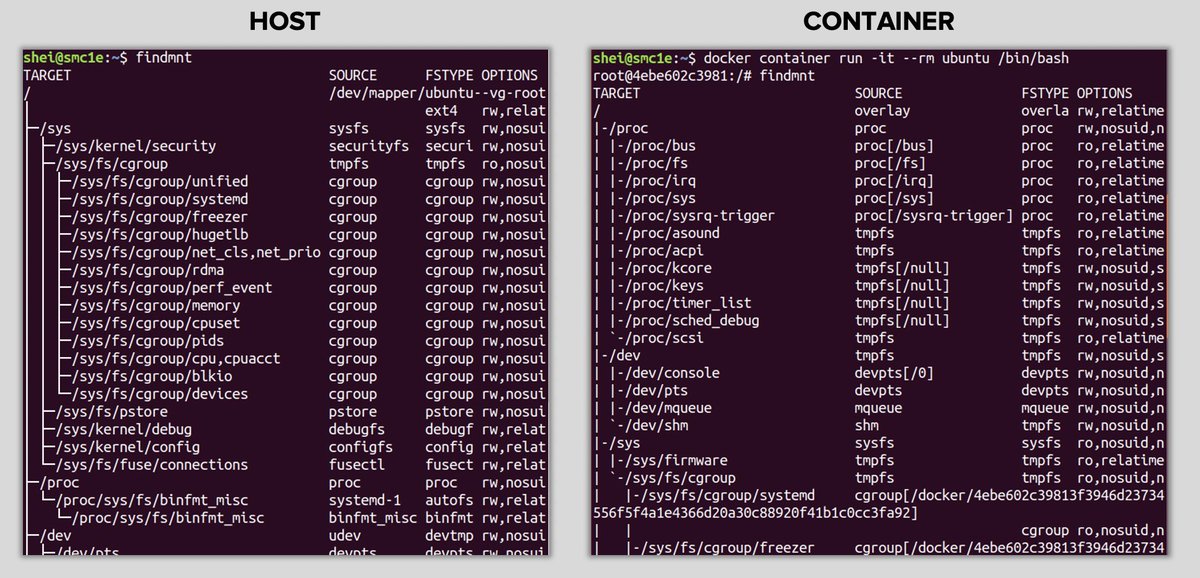
• Mount namespace: filesystem mount points isolation
A process running with its own UTS namespace can change the hostname and domain names for it and its children without altering the names of the host system or other processes. In this way...
Being super brief, IPC is a mechanism that allows processes to communicate each other. On Linux, the communication can be done through shared memory segments, semaphores and message queues.
It is possible to make use of the USER namespace in Docker, but it is not enabled by default. From a security viewpoint it is very interesting, I will talk more about this soon.
If you want to learn more about Docker security, we will give trainings (online format) at:
- Black Hat (english): blackhat.com/us-20/training…
- Eko (spanish): ekoparty.org/eko16/training…