It didn't take long till I got a direct contact and was directed to a private VDP on the major bounty platform. I agreed to use it (which meant NDA) because my contact was trustworthy
Expectedly I was reminded in the...
The fun thing about this reminder: It also stated that a team was working on a fix for this issue (which was not applicable, right?????).
After some back and forth, I had a TelCo with the ...
After more than TWO MONTHS a "communication specialist" from the bounty platform reached out to me.
While he admitted that it took a long...
- vulnerabilities unpatched
- customers not informed
- I'm not allowed to talk about in detail
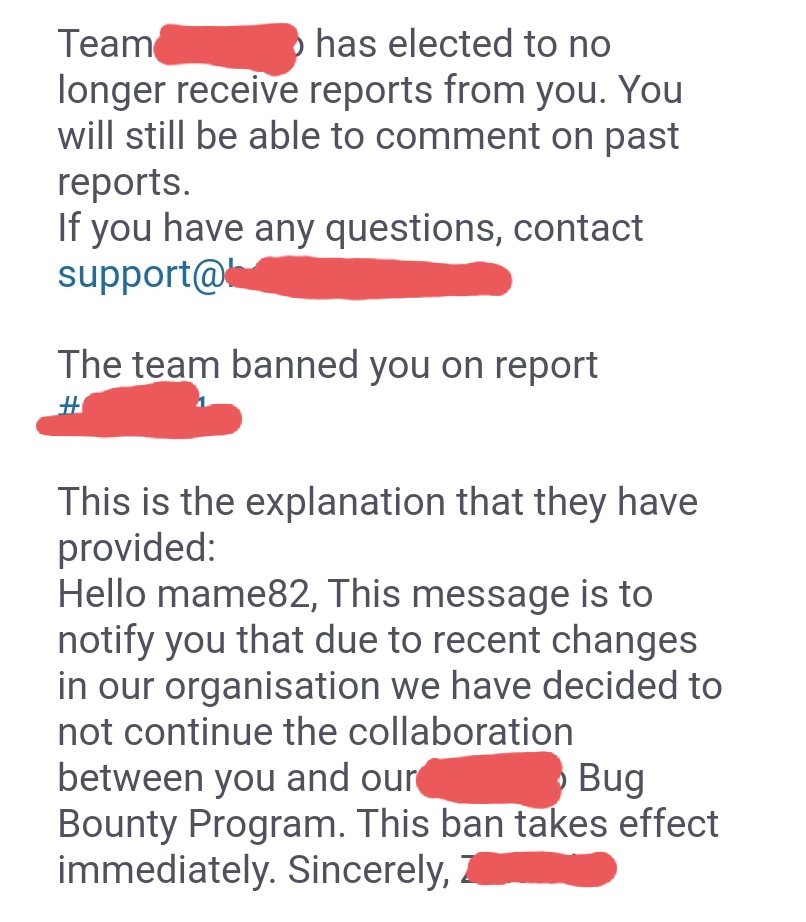
- involved communication partners on company end seem to be subject of "change ... in organisation"