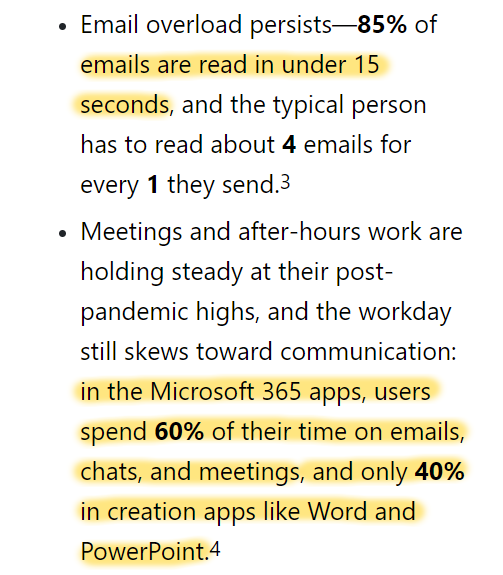
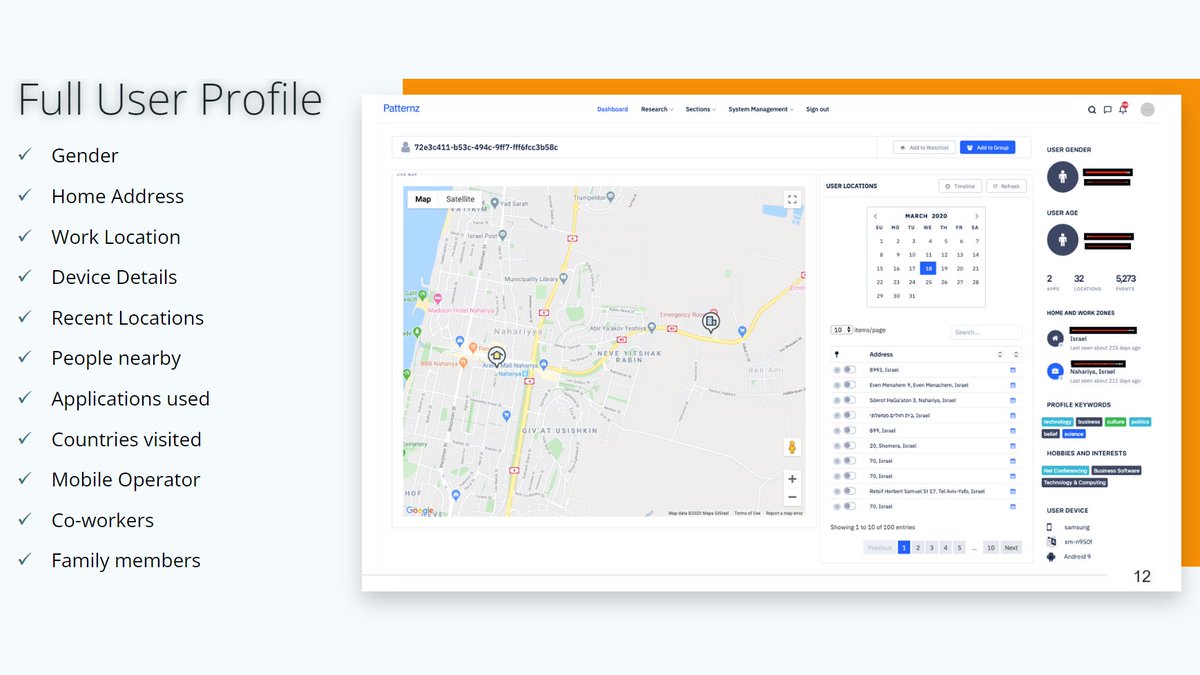
"The personal details of millions of people around the world have been swept up in a database compiled by a Chinese tech company with reported links to the country’s military and intelligence networks, according to a trove of leaked data" theguardian.com/world/2020/sep…
Data includes "dates of birth, addresses, marital status, along with photographs, political associations, relatives", data scraped from social media and "information which appears to have been sourced from confidential bank records, job applications".
abc.net.au/news/2020-09-1…
abc.net.au/news/2020-09-1…

Zhenhua Data looks like the Chinese version of US firms such as Babel Street, which sold its social media monitoring and data analytics products "to nearly every major defense, national-security or law-enforcement agency" in the US.
babelstreet.com
https://twitter.com/WolfieChristl/status/1285149707493421056
babelstreet.com

"The database is constructed around numerous existing databases or platforms and harvested into one large database with multiple points of overlap. Significant amounts of data comes from the Dow Jones owned database Factiva"
Summary of findings on SSRN:
papers.ssrn.com/sol3/papers.cf…
Summary of findings on SSRN:
papers.ssrn.com/sol3/papers.cf…

"Large amounts of the data was open source data ... 10-20% of the data was not publicly or easily available".
It includes "public sector employee records", "from known politicians to political aides to low level military personnel", as well as data on "organized crime figures".
It includes "public sector employee records", "from known politicians to political aides to low level military personnel", as well as data on "organized crime figures".
Zhenhua Data "builds a 'relational database', which records and describes associations between individuals, institutions, and information ... weaving in public or sentiment analysis around these targets, Zhenhua offers 'threat intelligence services'."
https://twitter.com/SilvermanJacob/status/1305314241885462529
Basically, like a combination of social media intel, cybersec/threat intelligence and data aggregation from public records and databases such as World Check, plus perhaps from some other data brokers, in combination with some Palantir-style network analysis capabilities.
"When a Globe and Mail reporter visited [the company's office in Shenzhen], three people sat at desks in what appeared to be a converted studio apartment, with the door open to the bathroom".
Thereafter, the "company’s website became inaccessible".
theglobeandmail.com/world/article-…
Thereafter, the "company’s website became inaccessible".
theglobeandmail.com/world/article-…
"The company, led by a former IBM data centre management expert, has also described its work online in job postings, LinkedIn records, blog articles and software patents. One employee described work 'mining the business needs of military customers for overseas data'."
"Stephanie Carvin, a former national security analyst who viewed the database on behalf of The Globe and Mail ... said it wasn’t clear whether this was a database used by Chinese intelligence – or just a database created by a company hoping to sell it to Chinese intelligence"
Zhenhua Data seems to be a tiny company. However, it is "believed to be owned by China Zhenhua Electronics Group which in turn is owned by state-owned China Electronic Information Industry Group (CETC), a military research company", according to ABC: abc.net.au/news/2020-09-1…
Oh, @Jeremy_Kirk writes "this data was sitting on an unsecured elasticsearch cluster for ages. Hundreds of gigabytes. For anyone to download. Including me in January"
https://twitter.com/Jeremy_Kirk/status/1305327734894112768
Some more interesting facts in his blog post:
databreachtoday.com/blogs/does-thi…
(I totally disagree with his assessment of gathering and combining publicly accessible personal information as generally not a problem)
databreachtoday.com/blogs/does-thi…
(I totally disagree with his assessment of gathering and combining publicly accessible personal information as generally not a problem)

❌ "This is nothing new"
❌ "Chinese surveillance omg, we'd never do this"
❌ "Nothing to see here, just China bashing, we're doing the same in the US"
✅ Scrutinize the intersection of govt+commercial surveillance both in China/US, put it into the context of key developments...
❌ "Chinese surveillance omg, we'd never do this"
❌ "Nothing to see here, just China bashing, we're doing the same in the US"
✅ Scrutinize the intersection of govt+commercial surveillance both in China/US, put it into the context of key developments...
(and, of course, not only in the US and Five Eyes countries, but also in the EU and in other regions)
• • •
Missing some Tweet in this thread? You can try to
force a refresh