Oooh fun one. Okay so let's start with literally MetaMask. Meaning your actual legit MetaMask extension is actually used in order to get the keys, rather than the keys that you generated with MetaMask or use in MetaMask are compromised without MetaMask involvement.
https://twitter.com/lampiao_1/status/1307050835990503427
1. Attacker gets physical access to your device.
e.g. Evil maid attack. Theft. Leaving it unlocked at starbucks.
MetaMask takes measures in how they store secrets + auto lock state. But honestly if someone targeting you and your crypto gets your physical device, RIP. ☠️⚰️🥀
e.g. Evil maid attack. Theft. Leaving it unlocked at starbucks.
MetaMask takes measures in how they store secrets + auto lock state. But honestly if someone targeting you and your crypto gets your physical device, RIP. ☠️⚰️🥀
2. Full remote access to your device.
Most commonly, Teamviewer. Hacker walks thru the door you left open & grabs your shit.
Here's an old example of exactly that. Bonus insights into securing a product like MetaMask/MyCrypto/MEW in full reddit thread.
Most commonly, Teamviewer. Hacker walks thru the door you left open & grabs your shit.
Here's an old example of exactly that. Bonus insights into securing a product like MetaMask/MyCrypto/MEW in full reddit thread.
https://twitter.com/myetherwallet/status/839527962349182976?s=19
3. 0-day in OS or browser that allows access to memory, keyboard, chrome storage, etc.
Like zdnet.com/article/google… that targets your crypto and/or MetaMask.
While it's rare to see super sophisticated 0-days go for crypto, it's not unheard of. See link.medium.com/j4Nvhmw4T9
Like zdnet.com/article/google… that targets your crypto and/or MetaMask.
While it's rare to see super sophisticated 0-days go for crypto, it's not unheard of. See link.medium.com/j4Nvhmw4T9
3b. It should be noted that it's not that 0-days *won't* go for crypto. It's just that historically they have had other fish to fry.
But you know...North Korea is a thing and they fucking love crypto.
google.com/search?q=lazar…
But you know...North Korea is a thing and they fucking love crypto.
google.com/search?q=lazar…
4. Malware or other not 0-day stuff that either targets your Metamask or crypto/secrets in general/clipboard or keyboard or something. But that's slightly out of scope for "literally your Metamask" and pretty uninteresting. Pro-tip: don't limewire porn, kids.
5. Far more interesting is a vulnerability in MetaMask rather than chrome storage or memory. The aforementioned malware, if targeting MetaMask specifically, would take advantage of this...if it existed.
5b. Since a vulnerability that leaks MM seeds has never existed as far as I know...we must look elsewhere for what it may look like.
(Ps: @danfinlay have there ever been any leaky vulns that weren't exploited, were disclosed responsibly, or in the very early days?)
(Ps: @danfinlay have there ever been any leaky vulns that weren't exploited, were disclosed responsibly, or in the very early days?)
5c. Password managers are the most obvious place to look as they are full of secrets, widely used and really sophisticated security researches go after them.
Here is a good article with tons of links to vulns in various pw managers over the years
zdnet.com/article/critic…
Here is a good article with tons of links to vulns in various pw managers over the years
zdnet.com/article/critic…
5d. Note: you are better off using a pw manager than not. Most, if not all, the scary articles about their vulns are from security researchers, NOT exploits in the wild.
Do not delete your pw manager (but maybe don't put your single signer admin of the defi treasury key there.)
Do not delete your pw manager (but maybe don't put your single signer admin of the defi treasury key there.)
5e. Okay. Most of the pw manager exploits 1) access plaintext pws in memory 2) single secret leaks to unauthorized sites.
The former is something that could happen w MM. That's why the lock exists. Your seed is (double) encrypted in storage but you decrypt to send. That's in mem
The former is something that could happen w MM. That's why the lock exists. Your seed is (double) encrypted in storage but you decrypt to send. That's in mem
5f. The later, credential leaks, don't apply as MetaMask never sends or inserts into the dom or even typically displays your seed or keys. There's no "give this dapp my key" function in MM like there is in a pw manager.
5g. I consider this type of vuln to be unlikely on a day-to-day basis but 50/50 chance we see one in the next 18 months. It would be quickly discovered and mitigated if in the wild and it's most likely to be discovered and disclosed by sec researcher before exploited.
5h. This should scare you I suppose but it's INSANELY LOW on my list of ways youll realistically have your crypto fucked out of you. Like maybe a <1% chance.
Mostly bc there's 1000 other ways to take your crypto that require less effort, no skill, and can't be patched in <24hrs.
Mostly bc there's 1000 other ways to take your crypto that require less effort, no skill, and can't be patched in <24hrs.
6a. Malicious code pushed by fake "MetaMask team" to legit MM extension.
The fact this hasn't yet occured and MM has had 1m+ active installs since 2017 means it's not likely to occur. Testament to teams security mindedness. Ways it could occur:
The fact this hasn't yet occured and MM has had 1m+ active installs since 2017 means it's not likely to occur. Testament to teams security mindedness. Ways it could occur:
6b. Most likely is the compromise of admin credentials of thing where code is. GitHub. Google Extension store thing. The thing that builds or signs the code prior to giving it to google. Etc.
Individuals who add code to MetaMask but don't admin it could be compromised but...
Individuals who add code to MetaMask but don't admin it could be compromised but...
6c. ...it's relatively easy to mitigate by protecting branches, reviewing PRs, etc. Basically: don't let random people force push to master. Don't let master get to google without reviewing code and commits within master.
7. Slightly diff is malicious code being snuck into the codebase by outside maintainer. Again, easy to mitigate and MM has and will continue to do.
If anyone has a good link to someone attempting to sneak in code, plz share. There was an attempt once on MEW but I can't find it.
If anyone has a good link to someone attempting to sneak in code, plz share. There was an attempt once on MEW but I can't find it.
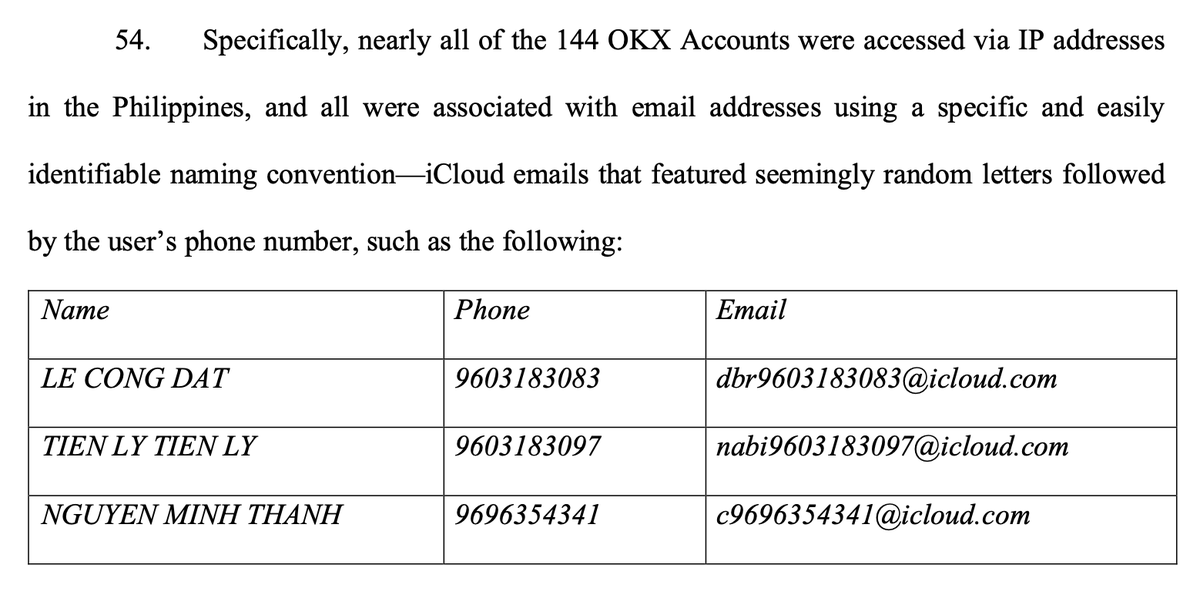
8. Most terrifying but not that likely but totally possible and fucking hard as fuck to truly mitigate is the compromise of fucking dependencies that are ultimately included in the MM codebase, unbeknownst to anyone.
Seriously just FUCK this type of attack.
Seriously just FUCK this type of attack.
8b. Typically known as "supply chain attacks" it does happen and it does happen against crypto companies!!! When they do happen in the wild, the security community goes nuts bc the attack is most often theoretical (and hard to mitigate). One example is kaspersky.com/blog/copay-sup…
8c. More on the attack in general: blog.acolyer.org/2019/09/30/sma…
These are both npm examples, but there have been ones in the wild for python's pip as well.
These are both npm examples, but there have been ones in the wild for python's pip as well.
8d. But hey. If there's literally anyone who could be fucked by this one but maybe wont, it's literally MetaMask. Why? Theyve been building an epic next-level thing called LavaMoat to address this attack vector for the last few years. 🤯
https://twitter.com/metamask_io/status/1278702444218732544?s=19
8e. It's seriously epic. (and there's more resources and examples in their readme too.) github.com/LavaMoat/LavaM… 
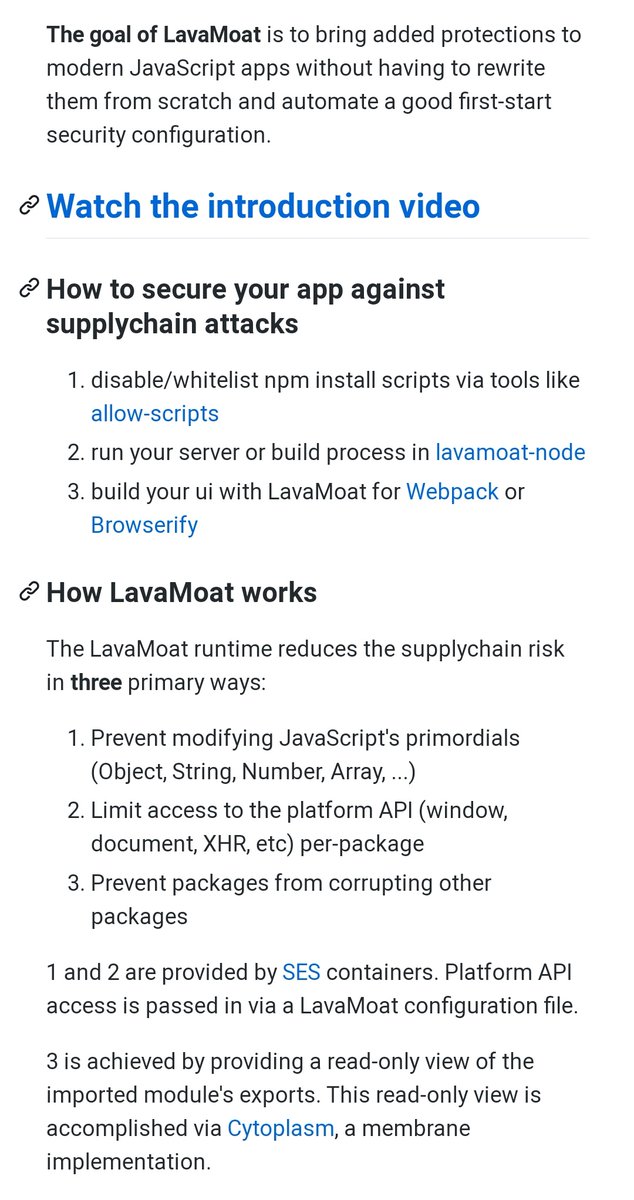
8f. Oops forgot about this one from June 2019 which really emphasizes how deep these dep roots go.
Add dep electron notify to easydex > add easydex as dep of Agama wallet -> add malicious code to electron notify
blog.npmjs.org/post/185397814…
Add dep electron notify to easydex > add easydex as dep of Agama wallet -> add malicious code to electron notify
blog.npmjs.org/post/185397814…
8e. Amazingly, after spending months orchestrating & pushing good code to sneak in bad code...he sent the keys to a publicly accessible server.
So the wallet devs were able to white-hat 90% of funds..using the seeds on the hackers public box. 🙃
komodoplatform.com/update-agama-v…
So the wallet devs were able to white-hat 90% of funds..using the seeds on the hackers public box. 🙃
komodoplatform.com/update-agama-v…
9. Slightly diff is same attack but entry occurs thru a compromised thing you've put in your app / on your site. Recently a Moonpay endpoint on cloudflare was compromised to add malicious code targeting Iota's desktop wallet.
blog.iota.org/trinity-attack…
(really good post mortem!)
blog.iota.org/trinity-attack…
(really good post mortem!)
9b. It was patched by...wait for it...not letting a third party url serve you code that your app then runs willy-nilly. No one else who used Moonpay was affected bc none of them served the necessary lib thru a url.
It was also patched by pausing Iota. You know. 🤷
It was also patched by pausing Iota. You know. 🤷
9c. Exchange Gate.io was compromised when hacker compromise StatCounter–analytics provider used by https://t.co/5vX3gQyOjb and 2m (!?) others)
Only https://t.co/5vX3gQyOjb was targeted. The script replaced BTC addresses on withdraw page.
welivesecurity.com/2018/11/06/sup…
Only https://t.co/5vX3gQyOjb was targeted. The script replaced BTC addresses on withdraw page.
welivesecurity.com/2018/11/06/sup…
9d. Being a dapp doesn't make you immune. Here's the version of an injection attack:
EtherDelta loads erc-20 tokens
Token contracts have token's name
EtherDelta gets name from chain to show user
Contract's name is actually code to steal users' keys
medium.com/@zhongqiangc/c…
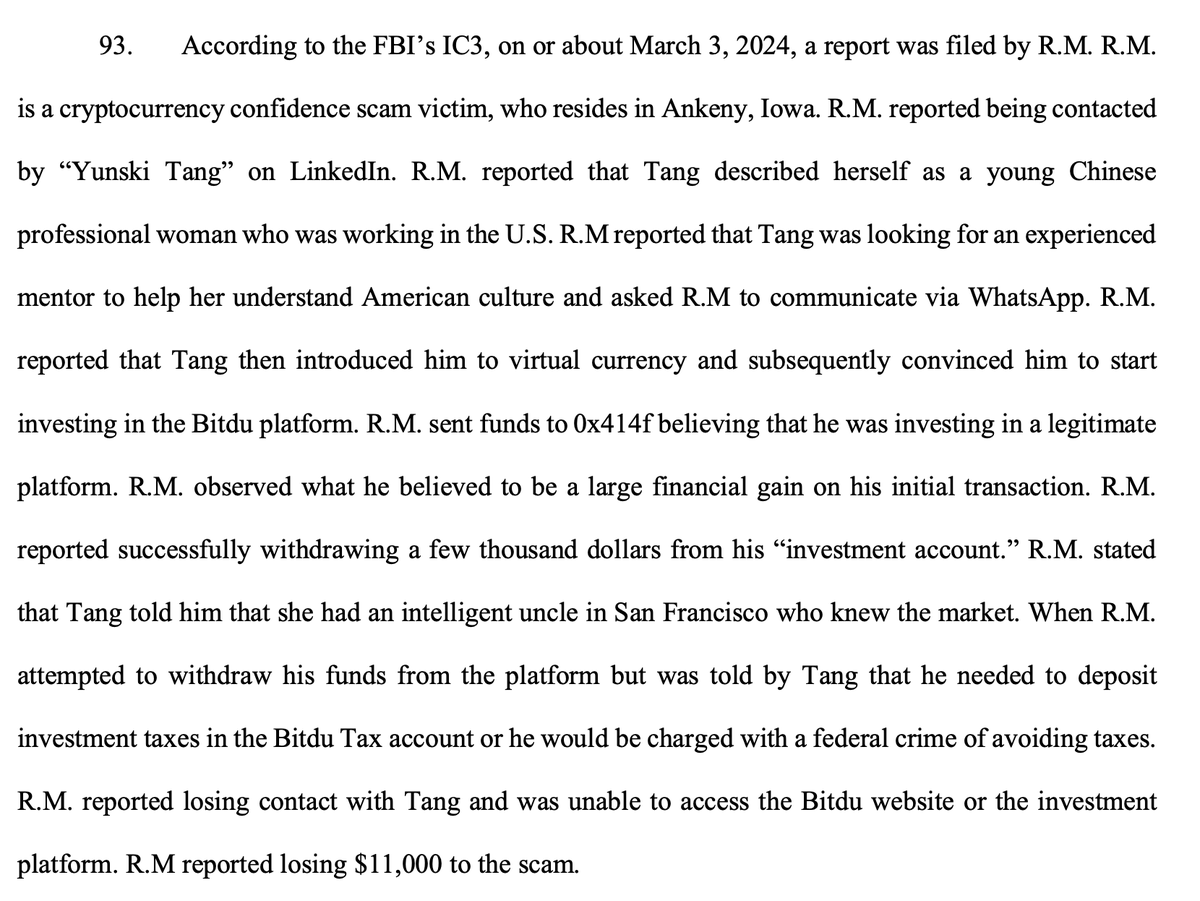
EtherDelta loads erc-20 tokens
Token contracts have token's name
EtherDelta gets name from chain to show user
Contract's name is actually code to steal users' keys
medium.com/@zhongqiangc/c…
9e. And neither does being a crypto exchange adding shitcoins willy nilly a la cryptsy + lucky7coin.
github.com/alerj78/lucky7…
These really aren't issues for MetaMask but they could be. But MetaMask avoids these easily.
github.com/alerj78/lucky7…
These really aren't issues for MetaMask but they could be. But MetaMask avoids these easily.
10. Last one for now is KEY DERIVATION. Again, like the above, MetaMask *could* be affected by this but *isn't.*
Any wallet can (and many have) derived mismatched pub/priv keys. Usually bc pks are assumed to be 32 bytes but they are 31 bytes 1/128 (or 1/256?) times.
Any wallet can (and many have) derived mismatched pub/priv keys. Usually bc pks are assumed to be 32 bytes but they are 31 bytes 1/128 (or 1/256?) times.
Here's all you need to know about cryptography to understand this.
12/24 word seed phrase + fancy math + dpath = private key
pk + fancy math = public key
public key + fancy math = address
Alls swell so long as you DON'T FUCK UP THE FANCY MATH
12/24 word seed phrase + fancy math + dpath = private key
pk + fancy math = public key
public key + fancy math = address
Alls swell so long as you DON'T FUCK UP THE FANCY MATH
2015 (reported originally by @ricmoo of ethers-js) reddit.com/r/ethereum/com…
+ lightwallet in '16
github.com/ConsenSys/eth-…
bc bitpay was wrong
github.com/bitpay/bitcore…
+ ian coleman in '17
github.com/iancoleman/bip…
bc bitpay/copay didnt fix that thing in '16
github.com/bitpay/copay/i…
+ lightwallet in '16
github.com/ConsenSys/eth-…
bc bitpay was wrong
github.com/bitpay/bitcore…
+ ian coleman in '17
github.com/iancoleman/bip…
bc bitpay/copay didnt fix that thing in '16
github.com/bitpay/copay/i…
To know if your app is affected (either in gen or importing) here's test keys that are < 32 bytes:
github.com/Gustav-Simonss…
and
radar blur cabbage chef fix engine embark joy scheme fiction master release
on m/44'/60'/0'/0
should be
0xac39b311dceb2a4b2f5d8461c1cdaf756f4f7ae9
github.com/Gustav-Simonss…
and
radar blur cabbage chef fix engine embark joy scheme fiction master release
on m/44'/60'/0'/0
should be
0xac39b311dceb2a4b2f5d8461c1cdaf756f4f7ae9
To complicate things, 12/24 word seed phrases have an add'l step where zeros may be dropped. If fancy math is diff across libs, it results in diff addresses being shown.
This DOES NOT result in *actual* loss like it does if in private -> public step.
This DOES NOT result in *actual* loss like it does if in private -> public step.
MetaMask and lightwallet figured this out in '16. And reported to bitpay. Who didn't fix it. 🤦♀️
github.com/MetaMask/metam…
medium.com/@alexberegszas…
github.com/bitpay/bitcore…
github.com/MetaMask/metam…
medium.com/@alexberegszas…
github.com/bitpay/bitcore…
The easiest way to not be the victim of this bug is to always send funds in AND out of a wallet before loading it up with your life savings. If you can successfully send out today, you will be tomorrow, even if its a bitch to do so.
The other way keys can be poorly derived is by not using enough entropy. Not enough entropy = private keys "mined" or brute-forced.
Ethereum has avoided randomness issues in keys, mostly bc devices + underlying crypto methods were better and more trusted when Ethereum launched.
Ethereum has avoided randomness issues in keys, mostly bc devices + underlying crypto methods were better and more trusted when Ethereum launched.
2015
reddit.com/r/Bitcoin/comm…
> random.org started enforcing HTTPS
> returns "301"
> the entropy has actually been the error message not a random number meaning everyone affected got the key for
1Bn9ReEocMG1WEW1qYjuDrdFzEFFDCq43F 😬
reddit.com/r/Bitcoin/comm…
> random.org started enforcing HTTPS
> returns "301"
> the entropy has actually been the error message not a random number meaning everyone affected got the key for
1Bn9ReEocMG1WEW1qYjuDrdFzEFFDCq43F 😬
Another Iota wallet was also affected by not-enough-entropy.
In 2018.
saturn.network/blog/iota-hack…
This is due to Iota rolling their own crypto and so wallets rolled their own crypto and...just dont.
In 2018.
saturn.network/blog/iota-hack…
This is due to Iota rolling their own crypto and so wallets rolled their own crypto and...just dont.
The other way to not have enough entropy is if users can choose their key.
Brain wallets are bad. Period. @ryancdotorg is the expert: allprivatekeys.com/brain-wallet
Ethereum has luckily mostly avoided this except that one time Roman argued with Ryan lolol gitter.im/ethereum/gener…
Brain wallets are bad. Period. @ryancdotorg is the expert: allprivatekeys.com/brain-wallet
Ethereum has luckily mostly avoided this except that one time Roman argued with Ryan lolol gitter.im/ethereum/gener…
You will always underestimate users. Always. Always. Do not let them generate or unlock low entropy shit. If they can, they will, and they will lose. Just like the guy who used private key 00000....000001. 🤦♀️
github.com/MyEtherWallet/…
github.com/MyEtherWallet/…
I'll leave you w/ this.
Keys have to enter memory to sign a transaction and your memory is ultimately not safe IF there is a high enough incentive to get it.
MetaMask is your daily driver, NOT your life savings. It's safe to a point. Paper is your fren.

Keys have to enter memory to sign a transaction and your memory is ultimately not safe IF there is a high enough incentive to get it.
MetaMask is your daily driver, NOT your life savings. It's safe to a point. Paper is your fren.
https://twitter.com/ryancdotorg/status/1025891193039642625

• • •
Missing some Tweet in this thread? You can try to
force a refresh