BREAKING: Multiple platforms took down assets from various Russian info ops today.
The ops did *not* primarily target the US election. Much more on RU strategic concerns.
@Facebook kicked this off. Reports by @Graphika_NYC and @DFRLab to follow.
about.fb.com/news/2020/09/r…
The ops did *not* primarily target the US election. Much more on RU strategic concerns.
@Facebook kicked this off. Reports by @Graphika_NYC and @DFRLab to follow.
about.fb.com/news/2020/09/r…
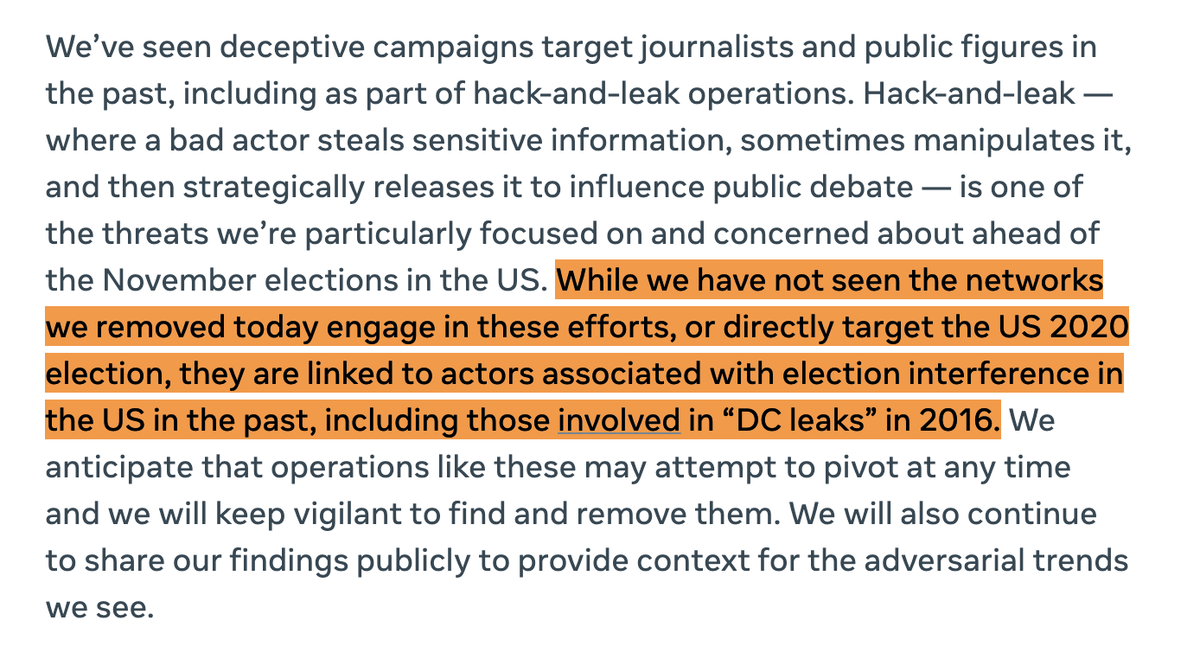
The FB investigation took down several different sets of inauthentic assets, including Russian military and individuals associated with the IRA.
They have a track record of election interference. Cleaning their assets out before the U.S. election seems… prudent.
They have a track record of election interference. Cleaning their assets out before the U.S. election seems… prudent.
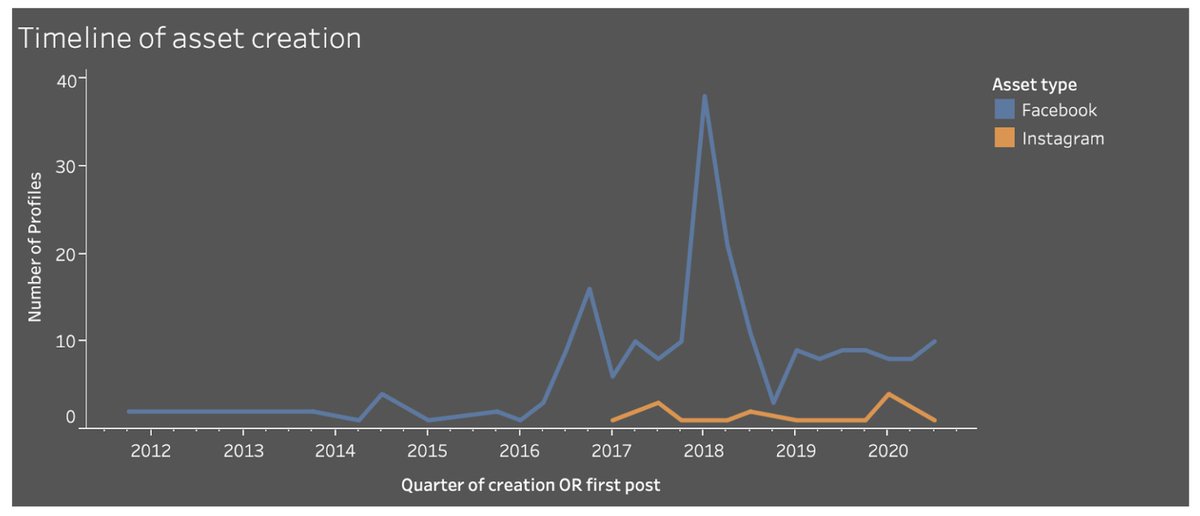
The @Graphika_NYC team looked at the Russian military assets. About 300 of them, activity ranging from 2013 to 2020.
It wasn’t one coherent set: more like different clusters at different times and looking in different directions, north, south, east and west.
It wasn’t one coherent set: more like different clusters at different times and looking in different directions, north, south, east and west.
On Facebook, there were various fake assets. Some posed as journalists. Others were batch-created, with stolen profile pics, serving as amplifiers.
Fake accounts, making friends with each other.
Fake accounts, making friends with each other.

But this was a cross-platform effort. Some of the networks - there were several - ran the same persona across multiple platforms. Trying to make them look more credible? 
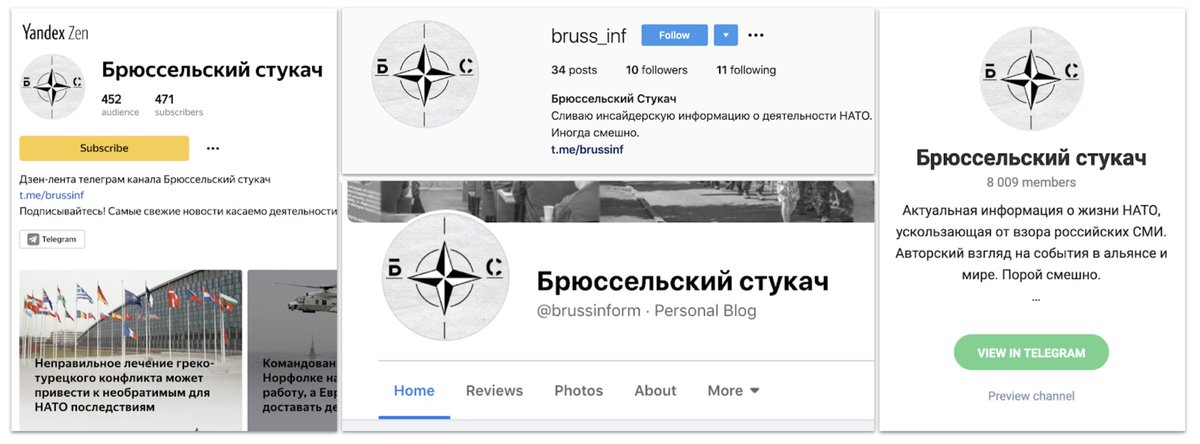
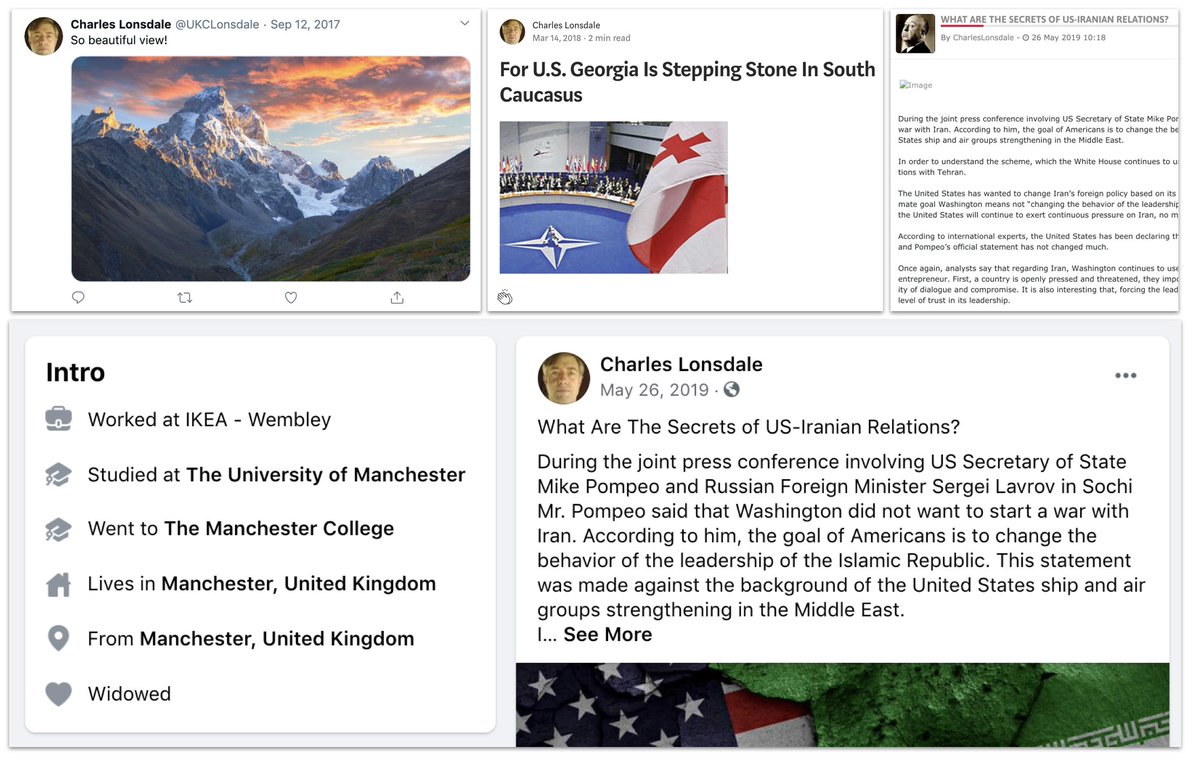
This was an interesting one. Pamela Spenser, until recently on Facebook, Medium and Twitter.
The persona wrote a lot about Syria, from a very pro-Russian stance.
Personally, she reminds me of Alice Donovan.
The persona wrote a lot about Syria, from a very pro-Russian stance.
Personally, she reminds me of Alice Donovan.
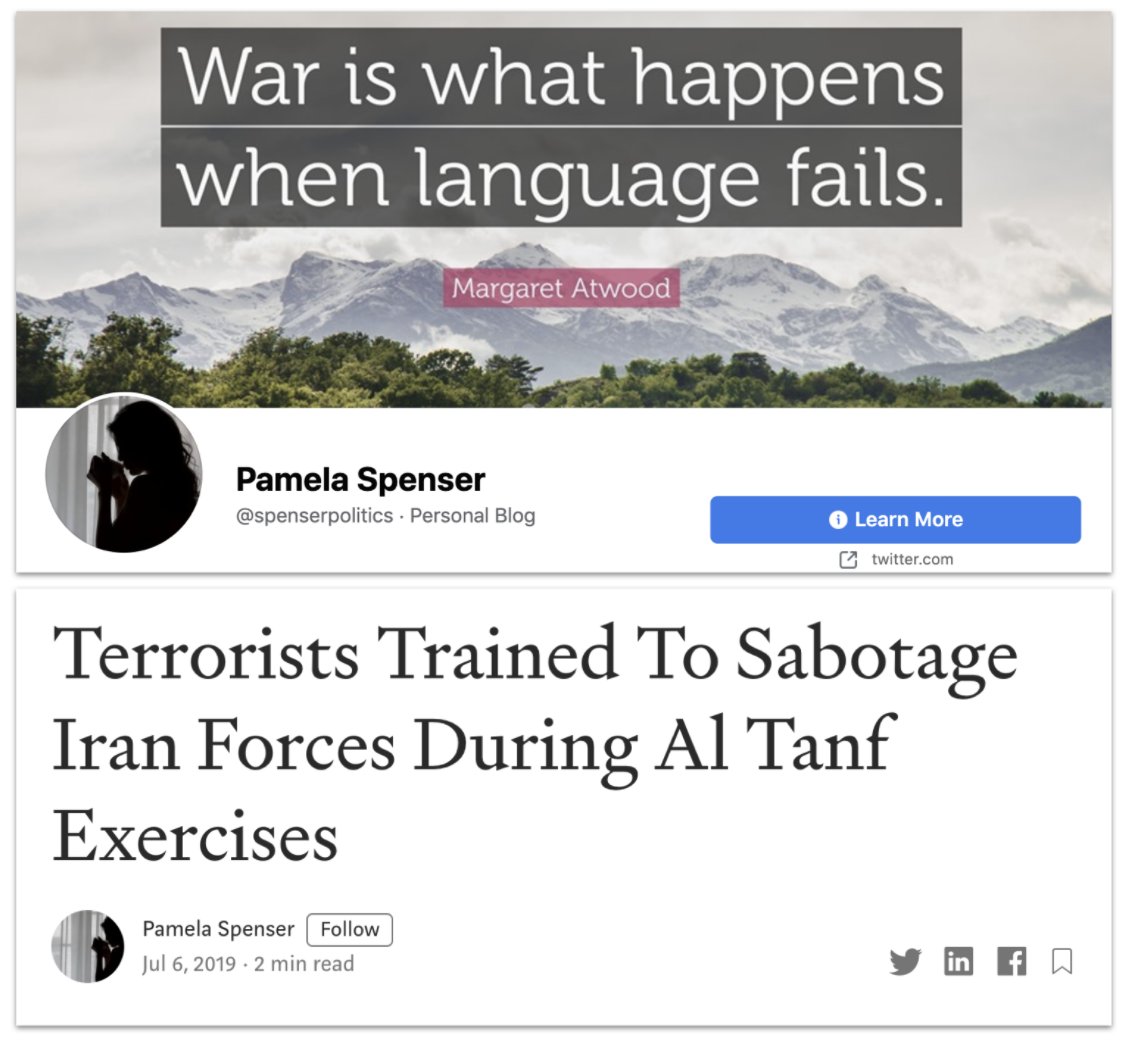
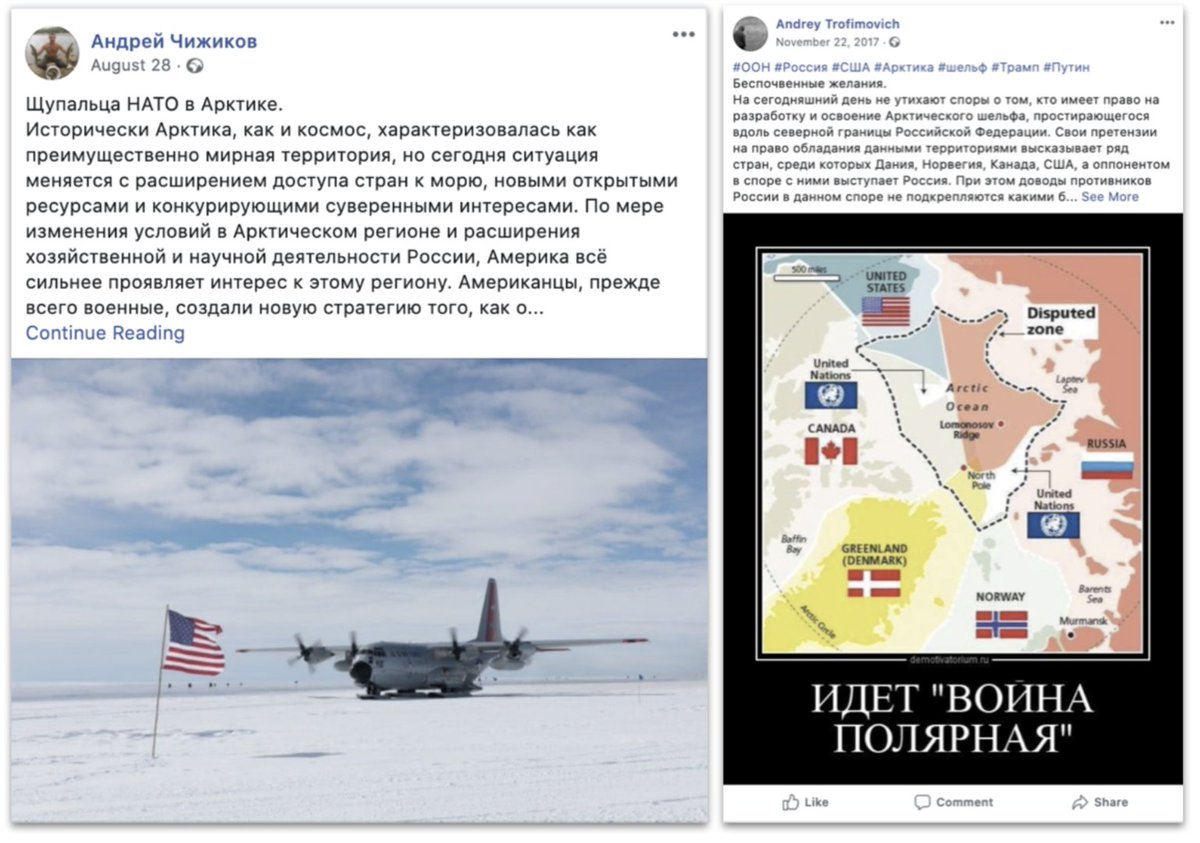
More broadly, Syria was a big theme in this takedown set.
English, Arabic and Russian posts. Basic message: Russia and Assad good, America and the West bad.
Oh, and chemical attacks as false flags.
Subtle.
English, Arabic and Russian posts. Basic message: Russia and Assad good, America and the West bad.
Oh, and chemical attacks as false flags.
Subtle.

And as for organisations like @Greenpeace, @WWF and @Bellona_no, well... I don't think this operation liked them much. 

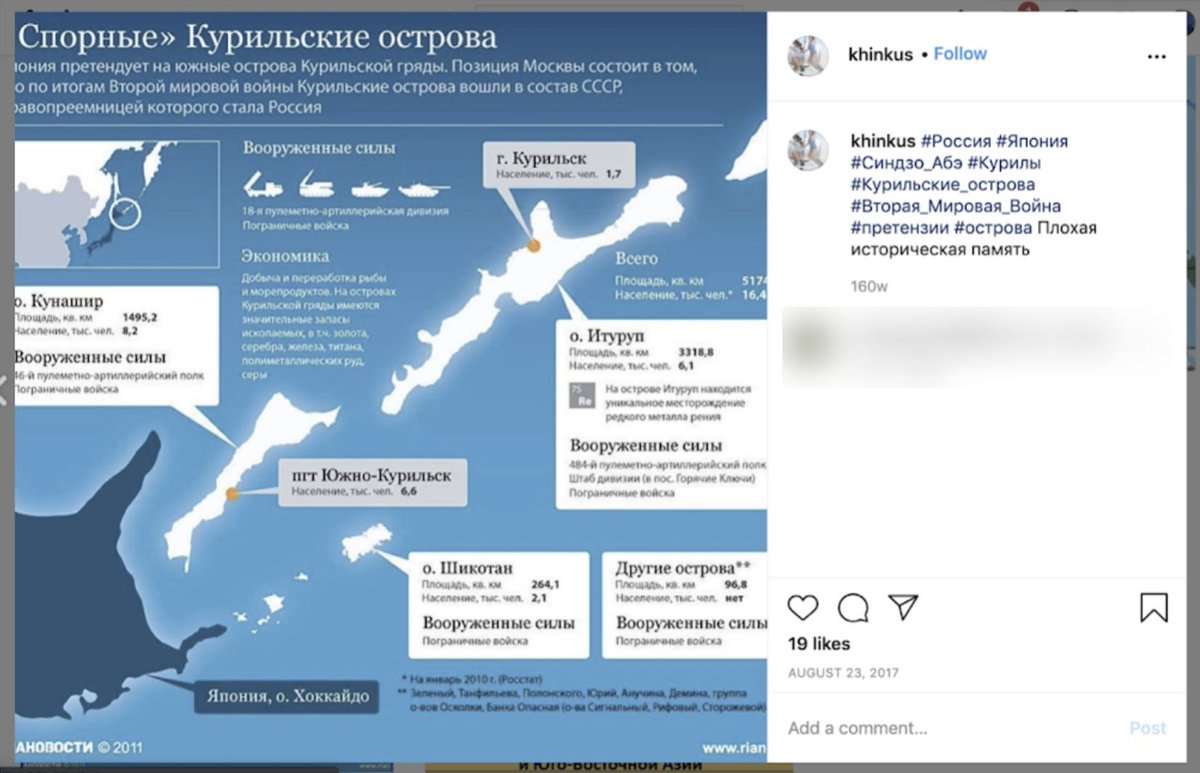
Interestingly, a whole cluster of assets across multiple platforms took aim at Japan, especially over the Kuril islands.
Some of those claimed to be run from Khabarovsk, in the Russian Far East.
Some of those claimed to be run from Khabarovsk, in the Russian Far East.
That may be true. An earlier takedown of Russian military assets included links to a website called nbenegroup[.]com, which posed as a student geopolitical analysis group.
This was its domain registration. Awkward.
This was its domain registration. Awkward.
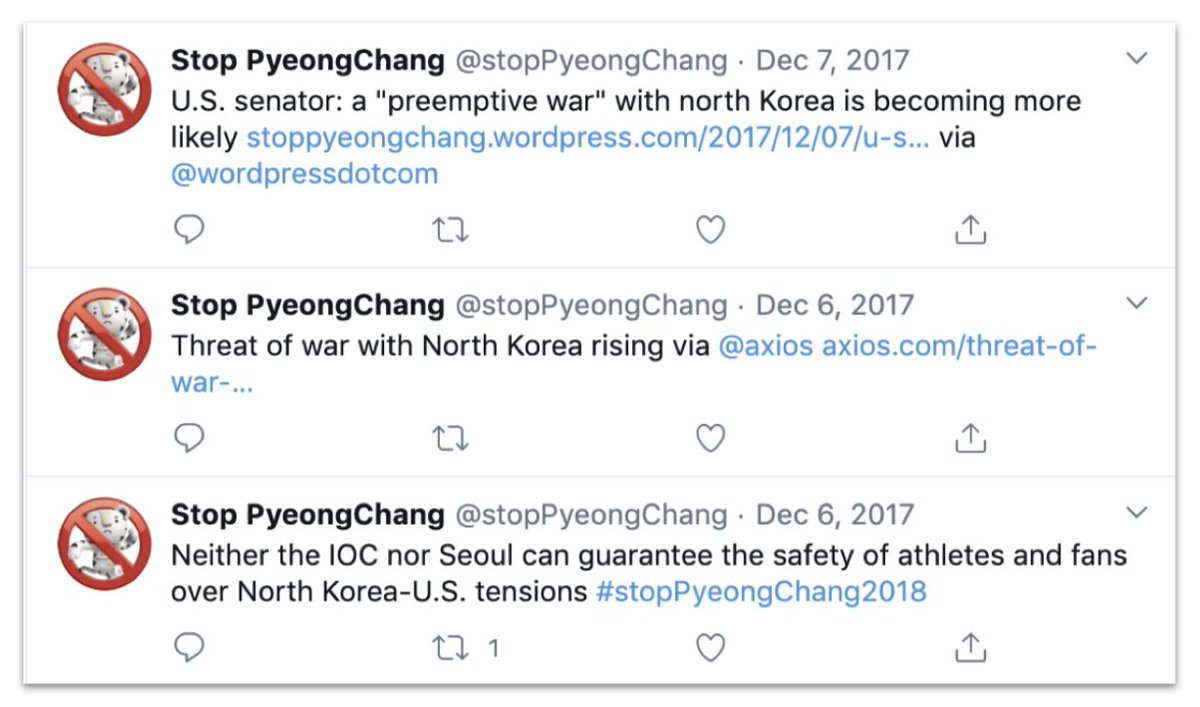
One of my favourite personas in the whole set was this one. (On Twitter and Wordpress as well as Instagram).
Stop the Winter Olympics because, um, Russia got banned for doping.
Think of it as Operation Sour Grapes.
Stop the Winter Olympics because, um, Russia got banned for doping.
Think of it as Operation Sour Grapes.
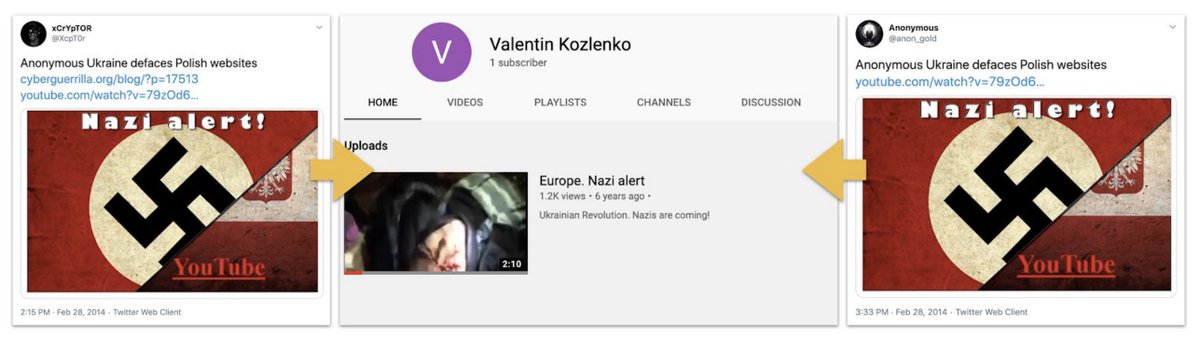
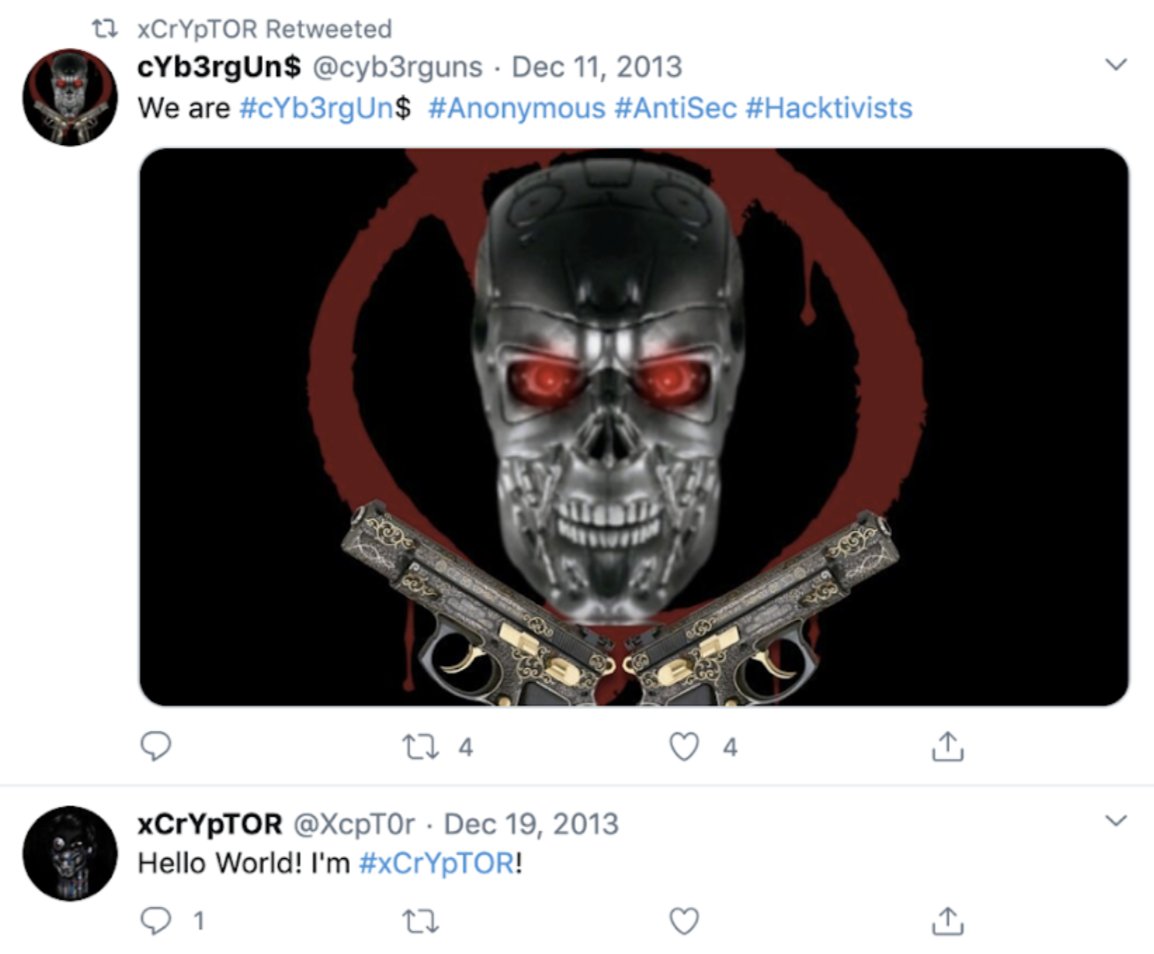
There was even a really early cluster of accounts that posed as ... wait for it... hacktivists.
Late 2013-early 2014. They went silent by mid-2014.
Late 2013-early 2014. They went silent by mid-2014.
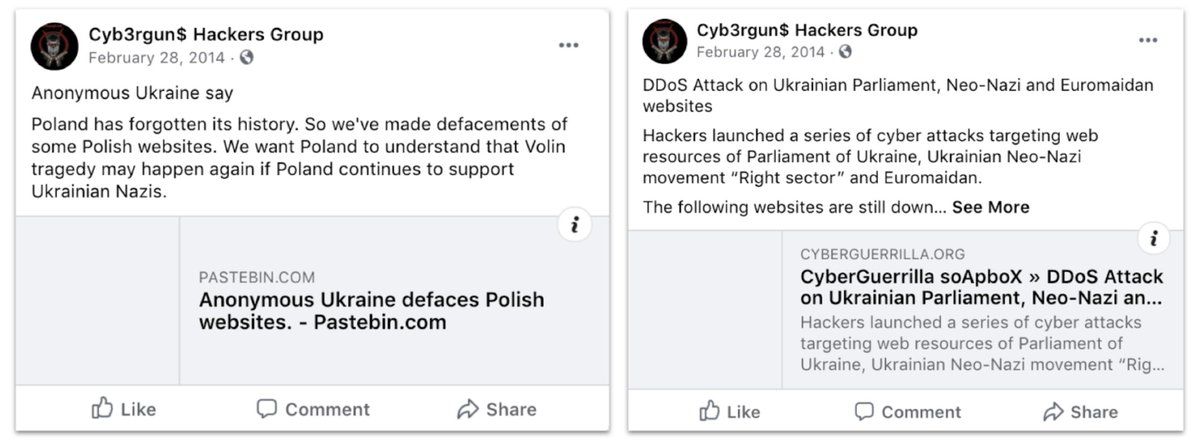
Hacking and defacing Ukrainian and allied websites around February-March 2014, just as Russia was annexing Crimea. 
Further West, this cluster seemed to dislike, well, pretty much everybody, really.
NATO, the Baltics, the USA, Georgia...
NATO, the Baltics, the USA, Georgia...

Mostly this was in English or Russian, but sometimes they really stretched.
Also, they targeted Angela Merkel. As Russian operations so often do.
Also, they targeted Angela Merkel. As Russian operations so often do.
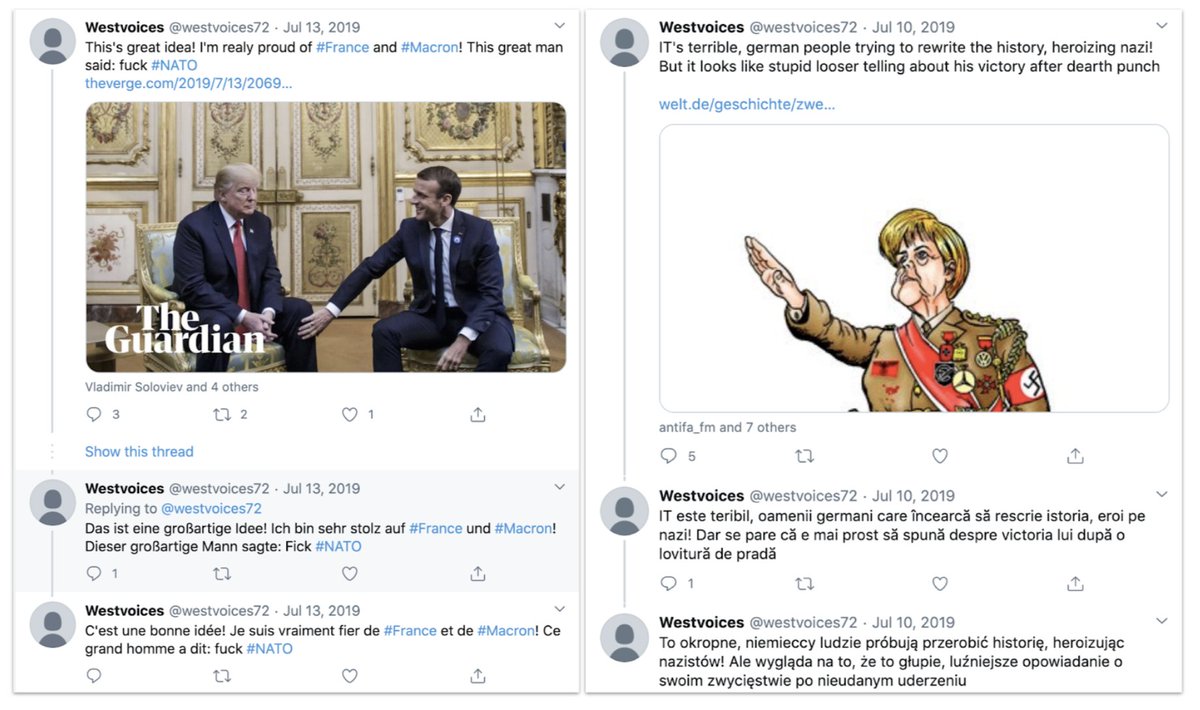
Sometimes, the strategic interests of different clusters intersected. Here's a Syria-focused asset riffing on the Skripal poisoning. 

Only one small cluster focused on US politics. That was based around a blog called "Black and intelligent."
Before anyone loses perspective, it last posted in January, and had less than 500 followers across all platforms.
Important for the attempt, not the reach.
Before anyone loses perspective, it last posted in January, and had less than 500 followers across all platforms.
Important for the attempt, not the reach.
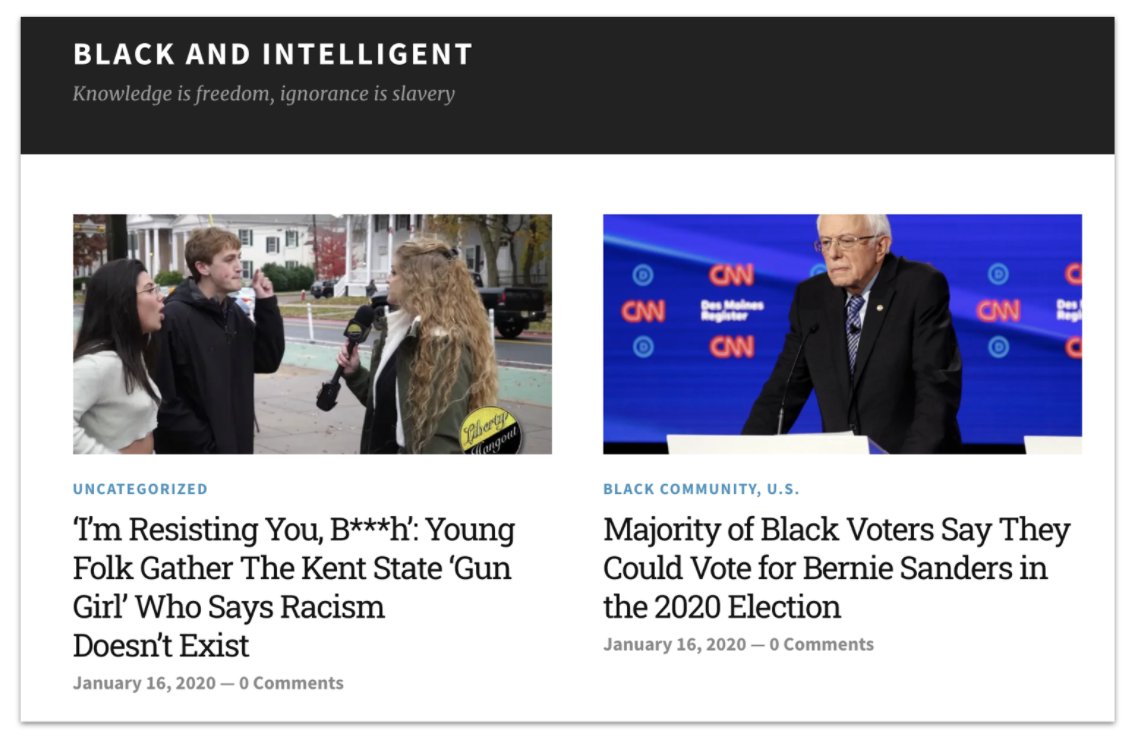
The blog worked by copying content from bona fide news outlets. Every article was plagiarised.
That looks like an audience-building exercise that was dropped before it built an audience.
That looks like an audience-building exercise that was dropped before it built an audience.
So overall, where are we?
Different clusters of fake accounts, most likely run by different teams in different places.
Some were active right up to the takedown, some stopped posting years ago.
Common thread: Russian strategic narratives, especially around the military.
Different clusters of fake accounts, most likely run by different teams in different places.
Some were active right up to the takedown, some stopped posting years ago.
Common thread: Russian strategic narratives, especially around the military.
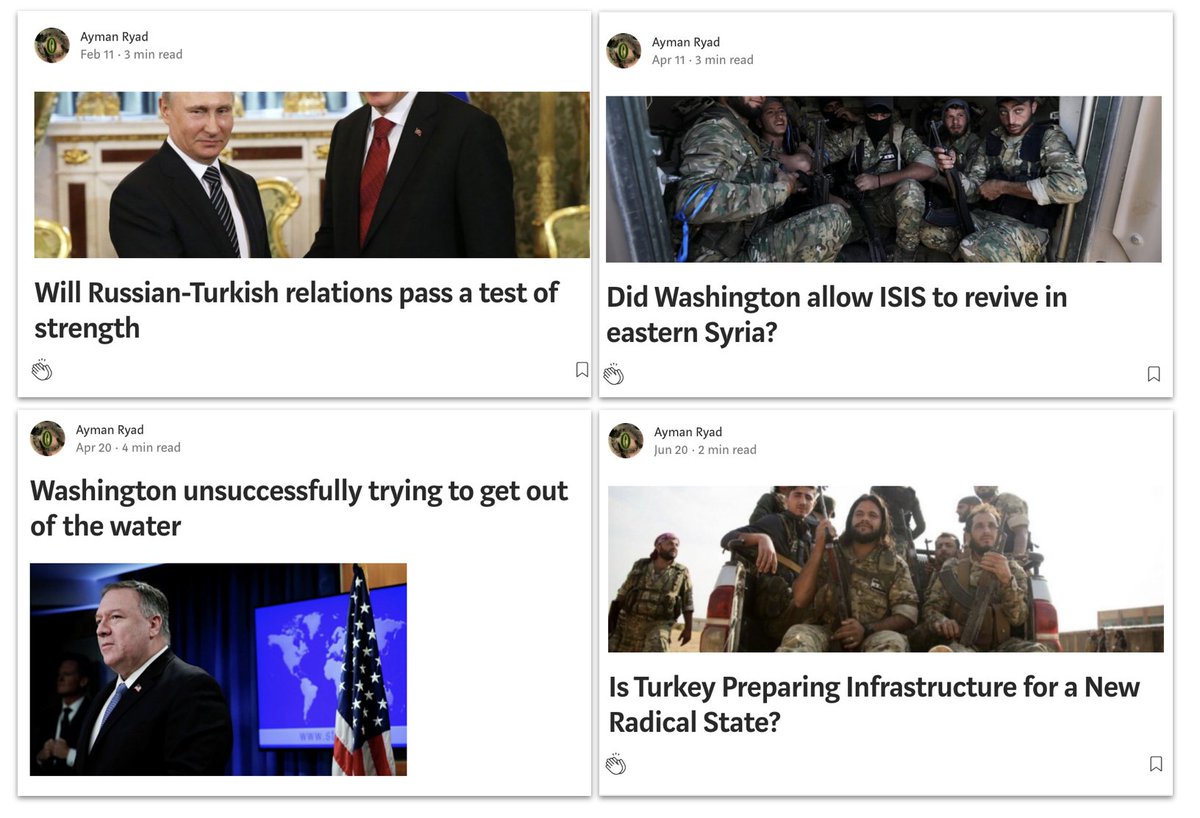
They didn't have much impact. The most popular page had about 3,500 followers, the most popular page had about 6,500 members.
Posts like this had a certain charm, though.
So beautiful view, indeed.
Posts like this had a certain charm, though.
So beautiful view, indeed.
Like I said, finding and taking down threat actors *before* the election is a smart move.
But that doesn't mean the threat actors have gone away.
Like I've also said: keep calm, but keep watch.
But that doesn't mean the threat actors have gone away.
Like I've also said: keep calm, but keep watch.
• • •
Missing some Tweet in this thread? You can try to
force a refresh