NEW: A Russian operation posed as a far-right website to target U.S. divisions and the election.
Most active on Gab and Parler.
A few months old.
Looks related to the IRA-linked PeaceData (which targeted progressives).
@Graphika_NYC report: public-assets.graphika.com/reports/graphi…
Most active on Gab and Parler.
A few months old.
Looks related to the IRA-linked PeaceData (which targeted progressives).
@Graphika_NYC report: public-assets.graphika.com/reports/graphi…

Credit to @jc_stubbs of @Reuters, who tipped us off to this.
A legend in his own byline.
reuters.com/article/us-usa…
A legend in his own byline.
reuters.com/article/us-usa…
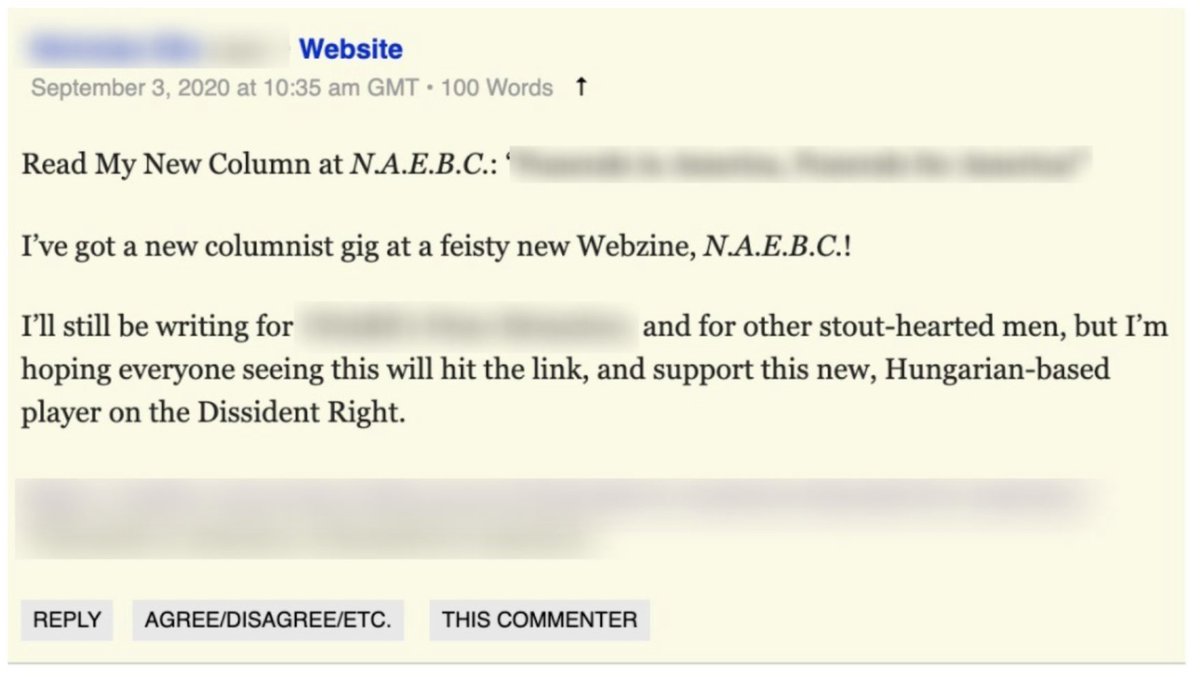
This op was based on a website called the Newsroom for American and European Based Citizens, NAEBC.
@Alexey__Kovalev might enjoy this name: it’s close to the Russian swear word “наёбка”.
Just like PeaceData sounded like the Russian epithet “пиздато.”
There’s a theme there.
@Alexey__Kovalev might enjoy this name: it’s close to the Russian swear word “наёбка”.
Just like PeaceData sounded like the Russian epithet “пиздато.”
There’s a theme there.
The other theme it had was being heavily into the far right. Gothic font, “war on faith,” “media bias,” “war on family”... Playing to a very specific audience. 

The operation claimed to be based in Hungary, with editorial staff also in the Netherlands.
I love the coyness here. “We’re a group of friends in *certain European country*” (blame secrecy on those pesky EU laws).
I love the coyness here. “We’re a group of friends in *certain European country*” (blame secrecy on those pesky EU laws).

But here’s a funny thing: the vast majority of the website’s articles were about the U.S., and especially race and politics.
Not, y’know, Hungary or the Netherlands. Or even the EU.
Not, y’know, Hungary or the Netherlands. Or even the EU.
The content it posted was… inflammatory. This was its very first headline, on July 2.
Note the tag, “War on Citizens.”
Note the tag, “War on Citizens.”

The early articles look like they were written by the operation itself. No byline, not copied from elsewhere, unidiomatic English.
This was their first ever lede.
This was their first ever lede.
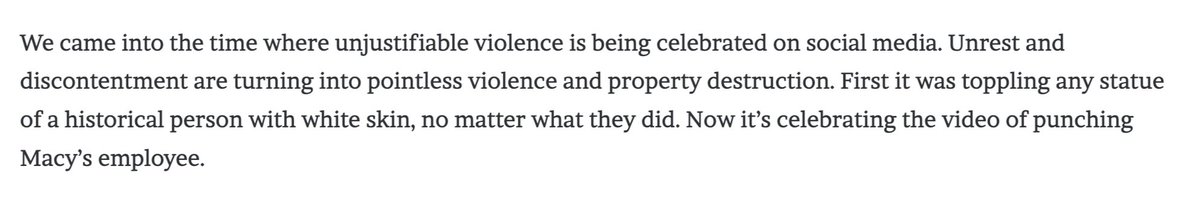
The reporting on race was not subtle.
“It’s time to say goodbye to White law enforcement officers. That means that Law and Order will be forgotten.”
“It’s time to say goodbye to White law enforcement officers. That means that Law and Order will be forgotten.”

That was the build-up phase. They didn’t much advertise those articles: it’s more like they were stocking the website with appropriate content, to give it a track record.
From August, they switched to publishing articles by real Americans. Some were copies…
From August, they switched to publishing articles by real Americans. Some were copies…
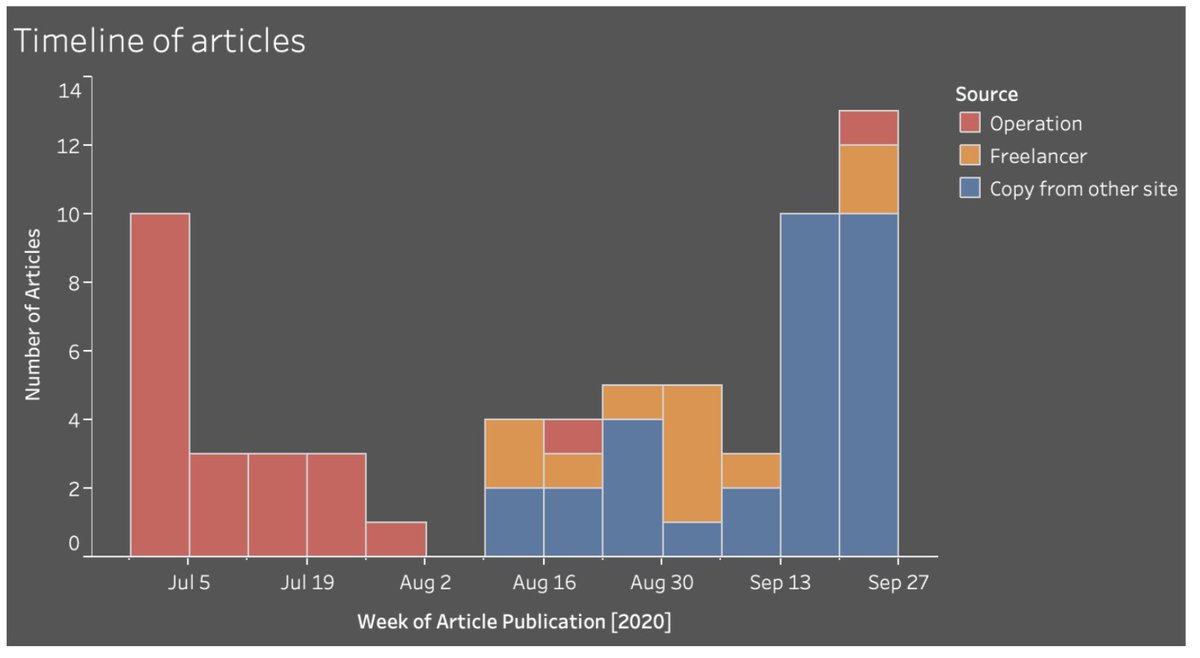
Especially in late August, they reached out directly to bloggers. One-on-one targeting, inviting them to contribute.
Never forget, journalists can be targets as well as reporters.
Never forget, journalists can be targets as well as reporters.
And where did they advertise those articles? That’s one of the interesting things.
They had a couple of accounts on Twitter, and tried (but failed) to create one on Facebook, but…
They had a couple of accounts on Twitter, and tried (but failed) to create one on Facebook, but…
...as this went on, they focused more and more on Gab and Parler.
Permissive environments, and an audience appropriate to their content?
As far as we know, this is the first Russian operation exposed on those platforms.
(Timeline of asset activation here.)
Permissive environments, and an audience appropriate to their content?
As far as we know, this is the first Russian operation exposed on those platforms.
(Timeline of asset activation here.)

To do that, they used just five fake personas.
“Oh Grandma, what a small operation you have.”
“All the better to evade detection with, my dear.”
Also to evade detection, three of them used AI-generated faces. Again.
“Oh Grandma, what a small operation you have.”
“All the better to evade detection with, my dear.”
Also to evade detection, three of them used AI-generated faces. Again.

These assets formed a self-sustaining community. On Parler, they liked each other lots, and then liked prominent voices on the right and far right, trying to get attention.
There’s no indication that any major amplifiers picked them up, though.
There’s no indication that any major amplifiers picked them up, though.
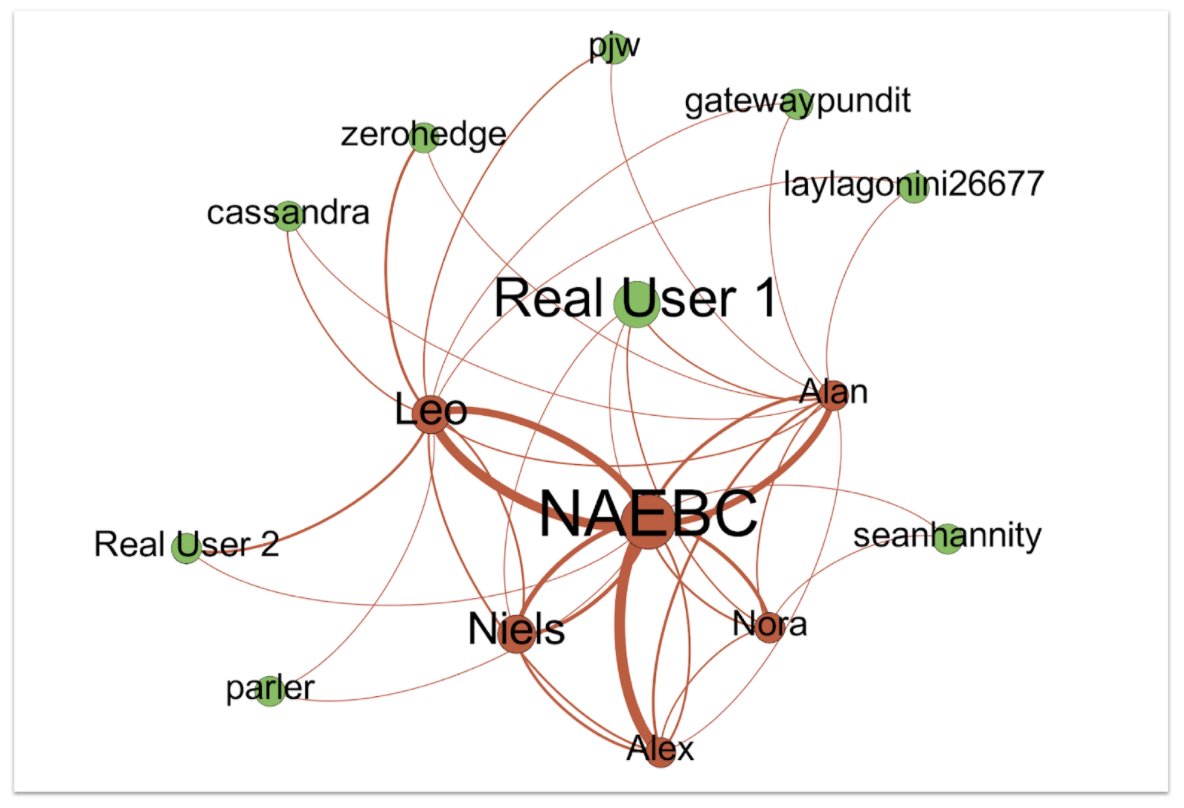
For an operation that was only really active on social media for two months, they weren’t a total flop. About 14k followers on Parler, 3k on Gab.
But every account followed many more accounts than it was following. That isn’t a sign of viral appeal.
But every account followed many more accounts than it was following. That isn’t a sign of viral appeal.

One of the most interesting questions now is: what are Gab and Parler going to do about it?
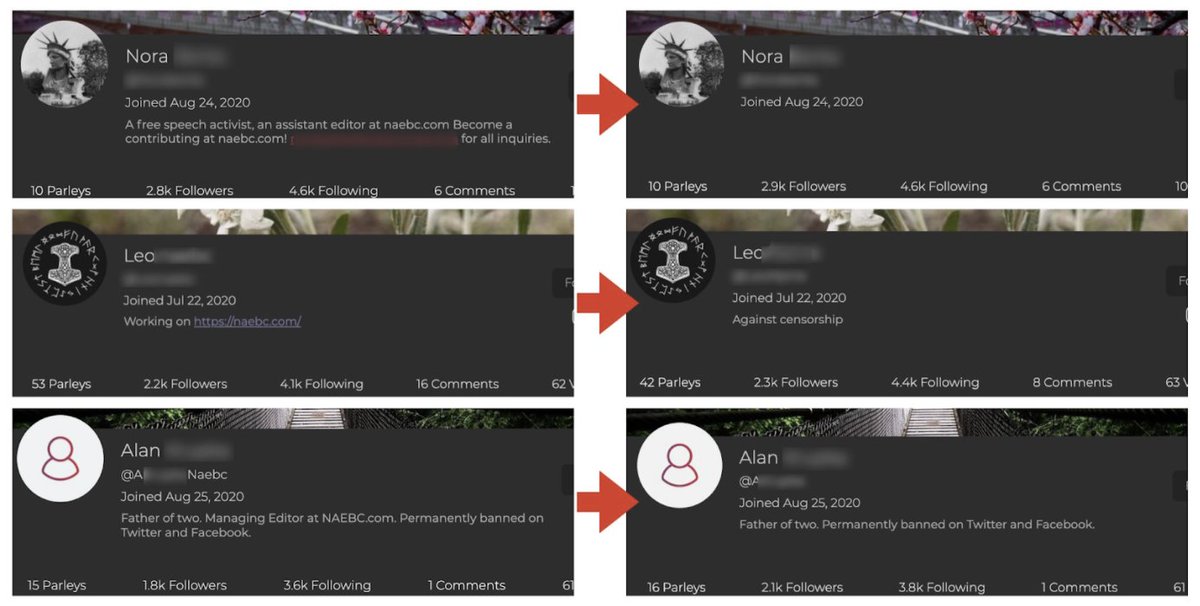
As soon as @jc_stubbs exposed them, all the fake assets scrubbed mentions of NAEBC from their bios. They even changed their Parler handles to do the same.
Operation Guilty Conscience?
As soon as @jc_stubbs exposed them, all the fake assets scrubbed mentions of NAEBC from their bios. They even changed their Parler handles to do the same.
Operation Guilty Conscience?
But this looks really like the Russian IRA.
The resemblances with PeaceData, which has been attributed to IRA-linked individuals, go well beyond the punning name.
The resemblances with PeaceData, which has been attributed to IRA-linked individuals, go well beyond the punning name.
Both claimed to be young European news outlets. Both targeted very precise demographics. Both hired genuine freelancers, including people who’d never written before - perhaps the better to steer them editorially. 
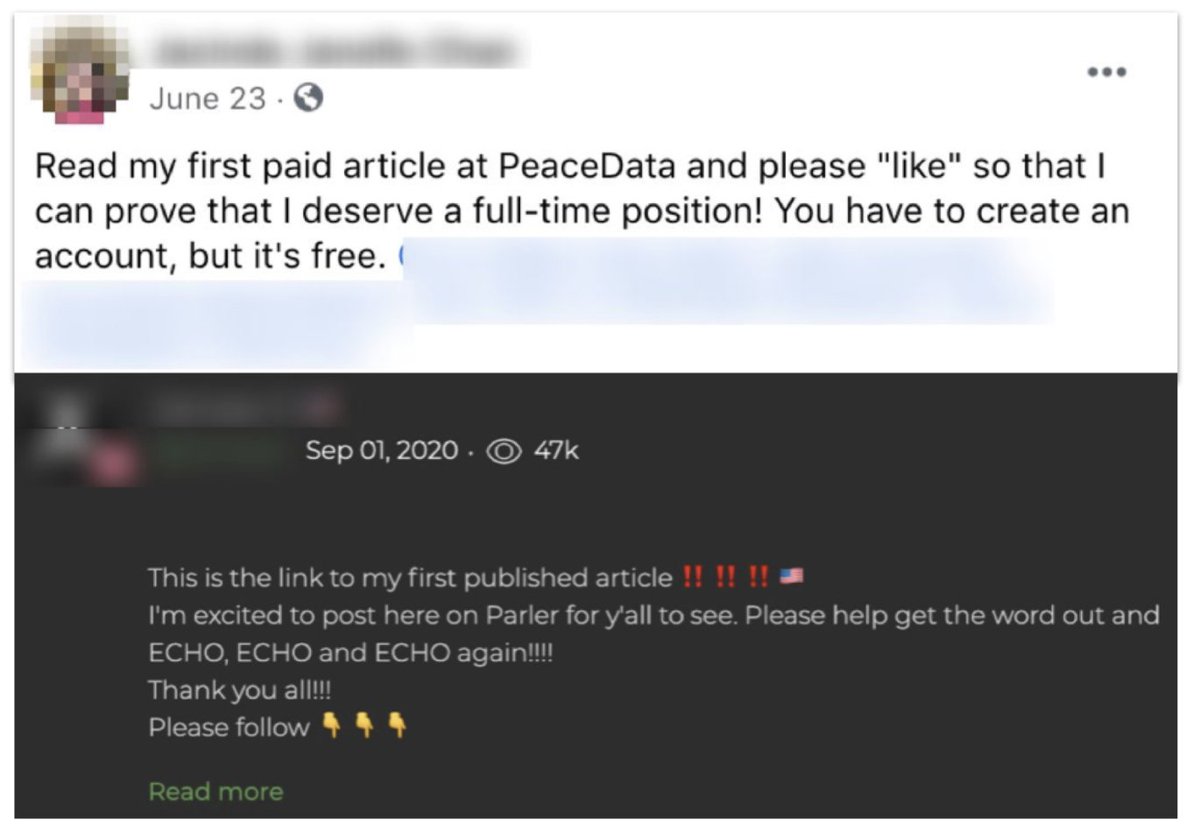
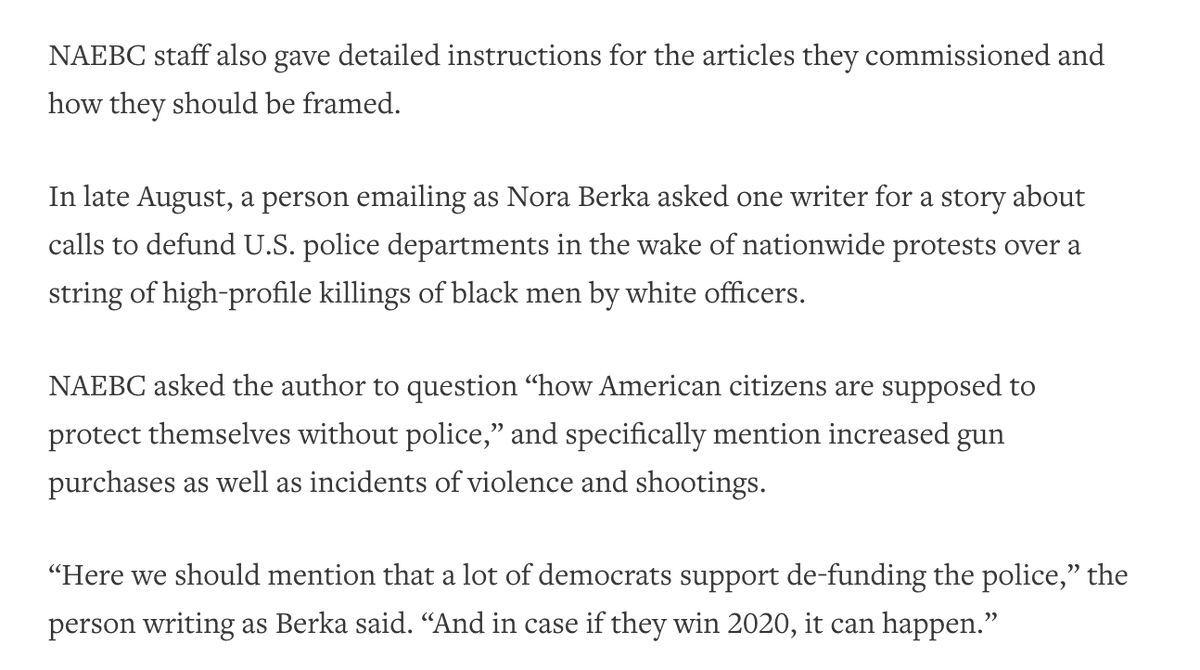
This describes the editorial direction they sent by email, per @Reuters. 
Both had personas with GAN faces. Oddly, many of those personas had names beginning with “Al” - a stylistic quirk?
(PeaceData top two rows, NAEBC bottom. Eye alignment is typical of AI-generated sets.)
(PeaceData top two rows, NAEBC bottom. Eye alignment is typical of AI-generated sets.)

Put them together, and what were they doing?
Well, NAEBC posted pro-Trump and anti-Biden messaging. This dropped an hour ago - again, timing publication for the US market, not just Europe.
Well, NAEBC posted pro-Trump and anti-Biden messaging. This dropped an hour ago - again, timing publication for the US market, not just Europe.
PeaceData pushed anti-Biden messaging to further left groups, especially Democratic Socialists and progressives. 
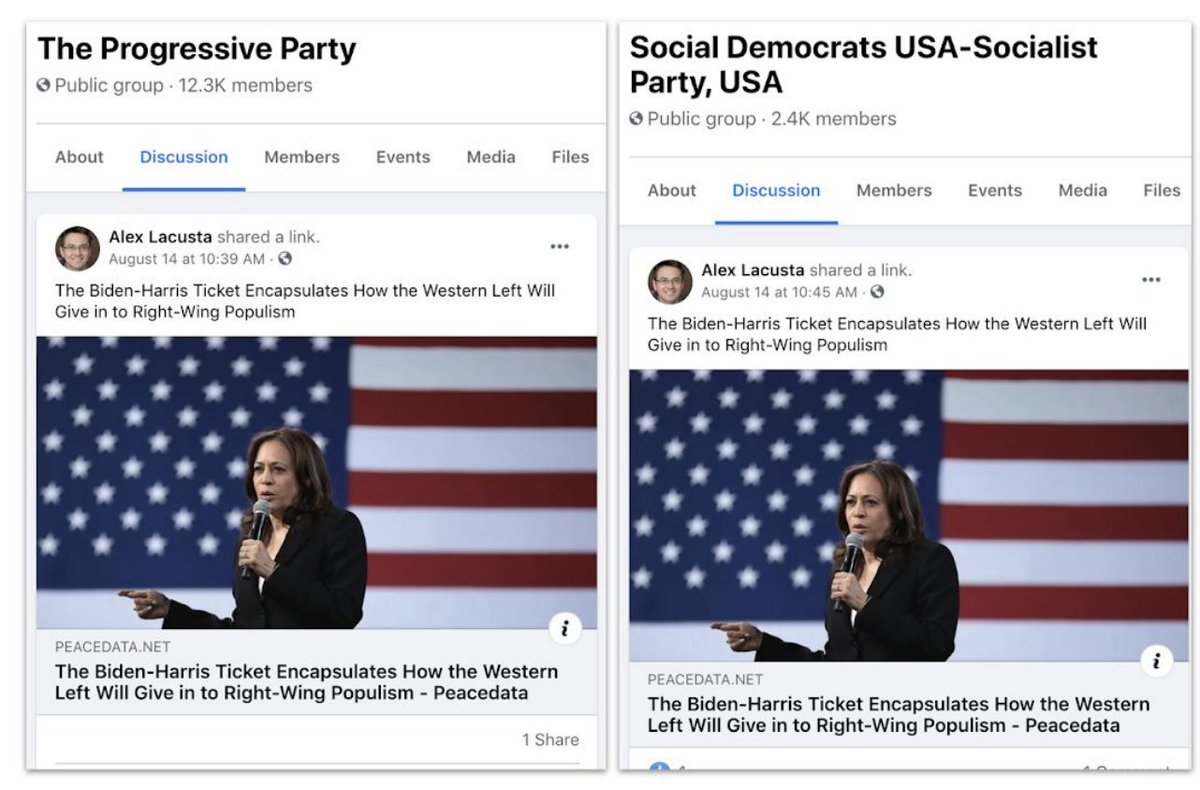
That's very similar to what the original IRA did in 2016: energise support for Trump, depress support for the Democratic candidate, and push polarising content to both ends of the spectrum.
These two efforts were much, much less viral than in 2016. The PeaceData Facebook page in English had 200 followers. The NAEBC ones had a few thousand, and followed more than they had followers themselves. 
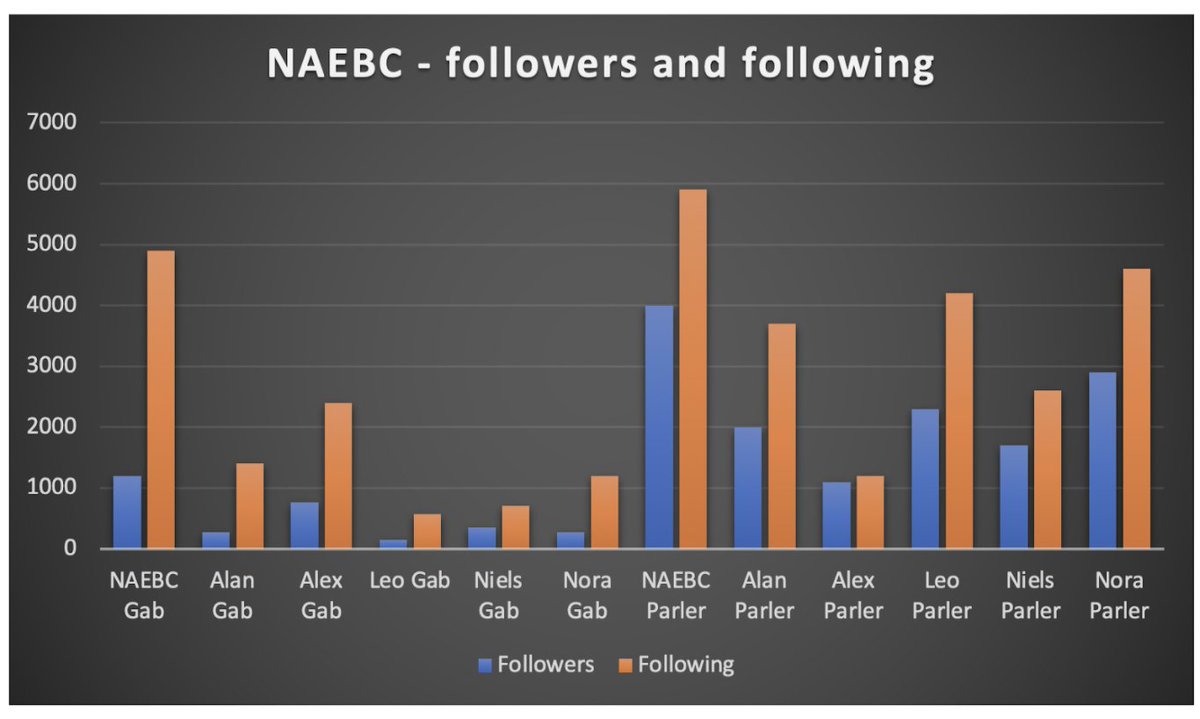
As @RidT pointed out yesterday, one question about operations like this is whether they were just working the budget in some way.
https://twitter.com/RidT/status/1311475149716234241
But by the same token, operations that look like utterly futile exercises in budget-burning - like Secondary Infektion - can actually break into the mainstream under the right circumstances, like a hack-to-leak operation. 

I'd rate NAEBC as a Category 2 on the breakout scale of info ops - multiple platforms, but not really breaking out of its immediate communities.
Even with PeaceData, it edges up towards Category 3, but it's a pretty borderline case.
Even with PeaceData, it edges up towards Category 3, but it's a pretty borderline case.

So it's important for what it shows, not what it achieved.
Ongoing attempts by Russian operators to target American voters with polarising and partisan messaging.
As always, keep calm. But keep watch, especially as the election comes.
Ongoing attempts by Russian operators to target American voters with polarising and partisan messaging.
As always, keep calm. But keep watch, especially as the election comes.
• • •
Missing some Tweet in this thread? You can try to
force a refresh