
So the resolution explicitly calls for gaining “targeted access to encrypted data”, but we’re going to say that’s not a “backdoor in encryption”. Because we say things. 
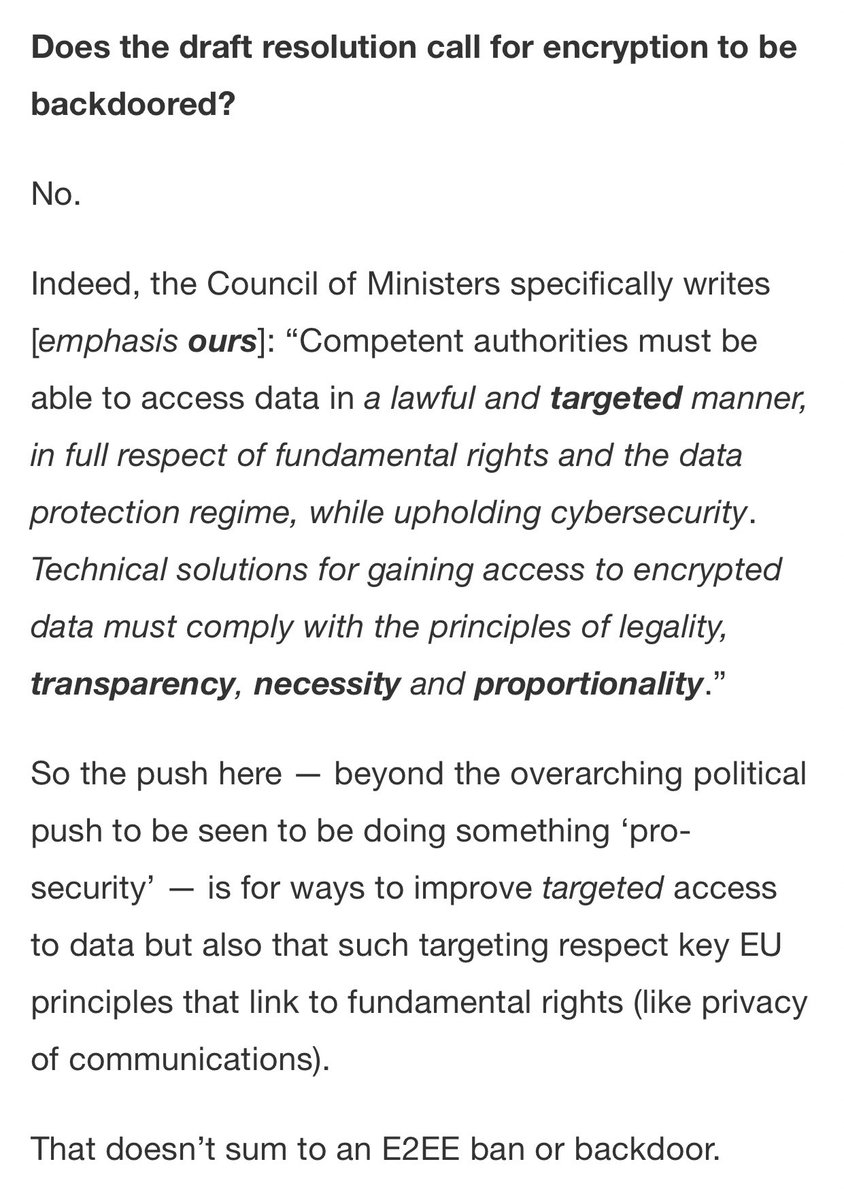
Sorry, @TechCrunch. The resolution may or may not be serious, but it’s not ambiguous. You either gain access to encrypted data or you don’t. techcrunch.com/2020/11/09/wha…
The problem with encryption backdoors isn’t solved by “proportionality” or having great laws that ensure the tech is only used in a targeted manner.
The problem with encryption backdoors is that to use them in a targeted way, you first need to create an encryption backdoor.
The problem with encryption backdoors is that to use them in a targeted way, you first need to create an encryption backdoor.
I’ve been watching these proposals for years now, and they always include boilerplate about warrants and proportionality and “targeted access”. But when you ask real technical requirements questions, it becomes obvious that technical restrictions are not acceptable.
For example: a terrorist attack has occurred, and the suspect is dead. Police want access to his texts — but he wasn’t a suspect when the texts were sent.
Does the technology allow police to decrypt texts sent by a non-suspect? Then congratulations: it can access anyone’s texts.
Does the technology allow police to decrypt texts sent by a non-suspect? Then congratulations: it can access anyone’s texts.
If you ask police whether they’d accept a system that can only access the texts of people who were specifically targeted for surveillance in advance, they think about it and tell you “no”.
(But it takes them a while to think about this, because it doesn’t occur to them that “restricting surveillance only to specific targets”, in a technological sense, generally only works if the targeting is done before messages are sent.)
The minute you say “I may need access to the texts of a suspect who wasn’t necessarily a suspect when they sent the texts”, you’re throwing away basically every *technological* mechanism for preventing mass surveillance.
At this point your only option is to make sure you can protect (and prevent yourself from abusing) the incredibly powerful encryption keys that give you this incredible surveillance power.
And you won’t be able to do any of that.
And you won’t be able to do any of that.
The only serious (messaging backdoor) proposal I’ve seen that takes a technical approach to preventing mass surveillance is the one from GCHQ, which proposes to “wiretap” group messaging systems by adding “ghost users” to chat sessions.
This actually is somewhat more resilient to abuse, because it requires active surveillance of targeted individuals. You can’t go back in time and read anyone’s messages from last week. (I have some other issues with that proposal, but I give it points for caring.)
But police don’t want some annoying targeted access system that keeps them honest. They want to read the messages from the guy they *didn’t* know was a criminal last week. That’s what San Benardino was, that’s what Vienna is. Etc.
• • •
Missing some Tweet in this thread? You can try to
force a refresh






