Giga arbitrage/exploit
etherscan.io/address/0xa773…
etherscan.io/address/0xa773…
https://twitter.com/The3D_/status/1327638923183591425

This is the complex exploit I've ever seen. It used 2 FLASHLOANS, one with @AaveAave (80k ETH) and one using flashswap with @UniswapProtocol (116M DAI).
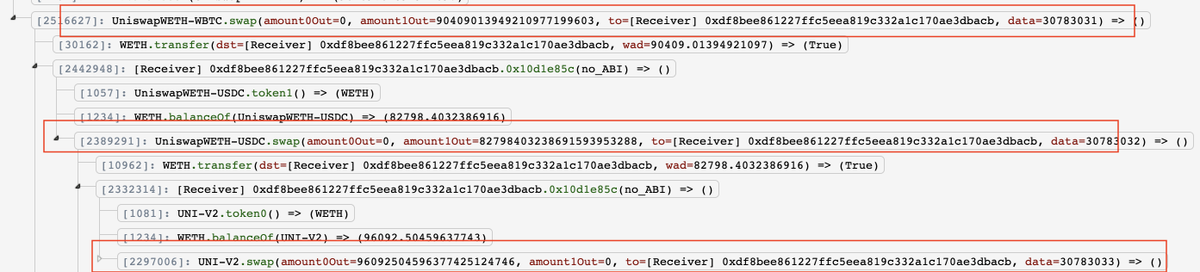
In the image the steps!
In the image the steps!

TL;DR the manipulation occured at step 5. And 6.
Withdrawal at step 7. is using the wrong Curve function to do the math
Withdrawal at step 7. is using the wrong Curve function to do the math
• • •
Missing some Tweet in this thread? You can try to
force a refresh