1/8
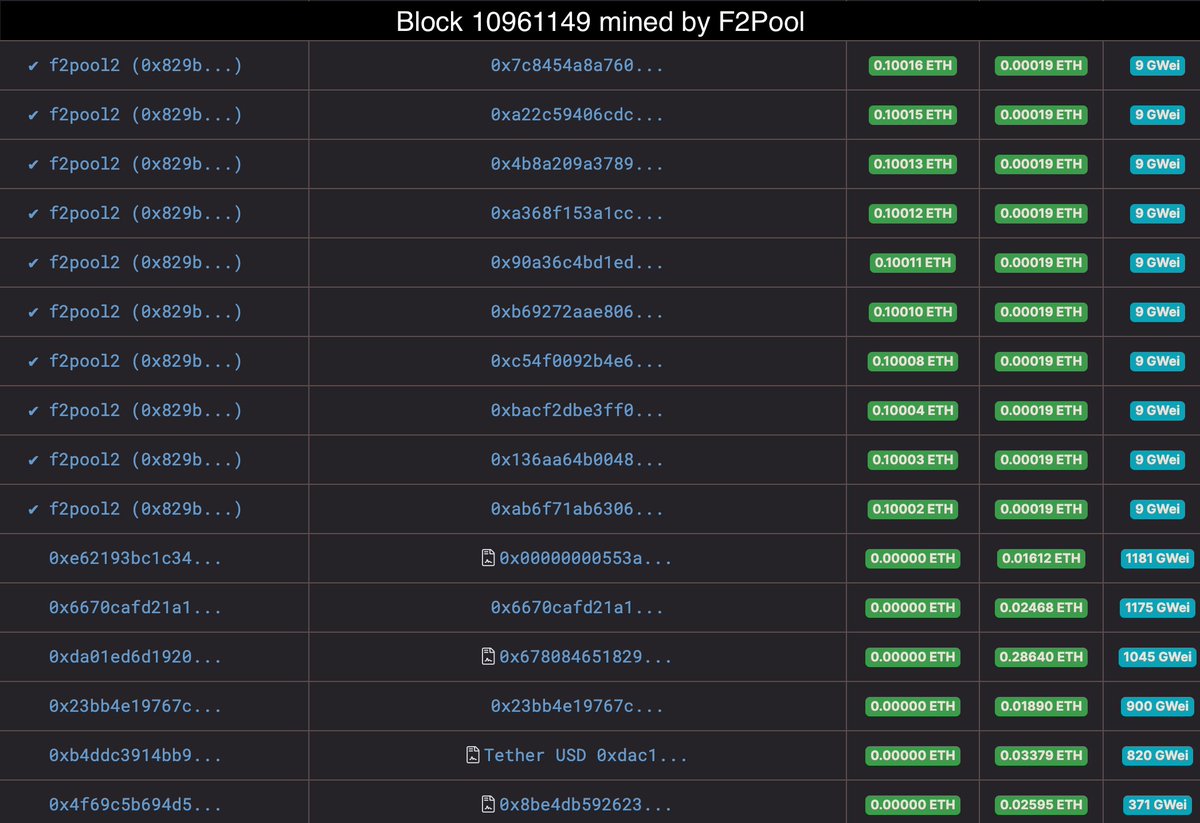
6 hours ago, there was another attack using flash loan, this time @OriginProtocol was affected. This attack is similar to Akropolis hack, because the problem is in re-entrancy and use of a fake token. All of this was needed to manipulate rebasing. Let’s see how it happened:
6 hours ago, there was another attack using flash loan, this time @OriginProtocol was affected. This attack is similar to Akropolis hack, because the problem is in re-entrancy and use of a fake token. All of this was needed to manipulate rebasing. Let’s see how it happened:
2/8
1. Flash loan 70k ETH from dYdX
2. Swap 17.5k ETH for 7.86 mln USDT on Uniswap
3. Swap 52.5k ETH for 20.99 mln DAI on Uniswap
4. Allow to rebase the attack contract
5. Mint 7.5 mln OUSD with 7.5 mln USDT
1. Flash loan 70k ETH from dYdX
2. Swap 17.5k ETH for 7.86 mln USDT on Uniswap
3. Swap 52.5k ETH for 20.99 mln DAI on Uniswap
4. Allow to rebase the attack contract
5. Mint 7.5 mln OUSD with 7.5 mln USDT
3/8
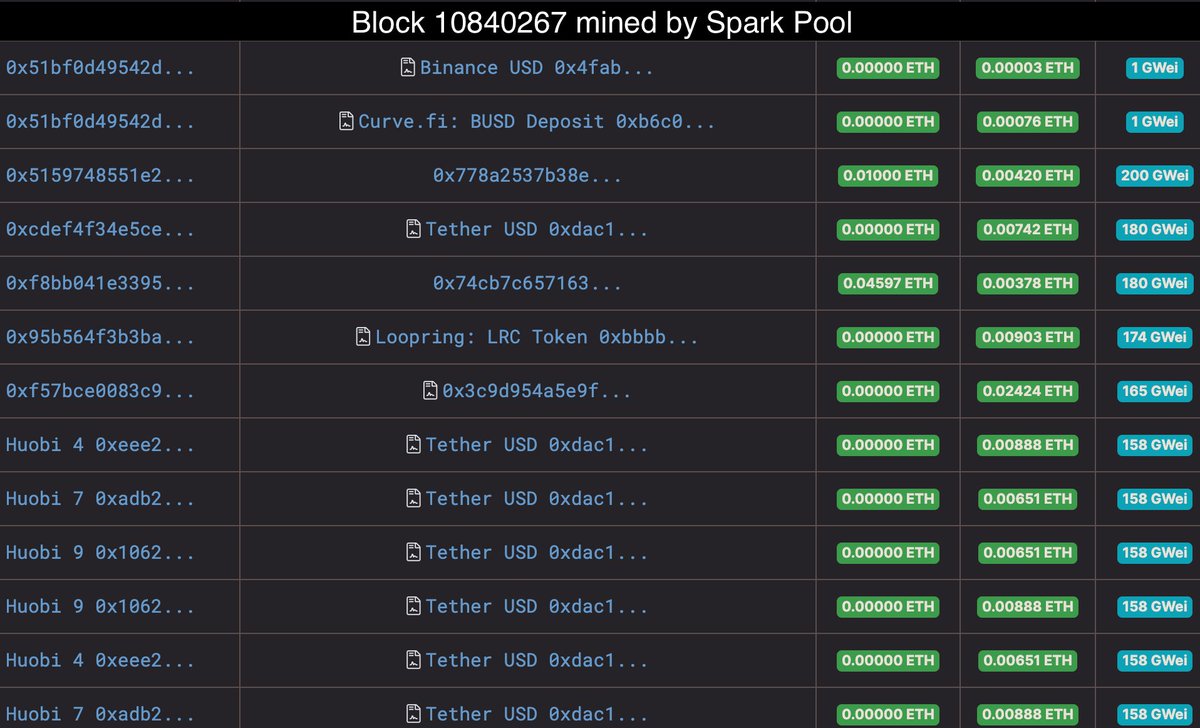
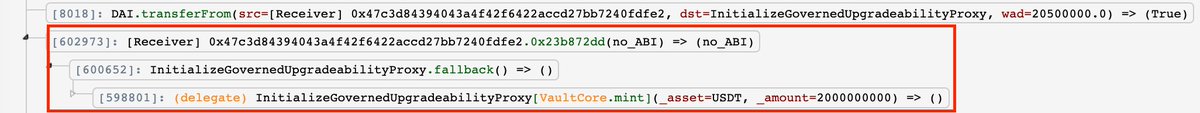
6. Call MintMultiple() function with:
6.1 mint 20.5 mln OUSD with 20.5 mln DAI
6.2 mint 2k OUSD with 2k USDT with rebasing through re-entrancy because the second asset is a fake token
7. Swap 300k OUSD to 158.5k USDT on Uniswap
8. Swap 1 mln OUSD to 520.7k USDT on Sushiswap

6. Call MintMultiple() function with:
6.1 mint 20.5 mln OUSD with 20.5 mln DAI
6.2 mint 2k OUSD with 2k USDT with rebasing through re-entrancy because the second asset is a fake token
7. Swap 300k OUSD to 158.5k USDT on Uniswap
8. Swap 1 mln OUSD to 520.7k USDT on Sushiswap

4/8
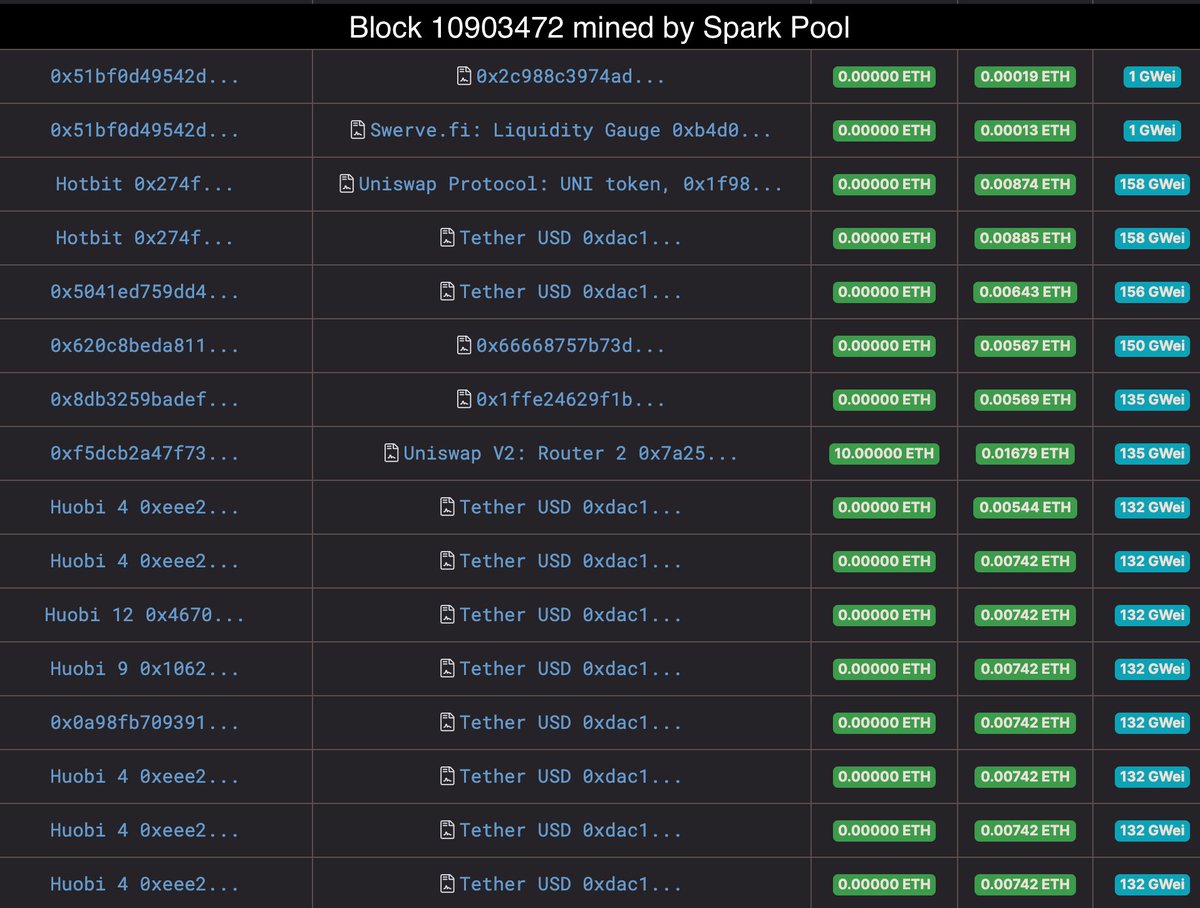
9. Redeem 33.27 mln OUSD after rebasing for 19.5 mln DAI, 3.9 mln USDC and 9.4 mln USDT
10. Swap 10.4 mln USDT to 22.9k ETH on Uniswap
11. Swap 3.9 mln USDC to 8.3k ETH on Uniswap
12. Swap 19 mln DAI to 47.9k ETH on Uniswap
13. Payback flash loan 70k ETH to dYdX
9. Redeem 33.27 mln OUSD after rebasing for 19.5 mln DAI, 3.9 mln USDC and 9.4 mln USDT
10. Swap 10.4 mln USDT to 22.9k ETH on Uniswap
11. Swap 3.9 mln USDC to 8.3k ETH on Uniswap
12. Swap 19 mln DAI to 47.9k ETH on Uniswap
13. Payback flash loan 70k ETH to dYdX
5/8
After this manipulation attacker made:
- 7 transactions in which he redeemed his OUSD
- 2 transactions to swap 300k OUSD to USDT on Uniswap
- 4 transactions with profit collection (swap all USDT and USDC for ETH on Uniswap and withdraw DAI and ETH from attack contract)
After this manipulation attacker made:
- 7 transactions in which he redeemed his OUSD
- 2 transactions to swap 300k OUSD to USDT on Uniswap
- 4 transactions with profit collection (swap all USDT and USDC for ETH on Uniswap and withdraw DAI and ETH from attack contract)
6/8
Finally, he used SELFDESTRUCT for destroying the contract.
As a result, the attacker was able to get ~$7.7M:
- 2,249,821 DAI
- 11,804 ETH
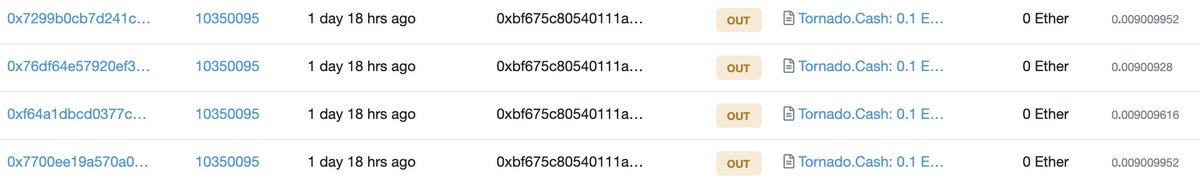
Also, the attacker deposited 333 ETH to Tornado Cash and tried to wash money using:
1. Uniswap for swap ~4338 ETH to 120 WBTC
Finally, he used SELFDESTRUCT for destroying the contract.
As a result, the attacker was able to get ~$7.7M:
- 2,249,821 DAI
- 11,804 ETH
Also, the attacker deposited 333 ETH to Tornado Cash and tried to wash money using:
1. Uniswap for swap ~4338 ETH to 120 WBTC
7/8
2. Curve for swap 120 WBTC to ~120 renBTC
3. REN for withdrawal ~120 BTC to four addresses:
- bc1qdky68q9uv24ah8mf8uykj8x437u2hlrz6k4vzg
- bc1q2atlthkh04hsnk76w08ek5stk28wxgzhh8xvnu
- bc1qr0v3zz5wl0wjt79hj7yq57f3tkswj79jmjaynh
- bc1q4f645352dsam42ag3uym8rt0qzxwd8qlqe336h
2. Curve for swap 120 WBTC to ~120 renBTC
3. REN for withdrawal ~120 BTC to four addresses:
- bc1qdky68q9uv24ah8mf8uykj8x437u2hlrz6k4vzg
- bc1q2atlthkh04hsnk76w08ek5stk28wxgzhh8xvnu
- bc1qr0v3zz5wl0wjt79hj7yq57f3tkswj79jmjaynh
- bc1q4f645352dsam42ag3uym8rt0qzxwd8qlqe336h
8/8
Fun fact: an unnecessary argument *address* was used in collect() function called by the attacker, which is the address of @value_defi hacker. Whether this address is an easter egg, whether one attacker belongs to two hacks, or just trolling, we probably won’t know for sure.
Fun fact: an unnecessary argument *address* was used in collect() function called by the attacker, which is the address of @value_defi hacker. Whether this address is an easter egg, whether one attacker belongs to two hacks, or just trolling, we probably won’t know for sure.

• • •
Missing some Tweet in this thread? You can try to
force a refresh