1/ I saw many wrong tweets about the @picklefinance exploit. Let me try to explain it.
It's not an economic exploit. It's more like a traditional CTF combining all coincidence. More details in the following threads.
TL;DR 👇This precisely describes how the exploit works.
It's not an economic exploit. It's more like a traditional CTF combining all coincidence. More details in the following threads.
TL;DR 👇This precisely describes how the exploit works.

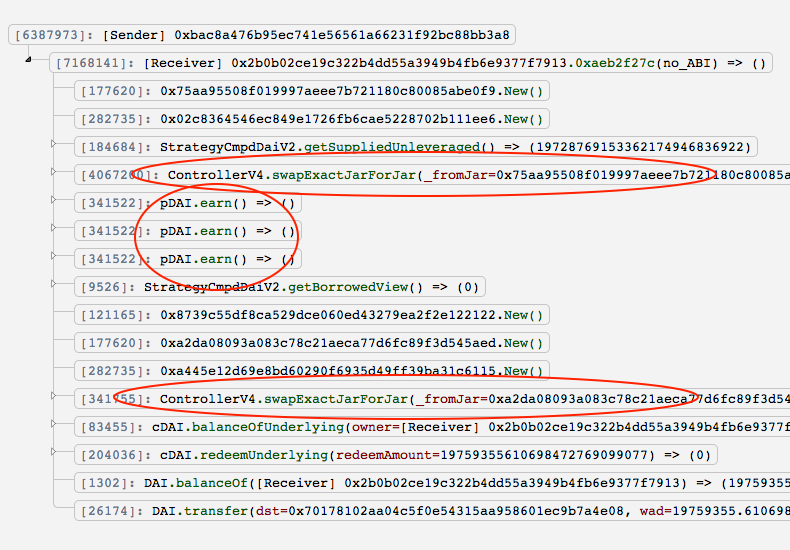
3/ from the screenshot, we can see that this exploit is very short. Let's divide them into 3 essential parts and focus on what they did actually. `swapExactJarForJar`, `earn()`, and `swapExactJarForJar` again.
4/ In first `swapExactJarForJar`, it let current DAI strategy deleverage DAI from Compound and send it back to pDAI Jar. In `earn()`, it turned DAI into cDAI as expected. In the second `swapExactJarForJar`, it withdrew cDAI back to controller and then put them into the fake Jar.
5/ There are actually 8 flaws utilized in this exploit. YET, there's one thing worth pointing out. This exploit only happens when these 8 flaws occur at the same time. So either 1 of 8 was fixed or didn't even exist, there wouldn't be this exploit.
6/ 8 flaws are here (ordered by the procedure of exploit, not severity):
1. no sanity check on address argument
2. allow to pass _target & _data openly
3. put withdrawForSwap in an unauthorized function
4. put delegatecall in an unauthorized function
1. no sanity check on address argument
2. allow to pass _target & _data openly
3. put withdrawForSwap in an unauthorized function
4. put delegatecall in an unauthorized function
7/
5. whitelisted address has an arbitrary function
6. whitelisted address is authorized to an unauthorized function
7. public earn
8. allow to withdraw working asset from strategy
None of them was related to economic technique like flash loan.
5. whitelisted address has an arbitrary function
6. whitelisted address is authorized to an unauthorized function
7. public earn
8. allow to withdraw working asset from strategy
None of them was related to economic technique like flash loan.
8/ I would say what pickle intended to do was nothing wrong. They wanted to make `swapExactJarForJar` generic and user-friendly. The problematic part was that all 8 flaws HAPPEN AT THE SAME TIME, and all used not in an intended way. That's why I said it's like a traditional CTF.
9/ Trade-off of making generic is necessity with more care.
My always motto for smart contracts: simplicity makes perfect.
My always motto for smart contracts: simplicity makes perfect.
• • •
Missing some Tweet in this thread? You can try to
force a refresh