Inspired by @cybergibbons hardware teardown thread, thought I'd document an investigation into an oddity that has been bugging me for a few years.
This is a TP-Link TL-WA701ND AP that I was using for a few years around the house. When I repurposed it, I noticed something odd..
This is a TP-Link TL-WA701ND AP that I was using for a few years around the house. When I repurposed it, I noticed something odd..

The AP can be set into different modes, including as Ethernet/Wifi client to permit wired devices to access a wireless network. I used this to connect my gaming machine as I was sick of ethernet cables lying across the floors. 
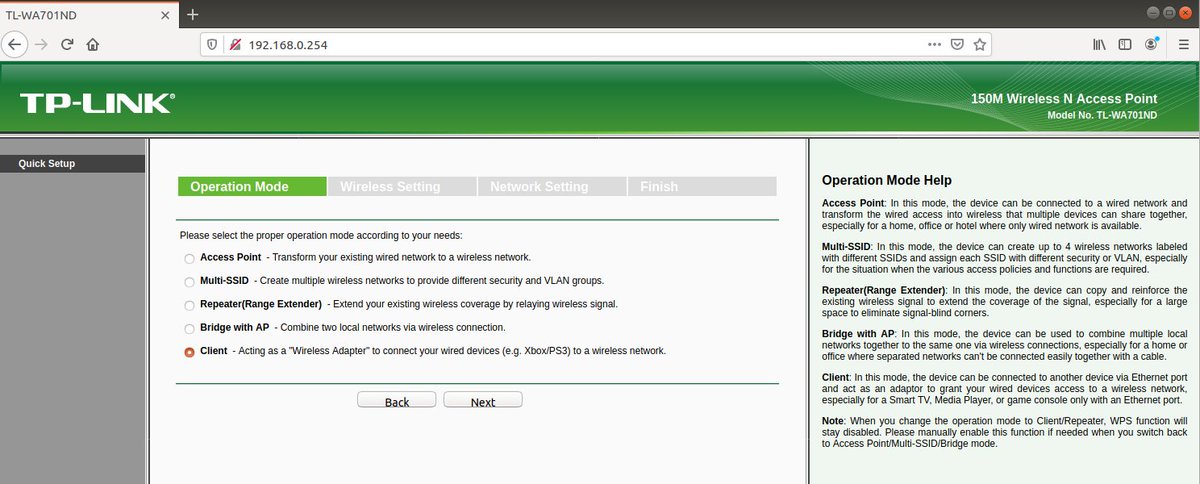
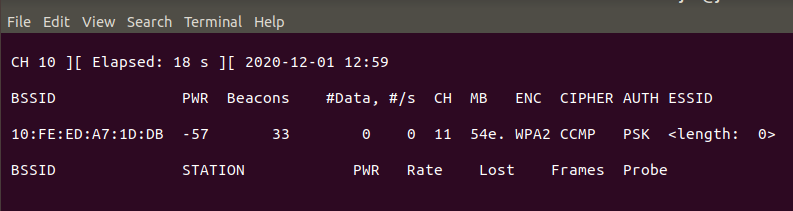
One day while I was scanning around my house for WiFi networks I noticed a high-powered WiFi network with a hidden SSID broadcasting from my main office. With a little more investigation I determined this was coming from the TP-Link, but what was it? 
The user interface doesn't show anything so we're going to have to find another way to get more access. Opening up the device shows four non-populated headers that look suspiciously like debug ports 

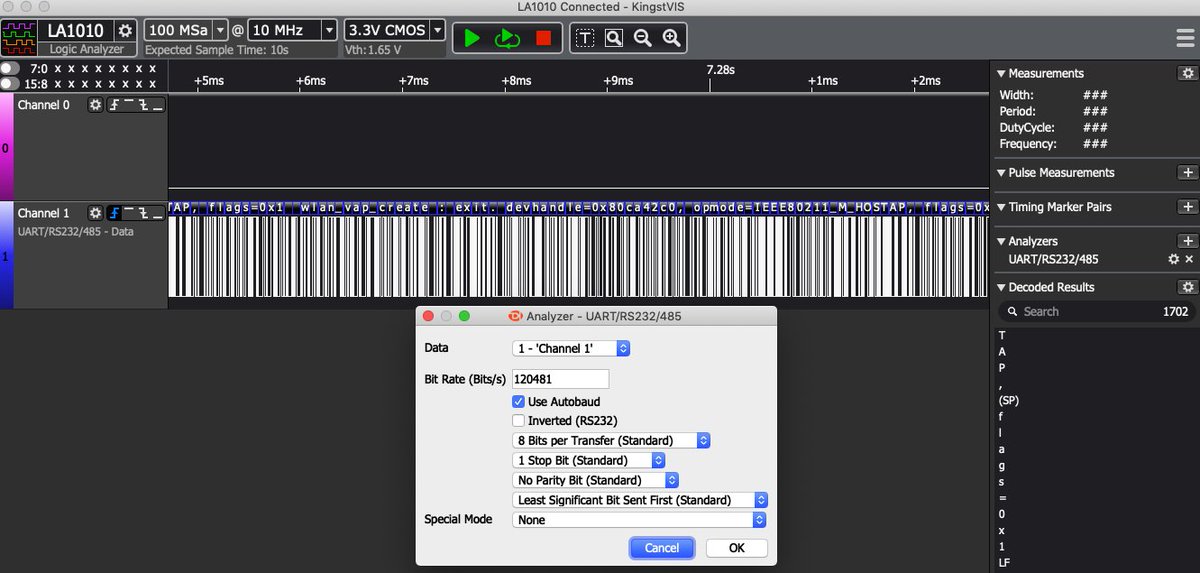
After a quick check with a multimeter to make sure the voltages won't fry my laptop, I connect up a Logic Analyser to work out if there is anything transmitting on any of the pins. I let the analyser work out the baud.
Bingo - we have serial data on 115200 baud!

Bingo - we have serial data on 115200 baud!

Next step, to connect up a USB to serial converter. By power cycling the device, we get a login prompt, but we don't have the credentials to get into it! 


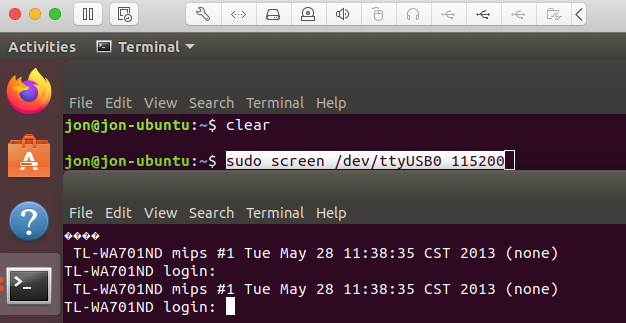
Fortunately there is another way to grab the credentials, we can use the uboot environment that appears before the main OS boots, as shown here with "autobooting in...". Make a note that there appears to be 4MB of flash storage on the device. 
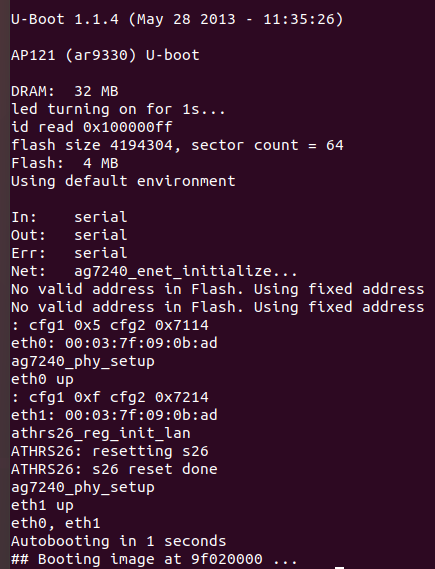
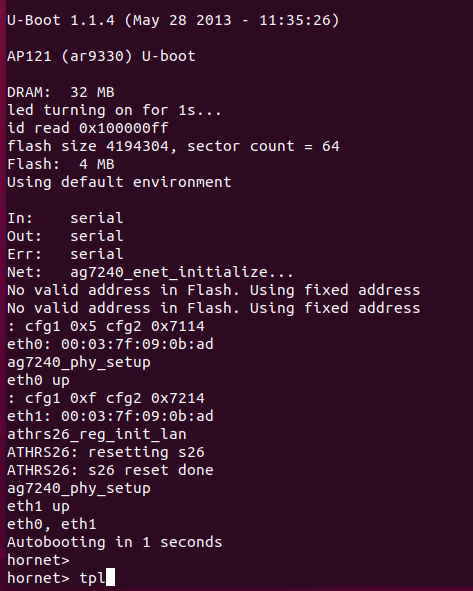
You need to type "tpl" very fast to break into this environment, I found you can either paste into the terminal as the device boots, or just type very quickly. And then we're in! 
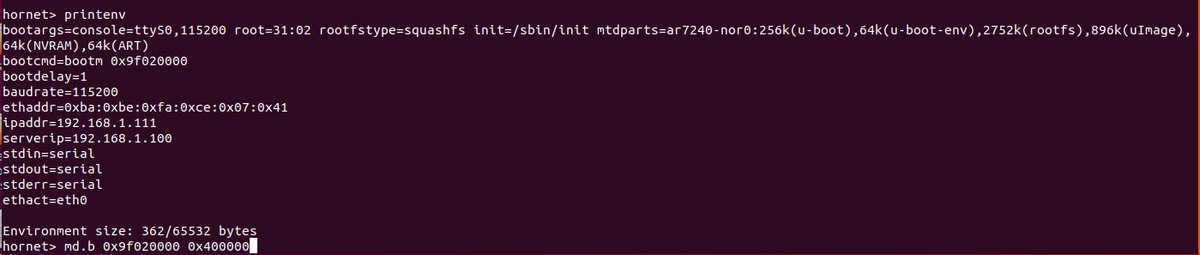
Next step is to dump the firmware of the device. Remember that 4MB of flash from earlier? We'll dump all of that out. 
Now we have all of the flash, we can extract it with binwalk and look around. Oh look, a shadow file with credentials in it. 

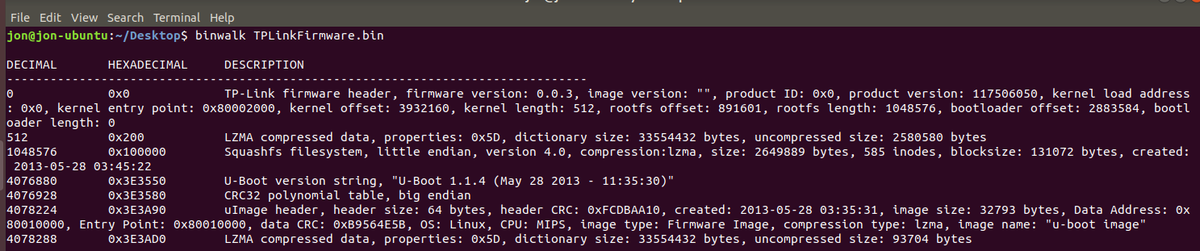
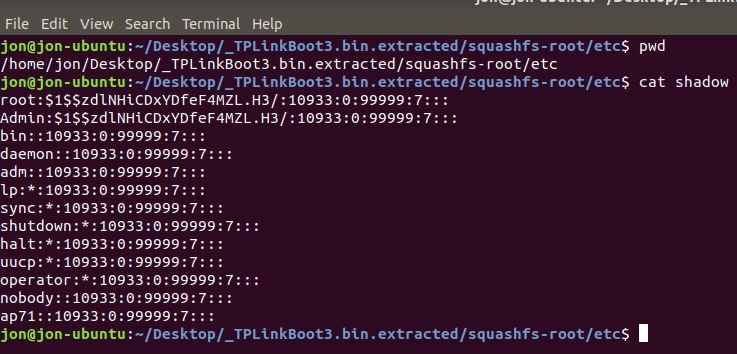
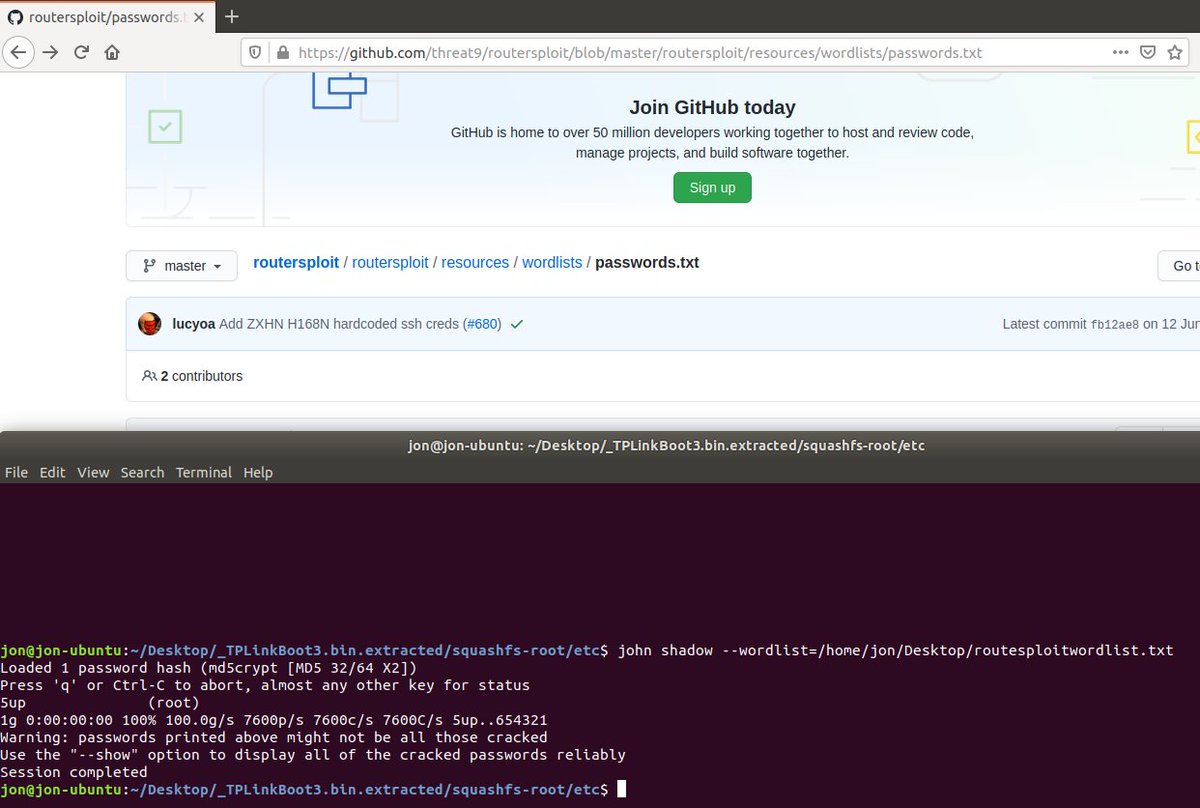
Fortunately there are some great wordlists already out there for cracking embedded devices passwords, and a quick google helps a lot as well. 
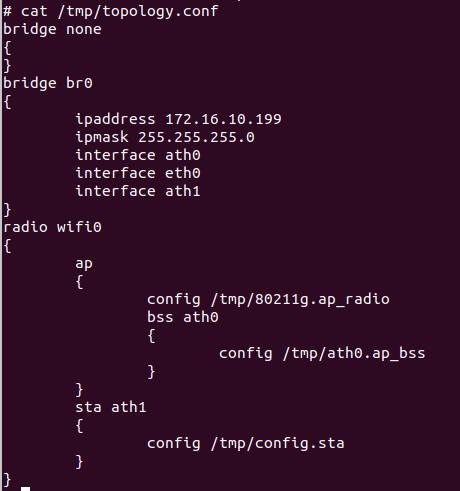
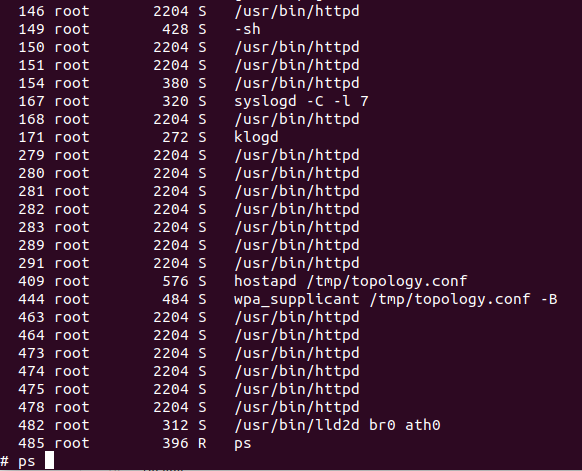
A quick reboot of the device and with the credentials we've just got, we're in! Running 'ps' shows us the processes on the device and as two processes reference the same topology.conf file that's a good place to start. 
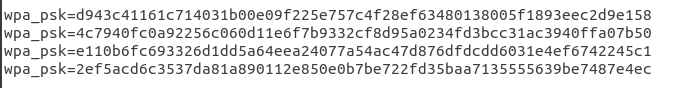
Aha! Look at that PSK, it's massive! Also note that the SSID of the hidden network is based on the MAC address, which is being broadcast by the hidden network, so not exactly hard to find. The question is, have I found the right config file? 
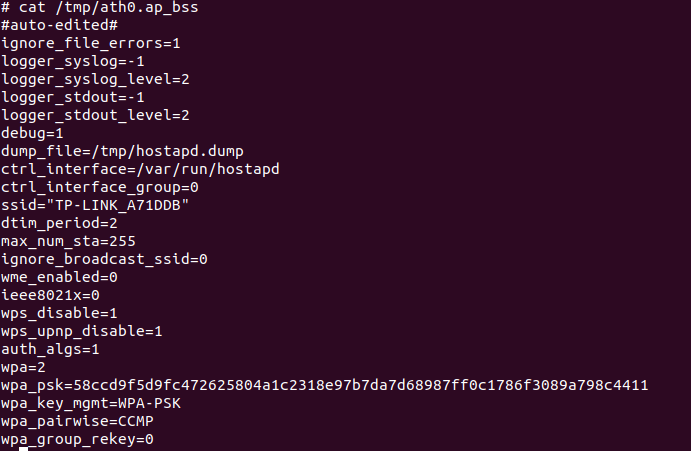
Yep. Connecting with those details lets me into the network. The hidden network in this case is bridging with the other WiFi network that I told the client to connect to, so we have a backdoor into my home network, not fun. But how is that PSK being generated? 

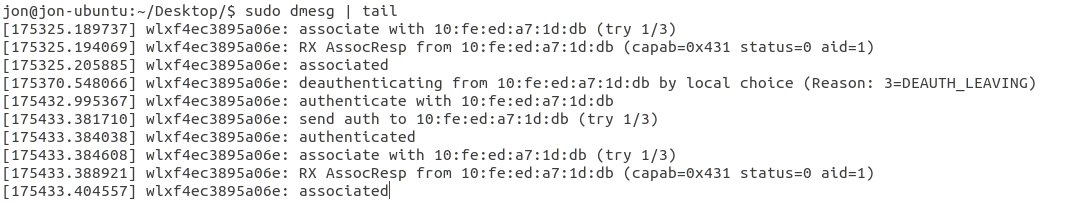
As everything is being run as httpd, that's the place to start. Running strings on the binary we obtained from the firmware dump earlier shows we are probably in the right place, but analysing this is outside of my skill set. The main concern I've got is, is that PSK fixed? 
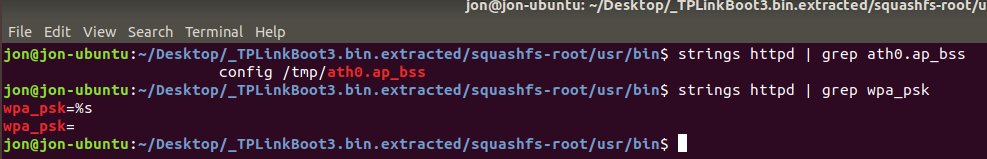
By resetting the AP a few times and setting it back up again shows that the PSK isn't fixed, although it's probably based upon a static string and mangled with a random number. So here ends my investigation, that was fun! 
The MD5 of the httpd binary in this firmware matches the one I see on my device if anyone wants to take look
static.tp-link.com/resources/soft…
static.tp-link.com/resources/soft…
• • •
Missing some Tweet in this thread? You can try to
force a refresh