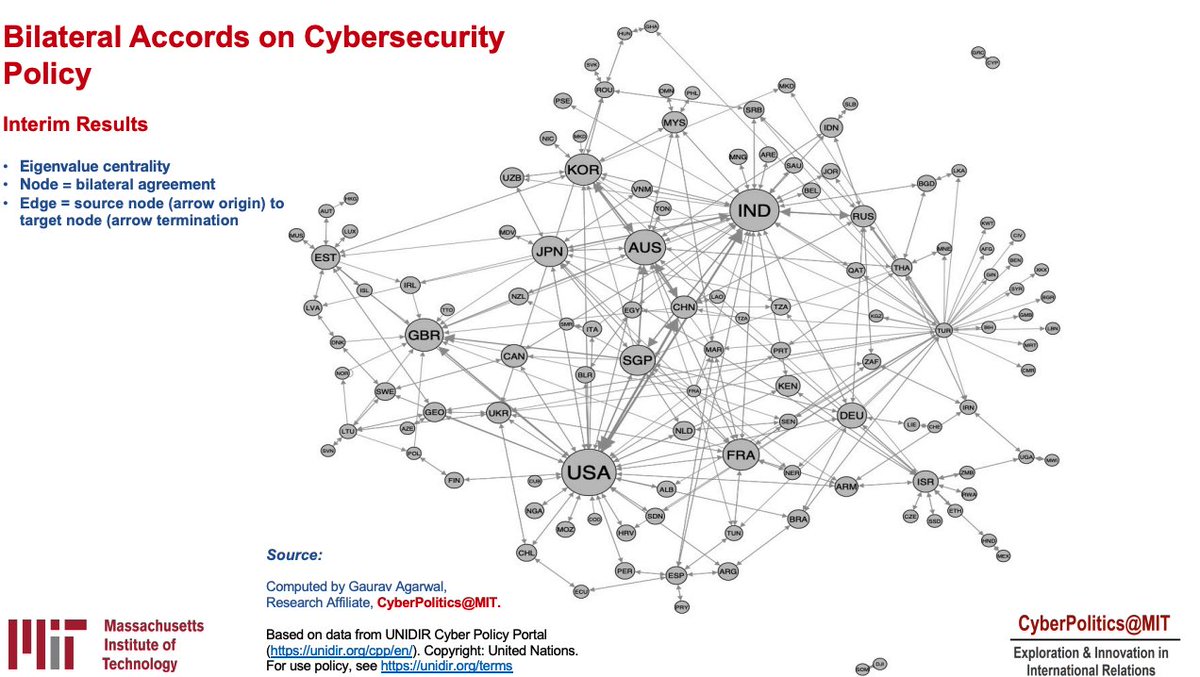
For a company to successfully achieve cyber-resiliency, it needs the full muscle of its leadership teams, across C-suites, boards, and investors. Discussing the emerging and existing threats on the cyber-threat landscape is @mk_palmore. #CyberSecureMIT #TechReviewEvents 

There are four types of adversaries out there:
-The financially-motivated adversary (they’re responsible for the vast majority of adversarial activity)
-The advanced, persistent threat (ie. nation states)
-The insider threat
-The hacktivist
#CyberSecureMIT
-The financially-motivated adversary (they’re responsible for the vast majority of adversarial activity)
-The advanced, persistent threat (ie. nation states)
-The insider threat
-The hacktivist
#CyberSecureMIT

.@mk_palmore is surprised by the prevalence of ransomware because many of these adversaries rely on known vulnerabilities. #CyberSecureMIT
He's also on this data breach investigations report from @VerizonBusiness #CyberSecureMIT enterprise.verizon.com/resources/repo…
And this cloud threat report from his company, @PaloAltoNetEMEA. #CyberSecureMIT start.paloaltonetworks.com/unit-42-cloud-…
You have to think like the cyber-adversary to better protect yourself from cyber threats. #CyberSecureMIT 
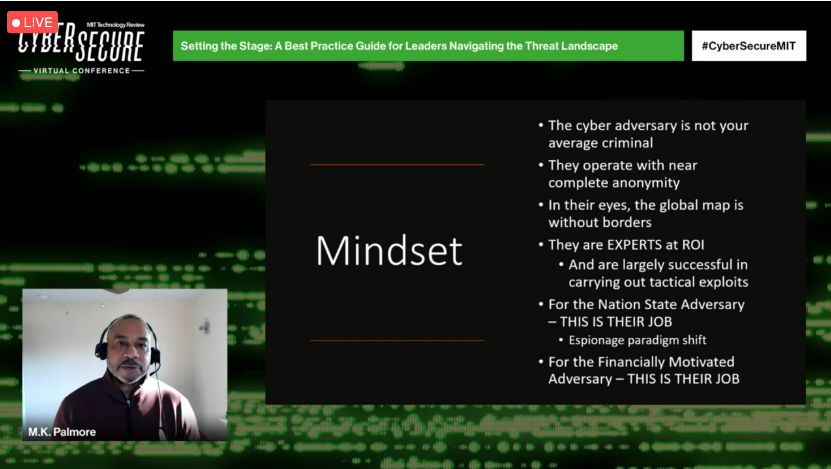
You should assume you will be attacked, and it may be successful. How you respond and recover is that resilience factor. #CyberSecureMIT 

You can lower the impact of cyber-attacks with these best practices. #CyberSecureMIT #TechReviewEvents 

If you enjoyed this thread, consider joining us for the rest of #CyberSecureMIT. Enter the "TWITTER" promo code at checkout to receive a discount on your ticket price.
emtech.technologyreview.com/cyber-secure-2…
emtech.technologyreview.com/cyber-secure-2…
• • •
Missing some Tweet in this thread? You can try to
force a refresh