
From now until Christmas, I will try to share something from my notes / research every day - most of them are old but might still be useful to remember #XMas2020 #AppSec #Web #HTTP
"max-forwards" http header:
- limit the number of proxies a request can traverse.
- not hop-by-hop
- can't go in the Trailer header
Some usage example:
old: securiteam.com/securityreview…
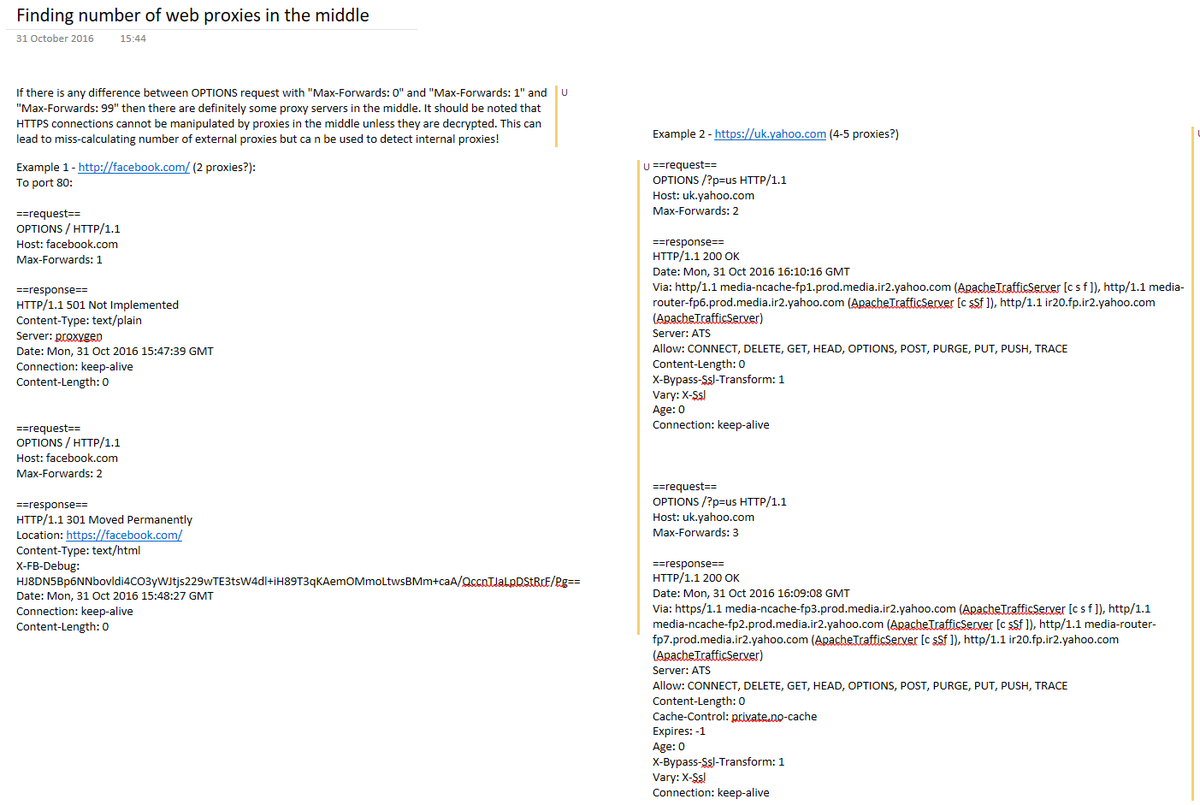
old: counting servers (proxies) in the middle
new: portswigger.net/research/crack…
- limit the number of proxies a request can traverse.
- not hop-by-hop
- can't go in the Trailer header
Some usage example:
old: securiteam.com/securityreview…
old: counting servers (proxies) in the middle
new: portswigger.net/research/crack…
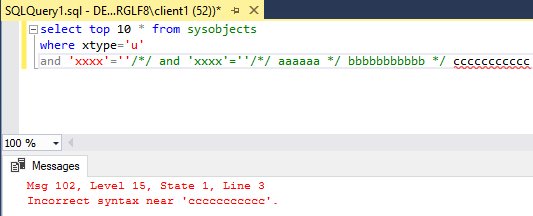
In something like JS
/*/ comment /*/
is the same as
/* comment */
, makes sense, right? But MSSQL sees it as
/* comment /*...
more interestingly, if you want to close it, you need 2 */
This is important when injections go into multiple places and newline is involved!
/*/ comment /*/
is the same as
/* comment */
, makes sense, right? But MSSQL sees it as
/* comment /*...
more interestingly, if you want to close it, you need 2 */
This is important when injections go into multiple places and newline is involved!
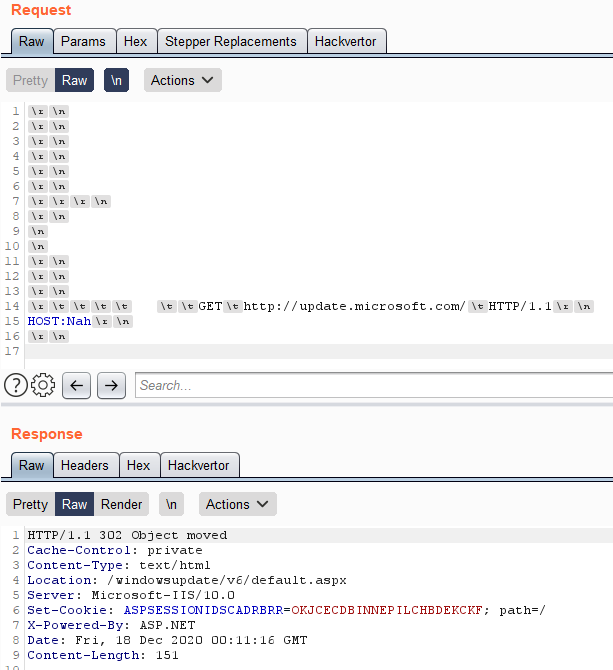
App blocks %0D%0A? we try %0A or %0D or %u2028 or %2029 (using correct encoding).
But also remember to try things like this especially if you are dealing with Java:
%C0%8D%C0%8A
%c4%8a
%EA%A8%8A
Find why & more using r12a.github.io/app-conversion/ and compart.com/en/unicode/sea…
But also remember to try things like this especially if you are dealing with Java:
%C0%8D%C0%8A
%c4%8a
%EA%A8%8A
Find why & more using r12a.github.io/app-conversion/ and compart.com/en/unicode/sea…
Sometimes you just need a simple match/replace in Burp or chain Burps to address problems fast. If you are testing a site that uses JSON, Burp Scanner does not automatically add quotes around numbers (or anything). The following easy match/replace can come in handy for numbers: 

Another example usage of HackVertor extension by @garethheyes can be to bypass WAFs using request encoding (slideshare.net/SoroushDalili/…)
See the screenshots in which a custom tag has been created in HV to do this properly - this was for an APSX page on IIS (catalog.update.microsoft.com/Search.aspx?q=…)


See the screenshots in which a custom tag has been created in HV to do this properly - this was for an APSX page on IIS (catalog.update.microsoft.com/Search.aspx?q=…)



If you are using Windows and like me too lazy to use something like github.com/ptoomey3/evila… to create ".." dir in zip files, you can download 7-zip version 9.20 (sourceforge.net/projects/seven…) and use its GUI! The only limit is that you need to drag and drop files to it 

Fiddler vs. Burp is not a good comparison. Fiddler is not for sec testing but has better performance & can be a life saver when testing some apps in Windows. Chaining `Client App ~> Fiddler -> Burp ~> Target` is normally a good solution and can be done like the screenshots - 1/3 



Burp vs. Fiddler is not a good comparison. Burp doesn't mess with the request to make standard, it sends what you want to send! Fiddler sometimes does not even let you send a mangled request so `if Fiddler is a professional kitchen knife, Burp is a surgical knife` yeaaah! 2/3
The screenshot shows an example of making a request with Burp while Fiddler does not let you send it!
BONUS: a similar req (w a few changes) over HTTP from the victim's box was enough to kill the local @kaspersky 2019 products which doesn't work in the latest version 3/3

BONUS: a similar req (w a few changes) over HTTP from the victim's box was enough to kill the local @kaspersky 2019 products which doesn't work in the latest version 3/3

If you are testing a multi-factor authentication, always check the MFA req after providing victim's credentials - sometimes it might have an object reference which is linked to MFA, change that to attacker's MFA ID as you have its value - a bizarre issue but can happen ;)
Reviewing .NET MVC Razor? Some quick tips next to normal checks:
> XSS: +@html.raw ->
> CSRF: +IgnoreAntiforgeryToken -ValidateAntiforgeryToken -AutoValidateAntiforgeryToken
> `Request`, `[HTTP`, `Route` to find paths/params
vulncat.fortify.com/en/weakness?co…
syncfusion.com/blogs/post/10-…
> XSS: +@html.raw ->
> CSRF: +IgnoreAntiforgeryToken -ValidateAntiforgeryToken -AutoValidateAntiforgeryToken
> `Request`, `[HTTP`, `Route` to find paths/params
vulncat.fortify.com/en/weakness?co…
syncfusion.com/blogs/post/10-…
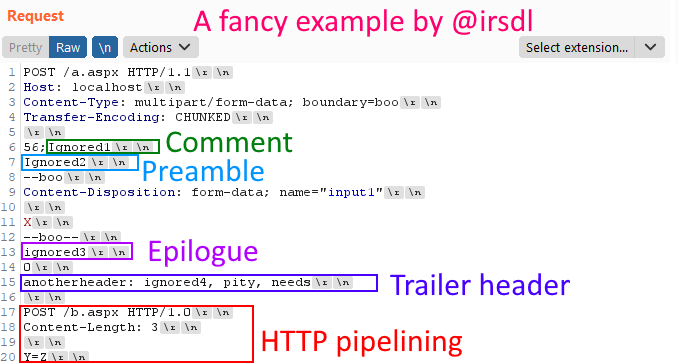
Trailer headers in HTTP 1/2:
- Additional header in the body of a HTTP request
- Come with `Transfer-Encoding: chunked` after the last 0\r\n and ends with
- There is a disallowed list in browsers
But, RFC does not limit it to HTTP Response, so can this be abused in requests?
- Additional header in the body of a HTTP request
- Come with `Transfer-Encoding: chunked` after the last 0\r\n and ends with
- There is a disallowed list in browsers
But, RFC does not limit it to HTTP Response, so can this be abused in requests?
Trailer headers in HTTP 2/2:
The trailer headers used to work at least until 2013 in PHP and Apache: martin.swende.se/blog/HTTPChunk…
httpd.apache.org/docs/2.4/mod/c…
However, IIS & Apache show error if you miss the : in the trailer header so it is somehow being validated but ignored?


The trailer headers used to work at least until 2013 in PHP and Apache: martin.swende.se/blog/HTTPChunk…
httpd.apache.org/docs/2.4/mod/c…
However, IIS & Apache show error if you miss the : in the trailer header so it is somehow being validated but ignored?


Removing headers by proxy: in 2016, I had written this note to remove some headers from a request:
"Connection header can be used to remove other headers after it passes through a proxy - not limited to the hop-by-hop headers..."
Little I knew about @albinowax research
"Connection header can be used to remove other headers after it passes through a proxy - not limited to the hop-by-hop headers..."
Little I knew about @albinowax research

In the past I have found many deserialization issues in .NET by source code review. Here is my list to find interesting points to start with:
gist.github.com/irsdl/9315521b…
If you want to know what to do next when you are in control, read the references in ysoserial .net
gist.github.com/irsdl/9315521b…
If you want to know what to do next when you are in control, read the references in ysoserial .net
My most faved tips in last 3yrs
https://twitter.com/irsdl/status/1259928358726635522?s=20
https://twitter.com/irsdl/status/1267420747363946496?s=20
https://twitter.com/irsdl/status/1131926233967726592?s=20
https://twitter.com/irsdl/status/1267195731439427585?s=20
https://twitter.com/irsdl/status/1264879988651757568?s=20
https://twitter.com/irsdl/status/1263080507367178240?s=20
https://twitter.com/irsdl/status/1156964410985984000?s=20
https://twitter.com/irsdl/status/1239310942158180352?s=20
https://twitter.com/irsdl/status/1125149974302470145?s=20
https://twitter.com/irsdl/status/1126990791828754433?s=20
RFC - 1/2: I started reading boring RFCs after learning this from other researchers. I love them now, here is why:
- I would understand a technology better to find more sec bugs
- Inconsistent implementations -> Canonical/Sec Issues
See RFC2119 -> even that needed RFC8174!!! 😄
- I would understand a technology better to find more sec bugs
- Inconsistent implementations -> Canonical/Sec Issues
See RFC2119 -> even that needed RFC8174!!! 😄

RFC - 2/2: Here is where I normally find the most interesting stuffs:
- Relaxed rules (SHOULD,MAY,...)
- Vague rules (is it clear enough to be implemented?)
- Complicated and/or parsing rules
- Changes in new versions
- Delimiters! (love it)
- Usage in other RFCs (more targets)
- Relaxed rules (SHOULD,MAY,...)
- Vague rules (is it clear enough to be implemented?)
- Complicated and/or parsing rules
- Changes in new versions
- Delimiters! (love it)
- Usage in other RFCs (more targets)
RFC - 2.001/2;: Logical issues can be missed by fuzzers that might detect hard to find [parsing] issues.
To find simple examples of identified issues by reading RFCs, see stuffs that have been done to bypass WAFs by reshaping a HTTP request.
Screenshots from my notes of RFC2616🤔

To find simple examples of identified issues by reading RFCs, see stuffs that have been done to bypass WAFs by reshaping a HTTP request.
Screenshots from my notes of RFC2616🤔


Burp Java Ext Debugging 1/3:
Most Burp extension writers do not use debugging and use the old style print line by line approach 😁The solution is easy for Java without running burp in legacy mode (jython can be memory intensive when code is not quality like most mine)
Most Burp extension writers do not use debugging and use the old style print line by line approach 😁The solution is easy for Java without running burp in legacy mode (jython can be memory intensive when code is not quality like most mine)
... 2/3:
NetBeans, Eclipse, & IntelliJ all support Remote Debugging (google it for your favourite IDE).
IJ Example:
0) Get this github.com/irsdl/EmptyBur… for start (🙏to @alexlauerman) and open it in IJ
1) Run> Edit Configurations...
2) Templates> Remote JVM Debug> Set your port

NetBeans, Eclipse, & IntelliJ all support Remote Debugging (google it for your favourite IDE).
IJ Example:
0) Get this github.com/irsdl/EmptyBur… for start (🙏to @alexlauerman) and open it in IJ
1) Run> Edit Configurations...
2) Templates> Remote JVM Debug> Set your port


... 3/3:
3) Run burp.jar with required debug args - e.g.: github.com/irsdl/BurpRunn…
4) Load your Burp extension after building the latest jar version in IJ (ensure there is no error)
5) Run MyBurpDebug
6) Set a breakpoint
7) Reload the extension (ctrl+click)
8) Proper debug time😎



3) Run burp.jar with required debug args - e.g.: github.com/irsdl/BurpRunn…
4) Load your Burp extension after building the latest jar version in IJ (ensure there is no error)
5) Run MyBurpDebug
6) Set a breakpoint
7) Reload the extension (ctrl+click)
8) Proper debug time😎




SalesForce apps tips; cmn vulns:
SOQL & SOSL injections, XSS, CSRF, Access control issues, Insecure storages, Insecure communications/cryptographic modules, etc.
>know.bishopfox.com/research/sfdc-…
>vulncat.fortify.com/en/weakness?co…
-Apex in classes+triggers
-Make valid requests from Apex
& more ;)


SOQL & SOSL injections, XSS, CSRF, Access control issues, Insecure storages, Insecure communications/cryptographic modules, etc.
>know.bishopfox.com/research/sfdc-…
>vulncat.fortify.com/en/weakness?co…
-Apex in classes+triggers
-Make valid requests from Apex
& more ;)



- Mental health is important; don't be afraid of seeking help & sharing with someone. Don't suffer in silence, it's not just you!
- Improve your soft skills
- Share notes/tools/etc but avoid re-inventing the wheel/rediscover XSS
- Reference other people's work
Happy Holidays 🎅
- Improve your soft skills
- Share notes/tools/etc but avoid re-inventing the wheel/rediscover XSS
- Reference other people's work
Happy Holidays 🎅
@UnrollHelper unroll please
• • •
Missing some Tweet in this thread? You can try to
force a refresh


