Can we just have one quiet weekend...
https://twitter.com/Bing_Chris/status/1338194968389840897
Can confirm @Bing_Chris's report that several federal agencies incl NTIA are investigating breaches seemingly tied to nation-state hackers.
"It's not entirely certainly what vulnerability they're using, how they got in, but it continues to be a problem," a U.S. official told me.
"It's not entirely certainly what vulnerability they're using, how they got in, but it continues to be a problem," a U.S. official told me.
"The FBI's on site" at the Commerce Department, the parent agency of NTIA, per this official.
Emergency NSC meeting yesterday, this person said.
"It seems like it's gonna be a much bigger issue, but there's not a lot of firm understanding of how broad the scale is."
Emergency NSC meeting yesterday, this person said.
"It seems like it's gonna be a much bigger issue, but there's not a lot of firm understanding of how broad the scale is."
In addition to the FBI, CISA is providing support, and ODNI and U.S. Cyber Command have gotten involved.
"When CyberCom starts getting involved in something, it's a big deal," U.S. official said. "The implication is that it's a nation-state confrontation."
"When CyberCom starts getting involved in something, it's a big deal," U.S. official said. "The implication is that it's a nation-state confrontation."
The attack appears to have involved victims' Microsoft authentication tokens, raising concerns that the same techniques could be used on a wider scale.
"This seems to be connected to microsoft in some way," U.S. official said.
"This seems to be connected to microsoft in some way," U.S. official said.
.@nakashimae is reporting that Russia's foreign intelligence service, the SVR, is behind these federal agency intrusions: washingtonpost.com/national-secur…
The SVR was also reportedly behind the FireEye hack.
The SVR was also reportedly behind the FireEye hack.
@nakashimae When FireEye announced its breach, it said that it was working with Microsoft to investigate.
Seems possible that these attacks are connected in terms of technique not just perpetrator.
Seems possible that these attacks are connected in terms of technique not just perpetrator.
From Reuters' story: "Hackers broke into the NTIA’s office software, Microsoft’s Office 365. Staff emails at the agency were monitored by the hackers for months..."
The hackers were "able to trick the Microsoft platform’s authentication controls..."
reuters.com/article/us-usa…
The hackers were "able to trick the Microsoft platform’s authentication controls..."
reuters.com/article/us-usa…
A bit more specificity on timing, per a U.S. official: Investigators believe that the hackers had been monitoring federal workers' emails since June.
Fear is that "the same techniques…could have been leveraged against other agencies," since "everybody uses Microsoft products."
Fear is that "the same techniques…could have been leveraged against other agencies," since "everybody uses Microsoft products."
Solar Winds' other government customers, per its website: Census Bureau, DOJ, Oak Ridge and Sandia National Labs, VA, Army, Air Force, Navy, and Marine Corps. solarwinds.com/federal-govern…
Plus state, local, educational, and foreign customers, e.g. Texas, NHS, and European Parliament.
Plus state, local, educational, and foreign customers, e.g. Texas, NHS, and European Parliament.
https://twitter.com/nakashimae/status/1338244109107163137
CISA statement: “We have been working closely with our agency partners regarding recently discovered activity on government networks. CISA is providing technical assistance to affected entities as they work to identify and mitigate any potential compromises.”
NTIA referred to Commerce, which said: "We can confirm there has been a breach in one of our bureaus. We have asked CISA and the FBI to investigate, and we cannot comment further at this time."
NSC spokesman John Ullyot: “The United States government is aware of these reports and we are taking all necessary steps to identify and remedy any possible issues related to this situation.”
FBI and Treasury Department have not provided comments yet.
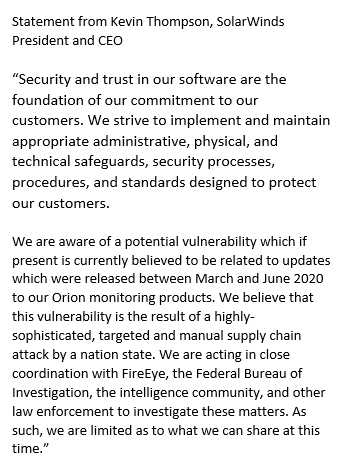
Solar Winds, IT firm used by federal agency victims, says "a highly-sophisticated, targeted and manual supply chain attack by a nation state" compromised the software updates released earlier this year for its Orion IT monitoring platform. 
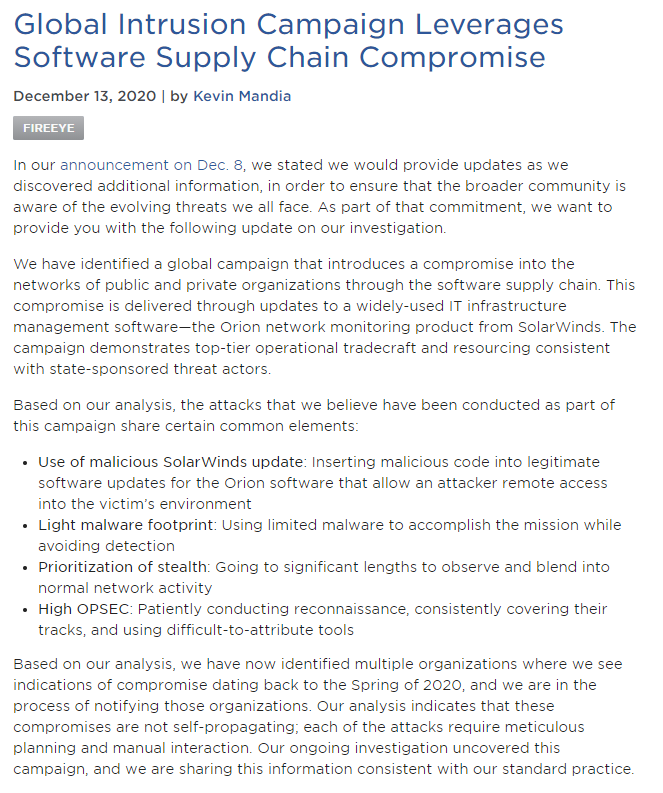
Confirming earlier suspicions, FireEye says that its breach was part of a global campaign of cyberattacks leveraging a compromised SolarWinds Orion software update.
FireEye is notifying victims it discovers.
fireeye.com/blog/products-…
Technical details: fireeye.com/blog/threat-re…
FireEye is notifying victims it discovers.
fireeye.com/blog/products-…
Technical details: fireeye.com/blog/threat-re…
🚨 CISA has issued an emergency order requiring federal agencies to disable SolarWinds IT products, which hackers exploited to penetrate Treasury, NTIA, and possibly other agencies. cyber.dhs.gov/ed/21-01/
Disconnection "is the only known mitigation measure currently available."
Disconnection "is the only known mitigation measure currently available."
Microsoft has published a report on the hacking campaign that has breached several federal agencies. It confirms that the intruders used SolarWinds product vulnerabilities for initial access and then forged authentication tokens to spread further. msrc-blog.microsoft.com/2020/12/13/cus…
Worth noting: Trump eliminated the position of White House cyber coordinator in 2018 and fired the CISA director last month.
https://twitter.com/WHNSC/status/1338454126120882179
The rationale for eliminating the cyber coordinator was that the government's cyber work would be coordinated enough without it.
Now we'll see how true that is.
Now we'll see how true that is.
No surprise here, but the NSC has activated PPD-41 (obamawhitehouse.archives.gov/the-press-offi…) and stood up the government's Cyber Response Group to respond to the breaches of various agencies.
They're holding a phone meeting (NSC PCC level) today, a U.S. official tells me.
They're holding a phone meeting (NSC PCC level) today, a U.S. official tells me.
One problem for the CRG as it tries to get a handle on the situation: The government doesn't even have a full list of which agencies use the SolarWinds products that led to the initial compromise, per person familiar. "FISMA/FITARA require inventories, but it’s an absolute mess."
Solar Winds says in a new SEC filing that it believes 33,000 Orion customers were vulnerable to the malicious software updates, but "the actual number" with infected products is likely "fewer than 18,000."
Note oblique reference to O365 vector...
sec.gov/ix?doc=/Archiv…
Note oblique reference to O365 vector...
sec.gov/ix?doc=/Archiv…

At the risk of jinxing everything, this could have been much worse.
https://twitter.com/a_greenberg/status/1338508457515872261
As news breaks about DHS falling victim to this hacking campaign, a U.S. official tells me that there's "massive frustration with CISA on a sluggish response to agency breaches."
According to this official, "incident response teams" meant to assist victim agencies "are delayed."
According to this official, "incident response teams" meant to assist victim agencies "are delayed."
https://twitter.com/Bing_Chris/status/1338552048342753288
New from a spokesperson for the IT office in Texas, where some state agencies used SolarWinds: "We have informed known users...and provided them with countermeasures."
IT staff are "actively engaged with our federal, state, and industry partners."
IT staff are "actively engaged with our federal, state, and industry partners."
• • •
Missing some Tweet in this thread? You can try to
force a refresh