I have report from Microsoft about SolarWinds hack, including IoCs. Excerpts in this thread: "Microsoft security researchers recently discovered a sophisticated attack where an adversary inserted malicious code into a supply chain development process.... 1/
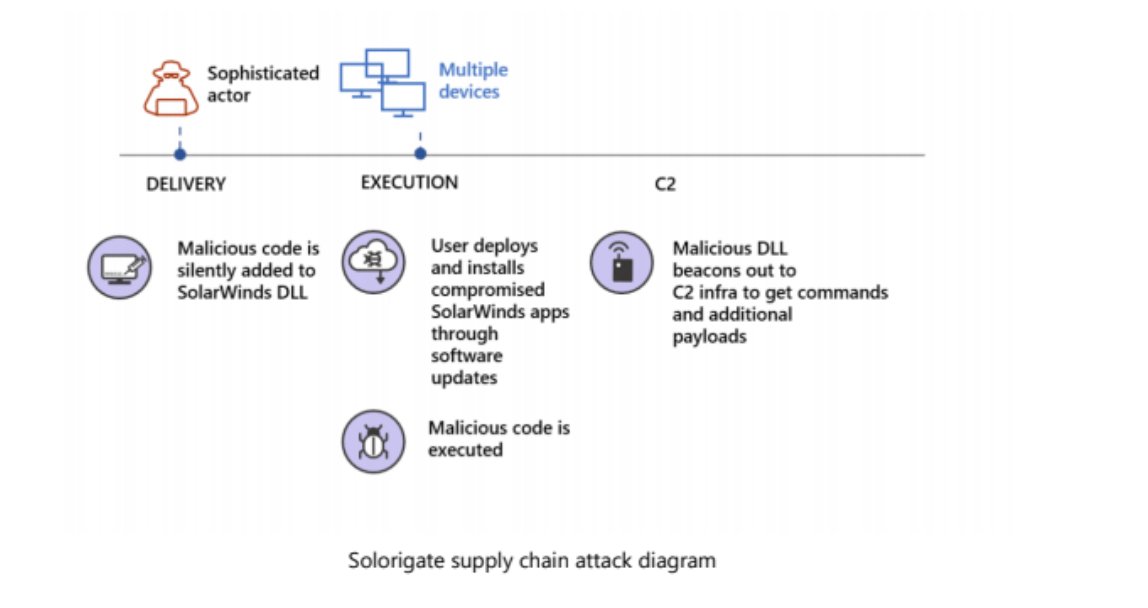
"A malicious software class was included among many other legitimate classes and then signed with a legitimate certificate. The resulting binary included a backdoor and was then discreetly distributed into targeted organizations.... 2/
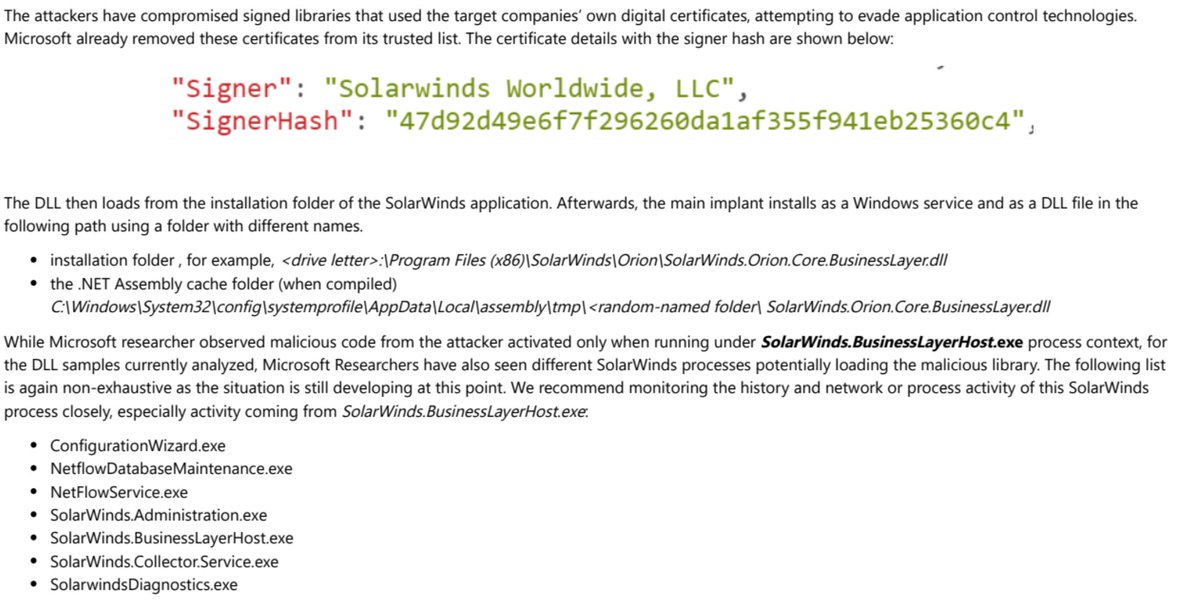
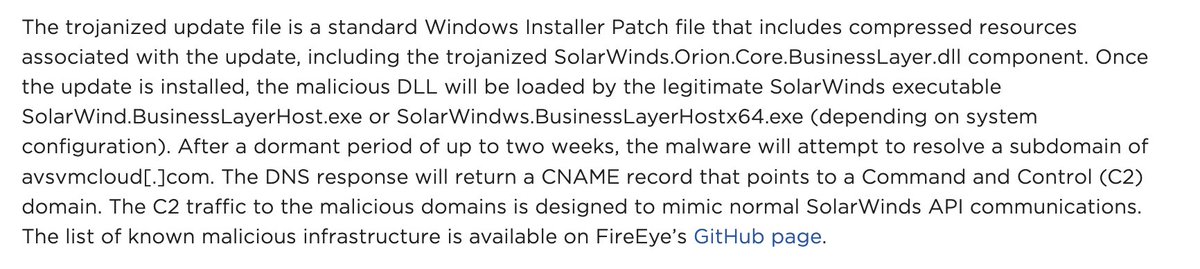
"we do not know how the backdoor code made it into the library..research indicates...the attackers might have compromised internal build or distribution systems of SolarWinds, embedding backdoor..into a legitimate SolarWinds library" - SolarWinds.Orion.Core.BusinessLayer.dll 4/
"While updating the SolarWinds application, the embedded backdoor code loads before the legitimate code runs. Organizations are misled into believing that no malicious activity has occurred and that the program or application dependent on the libraries is behaving as expected."
"The malicious DLL calls out to a remote network infrastructure using the domains avsvmcloud.com. to prepare possible second-stage payloads, move laterally in the organization, and compromise or exfiltrate data"
Oh, and it looks like Microsoft released a patch for the SolarWinds hack yesterday, which it is calling "Solorigate."
"Microsoft detects the main implant and its other components as Solorigate." microsoft.com/en-us/wdsi/thr…
"Microsoft detects the main implant and its other components as Solorigate." microsoft.com/en-us/wdsi/thr…
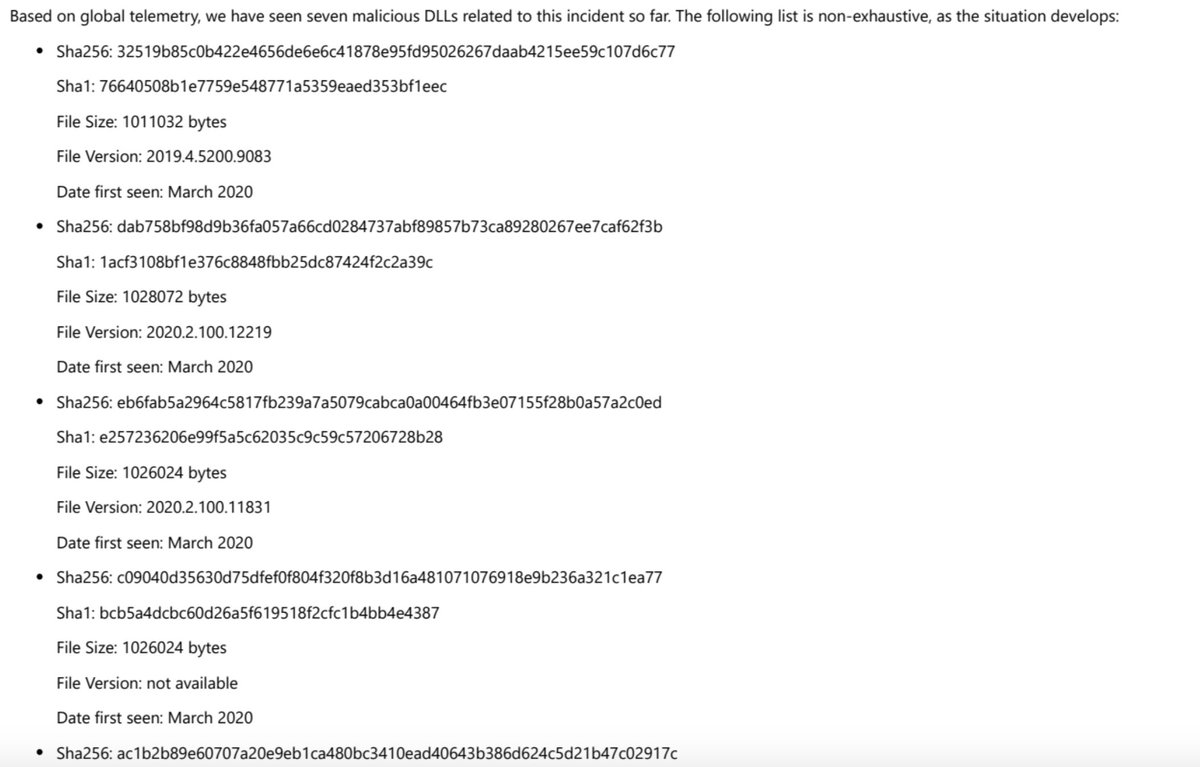
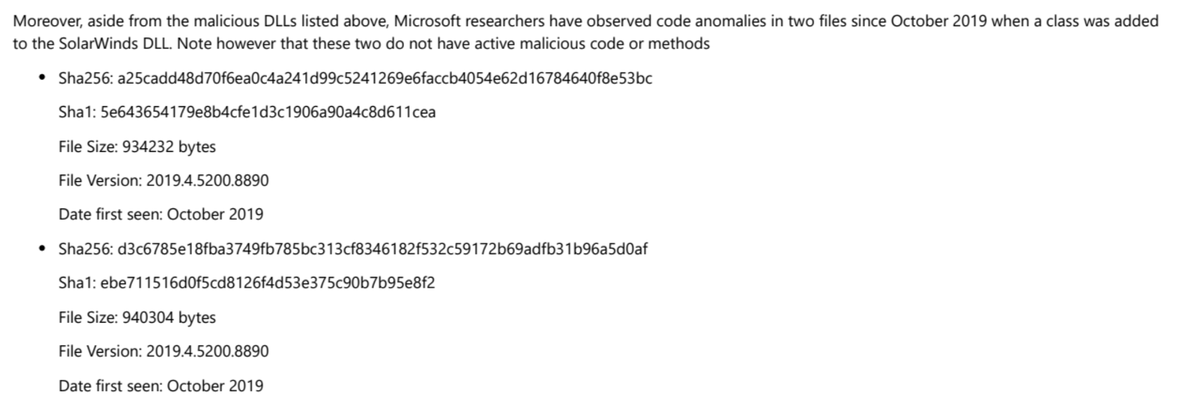
I didn't get all of the DLL hashes into my previous excerpt so here are the rest of them. I'm sorry these are just images, making it impossible to copy/paste. But you can get the report from Microsoft for this info and more. 
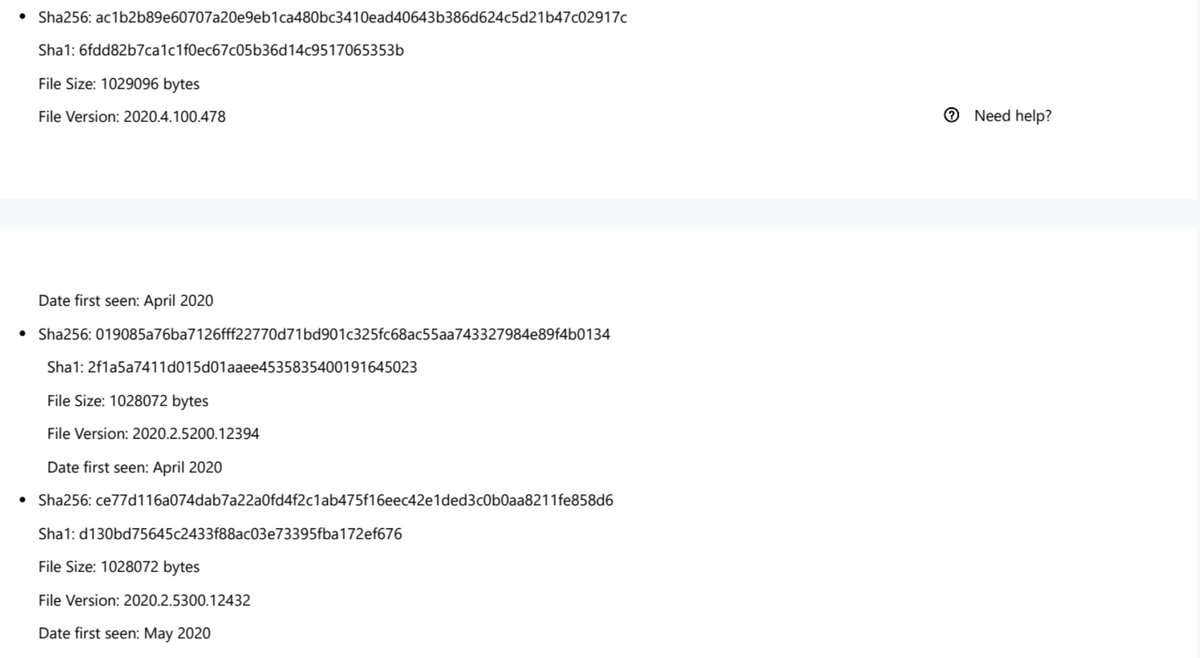
Apologies for calling the Windows Defender update a patch. To clarify, Microsoft did not release a patch for the SolarWinds vuln, they released an update to their definitions to detect the malicious SolarWinds DLL.
Here is FireEye's report on the SolarWind hack, published today. They're calling the threat SUNBURST: fireeye.com/blog/threat-re…
SolarWinds: "We are recommending you upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible..The latest version is available in the...Customer Portal..An additional hotfix release, 2020.2.1 HF 2 is anticipated to be made available Tues Dec 15" solarwinds.com/securityadviso…
This is from FireEye: "After an initial dormant period of up to two weeks, it retrieves and executes commands, called 'Jobs', that include the ability to transfer files, execute files, profile the system, reboot the machine, and disable system services...
"The malware masquerades its network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files allowing it to blend in with legitimate SolarWinds activity...
"The backdoor uses multiple obfuscated blocklists to identify forensic and anti-virus tools running as processes, services, and drivers....Multiple trojanzied updates were digitally signed from March - May 2020 and posted to the SolarWinds updates website"
"The victims have included government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East. We anticipate there are additional victims in other countries and verticals."
.@CISAgov has issued an emergency directive on actions that gov agencies need to take immediately to mitigate against the SolarWinds threat: cyber.dhs.gov/ed/21-01/ 
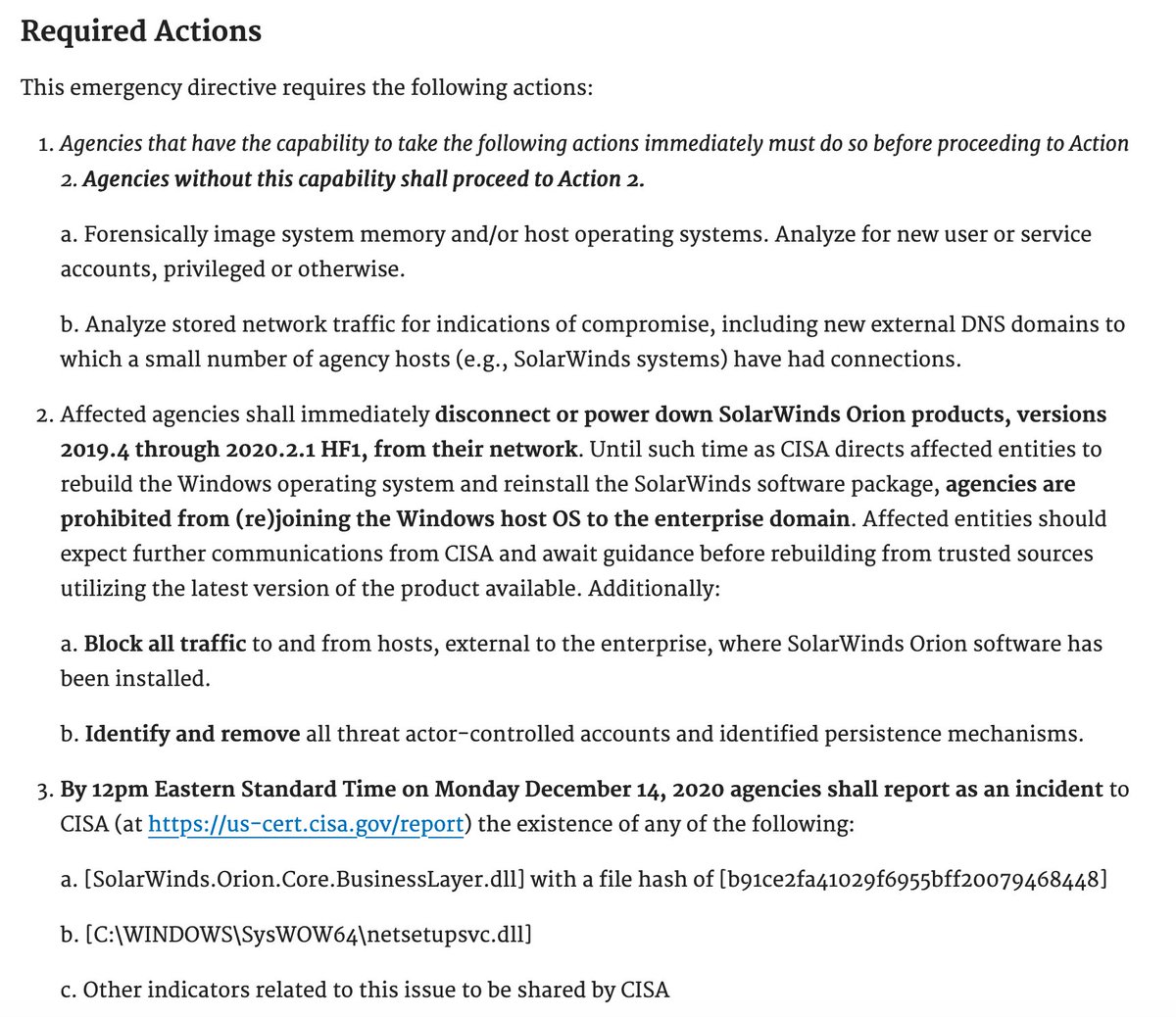
More from the @CISAgov emergency directive for gov agencies re SolarWinds threat 
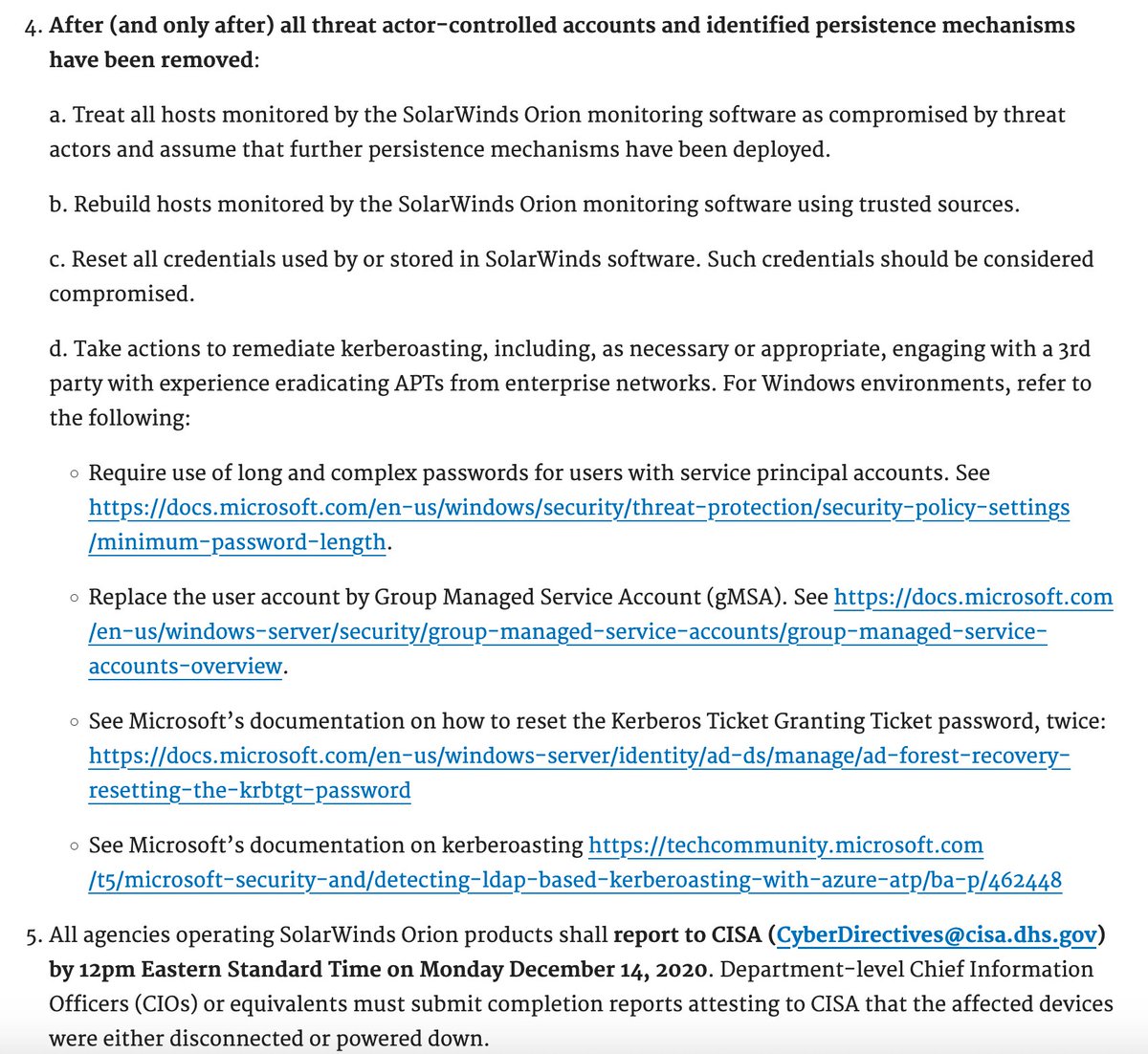
• • •
Missing some Tweet in this thread? You can try to
force a refresh