
I've been using AutoRepeater for years & I know from collabs/experience that not all are using it. I find it works magic in automating access control or other types of tests if you know how to configure it, so let's make an epic thread for AutoRepeater! #infosec #bugbounty [1]
AutoRepeater (AR) allows you to replace stuff on requests, with creative you can test limitless scenarios. It has 2 tabs 1) Base Replacements, 2) Replacements. Replacements are applied on top of Base Replacements. For each Replacement, a new request is generated. [2]
Let's look at a standard example. An app trasmits the organisation's UUID for operations in cookies, URL and other HTTP headers. Test its access control by replacing a string across the whole request, in this case the UUID. [3] 

When testing for access control flaws, it's vital you replace all relevant info properly to not break requests. "0" in "Resp. Len. Diff." column is likely to mean you found an issue as the response is the same, but it could be boring/resources. I sort requests in DESC mode. [4]
Assume you are testing for access control, but there's a CSRF HTTP header token too. You can now use 1 Base Replacement for session cookies together with Replacement rules for the CSRF token (remove it, replace it with attacker's one). See screenshots. [5] 



AutoRepeater allows you to perform ANY replacement ANY kind of testing if you practice it's replacement types and regular expressions. My favorite ones though are "Match Param/Cookie/Header Name, Replace Value" and "Remove by Name". [6]
Even automating privilege escalation testing is possible (as I said anything is possible). See screenshot for example rules, but you need to ensure replacements work in your case and a good method to filter results. Just configure and test the rules, and sweep the whole app. [7] 

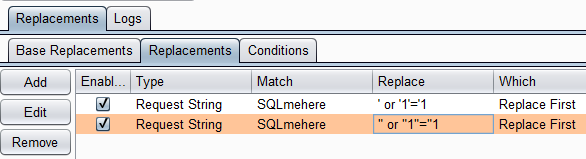
You can export/import your AutoRepeater rules from top level menu so you can create profiles for testing generic injections such as SQLi. Instead of manually testing 10 payloads through Repeater, you can submit 1 payload turn this into 10 requests/payloads. [8] 

To achieve this, create multiple Replacement rules using the same placeholder such as "InjectHereXSS". Ensure Conditions matches requests from any Burp tool or Proxy/Repeater. See screenshot for basic SQLi automation example. [9] 
In complex apps/environments (multiple sites) you want to filter results efficiently. You can use the Log Highlighter with AND/OR conditions. In this example I am flagging in green requests that led to 403/401 errors or returned specific permission error messages. [10] 

I usually tend to start building AutoRepeater configuration/rules/conditions, and manually inspect the modified responses. When I learn how the application behaves/errors etc, I carry on improving the configuration so I can sweep it quicker, efficiently but also accurately. [11]
Finally, AutoRepeater is a #BurpSuite plugin and it exists thanks to Justin Moore from @NCCGroupInfosec, but also the rest of its contributors. If you are going to try it, download from GitHub repo and not BApp Store as the version there is outdated. Also check the repo's wiki :)
• • •
Missing some Tweet in this thread? You can try to
force a refresh


