Are tweets about Xinjiang from @ChineseEmbinUS being artificially amplified by a network of repetitively named batch-created accounts? (Spoiler: yes, and they retweet other Chinese diplomatic and state media accounts as well.)
cc: @ZellaQuixote
cc: @ZellaQuixote
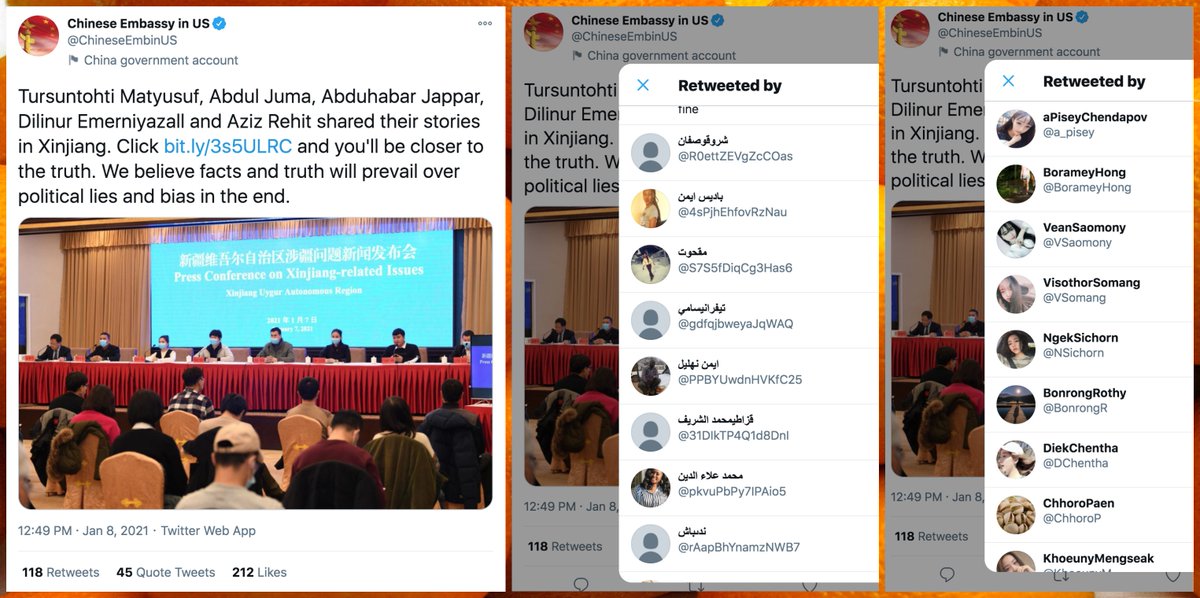
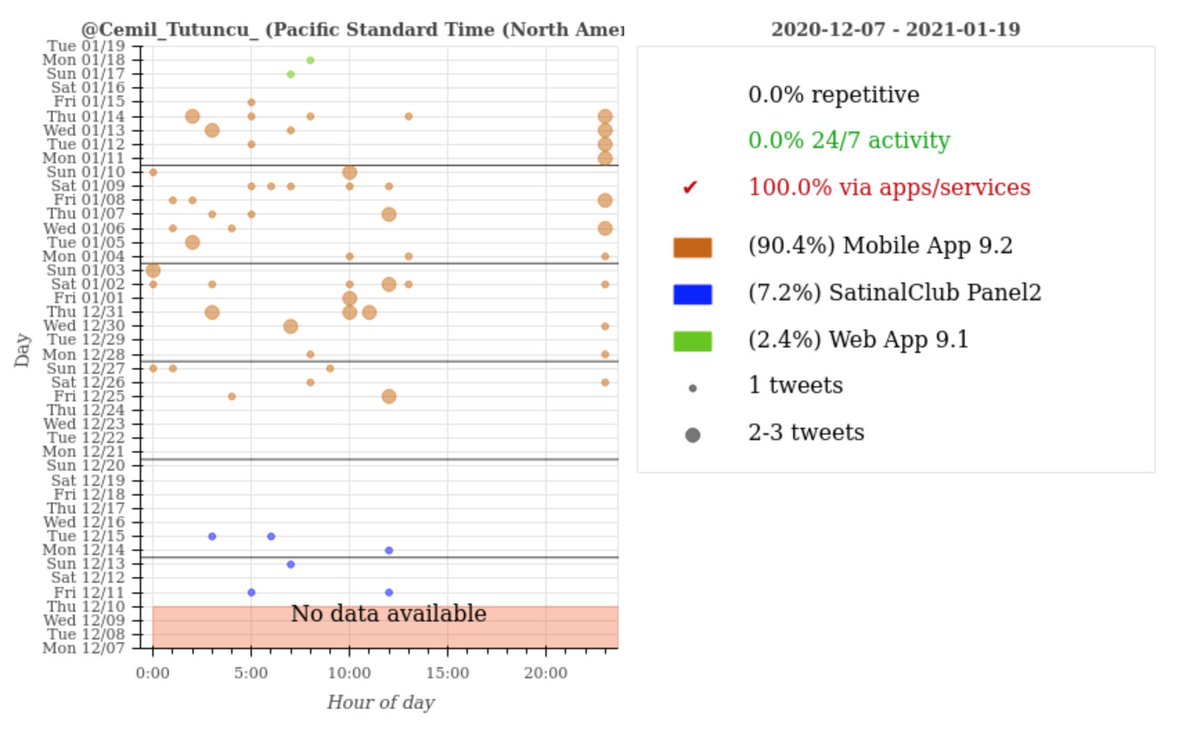
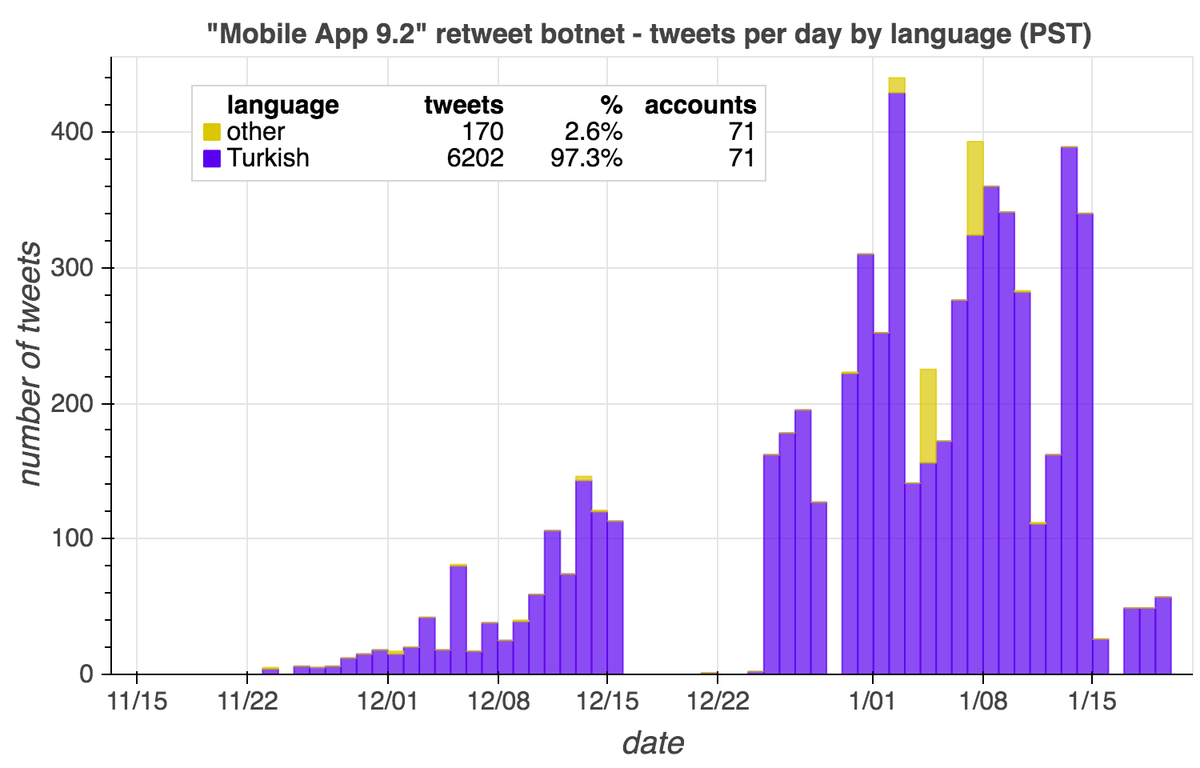
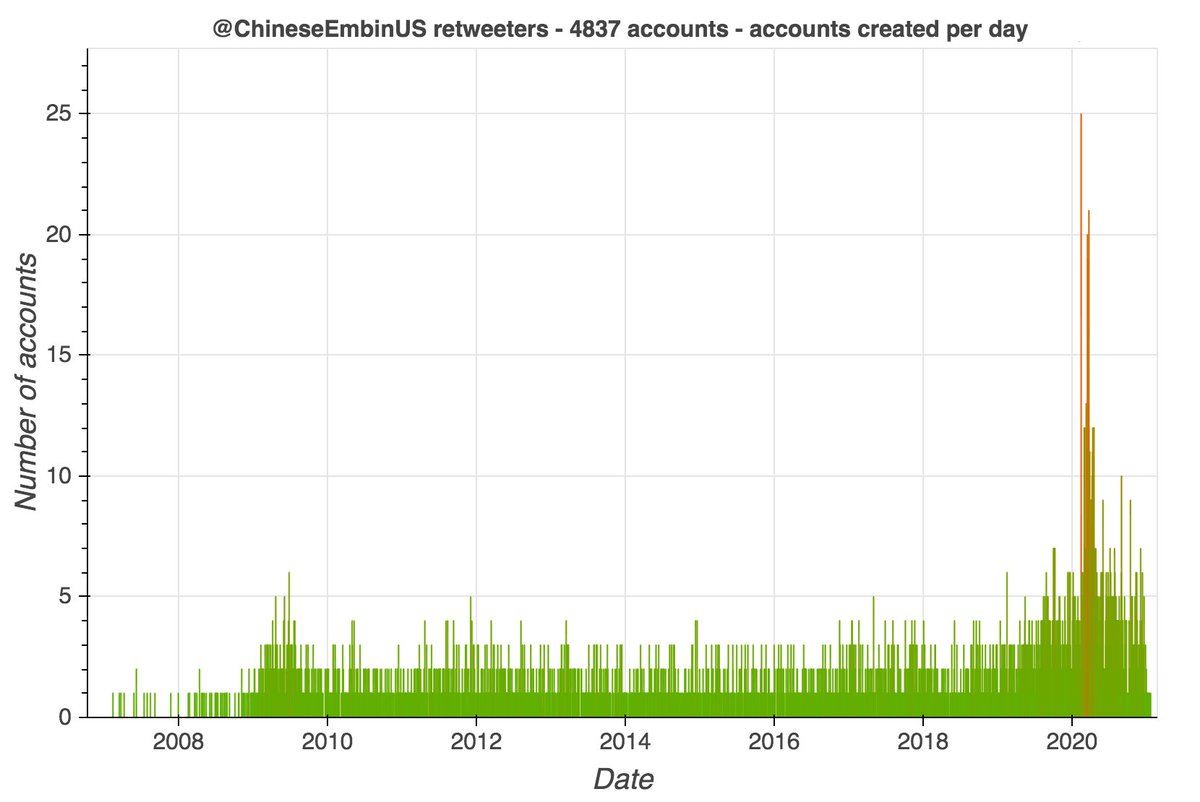
We downloaded recent retweets of @ChineseEmbinUS's tweets, and noticed several spikes in account creation (mostly in early 2020). The accounts created during these spikes have distinctive patterns in their names, similar numbers of tweets/likes, and so on. 


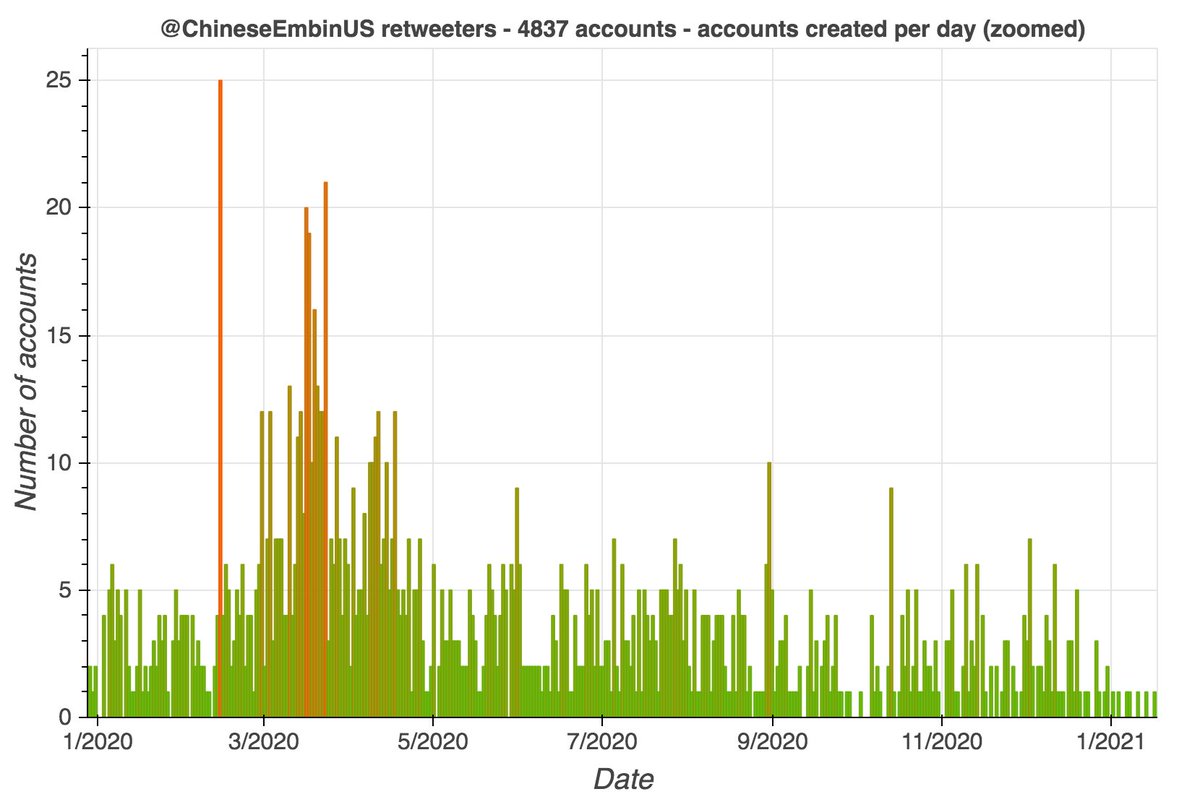
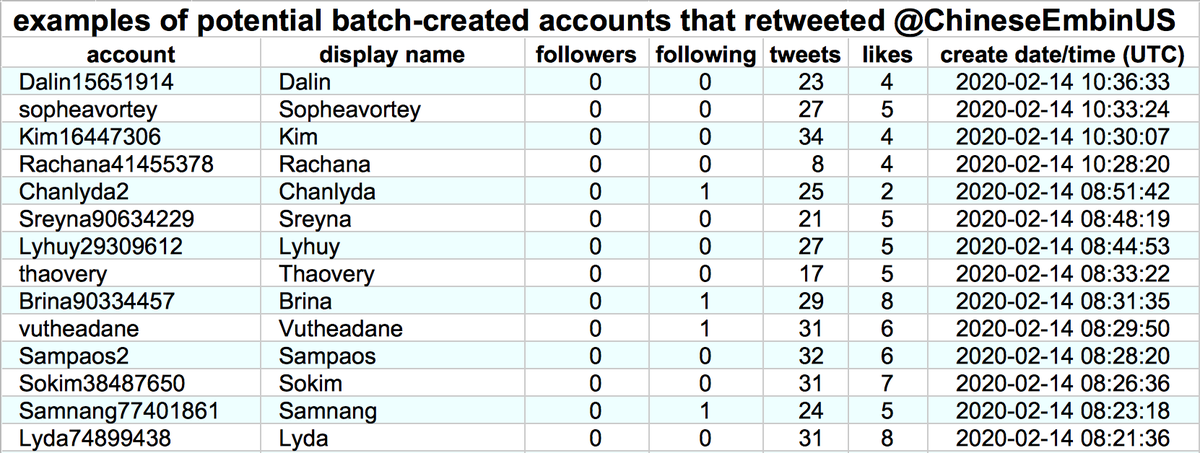
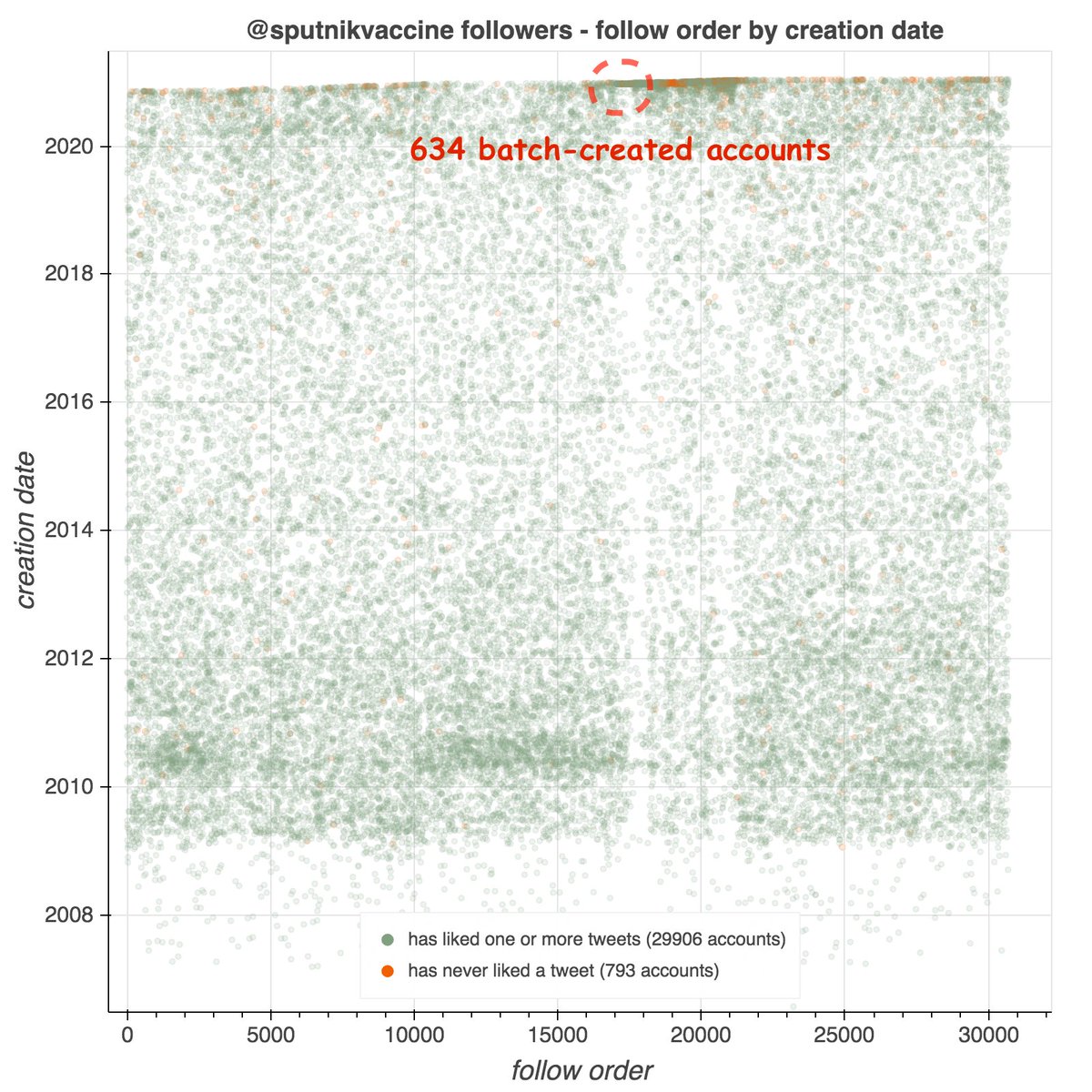
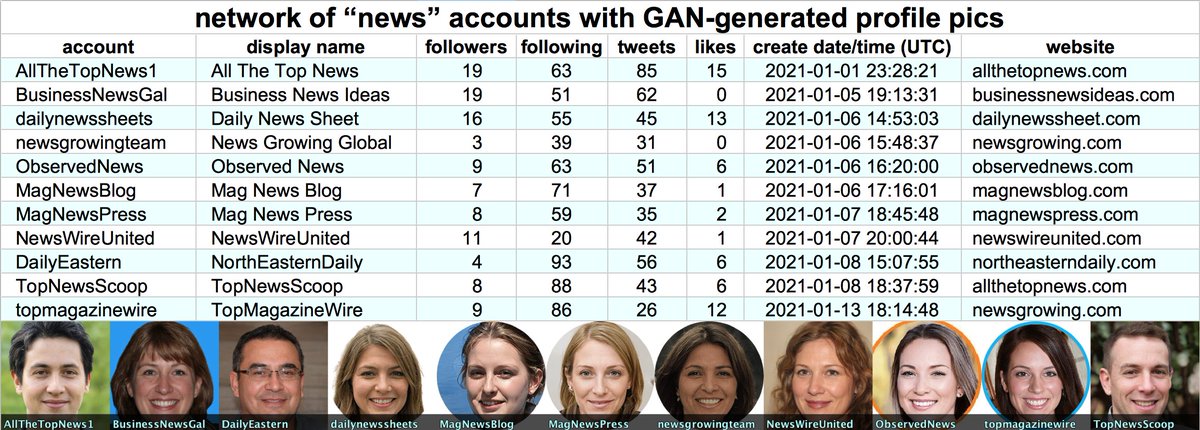
By exploring the retweeters of the other tweets retweeted by these accounts, we found a total of 674 batch-created accounts, created between December 2019 and January 2021. The naming schemes sometimes vary from batch to batch (table show representatives examples). 



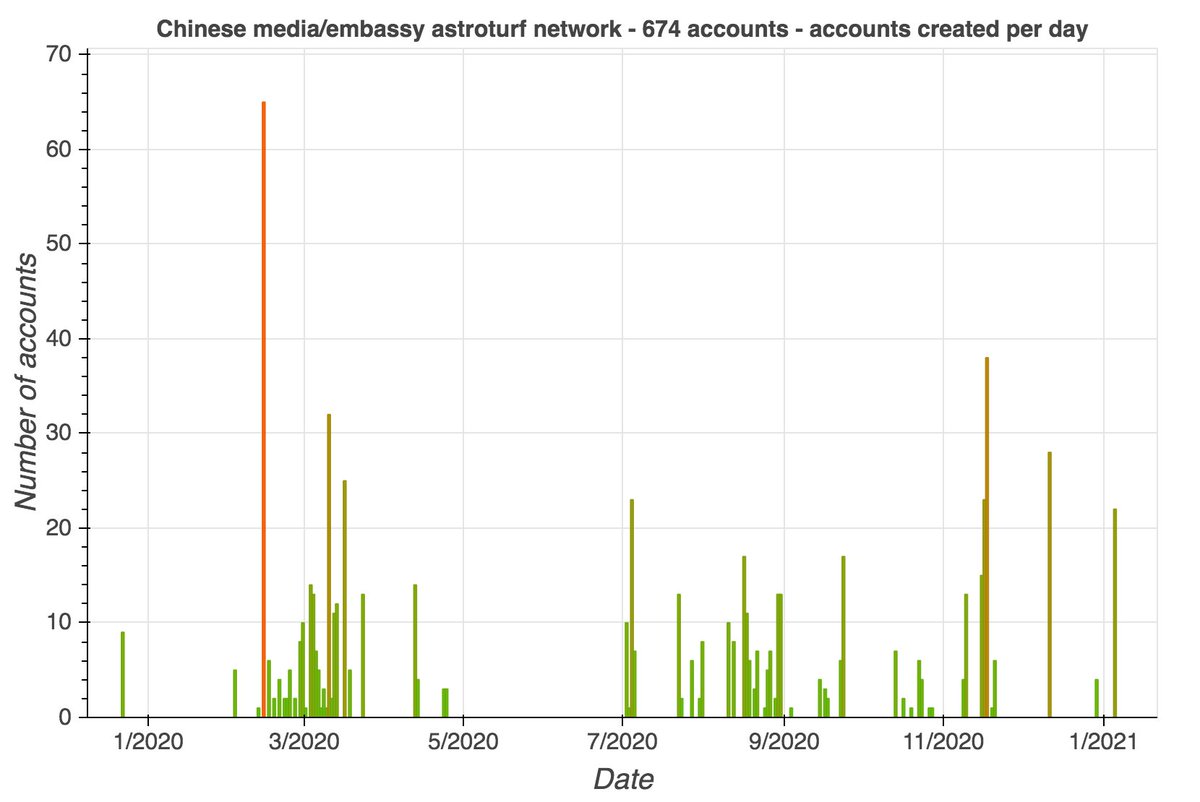
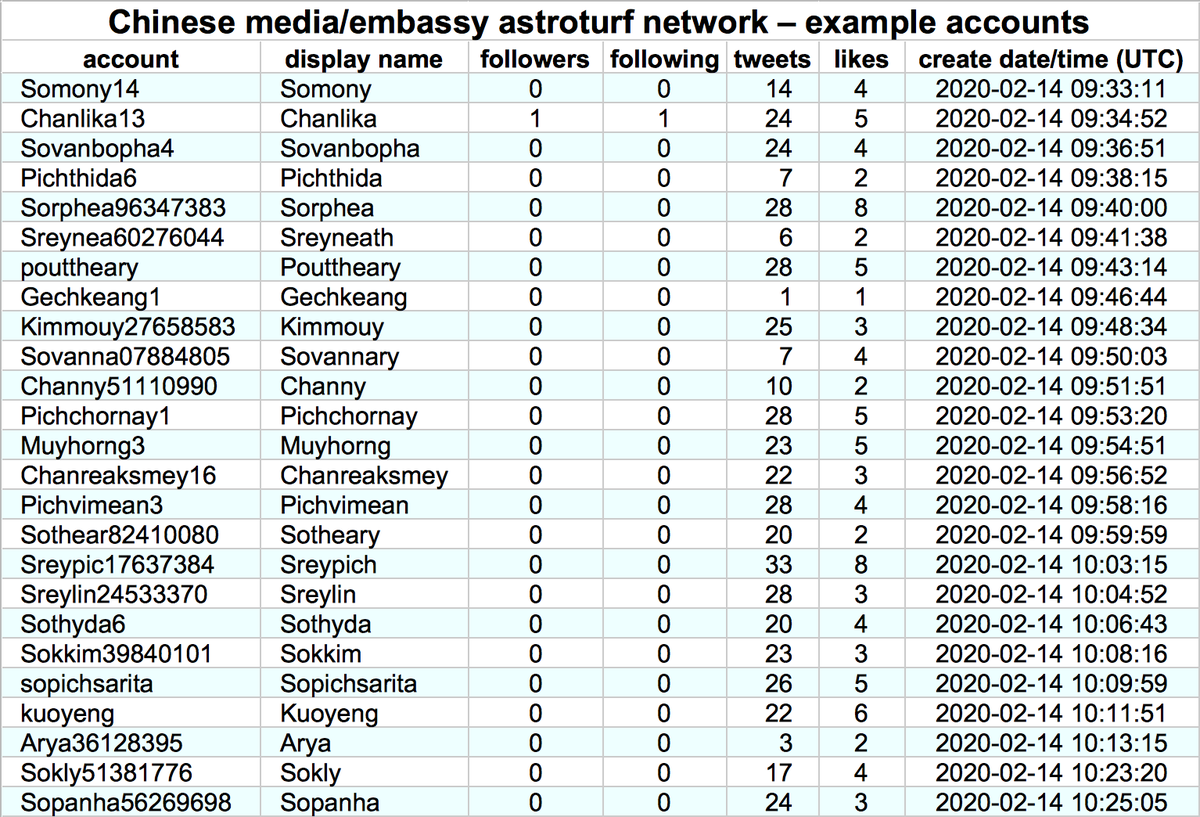
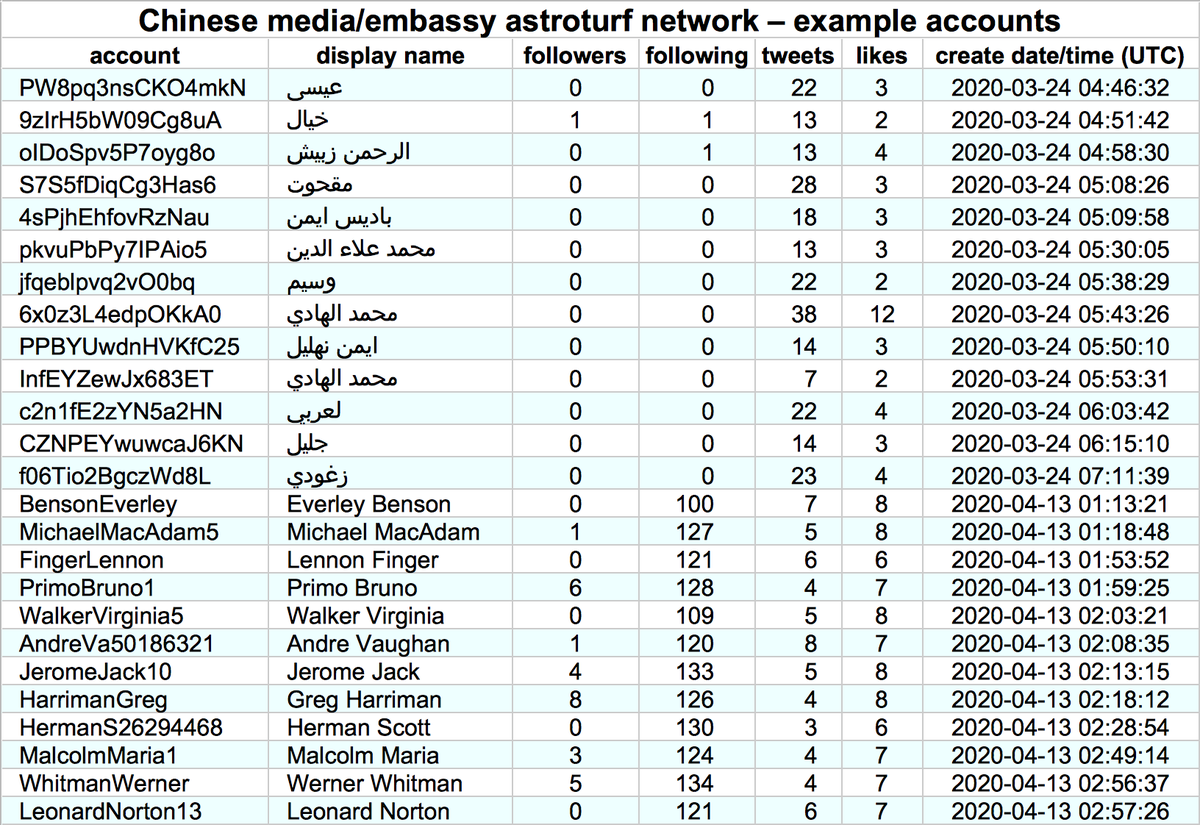
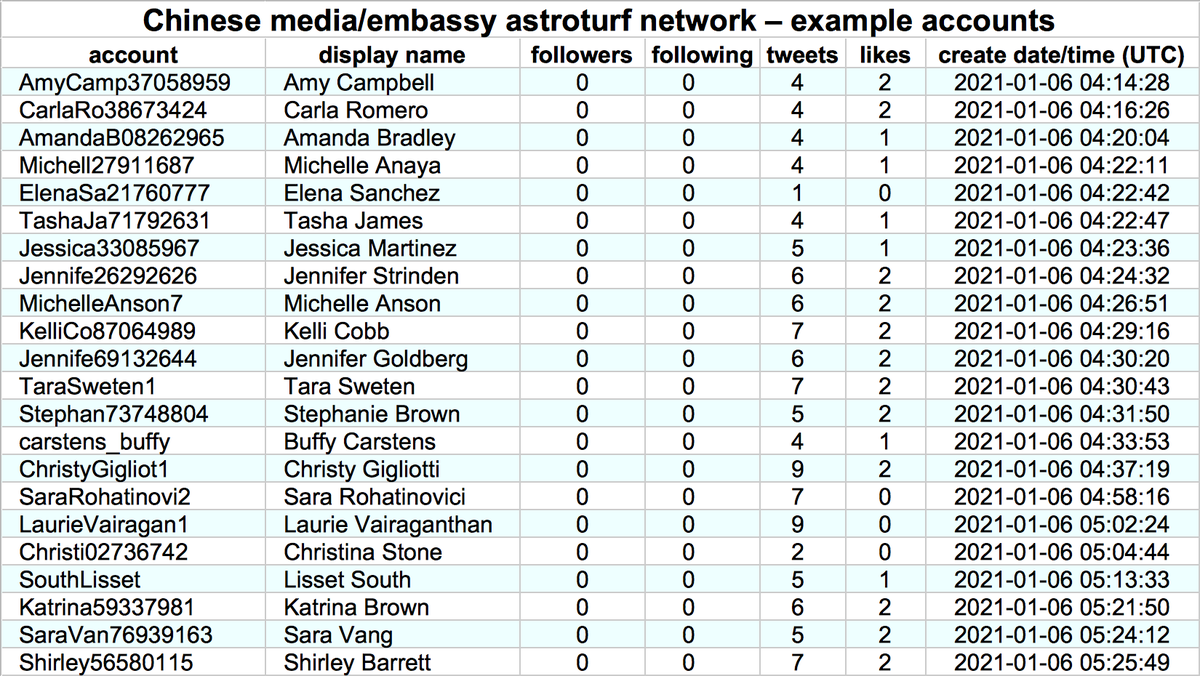
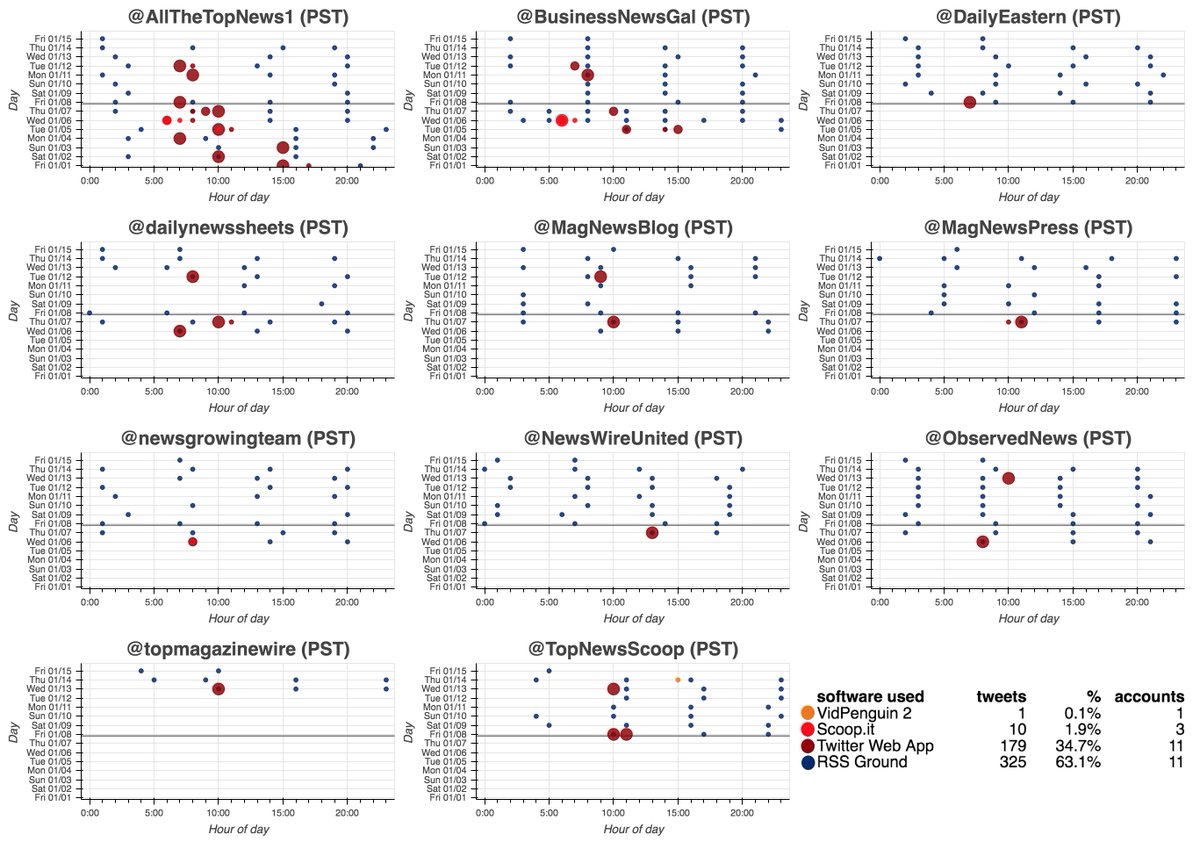
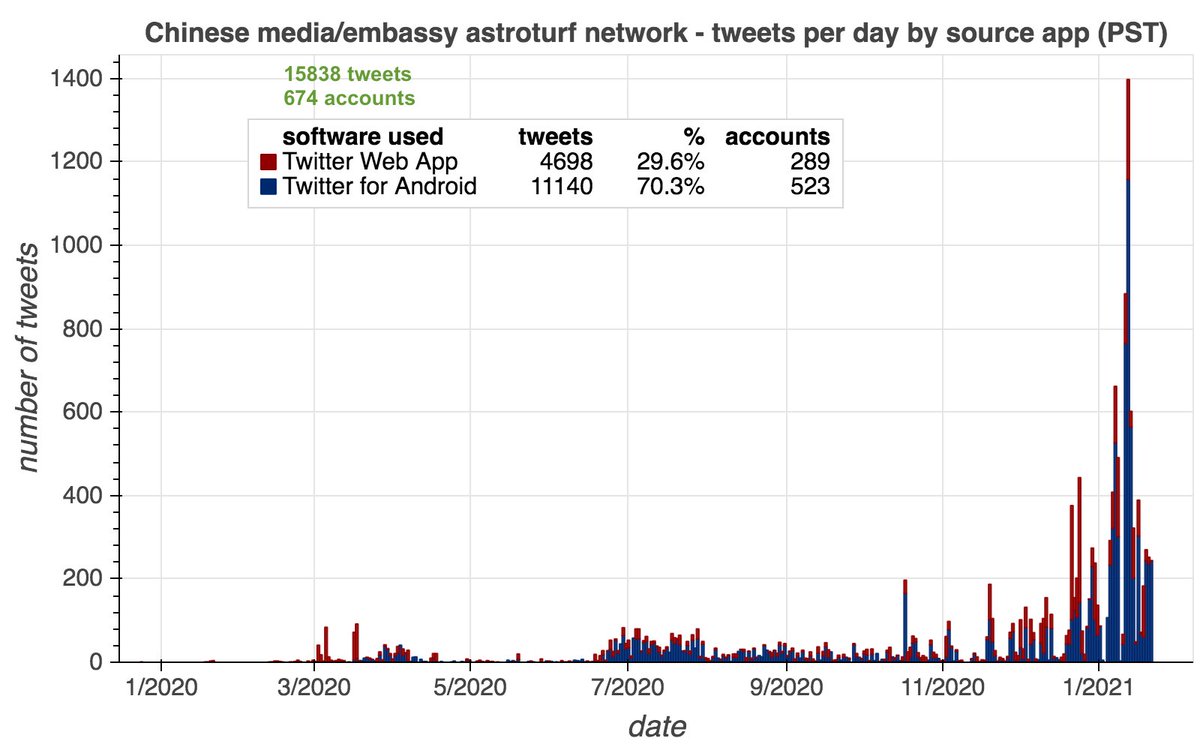
These 674 accounts allegedly tweet via the Twitter Android App and Twitter Web App (no iPhone/iPad tweets). We're uncertain whether these accounts are automated or the result of repetitive human activity, hence the use of the term "astroturf network" rather than "botnet". 
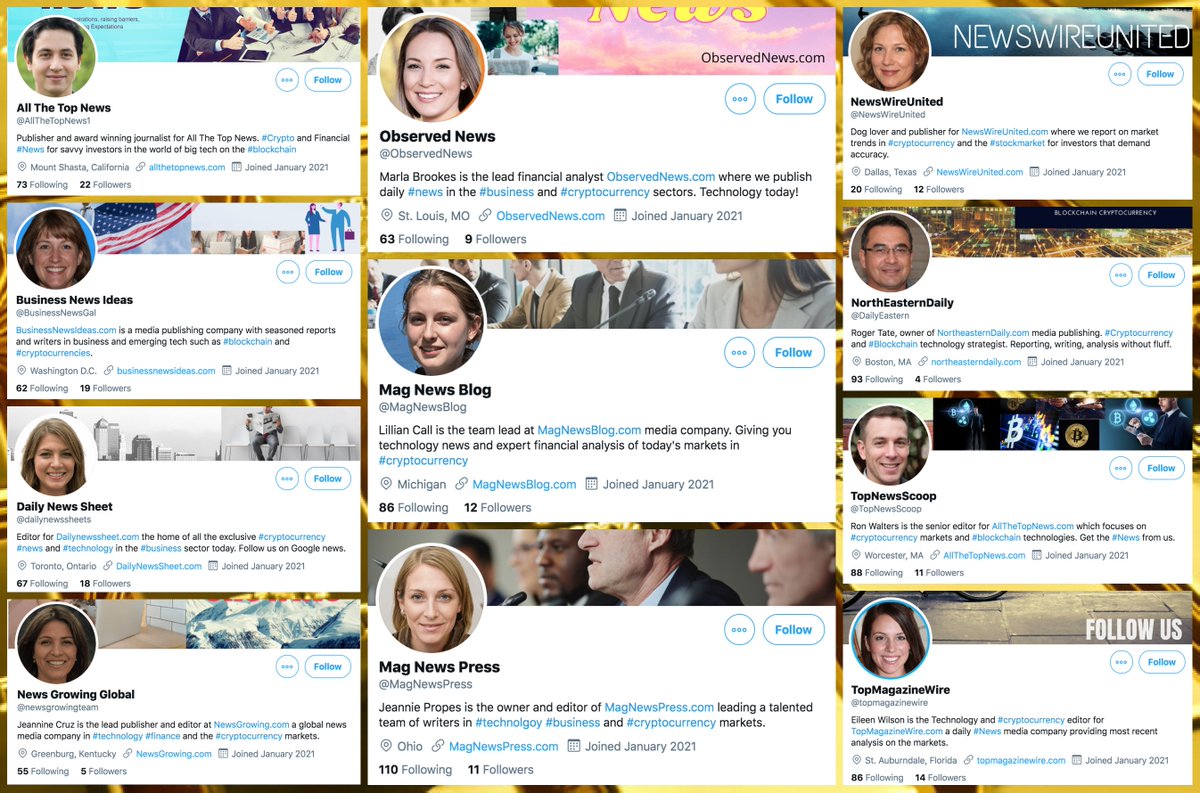
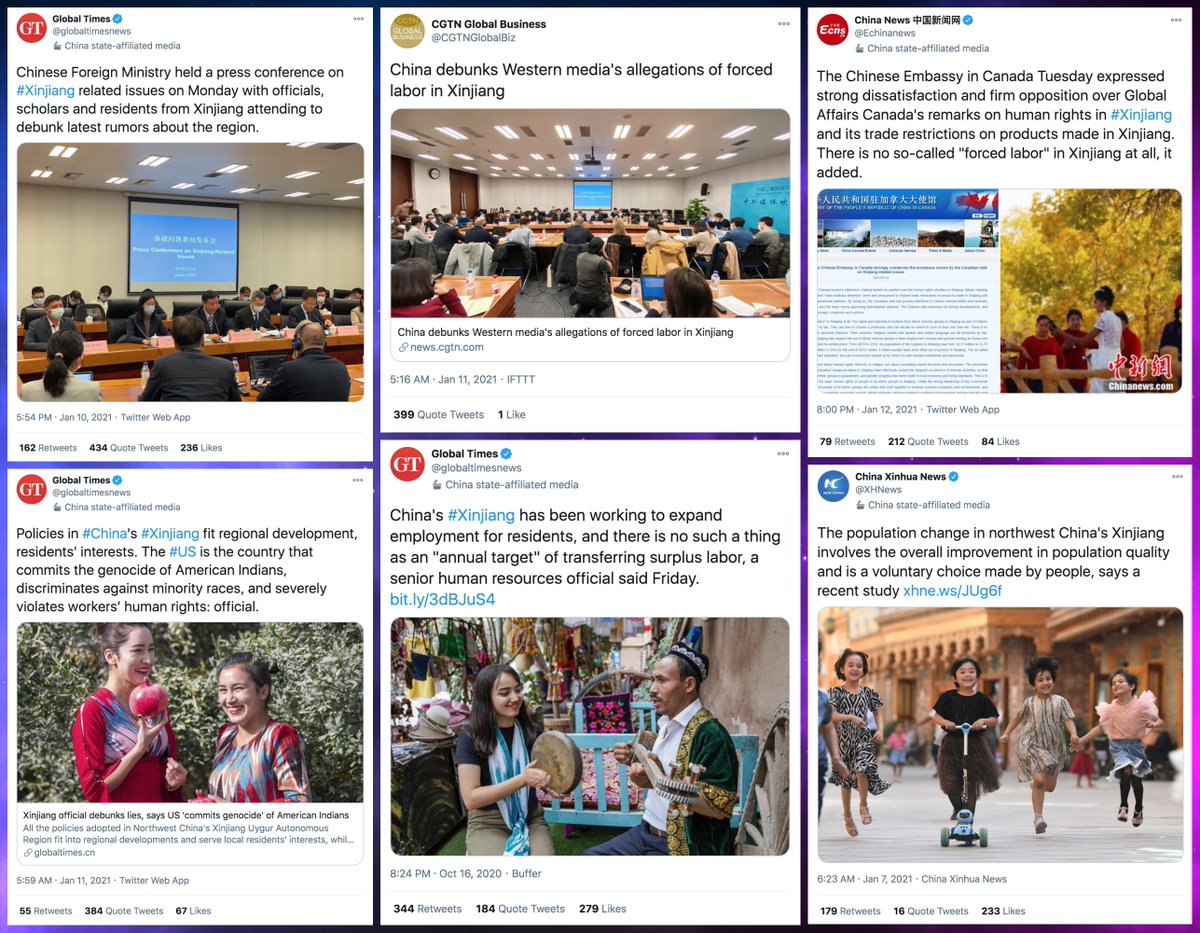
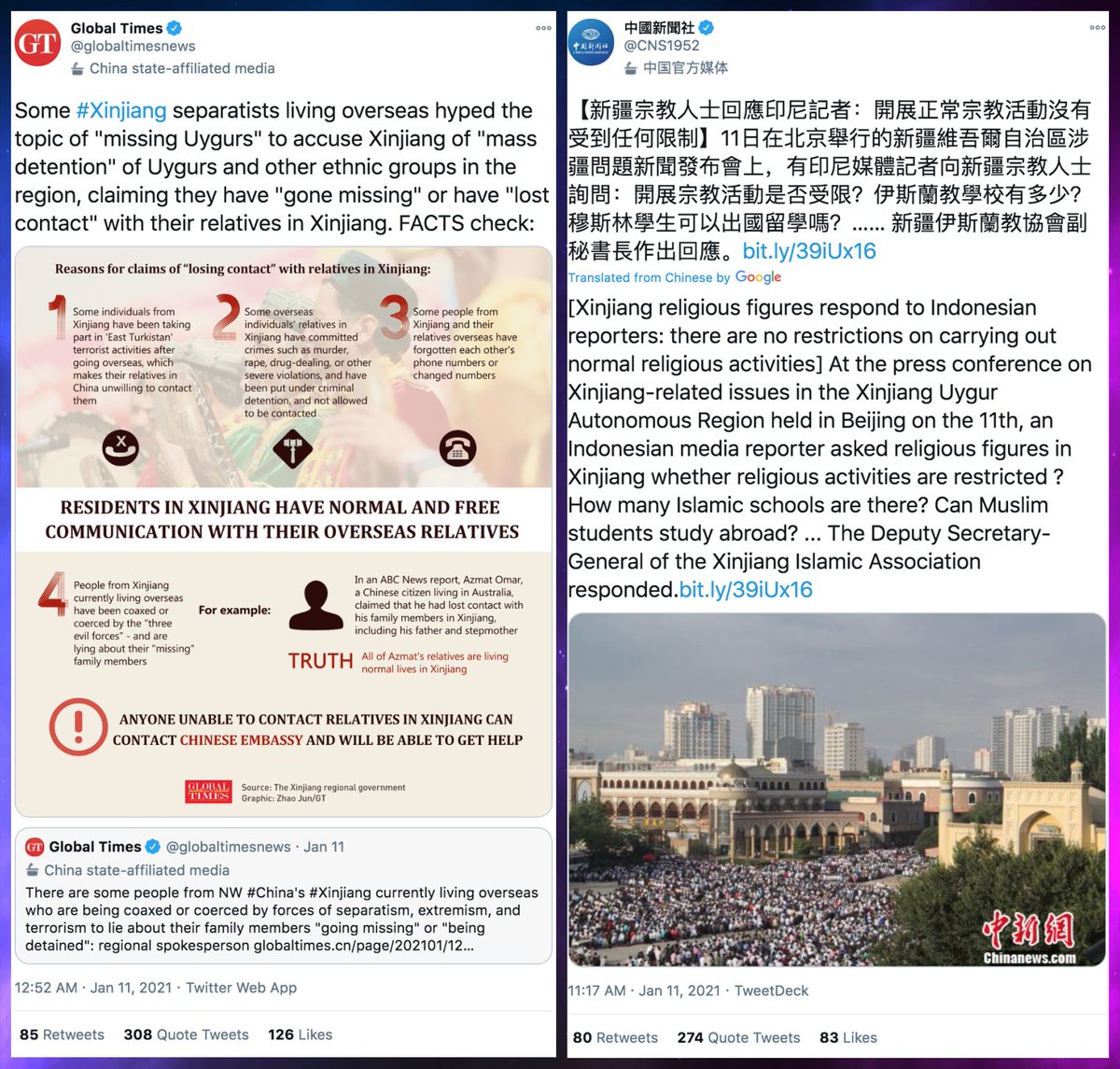
This network posts both original tweets and retweets/quote tweets. Original tweets are repetitive and are mostly links to Chinese media sites and YouTube videos. Propaganda about Xinjiang and denial of the existence of forced labor camps are the primary themes. 


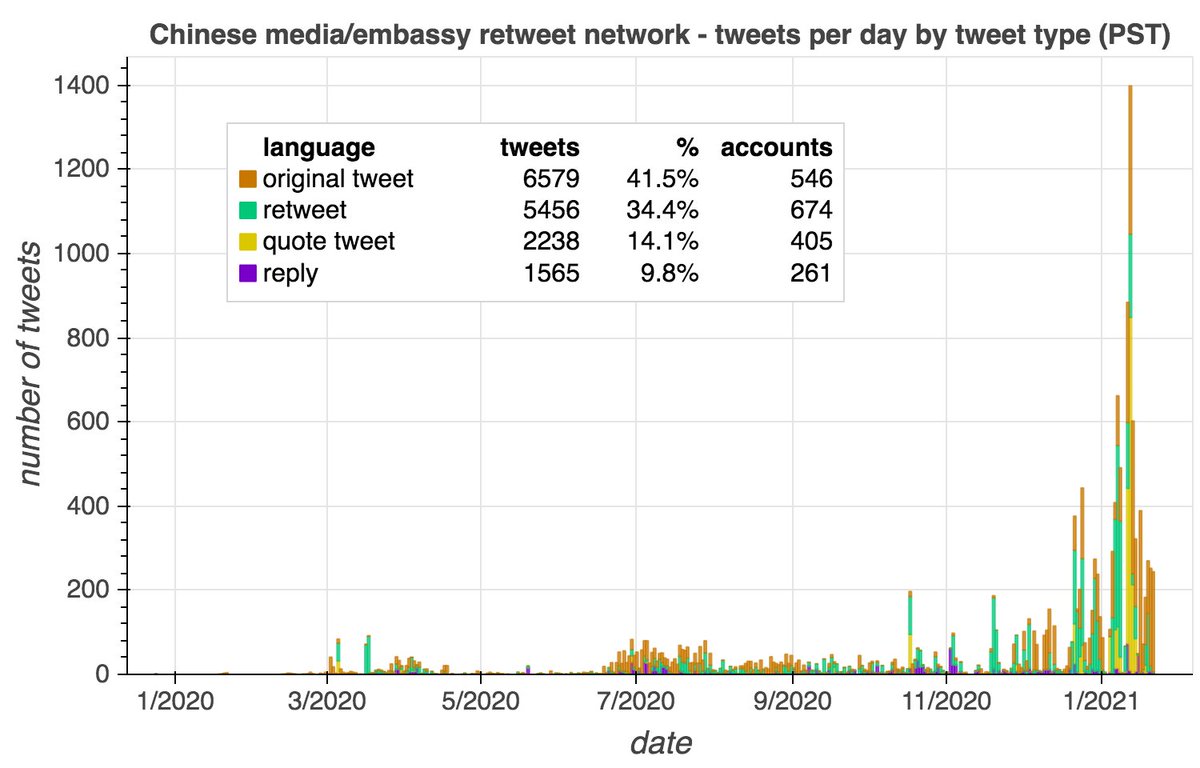
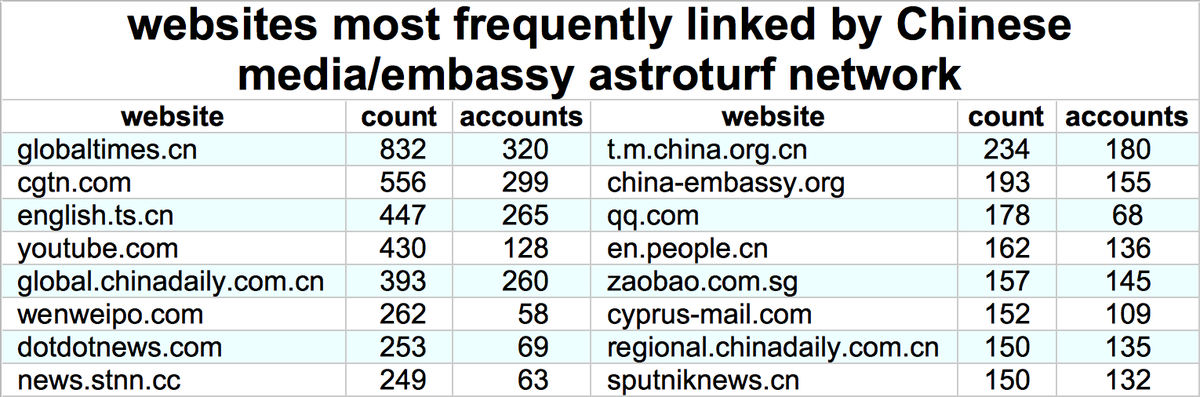
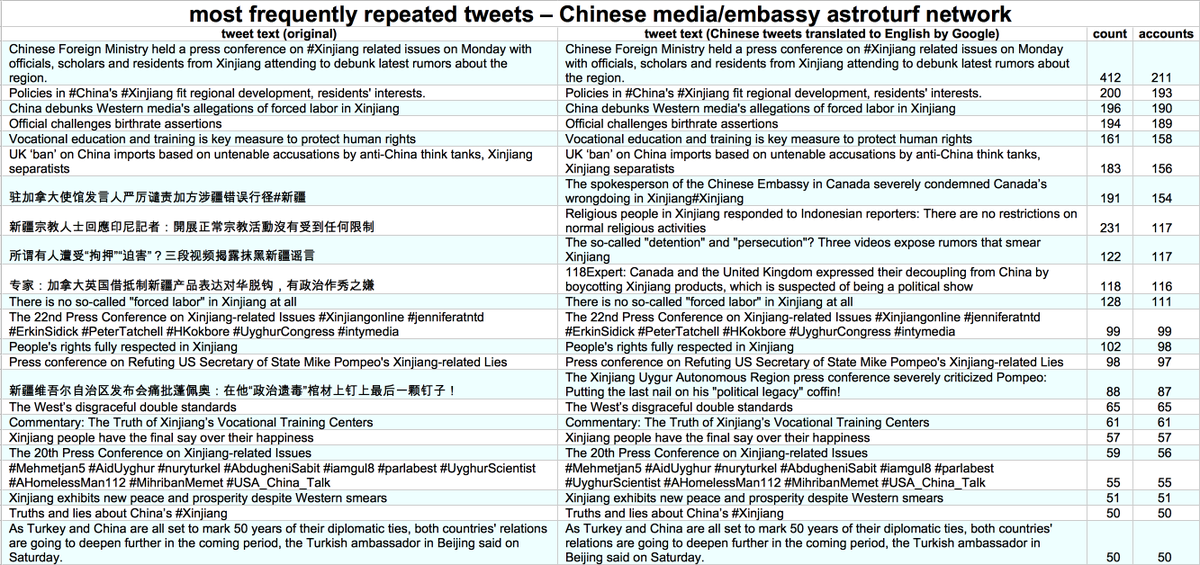
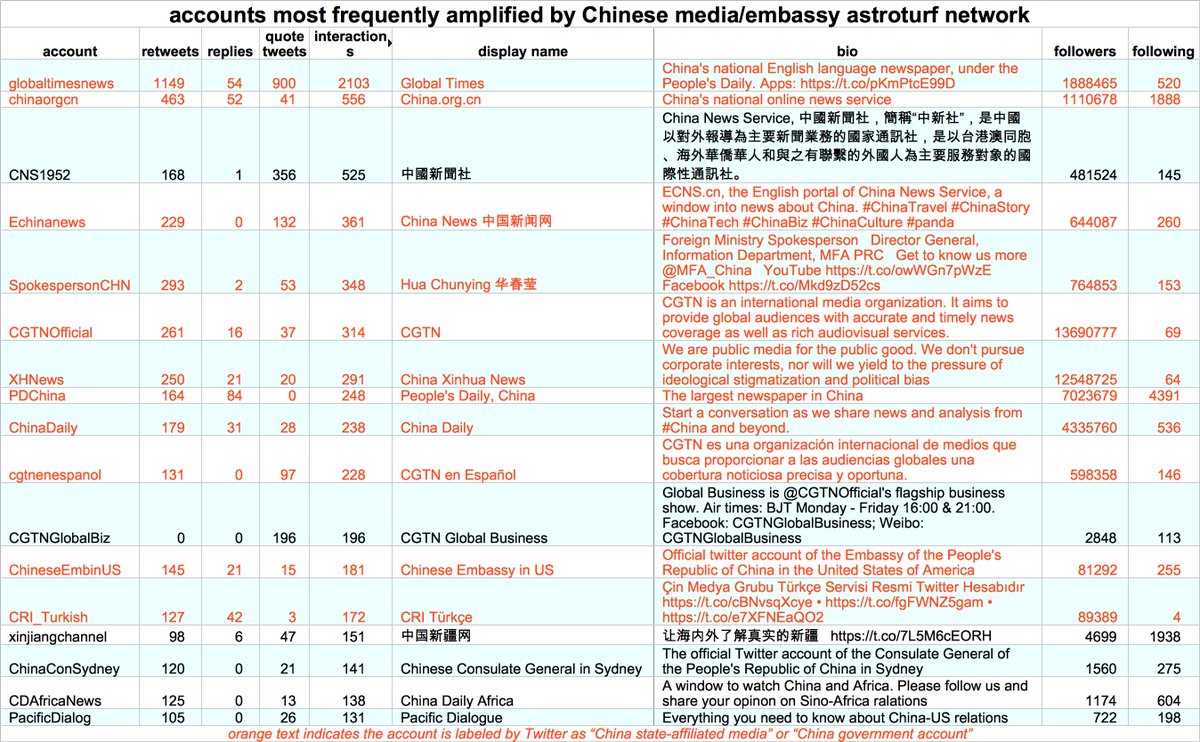
Who does this network amplify via retweets and quote tweets? Mostly Chinese diplomatic and state media accounts, and as with the network's original tweets, propaganda about Xinjiang is the main theme. 


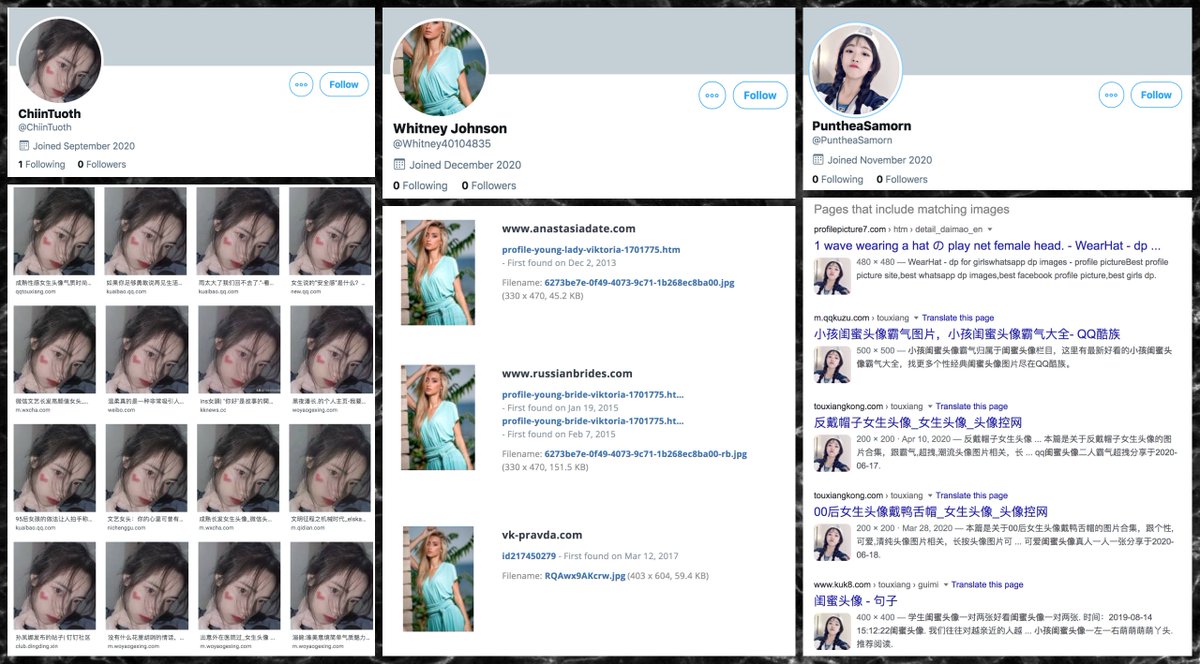
418 of the 674 accounts in this network (62%) use default profile pics; the rest mostly use stolen pics. We found both TinEye and Google reverse image search reasonably effective at finding pics stolen from other websites. 
• • •
Missing some Tweet in this thread? You can try to
force a refresh