
Last talk of #enigma2021 by Marcus Botacin: "DOES YOUR THREAT MODEL CONSIDER COUNTRY AND CULTURE? A CASE STUDY OF BRAZILIAN INTERNET BANKING SECURITY TO SHOW THAT IT SHOULD!"
usenix.org/conference/eni…
usenix.org/conference/eni…
The outcomes I get from my analysis of malware I find in Brazil were quite different than what I saw in analysis of malware from other researchers. Why? Because the malware attacks were different!
The Brazilian banking system:
* let's move banking to computers (80s)to keep up with hyperinflation
* desktop clients for users... and the attackers migrated from physical to fake desktop app attacks -- that would only work in Brazil because that's where the banking was

* let's move banking to computers (80s)to keep up with hyperinflation
* desktop clients for users... and the attackers migrated from physical to fake desktop app attacks -- that would only work in Brazil because that's where the banking was

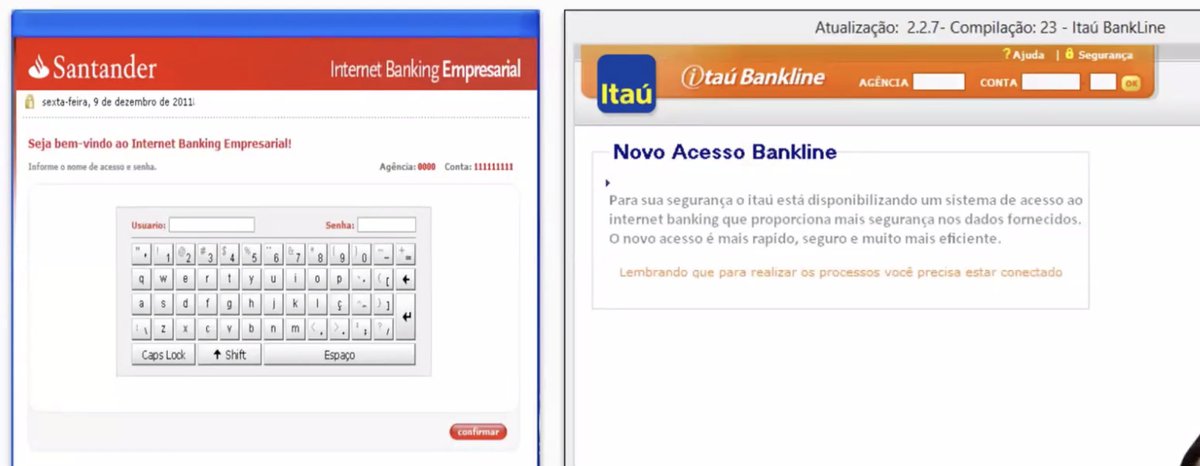
* these attacks weren't found by global malware detection at the time
* was "just" phishing, not anything that was detected an attack
Then decades later we still have the same attacks, but in SMS
* was "just" phishing, not anything that was detected an attack
Then decades later we still have the same attacks, but in SMS

Boletos case: payment instrument only in Brazil
* the banks were computerized but the people were not
* needed some way to mediate between the two
* the banks were computerized but the people were not
* needed some way to mediate between the two

The fake boletos made it so you paid the attacker, not the people you intended.
Does your threat model include offline people? It should!
Does your threat model include offline people? It should!
Why are attackers shifting between file formats so quickly?
The banks are reacting to all this malware by requiring everyone to install secure login plugin which searches your computer from malware. [whoa.]
The banks are reacting to all this malware by requiring everyone to install secure login plugin which searches your computer from malware. [whoa.]

... these secure login plugins were written in Java, so the attackers knew they could use Java, so they shifted attacks into Java
You can see particular attackers moving between technologies as the banks shift [diagram]
You can see particular attackers moving between technologies as the banks shift [diagram]

So need to shift the incentives for the password-stealing attacks that these folks are engaging in
Let's shift banking to mobile! All the security promises will become true, right? No.
Lots of restrictions e.g. economic constraints, most folks only got access to computers recently with mobile devices
Lots of restrictions e.g. economic constraints, most folks only got access to computers recently with mobile devices
The case of WhatsApp
* Data is *very* expensive in Brazil, so WhatsApp is very popular (people get plans with unlimited WhatsApp)
* Banks have chatbots in WhatsApp
* Attackers: ok, let's attack WhatsApp directly!
* Data is *very* expensive in Brazil, so WhatsApp is very popular (people get plans with unlimited WhatsApp)
* Banks have chatbots in WhatsApp
* Attackers: ok, let's attack WhatsApp directly!

* By outsourcing your app, you're outsourcing your security
* Attacker uses accessibility services to install a fake keyboard and bank can't disable it
Does your threat model consider WhatsApp and bank operations over WhatsApp? Users with limited data plans? It should!
* Attacker uses accessibility services to install a fake keyboard and bank can't disable it
Does your threat model consider WhatsApp and bank operations over WhatsApp? Users with limited data plans? It should!
Implications:
* Brazilian malware samples behave very differently than US and Japanese samples
* Stop writing malware reports that don't clearly state which countries are covered
* Brazilian malware samples behave very differently than US and Japanese samples
* Stop writing malware reports that don't clearly state which countries are covered

* Detection rates are only true if you look at a "balanced" dataset. But people live in the real world and their malware is specific to where they live
* So malware detection rates can be terrible for some people and not reflected in those rates
* It's really bad for Brazil

* So malware detection rates can be terrible for some people and not reflected in those rates
* It's really bad for Brazil


What happens when you train an ML model on a sample which includes Brazilian malware? It breaks
* Need to update frequently and specifically
* Need to update frequently and specifically

Recommendations:
* Develop threat models which consider regional and socio-cultural issues
* Incentivize localized and focused research work with specific datasets
* Promote local security teams
* Share local information with the world
[end of talk]
* Develop threat models which consider regional and socio-cultural issues
* Incentivize localized and focused research work with specific datasets
* Promote local security teams
* Share local information with the world
[end of talk]

• • •
Missing some Tweet in this thread? You can try to
force a refresh












