(1/of a few) Doing some training #threathunting runs with #suricata -with pcap from bit.ly/3jNUCyw
Fun fact: Alerts count only for 8% of the total logs produced - we also have protocol logs like Flow records, KRB5, SMB, DNS, TLS, HTTP, DCERPC,Fileinfo
Fun fact: Alerts count only for 8% of the total logs produced - we also have protocol logs like Flow records, KRB5, SMB, DNS, TLS, HTTP, DCERPC,Fileinfo

(2/of a few)
Just as regular protocol and flow logging of #Suricata gives us:
633 FLOW logs
295 HTTP logs
182 TLS logs
130 DNS logs
114 SMB logs
90 DCERPC logs
66 FILEINFO logs
23 KRB5 logs
2 NTP logs
Let's see some examples of the generated data...
Just as regular protocol and flow logging of #Suricata gives us:
633 FLOW logs
295 HTTP logs
182 TLS logs
130 DNS logs
114 SMB logs
90 DCERPC logs
66 FILEINFO logs
23 KRB5 logs
2 NTP logs
Let's see some examples of the generated data...
(3/of a few)
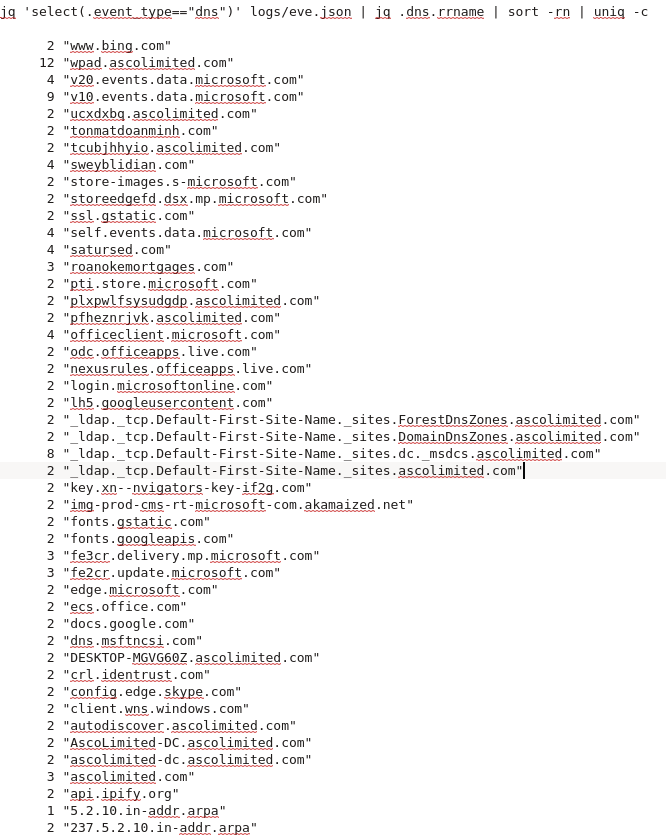
Quick and dirty cmd look at the DNS logs generated by #Suricata gives us the domain list for our #threathunting review
Couple of those jump out (at lest to me)
Quick and dirty cmd look at the DNS logs generated by #Suricata gives us the domain list for our #threathunting review
Couple of those jump out (at lest to me)
(4/of a few)
Quick and dirty cmd look at the #HTTP protocols logs of .@Suricata_IDS we have some interesting results for
1 - HTTP hostnames
2 - HTTP User agents
3 - HTTP servers
Quick and dirty cmd look at the #HTTP protocols logs of .@Suricata_IDS we have some interesting results for
1 - HTTP hostnames
2 - HTTP User agents
3 - HTTP servers

@Suricata_IDS (5/of a few) #suricata also gives us a pretty good snapshot form the TLS protocol logs for SNIs , Issuers, subjects that can lead the investigation of the pcap traffic trace too (quick jq on the cmd) 

@Suricata_IDS (6/of a few)
You can further add and build relation between the previous #suricata TLS protocol data generated and network traffic #encryption analysis based on flow and ja3 and ja3s as well to show clients/apps and servers comms in the #ThreatHunting process

You can further add and build relation between the previous #suricata TLS protocol data generated and network traffic #encryption analysis based on flow and ja3 and ja3s as well to show clients/apps and servers comms in the #ThreatHunting process


@Suricata_IDS (7/of a few) .@Suricata_IDS can identify (type/magic/hash etc) and also extract files from the following protocols - HTTP , SMTP , FTP, NFS, SMB, HTTP2
so for this #pcap that would give us another angle into the #ThreatHunting :
so for this #pcap that would give us another angle into the #ThreatHunting :

@Suricata_IDS (8/of a few)So then you can further break down the file transactions analysed by .@Suricata_IDS by protocol - HTTP and SMB "6lhjgfdghj.exe" sticks out 

@Suricata_IDS (9/of a few) Looking at the fileinfo #suricata log record of that #HTTP file transaction we have other valuable information like http hostname , size, file magic and sha256 among others.Both the hostname and the checksums are listed on virusTotal
virustotal.com/gui/file/94e60…
virustotal.com/gui/file/94e60…

@Suricata_IDS (10/of a few) We can count on @Suricata_IDS SMB and KRB5 protocol logging in this basic #ThreatHunting run to tell us who logged form where, AD domains and PC names 

@Suricata_IDS .@Suricata_IDS #protocol logging for KRB5 (example attached) could be quite revealing for lateral movement user involvement identification in the #ThreatHunting
docs.microsoft.com/en-us/openspec…
docs.microsoft.com/en-us/openspec…

@Suricata_IDS (12/of a few)
So would be #Suricata SMB protocol logging for that #ThreatHunting chase with that pcap (msg 1/of a few)
So would be #Suricata SMB protocol logging for that #ThreatHunting chase with that pcap (msg 1/of a few)

@Suricata_IDS (13/of a few)
#Suricata SMB protocol log for session setup of user "bill.cook" and host "DESKTOP-MGVG60Z" #threathunting
#Suricata SMB protocol log for session setup of user "bill.cook" and host "DESKTOP-MGVG60Z" #threathunting

@Suricata_IDS (14/of a few)
#Suricata DCERPC protocol logging can also help in highlighting movement in the #threathunting
#Suricata DCERPC protocol logging can also help in highlighting movement in the #threathunting

@Suricata_IDS (16/of a few) With #suricata you can also see all protocol logs for a specific flow - matching on "flow_id". In the case attached we have
1 - KRB5 event
2 - Anomaly applayer
3 - Flow record
That all share the same flow_id, in this case - "1400760090402734" #threathunting

1 - KRB5 event
2 - Anomaly applayer
3 - Flow record
That all share the same flow_id, in this case - "1400760090402734" #threathunting


@Suricata_IDS (17/of a few)
How to enable application layer anomalies in #suricata config that helps the #threathunting:
github.com/OISF/suricata/…
Docs:
suricata.readthedocs.io/en/suricata-6.…
suricata.readthedocs.io/en/latest/outp…
How to enable application layer anomalies in #suricata config that helps the #threathunting:
github.com/OISF/suricata/…
Docs:
suricata.readthedocs.io/en/suricata-6.…
suricata.readthedocs.io/en/latest/outp…
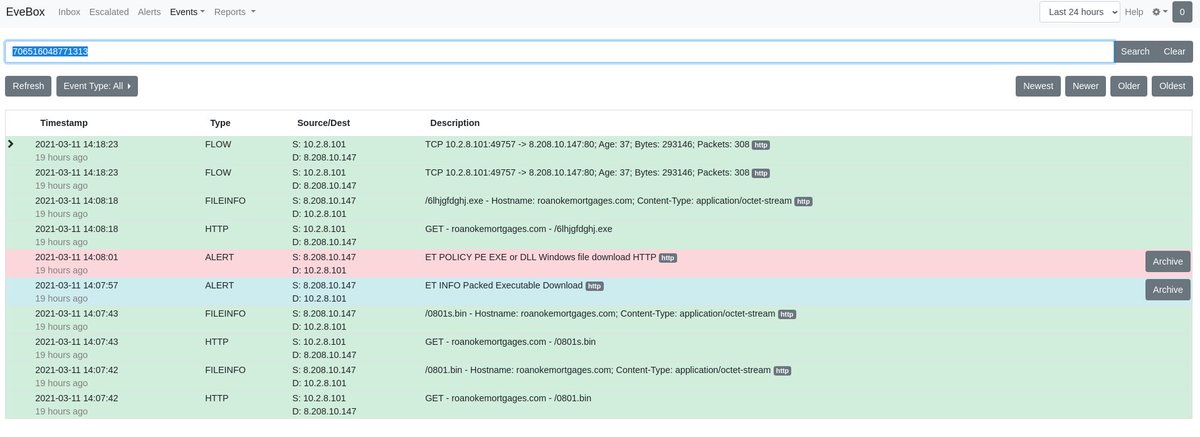
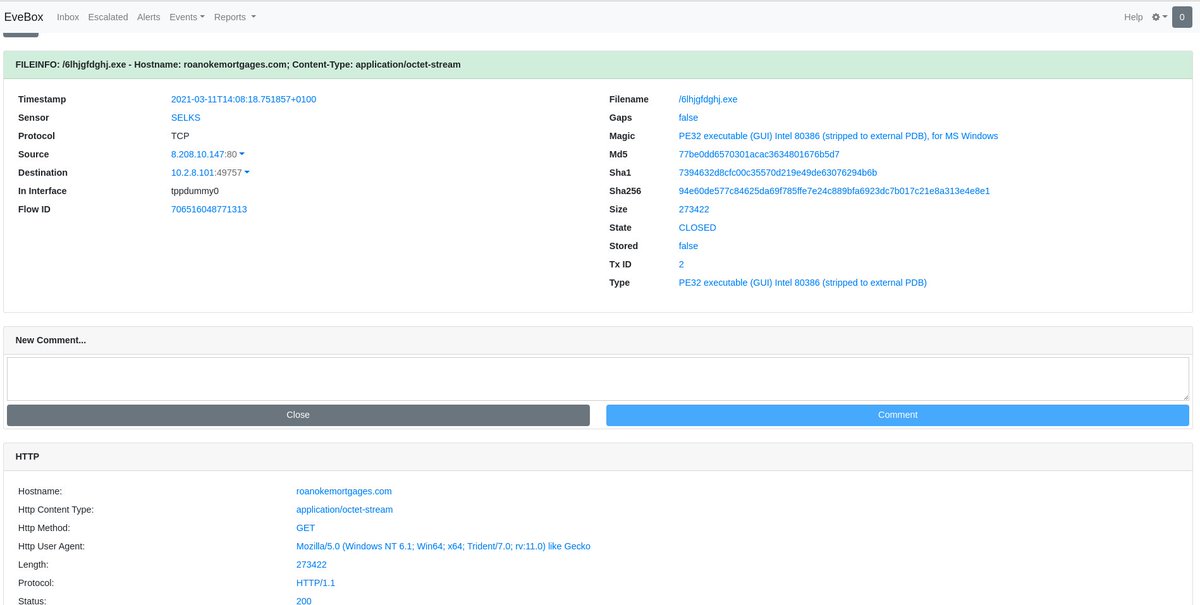
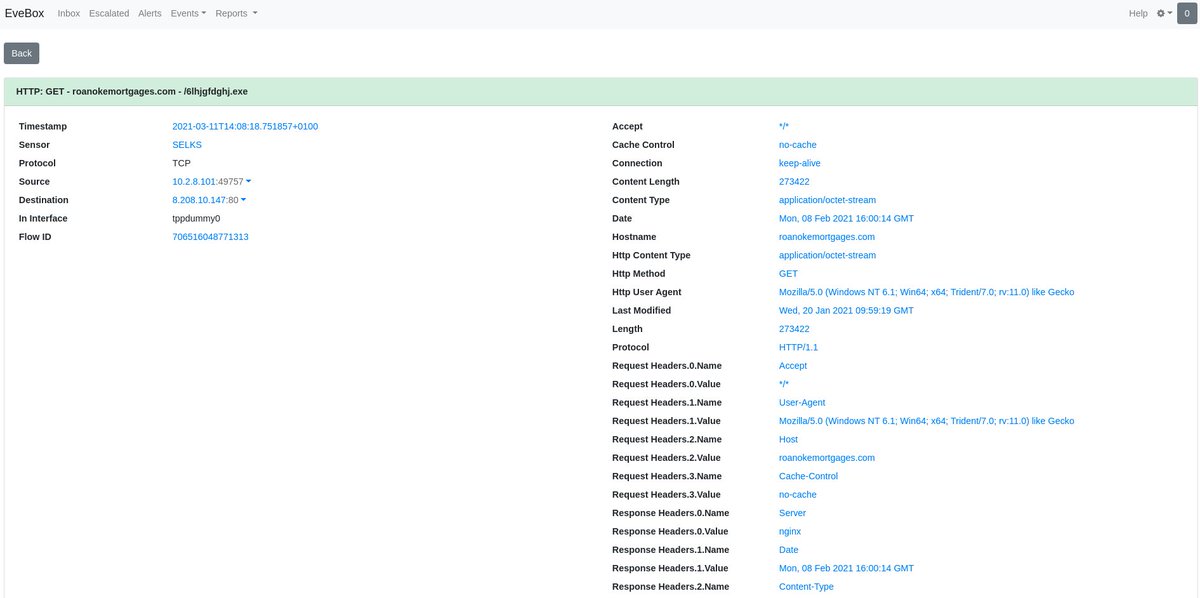
@Suricata_IDS (21/of a few)
In #evebox we can also zoom on the same host or flow_id to get files transferred, flow records and #HTTP transactions.
tinyurl.com/22msb6ts
#suricata #threathunting #evebox


In #evebox we can also zoom on the same host or flow_id to get files transferred, flow records and #HTTP transactions.
tinyurl.com/22msb6ts
#suricata #threathunting #evebox
• • •
Missing some Tweet in this thread? You can try to
force a refresh




