Microsoft is warning users to apply patch it's releasing today for four zero day vulns found in Exchange email servers - the vulns are being actively exploited by threat group believed to be from China. Details in this thread (and here after 2pm): microsoft.com/security/blog/…
"We strongly urge customers to update on-premises systems immediately. Exchange Online is not affected."
The vulns are CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065; all of which are addressed in today’s updates for Exchange Server.
The vulns are CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065; all of which are addressed in today’s updates for Exchange Server.
The vulns affect Microsoft Exchange Server. Exchange Online is NOT affected.
Versions affected are:
Microsoft Exchange Server 2013 , 2016 and 2019
Microsoft Exchange Server 2010 is being updated for Defense in Depth purposes.
Versions affected are:
Microsoft Exchange Server 2013 , 2016 and 2019
Microsoft Exchange Server 2010 is being updated for Defense in Depth purposes.
Microsoft says it's making the links available now instead of waiting until 2pm. I'll tweet them as soon as their live.
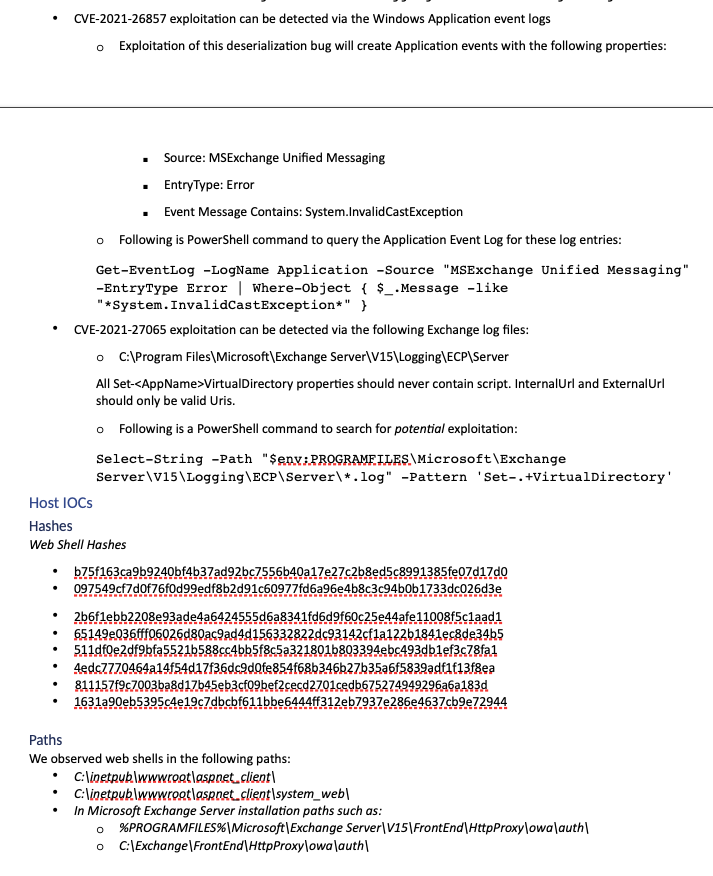
This image has IoC info to catch exploitation activity that may currently be happening. Microsoft said it had already briefed government customers. 

Ok, Microsoft has made all of the links live now so I'll stop posting IoCs. You can find everything here:
microsoft.com/security/blog/…
msrc-blog.microsoft.com/2021/03/02/mul…
blogs.microsoft.com/on-the-issues/…
microsoft.com/security/blog/…
msrc-blog.microsoft.com/2021/03/02/mul…
blogs.microsoft.com/on-the-issues/…
Volexity has post about how it discovered the active exploitation of the 4 zero-day vulns Microsoft is patching today. "These attacks appear to have started as early as January 6, 2021." volexity.com/blog/2021/03/0…
"attacker was exploiting a zero-day server-side request forgery vuln in...Exchange...to steal the full contents of several user mailboxes. This vuln...does not require authentication of any kind...attacker only needs to know the server running Exchange and the [email] account"
• • •
Missing some Tweet in this thread? You can try to
force a refresh