
Given recent activity, here's a thread on webshells from a behavioral perspective. Based on my experience over the years I can say the following is true:
- The src ip of the attacker will be seen on few webservers
- The uri of the webshell is likely to be rare
#DFIR 1/?
- The src ip of the attacker will be seen on few webservers
- The uri of the webshell is likely to be rare
#DFIR 1/?

- There will likely be few uri's visited on the webserver from attacker's ip (< 4)
- With every command issued the response bytes will likely be different
- There will be a high percentage of unique byte counts (think response to different commands issued).
#DFIR 2/?
- With every command issued the response bytes will likely be different
- There will be a high percentage of unique byte counts (think response to different commands issued).
#DFIR 2/?
- Attackers generally interact with the webshell for a few hours in a 24 hour period
Here's a search that accomplishes this.
#DFIR 3/?
Here's a search that accomplishes this.
#DFIR 3/?
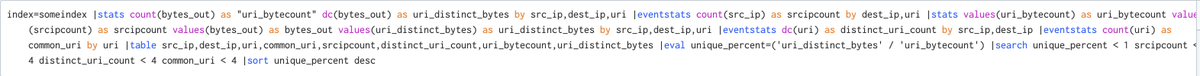
When I review the output of this search I generally look for entries where the unique percent is > 90% and the uri_bytecount is ~40. The 40 translatess to 40 commands issued in an hour.
The last line in the image would be something I would be interested in.
#DFIR 4/?
The last line in the image would be something I would be interested in.
#DFIR 4/?
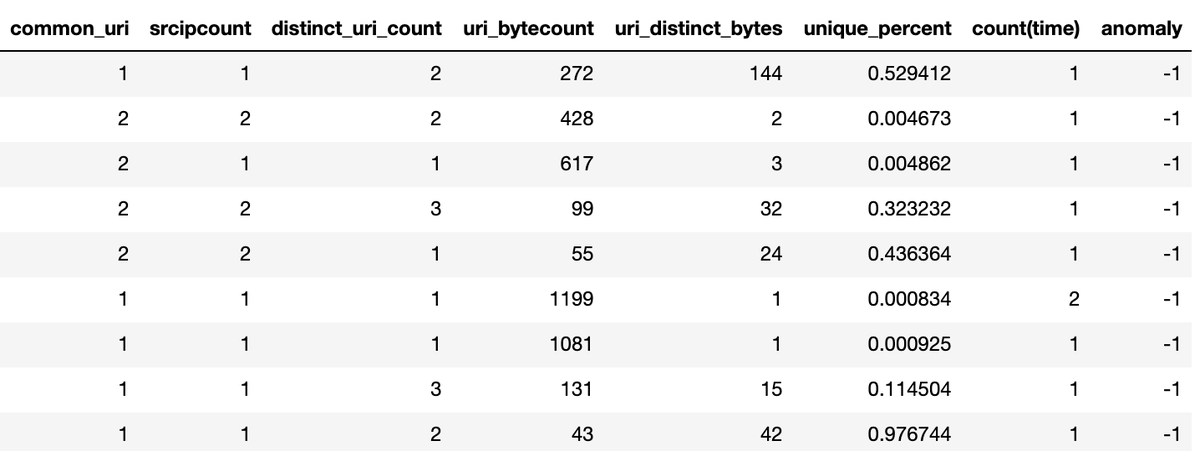
A description of fields:
Common_uri: Number of distinct webservers this uri has been seen on
Srcipcount: Number of src ip's that interacted with this uri
Distinct_uri_count: number of uri's visited by the src_ip
#DFIR 5/?
Common_uri: Number of distinct webservers this uri has been seen on
Srcipcount: Number of src ip's that interacted with this uri
Distinct_uri_count: number of uri's visited by the src_ip
#DFIR 5/?
Uri_bytecount: the count of destination bytes by src,dest,uri (translates to number of connections)
Uri_distinct_bytes: number of distinct bytes by src,dest,uri
Unique_percent: uri_distinct_bytes / uri_bytecount = percentage of unique outbound bytes
#DFIR 6/?
Uri_distinct_bytes: number of distinct bytes by src,dest,uri
Unique_percent: uri_distinct_bytes / uri_bytecount = percentage of unique outbound bytes
#DFIR 6/?
I believe this will help to describe the behavior of an attacker interacting with a webshell. I've also used this output in anomaly based detection with success.
#DFIR 7/7
#DFIR 7/7
• • •
Missing some Tweet in this thread? You can try to
force a refresh


