
NEW: The FBI warns in a new alert issued today that the FBI assesses malicious actors will be using deepfakes to advance their foreign influence & cyber-operations in the coming weeks, & that they already use them in influence ops. Details @CyberScoopNews cyberscoop.com/fbi-foreign-ac…
The FBI alert notes: “Foreign actors are currently using synthetic content in their influence campaigns & the FBI anticipates it will be increasingly used by foreign & criminal cyber actors for spearphishing & social engineering in an evolution of cyber operational tradecraft."
Some examples FBI points out: A pro-Chinese gov influence op @Graphika_NYC tracks as “Spamouflage Dragon,” has used profile images generated with AI to lend authenticity to the campaign, via @jeffstone500: cyberscoop.com/graphika-spamo…
In another case, the IRA/Russian government troll farm has used manipulated images for fake profile accounts, also via @jeffstone500: cyberscoop.com/russia-ira-qan…
Keep an eye out for more in this space, because the FBI warned in Wednesday’s alert that it would investigate deepfakes that have been attributed to foreign malicious actors.
The FBI's warning comes as concerns mount that if manipulated media is allowed to spread unabated, conspiracies/maligned influence will become more mainstream, w/ experts warning digital literacy & efforts to tamp down on misinfo need to be prioritized. cyberscoop.com/trump-riot-dis…
Lawmakers have recently enacted a series of laws that address deepfake technology, here's the latest update on that from @CyberScoopNews: cyberscoop.com/deepfake-porn-…
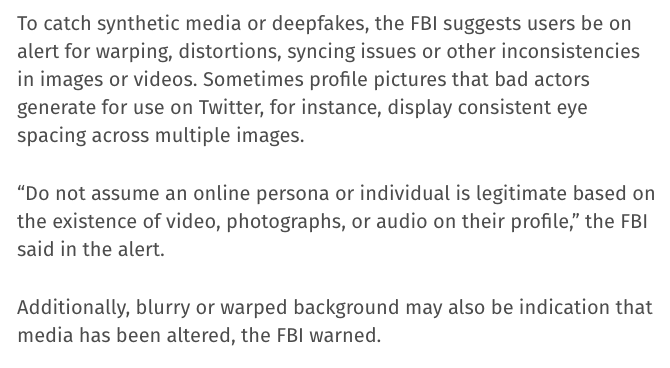
To catch a deepfakes the FBI suggests be on alert for warping, distortions, blurring/syncing issues or other inconsistencies in images/videos: “Do not assume an online persona or individual is legitimate based on the existence of video, photographs, or audio on their profile." 
• • •
Missing some Tweet in this thread? You can try to
force a refresh






