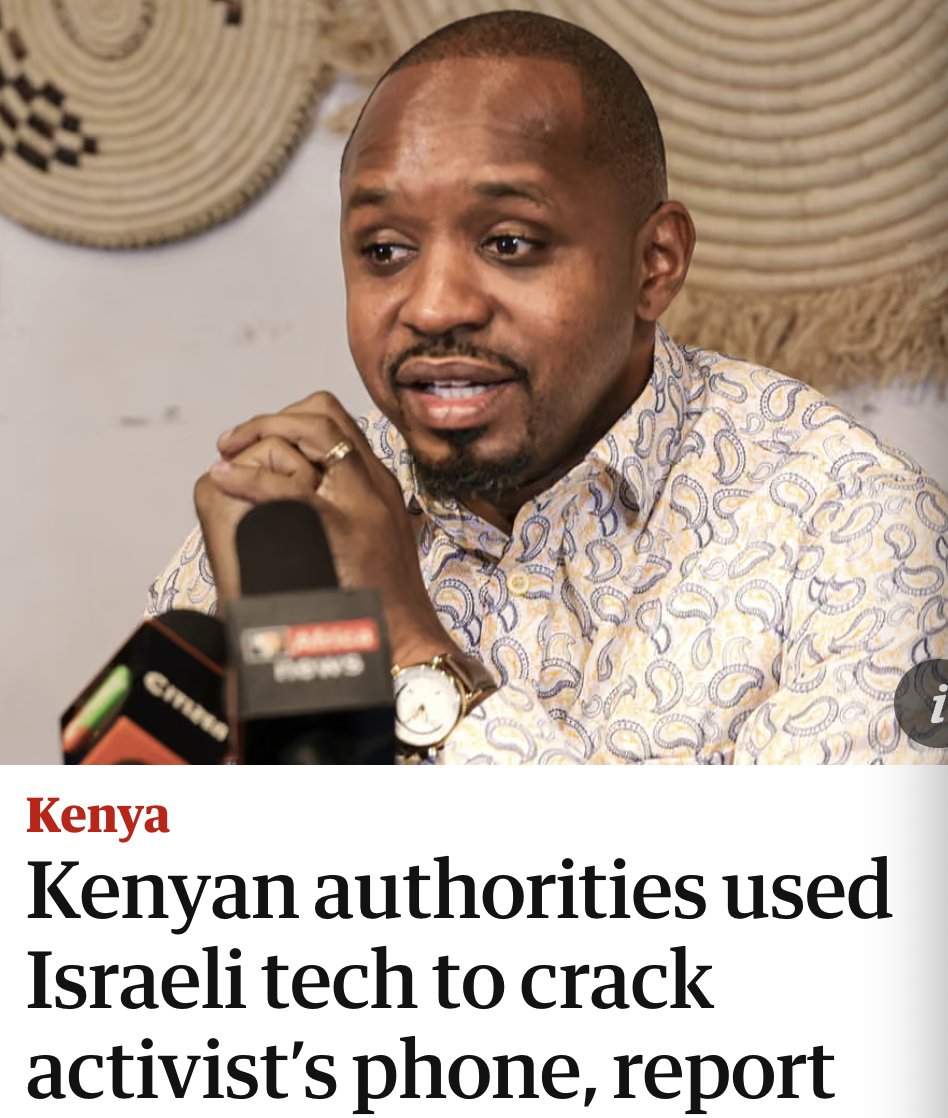
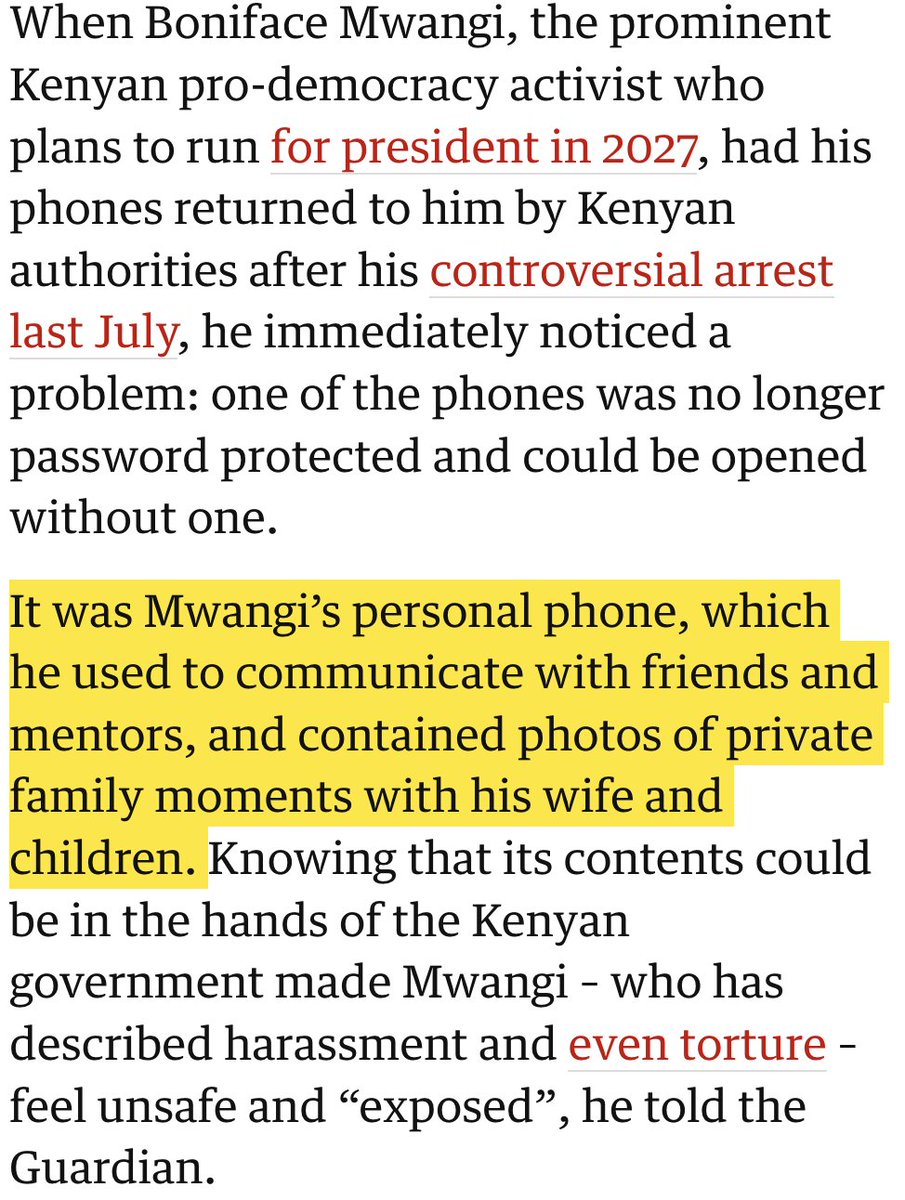
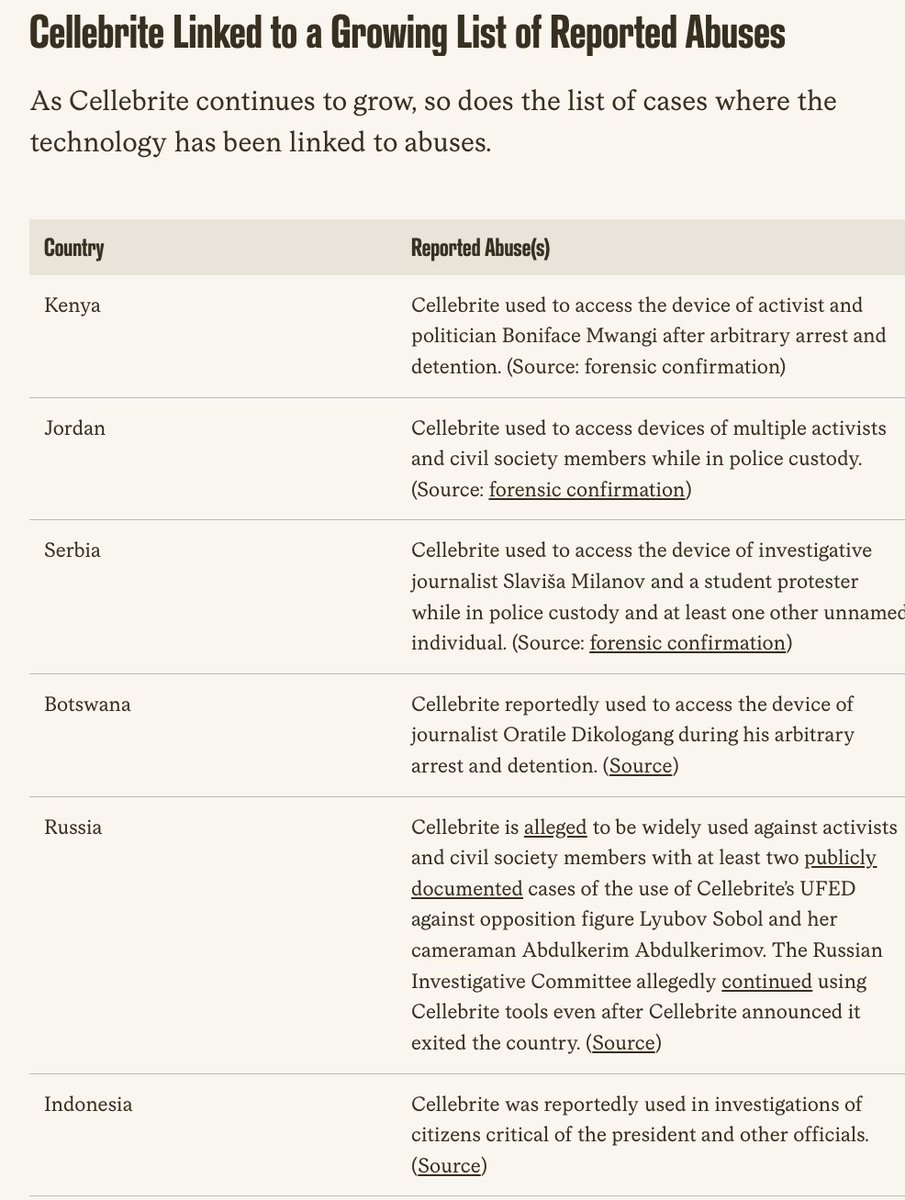
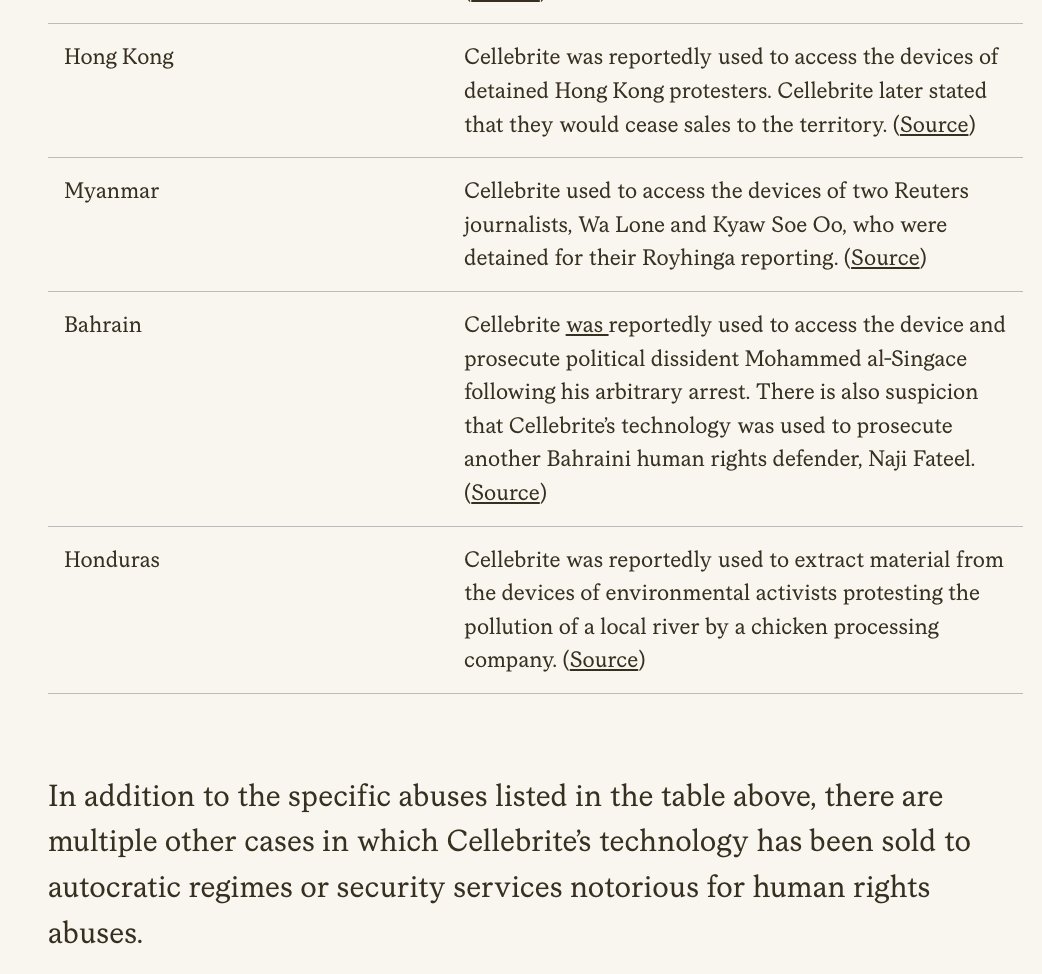
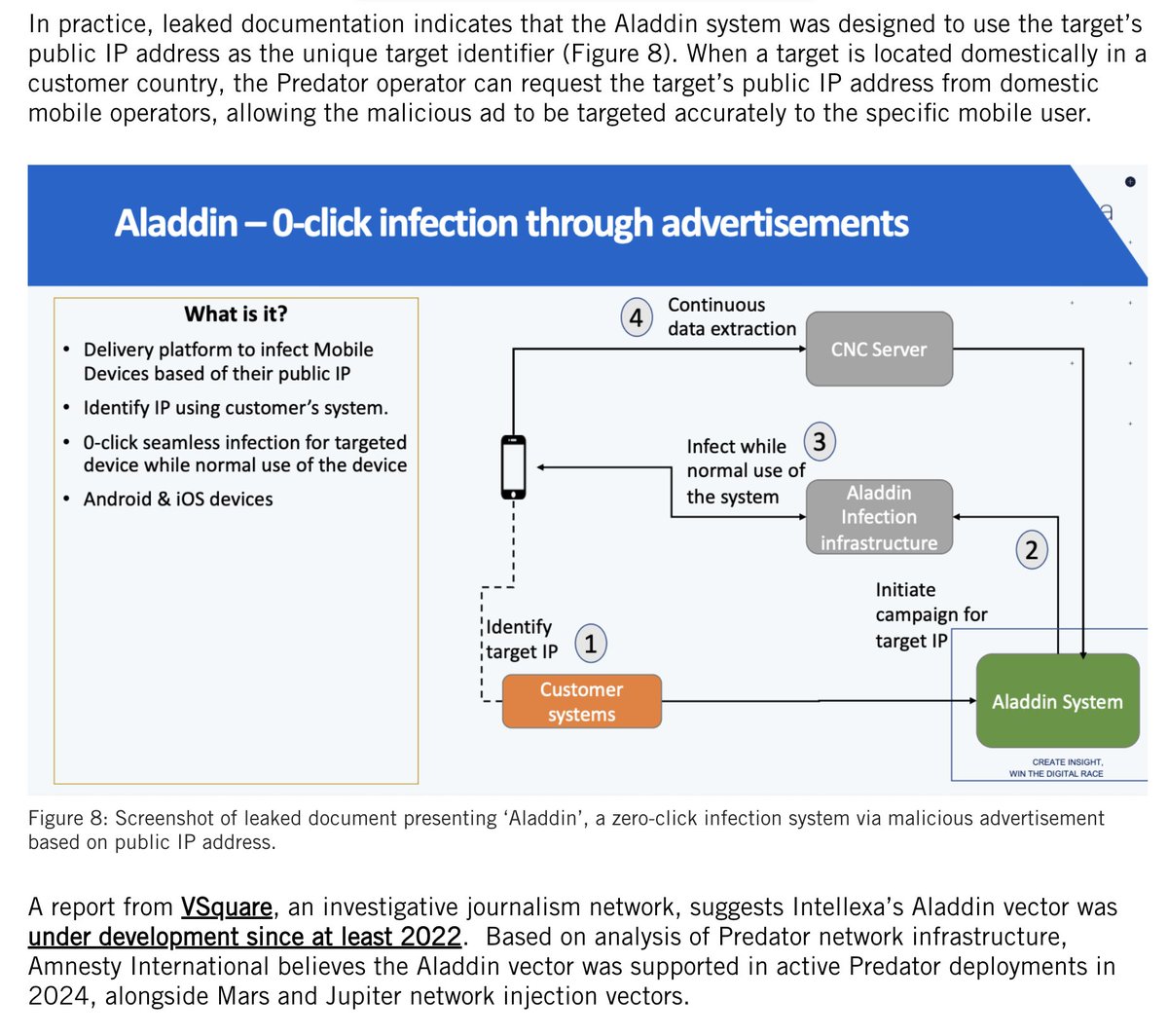
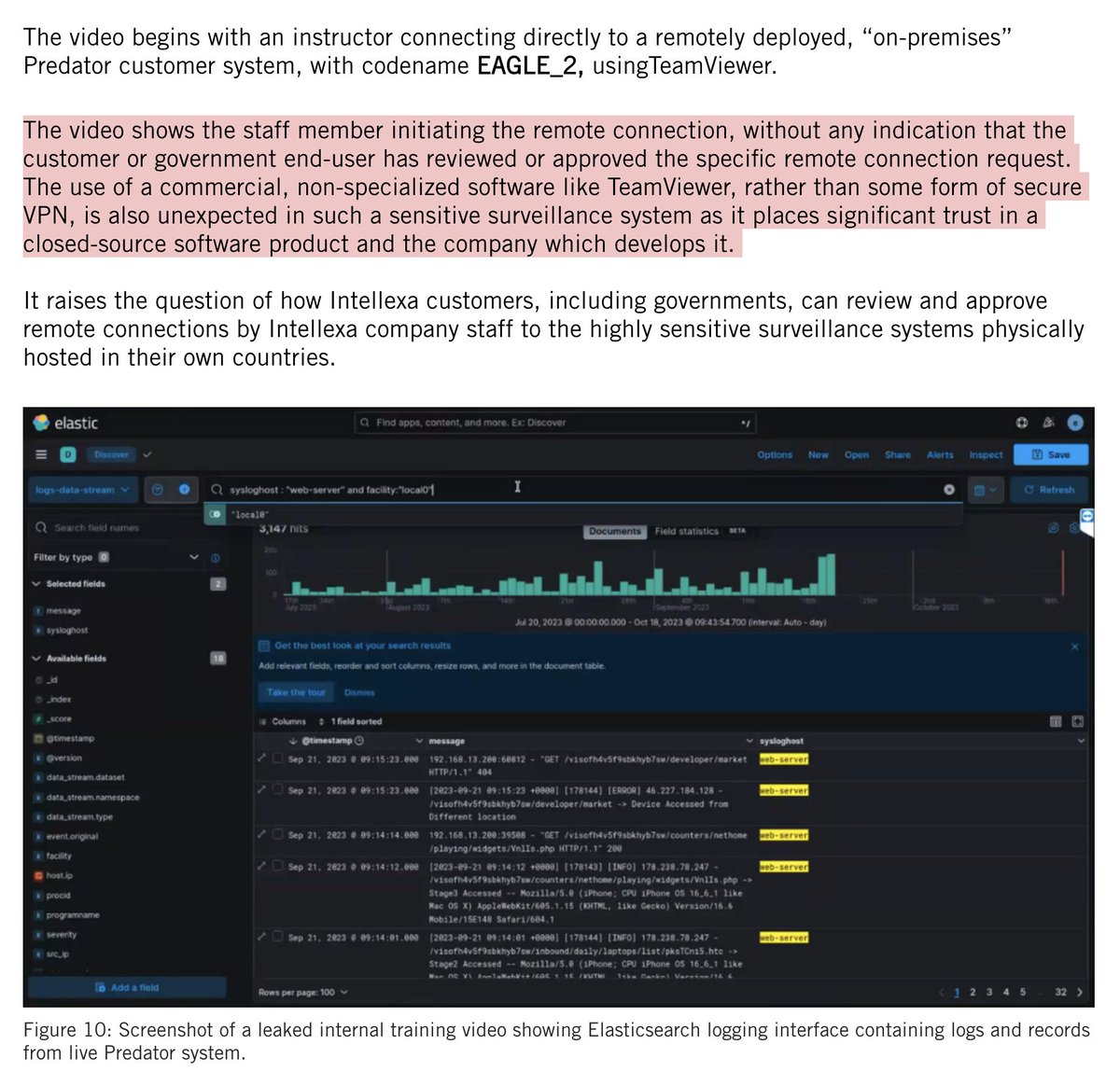
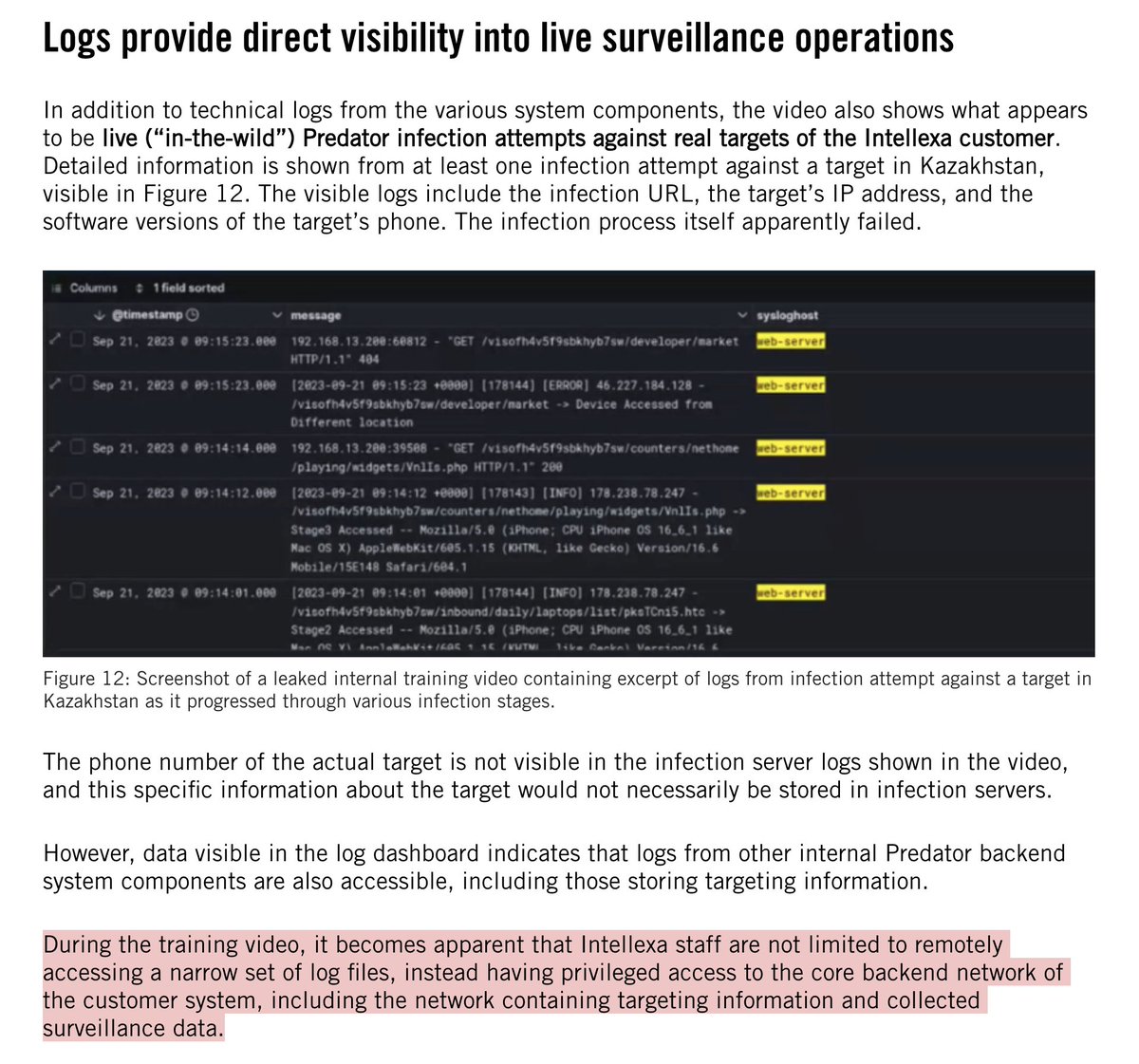
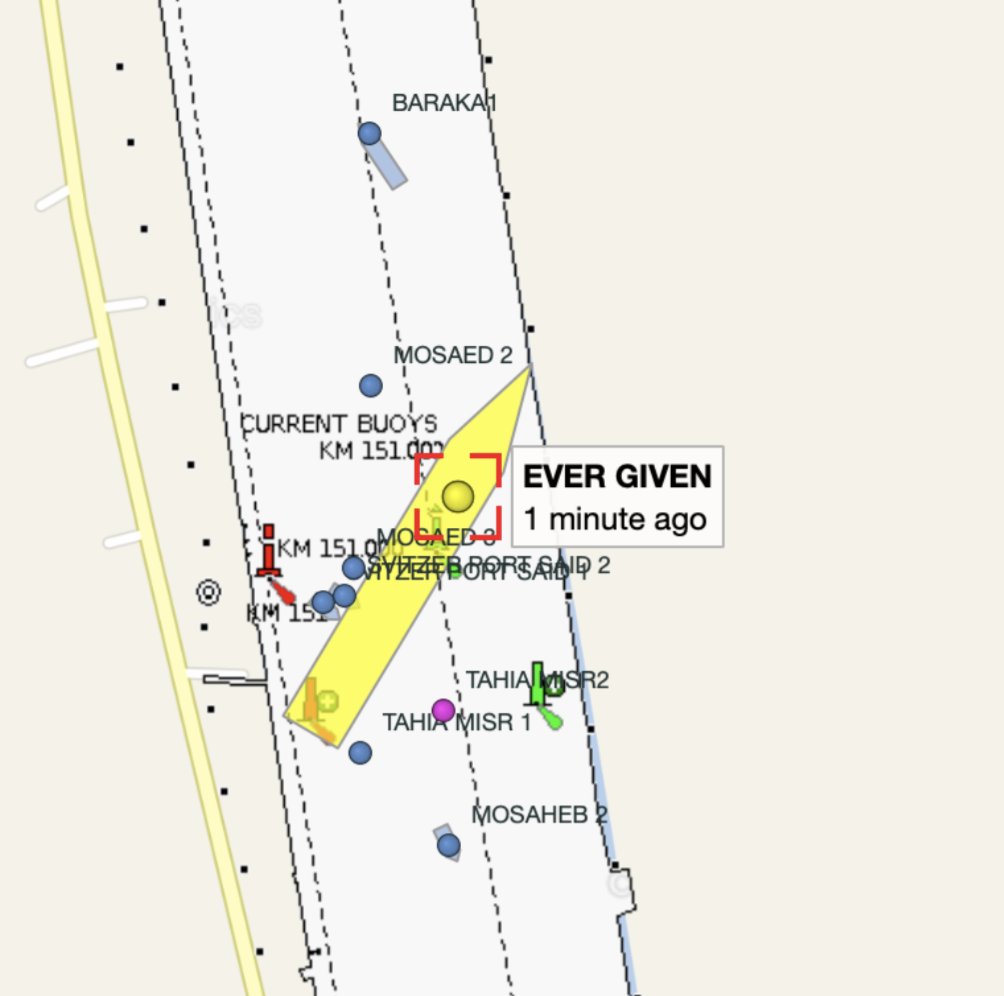
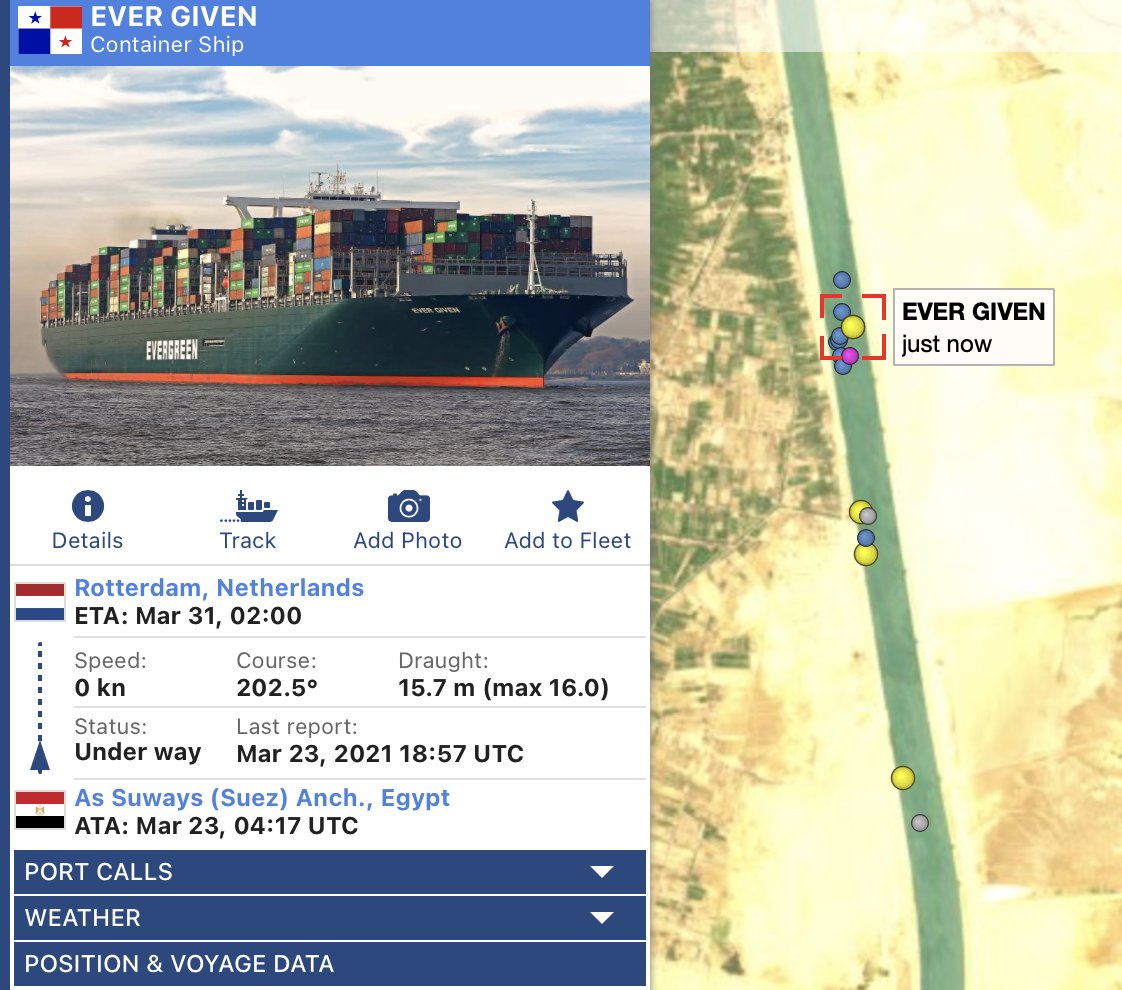
So, the #SuezCanal is blocked...
Massive container ship EVER GIVEN stuck in the most awkward way possible.
Ongoing for hours. Every tug Egypt could spare appear to be trying to pull it free.
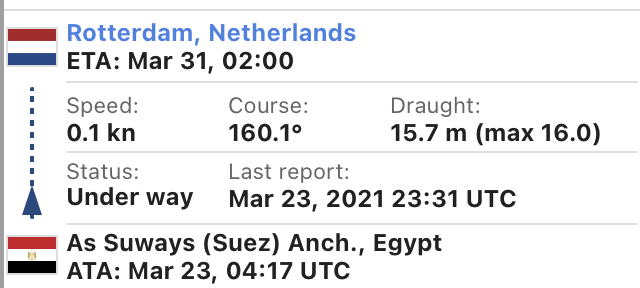
Vessel tracker: vesselfinder.com/?imo=9811000


Massive container ship EVER GIVEN stuck in the most awkward way possible.
Ongoing for hours. Every tug Egypt could spare appear to be trying to pull it free.
Vessel tracker: vesselfinder.com/?imo=9811000

"Is there a traffic jam?" Answer 👇
https://twitter.com/nat_ahoy/status/1374445914169831427
Latest update: the EVER GIVEN is... still ever-jammed across the #SuezCanal.
Also, a teeny excavator tried to help.
Thanks @rmcfadzean for surfacing the pic!
Source: instagram.com/p/CMxEKHanW62/


Also, a teeny excavator tried to help.
Thanks @rmcfadzean for surfacing the pic!
Source: instagram.com/p/CMxEKHanW62/



How soon till one of the big Dutch salvage companies shows up for an ultra-premium re-floating?
Also: forget #iceroadtruckers, marine salvage YouTube is where it's at.
Also: forget #iceroadtruckers, marine salvage YouTube is where it's at.
Update: still stuck.
How big is this #SuezCanal plug? Ultra big.
MV #EVERGIVEN
Size: 400m long / 59m wide
Gross tonnage: 219,079
Capacity: 20,388 TEUs (20ft container equivalents).
One of the largest container ships in operation.
How big is this #SuezCanal plug? Ultra big.
MV #EVERGIVEN
Size: 400m long / 59m wide
Gross tonnage: 219,079
Capacity: 20,388 TEUs (20ft container equivalents).
One of the largest container ships in operation.

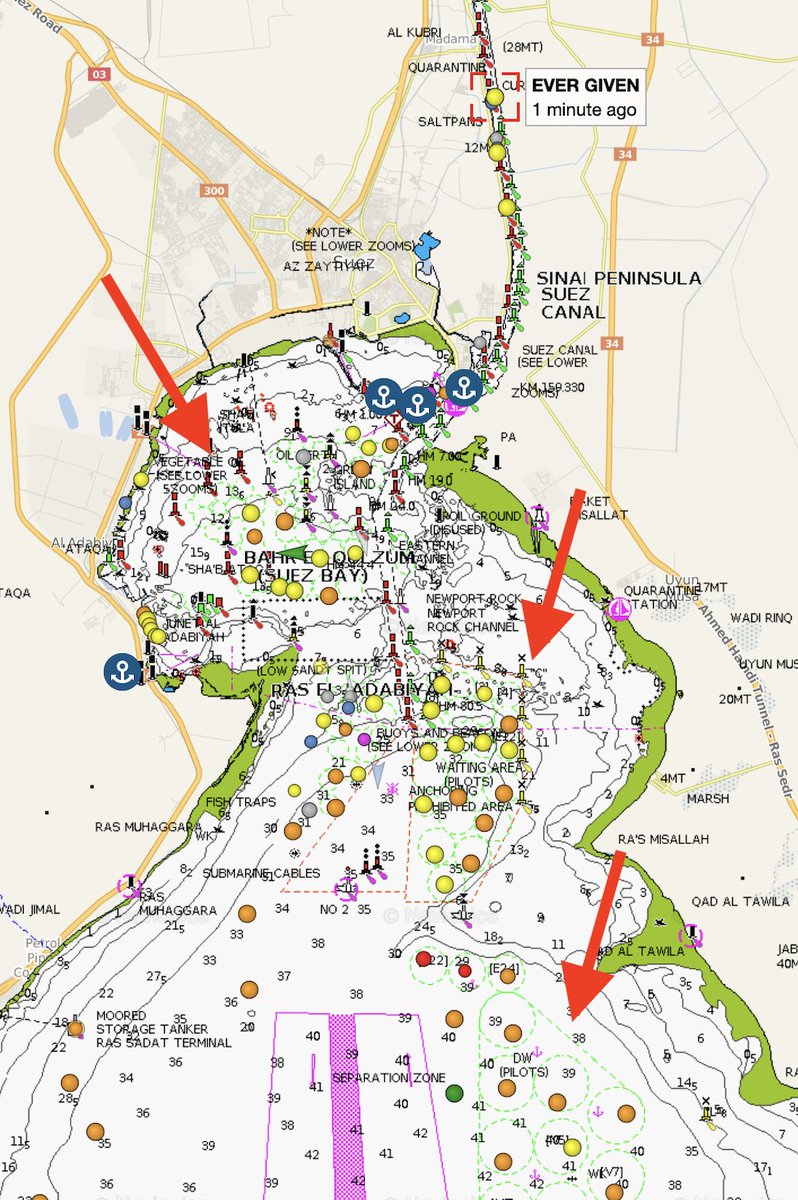
Another update: #SuezCanal waiting areas & anchorages have filled right up (I added some arrows.. look for green dashes)
For the confused: MV EVER GIVEN's operator is Evergreen Marine (evergreen-line.com) and Ever___ is a naming convention for some vessels.


For the confused: MV EVER GIVEN's operator is Evergreen Marine (evergreen-line.com) and Ever___ is a naming convention for some vessels.


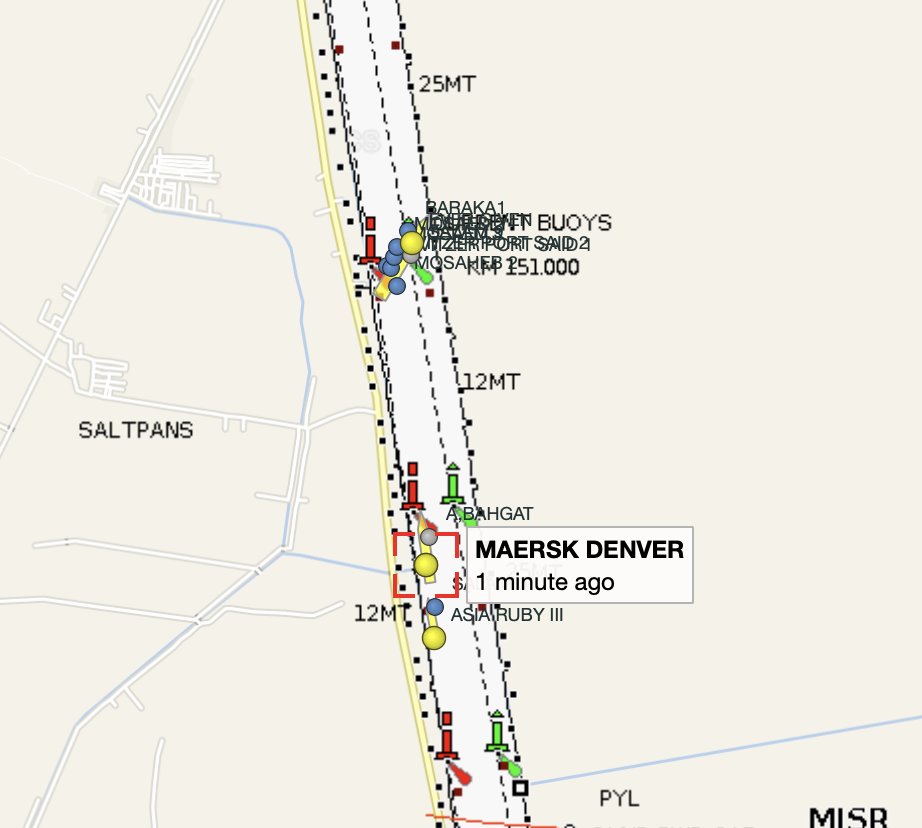
The pic we have comes from insta user fallenhearts17, who is on the @Maersk MV DENVER, stuck right behind MV EVER GIVEN.
Sincerely hope she posts again, Egyptian twitter shows up, or...if you know someone else on the DENVER, drop them a line!
Source: instagram.com/p/CMxEKHanW62/

Sincerely hope she posts again, Egyptian twitter shows up, or...if you know someone else on the DENVER, drop them a line!
Source: instagram.com/p/CMxEKHanW62/

@Maersk NARRATOR: the all-important #SuezCanal lets ships bypass the historically treacherous Horn of Africa...
... to mariners, canal officials have a historic reputation for 'appreciating' cartons of cigarettes...earning it the nickname "Marlboro Canal"
... to mariners, canal officials have a historic reputation for 'appreciating' cartons of cigarettes...earning it the nickname "Marlboro Canal"
1:30 AM Egypt Time Update: screws are turning & helm moving but... #EVERGIVEN appears to be in the same spot.
Austin-powers-stuck-in-tunnel vibe is getting stronger.
I feel for this crew, & the tugboat operators. Nobody is getting any sleep.
Austin-powers-stuck-in-tunnel vibe is getting stronger.
I feel for this crew, & the tugboat operators. Nobody is getting any sleep.
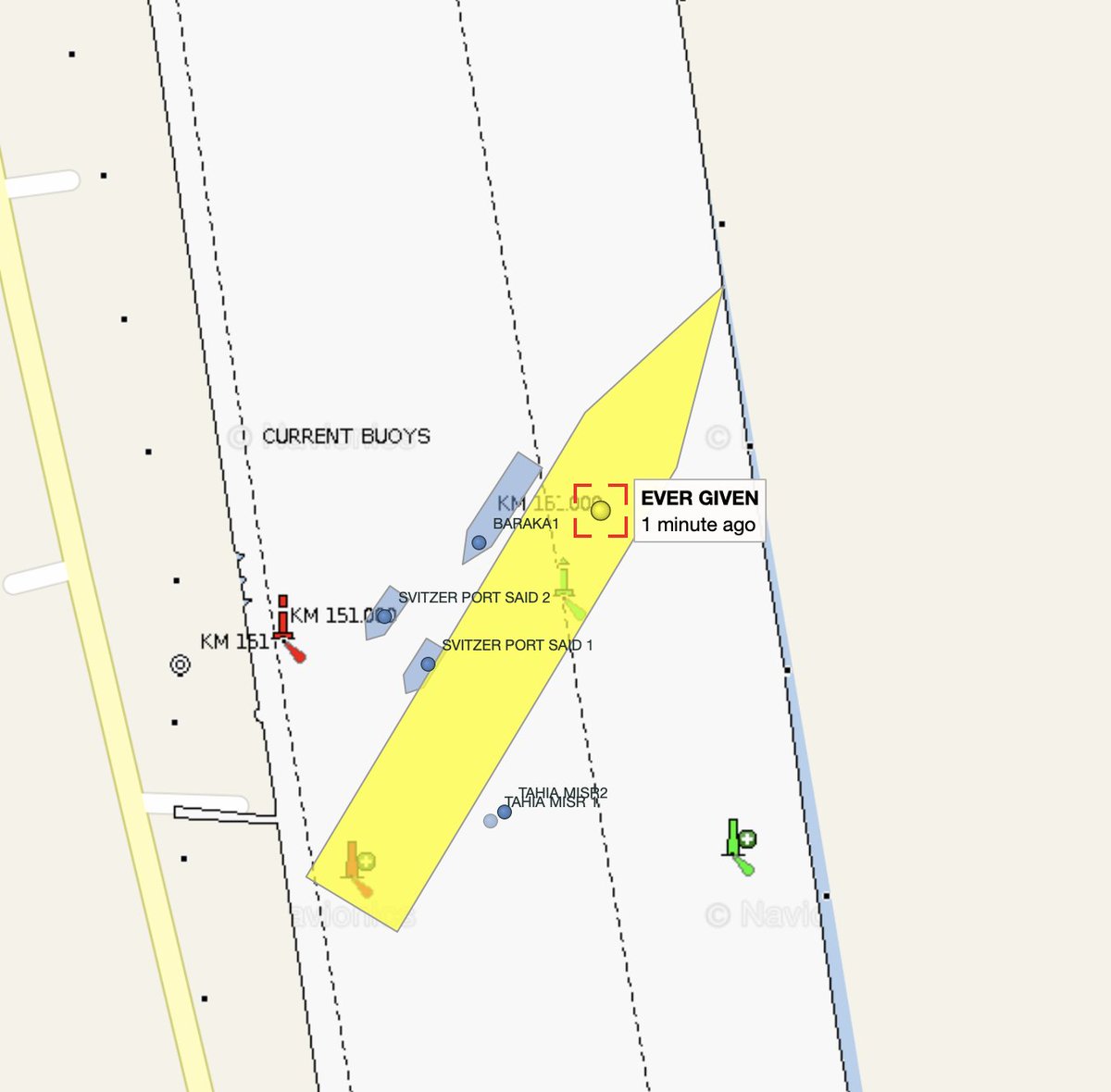
OH NO: misfortune's unerring aim touched #EVERGIVEN's track as it departed the designated anchorage and steamed into the Canal.
(innocent, but terrible luck)
Source: vesselfinder.com/?imo=9811000


(innocent, but terrible luck)
Source: vesselfinder.com/?imo=9811000


AIS data playback of the #SuezCanal the moment things went very, very wrong for the #EVERGIVEN...and then rest of global shipping.
By @TankerTrackers
By @TankerTrackers
Update: #EVERGIVEN still hard aground.
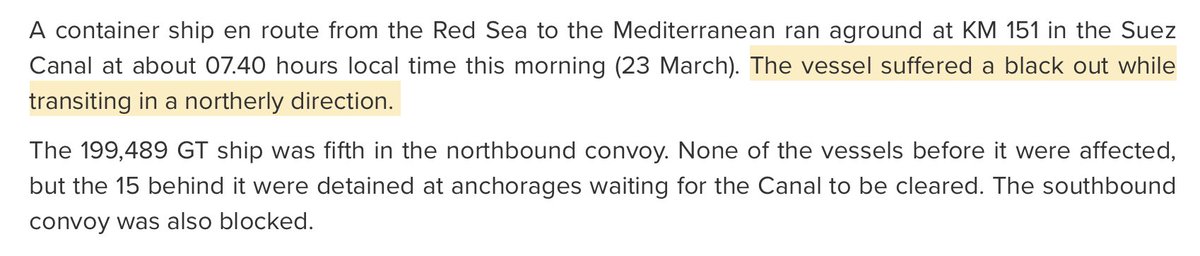
Reports from logistics company GAC say cause of grounding was a blackout.
This is worst-nightmare material when doing a canal transit.
Source: gac.com/news--media/ho…
Reports from logistics company GAC say cause of grounding was a blackout.
This is worst-nightmare material when doing a canal transit.
Source: gac.com/news--media/ho…
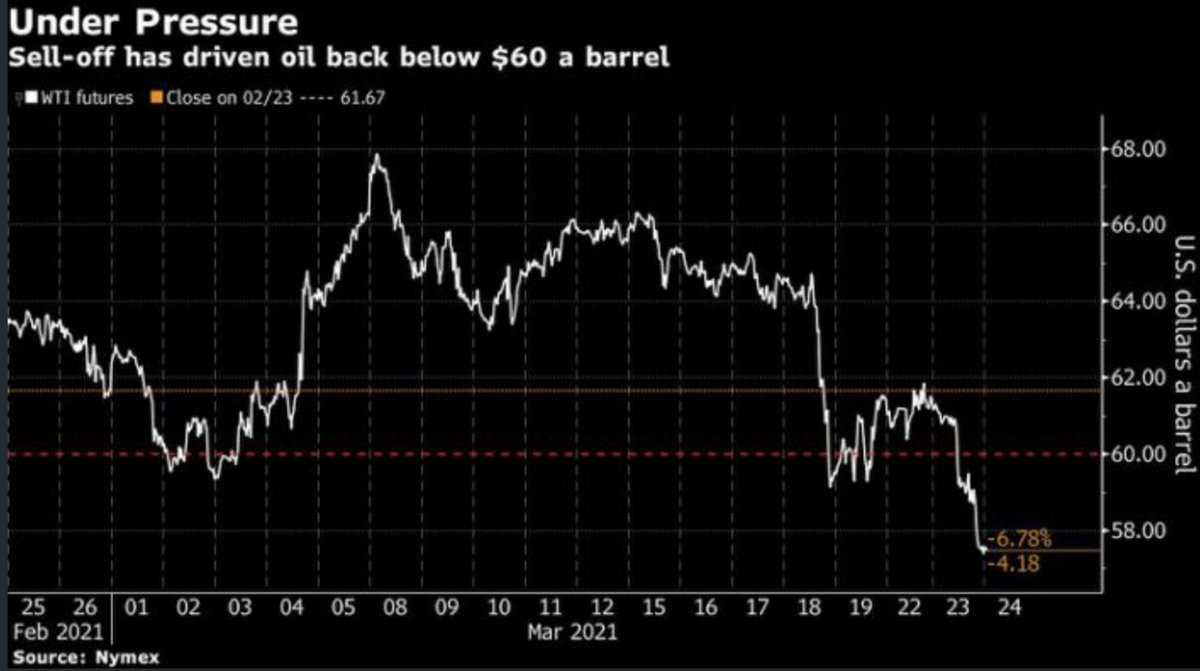
Effect on oil prices? Yes, likely temporary says head of commodities at ING.*
(~10% of global seaborne traded oil transits Suez & SUMED . ~9% of LNG.)
So, what if this closure persists...
*Source: news.yahoo.com/oil-extends-lo…

(~10% of global seaborne traded oil transits Suez & SUMED . ~9% of LNG.)
So, what if this closure persists...
*Source: news.yahoo.com/oil-extends-lo…

If for some reason the #SuezCanal blockage persists, shipping can divert.
Some oil will still flow through SUMED, but for everything else: global logistics madness. For example, US EIA calculates that a US tanker from KSA would add ~2,700 miles.
eia.gov/todayinenergy/…
Some oil will still flow through SUMED, but for everything else: global logistics madness. For example, US EIA calculates that a US tanker from KSA would add ~2,700 miles.
eia.gov/todayinenergy/…

Errata: nothing like a nit in a fun thread to bug me to no end...
I inadvertently left on the cutting room floor NARRATOR saying "AND the Cape of Good Hope."👇
No wonder I had so many chars to work with..
Also, #EverGiven is still stuck.
I inadvertently left on the cutting room floor NARRATOR saying "AND the Cape of Good Hope."👇
No wonder I had so many chars to work with..
Also, #EverGiven is still stuck.
https://twitter.com/jsrailton/status/1374488621319823364
OUF: new pics suggest the #EVERGIVEN might have impaled the canal shore with its bulbous bow. Wild if true.
Bulbous bows look weird but modify how water flows around the bow, making ships more efficient.
Cant find credits on pics 1&2, 3 is shipbuilder Samusung Heavy Industries.


Bulbous bows look weird but modify how water flows around the bow, making ships more efficient.
Cant find credits on pics 1&2, 3 is shipbuilder Samusung Heavy Industries.



HEADS UP: reports that #EVERGIVEN is partially re-floated likely premature.
Source, Lloyds List, citing vessel's technical manager Bernhard Schulte Shipmanagement (BSM).
Also, quick check of AIS shows... little change.
Pics: Suez Canal Authority
…list.maritimeintelligence.informa.com/LL1136229/Suez…



Source, Lloyds List, citing vessel's technical manager Bernhard Schulte Shipmanagement (BSM).
Also, quick check of AIS shows... little change.
Pics: Suez Canal Authority
…list.maritimeintelligence.informa.com/LL1136229/Suez…




PSA: woke to find inaccurate things circulating about the #EVERGIVEN situation.
Origin: various sources, some breathless, some from Egypt.
Spoiler: still stuck.
Are you a reporter? Vessel's technical manager BSM has a media contact. They should know.
bs-shipmanagement.com/en/media/1-med…
Origin: various sources, some breathless, some from Egypt.
Spoiler: still stuck.
Are you a reporter? Vessel's technical manager BSM has a media contact. They should know.
bs-shipmanagement.com/en/media/1-med…

UPDATE: MV #EVERGIVEN....still ever-so-stuck.
But...
-Multiple tugboats on scene (not new)
-Dredgers clearing sand & mud around hull
-Vessel's own winches in play
Says Bernhard Schulte Shipmanagement, via CNBC's @PippaStevens13 cnbc.com/2021/03/24/eve…
But...
-Multiple tugboats on scene (not new)
-Dredgers clearing sand & mud around hull
-Vessel's own winches in play
Says Bernhard Schulte Shipmanagement, via CNBC's @PippaStevens13 cnbc.com/2021/03/24/eve…
INBOX: seeking expert for media thing about #EVERGIVEN
ME: I'm not the maritime industry insider you need.
DETAIL: In college I briefly had the ambition to become a captain. Read the materials & crewed summers (e.g. tall ships) to build sea time for a license. Then moved on.
ME: I'm not the maritime industry insider you need.
DETAIL: In college I briefly had the ambition to become a captain. Read the materials & crewed summers (e.g. tall ships) to build sea time for a license. Then moved on.
Geospatial companies have begun flexing on the #EVERGIVEN..
-@planetlabs from 23rd: visual spectrum, low-res (color)
-@capellaspace: synthetic aperture radar (grayscale)
Also: I hope someone(s) has splashed out & tasked a high resolution commercial satellite for a pass.



-@planetlabs from 23rd: visual spectrum, low-res (color)
-@capellaspace: synthetic aperture radar (grayscale)
Also: I hope someone(s) has splashed out & tasked a high resolution commercial satellite for a pass.




It's going to be a while for the #EVERGIVEN.
Curious in meantime about what a #SuezCanal transit on a container ship looks like?
Maritime vlogger JeffHK's content is always good & this vid is an interesting watch.
Curious in meantime about what a #SuezCanal transit on a container ship looks like?
Maritime vlogger JeffHK's content is always good & this vid is an interesting watch.
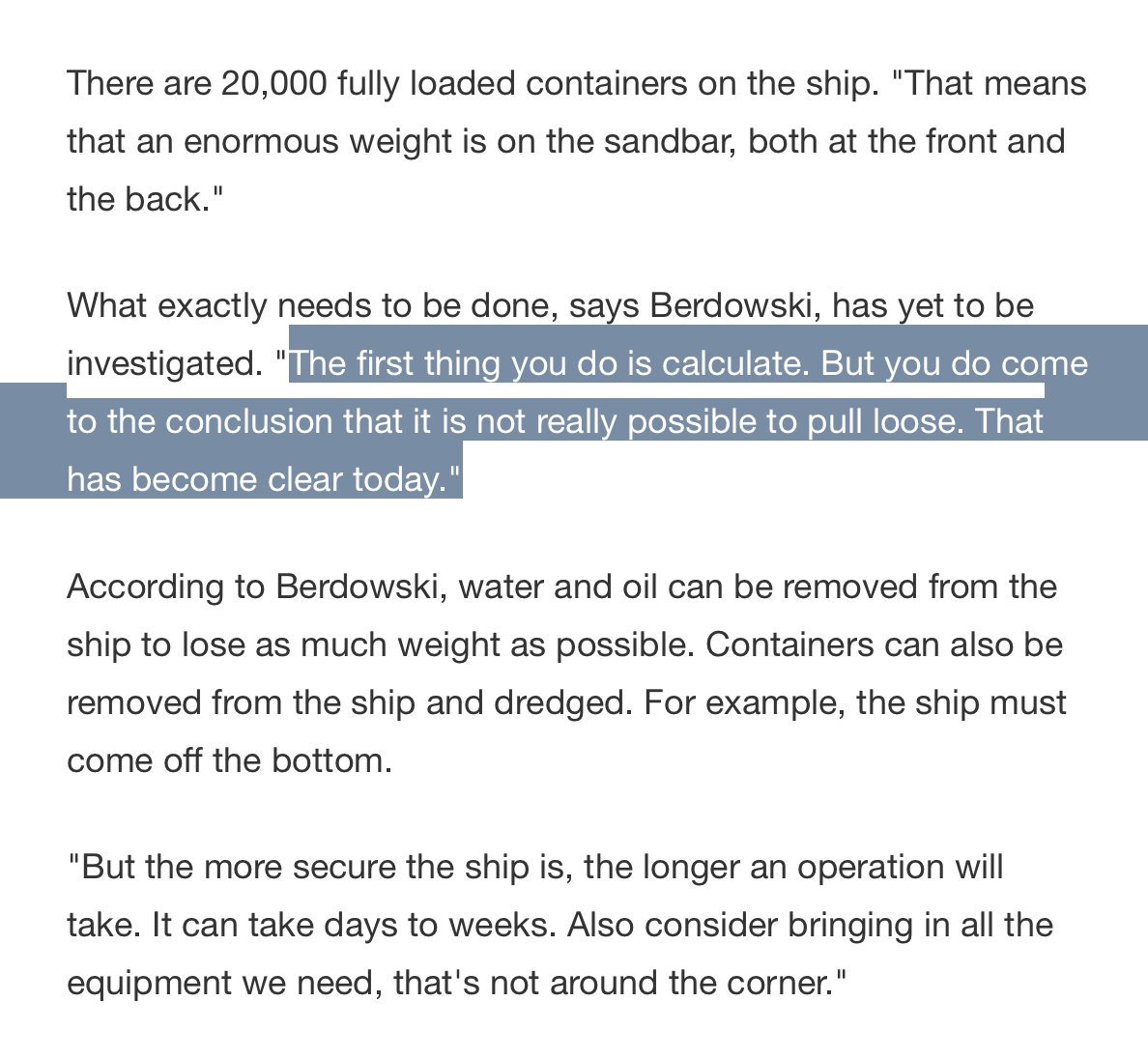
UPDATE: Help on the way for #EVERGIVEN.
Dredging & heavy lift experts Boskalis have a team steaming towards the "very heavy whale on the beach"* & expect to arrive Thursday AM.
CEO: could take days, or weeks.
*Google translate...
Story: nos.nl/nieuwsuur/arti…


Dredging & heavy lift experts Boskalis have a team steaming towards the "very heavy whale on the beach"* & expect to arrive Thursday AM.
CEO: could take days, or weeks.
*Google translate...
Story: nos.nl/nieuwsuur/arti…


Good work lil digger! #EVERGIVEN's bulbous bow has emerged.
No longer impaling, its now resting the #SuezCanal's shore.
Pic: Suez Canal Authority
No longer impaling, its now resting the #SuezCanal's shore.
Pic: Suez Canal Authority

The MV MAERSK DENVER just cleared the #SuezCanal breakwater, backwards, under tow.
#SuezCanal's hardworking tugs have now removed the full northbound convoy stuck behind the #EVERGIVEN.
Some already back at anchor at designated berths (E.g. pic 3 ASIA RUBY III)


#SuezCanal's hardworking tugs have now removed the full northbound convoy stuck behind the #EVERGIVEN.
Some already back at anchor at designated berths (E.g. pic 3 ASIA RUBY III)



NEW image from @AirbusSpace flexing their Pléiades constellation on the #SuezBLOCKED situation.
Our favorite excavator is barely visible, digging away.
Oblique shot (satellites are cool!) pointed NW is undated. Now-gone MAERSK DENVER is there, so.. probably yesterday.



Our favorite excavator is barely visible, digging away.
Oblique shot (satellites are cool!) pointed NW is undated. Now-gone MAERSK DENVER is there, so.. probably yesterday.




Confession: seeing it from space makes me realize I've developed feelings for...excavator #MARYANNE2
So (informally) christened because every child deserves to have Mike Mulligan and his Steam Shovel read to them.
I've found it on YouTube:



So (informally) christened because every child deserves to have Mike Mulligan and his Steam Shovel read to them.
I've found it on YouTube:




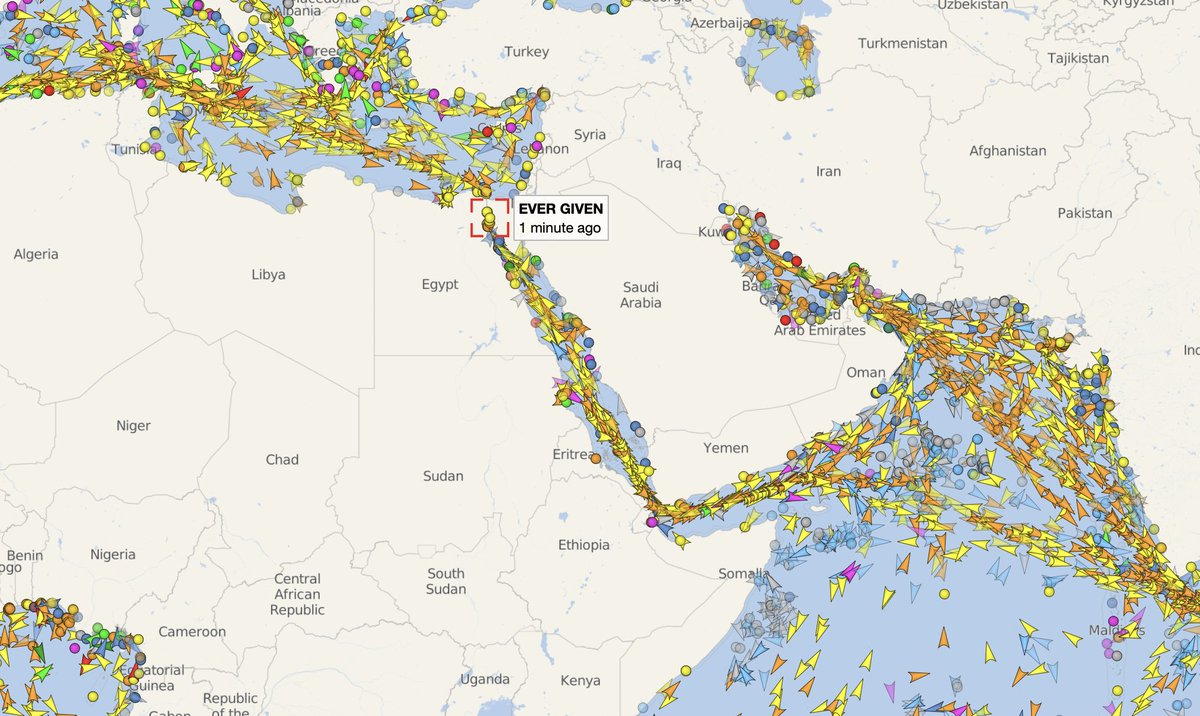
Seeing folks sharing marine traffic rounding Africa & concluding #Suez block is the cause.
Gentle fact check:
-ships aren't that fast
-these are major shipping lanes.
..but it will become more true if #EVERGIVEN stays stuck.
Pic: Tracks from 2012 (shipmap.org)
Gentle fact check:
-ships aren't that fast
-these are major shipping lanes.
..but it will become more true if #EVERGIVEN stays stuck.
Pic: Tracks from 2012 (shipmap.org)

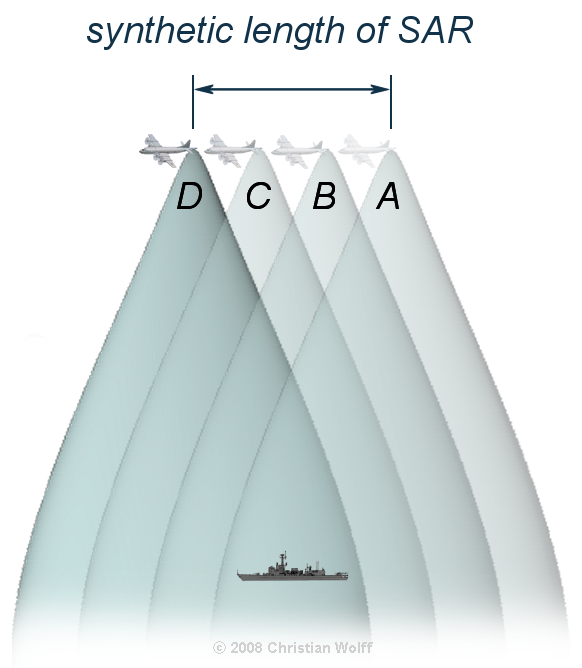
Curious? A Synthetic Aperture Radar (SAR) satellite zips along, beaming down radio waves. Some stuff reflects them (🚢 = bling), water not so much (🌊= dark). Classic radar.
Then antenna movement is leveraged to make a longer 'synthetic' antenna, getting you detail & dimension.


Then antenna movement is leveraged to make a longer 'synthetic' antenna, getting you detail & dimension.


The @Maxar image features the dredge. Doing what beyond trying to free the #EVERGIVEN's bow?
Likely opening up the not-usually-dredged & super shallow (blue) part of the canal by the vessel's bow.

Likely opening up the not-usually-dredged & super shallow (blue) part of the canal by the vessel's bow.


NICE: friends @bellingcat have put together a neat little OSINT synthesis!
Bonus: they found some shipping apparently turning & heading 'round Africa. bellingcat.com/resources/2021…
Bonus: they found some shipping apparently turning & heading 'round Africa. bellingcat.com/resources/2021…
UPDATE: 10:45PM in the #Suez and nobody is thinking about sleep.
So many tugboats on scene. Some big. Some small. Some probably pushing, others totally tugging.
For her part, the #EVERGIVEN remains stubbornly stuck.
So many tugboats on scene. Some big. Some small. Some probably pushing, others totally tugging.
For her part, the #EVERGIVEN remains stubbornly stuck.

Fact checking super popular tweets claiming that 1000s of ships are suddenly going the long way around Africa.
No. Please slow down :)
-These are longstanding super-busy shipping routes (pic 3)
-Even diverted ships don't move fast enough to be there yet.


No. Please slow down :)
-These are longstanding super-busy shipping routes (pic 3)
-Even diverted ships don't move fast enough to be there yet.



UPDATE: under much tugging and pushing the #EVERGIVEN 'budged.'
By how much? Accounts varied. Led to brief optimism, reflected in the..uh soundtrack... of this video out of Egypt.
However...still stuck tonight.
By how much? Accounts varied. Led to brief optimism, reflected in the..uh soundtrack... of this video out of Egypt.
However...still stuck tonight.
UPDATE: the *big tugboats with big pull* are coming. Expected arrival: 28th (pics)
-crew in good health (no word on morale, pride)
-no reported cargo damage or pollution
-early investigation rules out mechanical failure.
Source: BSM (#EVERGIVEN's technical manager)


-crew in good health (no word on morale, pride)
-no reported cargo damage or pollution
-early investigation rules out mechanical failure.
Source: BSM (#EVERGIVEN's technical manager)



UPDATE: tug-all-day & dredge-at-night continues.
-20,000 tons of muck sucked from around #EVERGIVEN
-Bow 'loosened'
-Stern cleared
-Rudder & propellor 'fully functional'
Per Evergreen. Video: dredger in action, via SCA #SuezBLOCKED
-20,000 tons of muck sucked from around #EVERGIVEN
-Bow 'loosened'
-Stern cleared
-Rudder & propellor 'fully functional'
Per Evergreen. Video: dredger in action, via SCA #SuezBLOCKED
Let's appreciate the MASHHOUR, the dredger that must suck muck till the ship comes unstuck.
Annotated a charming Suez Canal Authority *painting* of her for you #SuezBLOCKED
Annotated a charming Suez Canal Authority *painting* of her for you #SuezBLOCKED

Too embarrassed to ask about the "EVERGREEN" vs. #EVERGIVEN deal?
Evergreen Marine Corp. leases the ship. Some Evergreen container ships have the naming convention "EVER G____".
Others include: EVER GLOBE, EVER GENIUS, EVER GIFTED, EVER GENTLE, etc.
Evergreen Marine Corp. leases the ship. Some Evergreen container ships have the naming convention "EVER G____".
Others include: EVER GLOBE, EVER GENIUS, EVER GIFTED, EVER GENTLE, etc.

The moon is full & the tides are high, but Italian tug Carlo Magno is late for her date with #EVERGIVEN tonight.
Re-floating attempt postponed. Another will be made tomorrow.
(Dutch tug Alp Guard arrived on time)
Sources: SCA, vessel tracking. Pic: Reuters.
Re-floating attempt postponed. Another will be made tomorrow.
(Dutch tug Alp Guard arrived on time)
Sources: SCA, vessel tracking. Pic: Reuters.

BREAKING: SERIOUS MOVEMENT HAPPENING NOW.
Latest AIS data shows that the #EVERGIVEN's stern has been dramatically pivoted off the #Suez Canal's Western wall.
Stern now appears to be in the channel.


Latest AIS data shows that the #EVERGIVEN's stern has been dramatically pivoted off the #Suez Canal's Western wall.
Stern now appears to be in the channel.



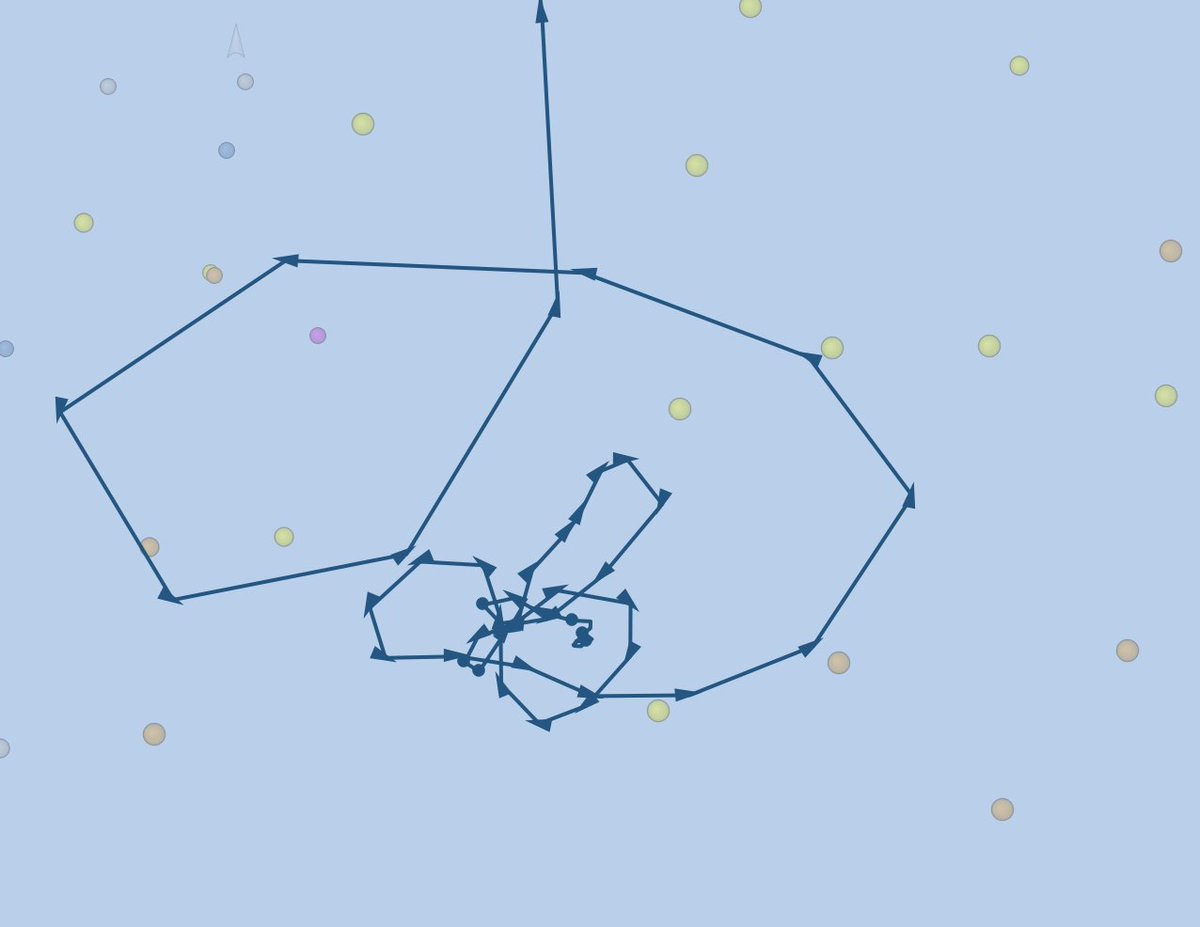
I count 17 tugs & support vessels on scene right now.
If you want to see how hard they have strained on the #EVERGIVEN I've included some of their tracks here.
Nice indirect illustration of how much the ship has shifted.



If you want to see how hard they have strained on the #EVERGIVEN I've included some of their tracks here.
Nice indirect illustration of how much the ship has shifted.




Made a quick diagram. This is a big change from the initial stuck situation...but the navigation channel is still partially obstructed by the #EVERGIVEN
The #Suez Canal is not opening to vessel traffic just yet...
The #Suez Canal is not opening to vessel traffic just yet...

So @AP now has the “partially refloated” report about this movement.
But... I think it was the wise @mercoglianos who said "partially refloated" means still "partially stuck"
But... I think it was the wise @mercoglianos who said "partially refloated" means still "partially stuck"
https://twitter.com/AP/status/1376388470063632384
Sunup in the #Suez & things indeed look different.
Video of the #EVERGIVEN's new, less meme-worthy position.
Video of the #EVERGIVEN's new, less meme-worthy position.
Here's a quick & approximate illustration I made of how the crews shifted the #EVERGIVEN overnight.
Usual caveats.
Usual caveats.

BREAKING: the #EVERGIVEN is ON THE MOVE, headed northwards at around 3 knots (3.5mph).
What a great thing to see.

What a great thing to see.


Joyful tooting from the tugboats that freed the #EVERGIVEN.
Position update: the ship is 1.6 nm north of her stuck position...and still moving!
Video: Egyptian Cabinet.
Position update: the ship is 1.6 nm north of her stuck position...and still moving!
Video: Egyptian Cabinet.
UPDATE: much joyful tooting as the dredge says goodbye to the #EVERGIVEN.
POSITION: ship is now >2 nautical miles north of her stuck position, steaming at just under 3 knots.
Roughly a half day till she hits the Great Bitter Lake.
Video @DailyNewsEgypt
POSITION: ship is now >2 nautical miles north of her stuck position, steaming at just under 3 knots.
Roughly a half day till she hits the Great Bitter Lake.
Video @DailyNewsEgypt
Folks, you love to see it.
Trailed by tugboats #EVERGIVEN is making 7 knots (~8mph) UNDER HER OWN POWER.
Quickly approaching Bitter Lakes.
Chance to move from the main #Suez navigation channel & let the 1st convoy of ships past.

Trailed by tugboats #EVERGIVEN is making 7 knots (~8mph) UNDER HER OWN POWER.
Quickly approaching Bitter Lakes.
Chance to move from the main #Suez navigation channel & let the 1st convoy of ships past.


BREAKING: the #Suez Canal now both OPEN and MOVING.
First Southbound convoy steaming into Suez canal from Port Said anchorage.
Long-stuck southbound convoy in Great Bitter Lake also resuming transit.


First Southbound convoy steaming into Suez canal from Port Said anchorage.
Long-stuck southbound convoy in Great Bitter Lake also resuming transit.



The #Suez Canal is moving & #EVERGIVEN is free. She's no doubt steaming towards a port for more inspections.
Time to inspect my...uh neglected inbox.
Thanks all that participated in this *epic thread.*
Where it all began👇👇
Time to inspect my...uh neglected inbox.
Thanks all that participated in this *epic thread.*
Where it all began👇👇
https://twitter.com/jsrailton/status/1374438210315513864
PSST: Legends at #SmitSalvage are competitive about making the best salvage YouTube videos.
I'm sure they won't disappoint for the #EVERGIVEN.
Subscribing to their channel in 3...2... youtube.com/channel/UCrL7O…
I'm sure they won't disappoint for the #EVERGIVEN.
Subscribing to their channel in 3...2... youtube.com/channel/UCrL7O…
The #Suez Canal is very much moving! Convoys making the transit now.
Will still take days for the backlog to clear.
Will still take days for the backlog to clear.

• • •
Missing some Tweet in this thread? You can try to
force a refresh