
1/ 🐛 📝 🥞 🆚 2️⃣
🚨 Smart Contract Bug found in Pancake V2 🚨
🐛: Pancake new router is incompatible with Pancake LP implementation.
Users may get __revert__ txs upon __swaps__ due to the bug.
Vulnerability was reported to @PancakeSwap team asap.
Thread below 👇
🚨 Smart Contract Bug found in Pancake V2 🚨
🐛: Pancake new router is incompatible with Pancake LP implementation.
Users may get __revert__ txs upon __swaps__ due to the bug.
Vulnerability was reported to @PancakeSwap team asap.
Thread below 👇
2/ After @PancakeSwap V2 announcement, we have been working on supporting the new V2 pools.
✅ As with our security standard, we always perform smart contract review and testing, to ensure our users’ safety.
❗️ We have found and informed the @PancakeSwap team on the issue.
✅ As with our security standard, we always perform smart contract review and testing, to ensure our users’ safety.
❗️ We have found and informed the @PancakeSwap team on the issue.
3/ 🐛 So, what is the actual bug?
The question comes down to: what changes from Pancake V1 to V2?
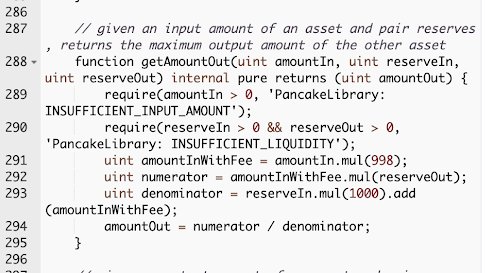
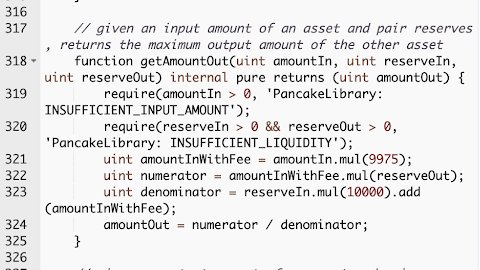
1️⃣ Swap fees: 0.2% ➡️ 0.25%
2️⃣ Fee distribution to LPs, to dev address
Below are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.

The question comes down to: what changes from Pancake V1 to V2?
1️⃣ Swap fees: 0.2% ➡️ 0.25%
2️⃣ Fee distribution to LPs, to dev address
Below are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.
4/ On the LP pair side, __swap__ function also encodes the swap fee for constant product calculation. Here are the V1 and V2 implementation: 

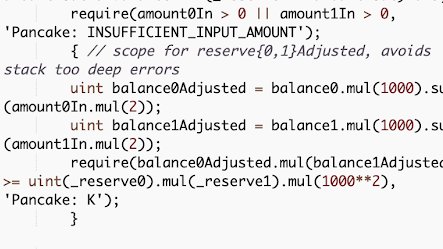
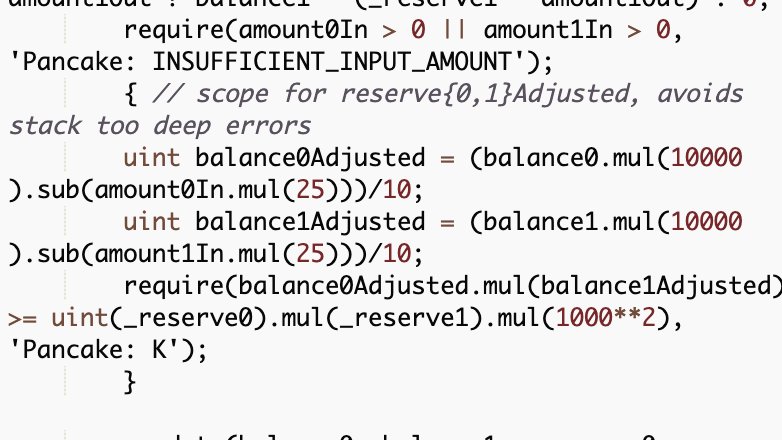
5/ 👀 At first glance, the implementation seems correct, as the parameters reflect 0.2% and 0.25% in the old and new versions, respectively.
However, in Solidity, there is no floating-point.
All divisions will be rounded down ⬇️.
However, in Solidity, there is no floating-point.
All divisions will be rounded down ⬇️.
6/ So, __balance0Adjusted__ and __balance1Adjusted__ can have their actual values truncated, reverting the next __require__ statement when checked for the constant product monovariant. 
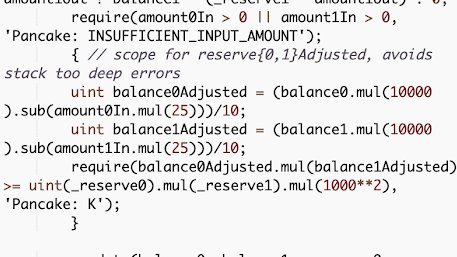
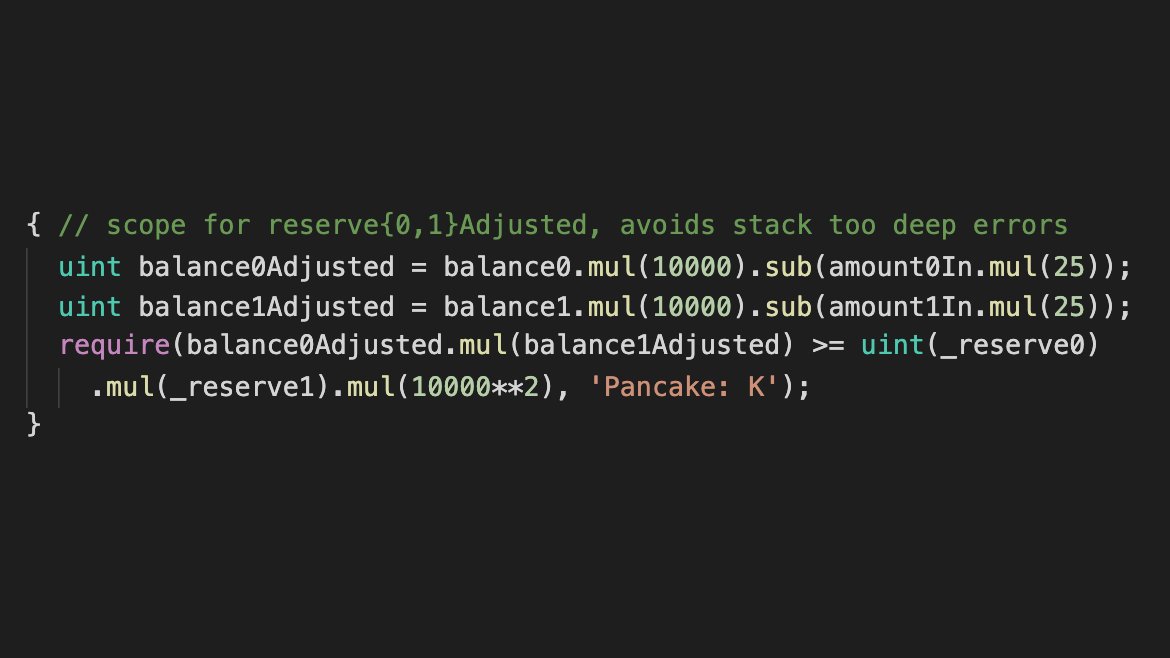
7/ Instead of performing divisions, it’s mostly always better to compare the cross-multiplication. This should be the correct implementation: 
9/ So, the next question is: How does this affect #AlphaHomora?
#AlphaHomora performs multiple complex txs into one, including swaps. This means that users who open new positions, refill existing positions, and also liquidations may get revert txs.
#AlphaHomora performs multiple complex txs into one, including swaps. This means that users who open new positions, refill existing positions, and also liquidations may get revert txs.
10/ 💦 As liquidation is one of the core security features of #AlphaHomora to keep the protocol solvent, this bug can cause security loopholes in our system.
Even if the chances of tx reversions are not high, security is one of @AlphaFinanceLab’s top priorities.
Even if the chances of tx reversions are not high, security is one of @AlphaFinanceLab’s top priorities.
11/ After we’ve found the bug and made sure it’s reproducible, we immediately contacted @PancakeSwap team to inform them re:vulnerability.
They immediately responded and confirmed the vulnerability within minutes.
They immediately responded and confirmed the vulnerability within minutes.
12/ To fix the issue, a new factory, router, and LP pairs need to be deployed.
We’ll be working towards supporting these new pools and again performing checks and tests on the new implementation.
🛄 And so let the new migration begin...
We’ll be working towards supporting these new pools and again performing checks and tests on the new implementation.
🛄 And so let the new migration begin...
https://twitter.com/PancakeSwap/status/1385501978667618304
• • •
Missing some Tweet in this thread? You can try to
force a refresh



