Want cliff notes on the chip shortage?
It’s fairly complex with all kinds of defensive & offensive tactics at play, but here is a summary from my position:
1/n
It’s fairly complex with all kinds of defensive & offensive tactics at play, but here is a summary from my position:
1/n
I design PCBs & have them assembled. All the little components on the board are purchased from a supplier, and have a reliable cost.
Many of the components have a piece of silicon inside them. Take this Arduino PCB for instance:
2/n
Many of the components have a piece of silicon inside them. Take this Arduino PCB for instance:
2/n
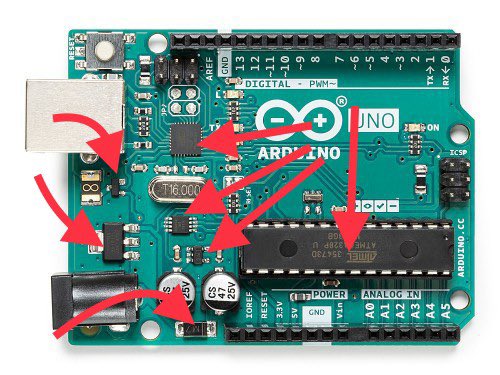
There are very few places that can produce this piece of silicon. The component makers are basically paying for time slots on the machines at the silicon fabs.
The pandemic cause auto makers to cancel their slots because they expected low demand.
3/n
The pandemic cause auto makers to cancel their slots because they expected low demand.
3/n
All the other component makers gladly took the slots. But then the auto makers realized their estimates were wrong. So they bought back those slots at 6-8x the cost. And governments pushed to give priority to the auto makers.
4/n
4/n
This translates to higher costs for everyone else, but also much longer wait times as everyone gets bumped out. Add in increased chip demand, & suddenly we have shortages.
If just one component is out of stock, my entire PCB cannot be made.
5/n
If just one component is out of stock, my entire PCB cannot be made.
5/n
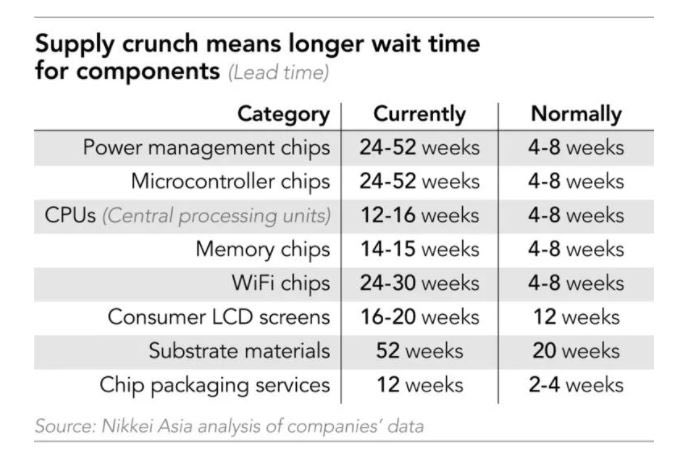
Normally that means waiting 1-2months for the stock to come back. But now the lead time is more like 1 year.
6/n
6/n
The amount of finished components on the market is fairly limited. So now PCB manufacturers of all sizes are resorting to buying up what they can and hoarding it. If they don’t, they won’t have products for their customers for a year or longer.
7/n
7/n
But you also have market competitors. What happens if your competitor has components but you don’t? What happens if you buy up what your competitor needs to hurt them? (it’s happening!)
8/n
8/n
When it gets down to the small independent hardware makers, we don’t have as much $ to participate in most of this.
If we are lucky, we can rebuild our PCB to use a different component. But by the time you do so, the replacement part is out of stock.
9/n
If we are lucky, we can rebuild our PCB to use a different component. But by the time you do so, the replacement part is out of stock.
9/n
There is way more going on, but that’s the high level.
You will probably see hardware go out of stock for extended periods of time. And if the maker is small, they may not survive long enough to put them back on the shelves. Sadly, that has already started happening.
10/n
You will probably see hardware go out of stock for extended periods of time. And if the maker is small, they may not survive long enough to put them back on the shelves. Sadly, that has already started happening.
10/n
I’m certainly missing a lot here. So I welcome additional info!
People off the top of my head who are also in this space: @colinoflynn @securelyfitz @esden @ktemkin @Chris_Gammell @zhovner @obra @GregDavill @timonsku @joegrand @nwsayer
People off the top of my head who are also in this space: @colinoflynn @securelyfitz @esden @ktemkin @Chris_Gammell @zhovner @obra @GregDavill @timonsku @joegrand @nwsayer
I may actually do a video that allows this to be covered in slightly more depth if anyone is interested in viewing that (or collaborating on it!)
I have seen varying opinions on when chip supply returns to normal if nothing else bad happens (like one chip fab starting on fire, one losing power for an extended period, or the upcoming drought for another). Seems to be in the range of 1-2 years.
13/n
13/n
From that point, it usually takes 2-5 months for a PCB to get assembled and eventually go up for sale.
14/n
14/n
FOLLOWUP
Since this thread seems to be helpful for others, I’ll add more as it comes up.
Some of us are seeing significant rises in component prices from those who hoarded with the intent to resell. Colin here was quoted a 60x jump in price. 😭
15/n
Since this thread seems to be helpful for others, I’ll add more as it comes up.
Some of us are seeing significant rises in component prices from those who hoarded with the intent to resell. Colin here was quoted a 60x jump in price. 😭
15/n
https://twitter.com/colinoflynn/status/1391788417017651202
A month later and the pricing is still silly
https://twitter.com/sad_electronics/status/1404537541823537159
Shipping costs are going through the roof now. This obviously applies to anything being transported in a shipping container, not just electronics.
https://twitter.com/davellorens/status/1408493964429172736
The shipping container issue is its own complex supply chain problem. Heavily backed up ports, under staffing, empty containers on the wrong side of the world (imbalanced trade flows), etc.
But it goes to show how many fragile & complex pipelines are needed for goods.
18/n
But it goes to show how many fragile & complex pipelines are needed for goods.
18/n
Assembly houses are now sending cold emails that offer up cannibalism services to deal with the shortage.
This kind of thing costs SO much money to do.
19/n
This kind of thing costs SO much money to do.
19/n
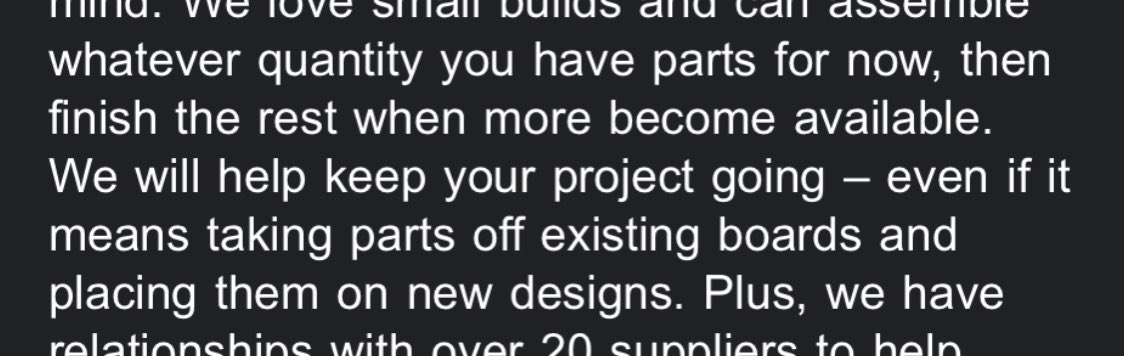
This is continuing to take a heavy toll on small companies. This is terrible.
20/n
20/n
https://twitter.com/dangoodin001/status/1417995035182698496
Flipper Zero is hitting some serious hurdles of delays and component prices jumping by 20x
@zhovner must have his hands full right now. Pretty detailed post on the numerous problems:
kickstarter.com/projects/flipp…
21/n
@zhovner must have his hands full right now. Pretty detailed post on the numerous problems:
kickstarter.com/projects/flipp…
21/n
I just tried to buy a chip antenna. (No silicon. Just a wire encapsulated in ceramic) It’s out of stock almost everywhere with a 10 month lead time.
One shop hoarded them all and wants 500% the normal price.
22/n
One shop hoarded them all and wants 500% the normal price.
22/n
It’s the time of year when contracts are negotiated for most silicon fab. Costs are going up by 20% and discounts for big customers are going away.
While this means prices will rise, I’m hoping it means that chip access for small players improves.
wsj.com/articles/world…
23/n
While this means prices will rise, I’m hoping it means that chip access for small players improves.
wsj.com/articles/world…
23/n
• • •
Missing some Tweet in this thread? You can try to
force a refresh











