How to get URL link on X (Twitter) App

 Yes. I’d love to know what “I have confirmation … its turned off” refers to as well :p
Yes. I’d love to know what “I have confirmation … its turned off” refers to as well :p



 The Atlantic article on this touches on policy of where & how these comms should happen, but completely misses the Signal failure that started this.
The Atlantic article on this touches on policy of where & how these comms should happen, but completely misses the Signal failure that started this. 
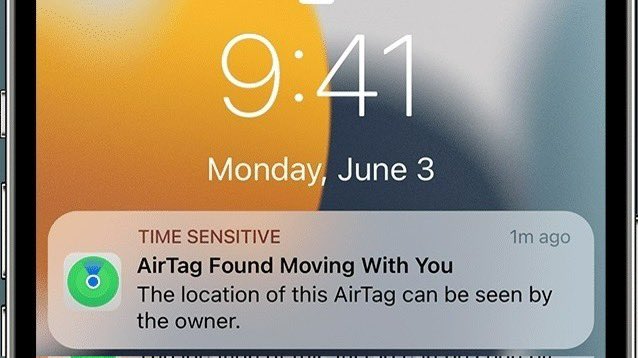

https://twitter.com/uk_daniel_card/status/1861451286937280804


 Every large company has security tools running on employee computers. It’s critical for detecting breaches of security & providing trails of evidence to understand how. Employees bypassing inactivity timeouts get caught in the net & are easy to detect IF the company WANTS.
Every large company has security tools running on employee computers. It’s critical for detecting breaches of security & providing trails of evidence to understand how. Employees bypassing inactivity timeouts get caught in the net & are easy to detect IF the company WANTS.
https://twitter.com/nottscooterr3/status/1796645988439826922First, USB-C is a specification for the physical connector. NOT the protocol. And it intentionally supports multiple protocols like USB, USB-PD, Thunderbolt, DisplayPort, HDMI, PCIe, etc.







https://twitter.com/samwcyo/status/1570583182726266883Also, in the 95% chance this was kids: maybe don’t throw the book at them. Realize how bad it could have gone if this was a funded adversary.
https://twitter.com/jrozner/status/1570112245077807105It looks like iOS apps do not have this issue, nor does MacOS Safari. They can all use local. So it feels like an oversight, but the optics are not great with the release of Passkey, and the constant push toward iCloud services.



https://twitter.com/Ax_Sharma/status/1499764199618228227These are common and fixable mistakes. Whatever. But not notifying does 2 things:
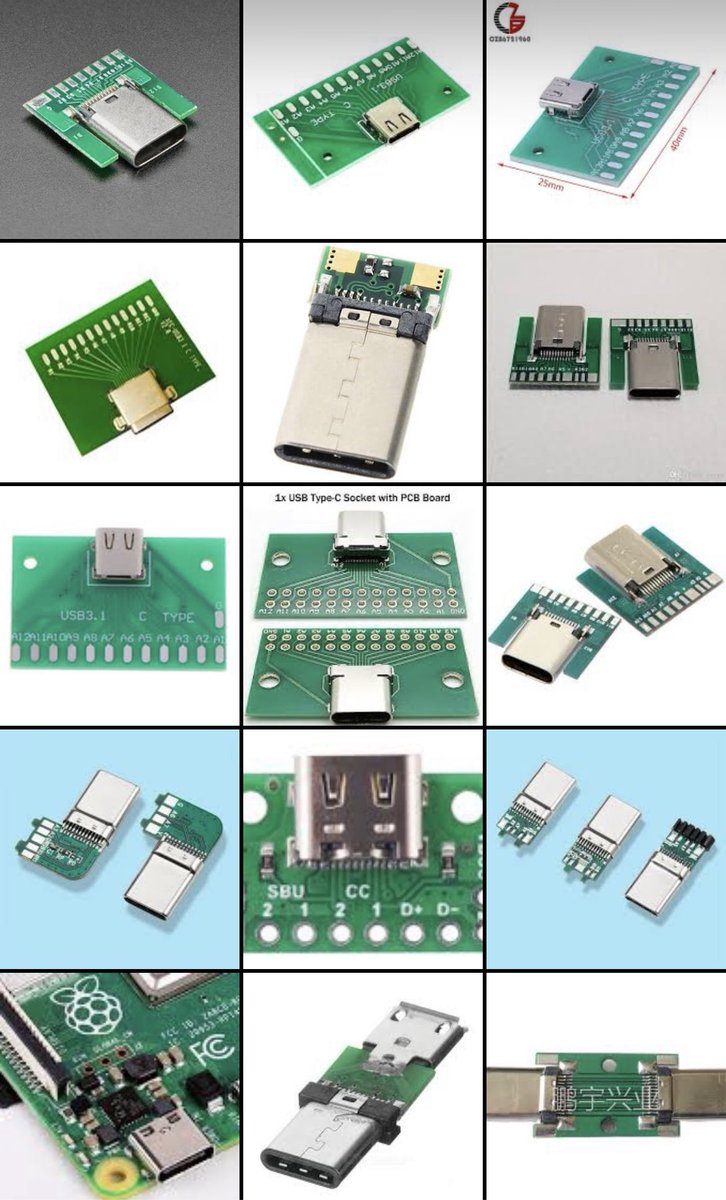
 Let’s compare the pin density of a common USB Micro connector to the most common USB C connector.
Let’s compare the pin density of a common USB Micro connector to the most common USB C connector. 


 So first, let’s run through WHY this is my ideal option for loading firmware, especially for hardware designed for mischief.
So first, let’s run through WHY this is my ideal option for loading firmware, especially for hardware designed for mischief. 