(1/n) The other day, @JulioUrena asked a great question in the BloodHound Slack:
"How can I determine which Group Policies apply to members of a certain group?"
We can use #BloodHound to answer this question, but I want to explain the moving pieces here as well
"How can I determine which Group Policies apply to members of a certain group?"
We can use #BloodHound to answer this question, but I want to explain the moving pieces here as well
(2/n) Group Policy can't be applied directly to security groups, except when using SID filtering and linking the Group Policy correctly. SID filtering on GPOs is not very common, so #BloodHound doesn't currently model that.
We can still use #BloodHound to figure this out though
We can still use #BloodHound to figure this out though
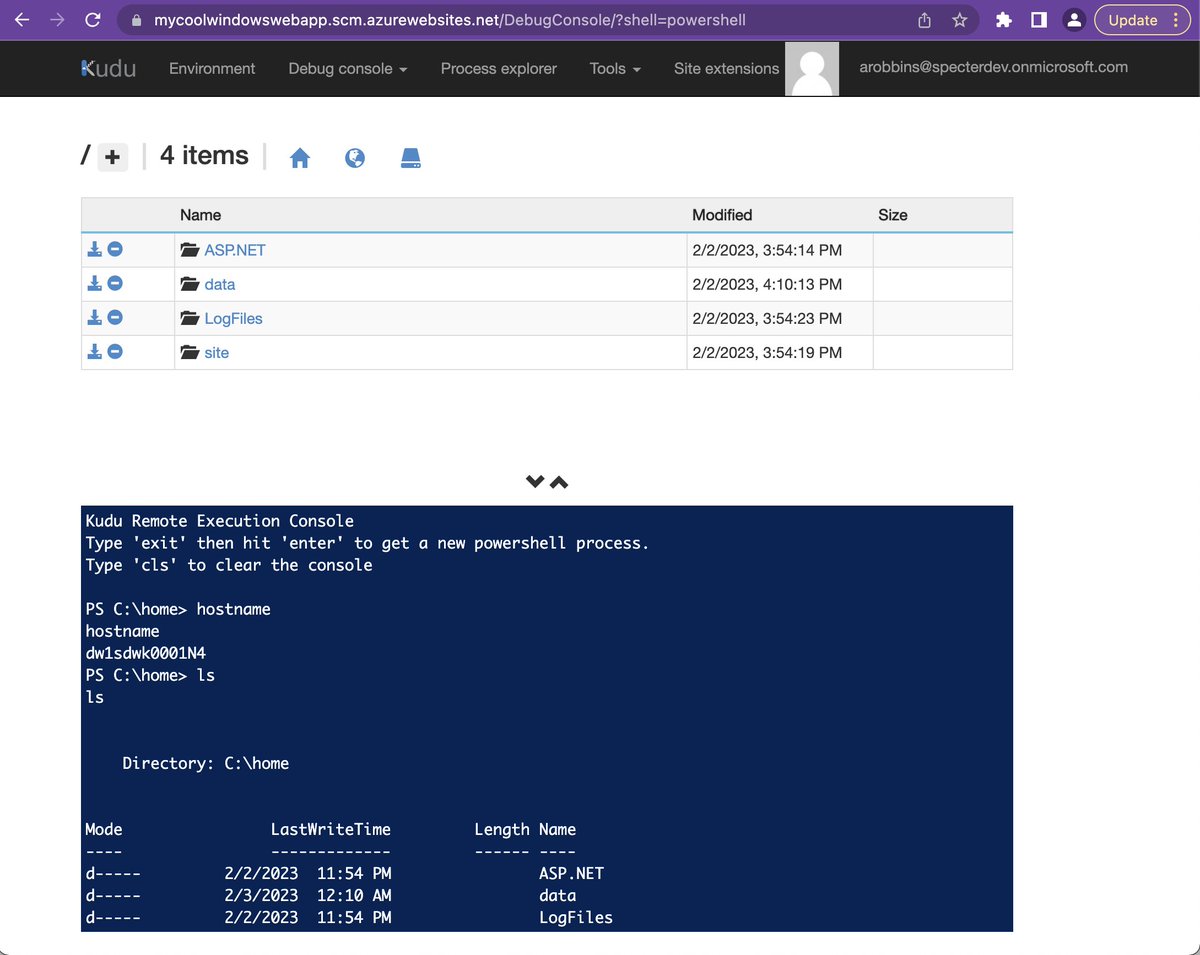
(3/n) Take for example this security group -- real data so labels are hidden (left CTRL in BloodHound GUI). This group has 7 users in it, but because it has a group added to it... 

(5/n) Group Policies are linked to containers, so let's find out where these users live in the OU tree structure: 

(7/n) The best part of all this? The cypher for this query is *very* simple, and @neo4j completes the query in milliseconds: 

(8/8) Read more about how Group Policy works here: wald0.com/?p=179 - with special thanks to @grouppolicyguy.
Join the #BloodHound Slack here: bloodhoundgang.herokuapp.com
Join the #BloodHound Slack here: bloodhoundgang.herokuapp.com
• • •
Missing some Tweet in this thread? You can try to
force a refresh